GEMS
Open World Pioneer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP

Hey Folks, today we have come up with a very tremendous tool called “WPrecon” which is specially made for WordPress reconnaissance or penetration testing purposes.
About WPrecon Tool
WPrecon (WordPress Recon) is a tool for wordpress exploration, fully developed in golang, to get better performance from your device. We are still in the alpha/beta phase, there are still bugs to be fixed, but we are discovering them over time. The focus is to make wprecon the best wordpress exploration tool, and keeping wprecon for free.
Let’s take a look
Dependencies Setup – Golang Installation
Go is an open source programming language that makes it easy to build simple, reliable, and efficient software. The Wprecon tool is designed in the Go language, so we have to install the Go language environment in our linux machine to operate this tool.
apt install golang1apt install golang
Wprecon Tool Installation
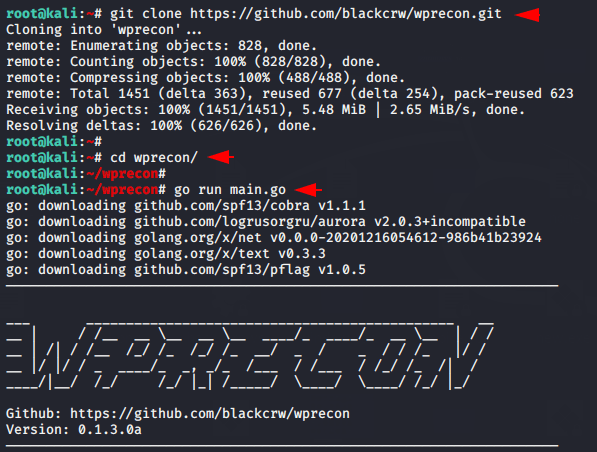
Now we have come here to set up this tool. We execute the git command to download the tool from gitub, go to the directory and boot the tool directly from the go utility.
git clone https://github.com/blackcrw/wprecon.git
cd wprecon/
go run main.go123git clone
https://github.com/blackcrw/wprecon.gitcd wprecon/go run main.go
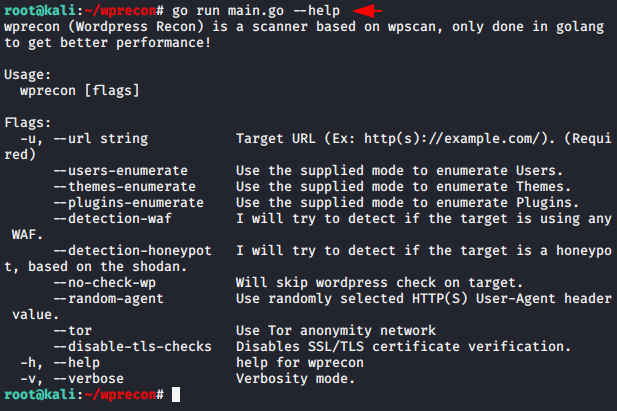
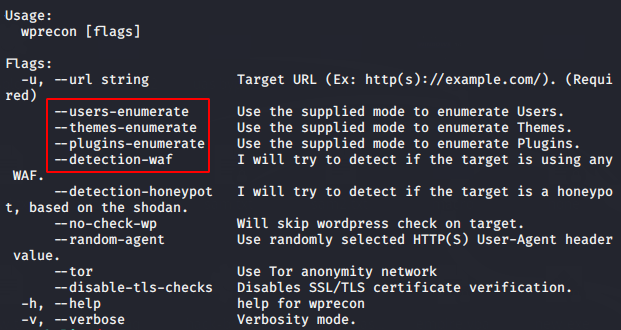
Also, you can identify all the features available in this tool using the help command.
go run main.go --help1go run main.go--help
Enumerate WordPress Users
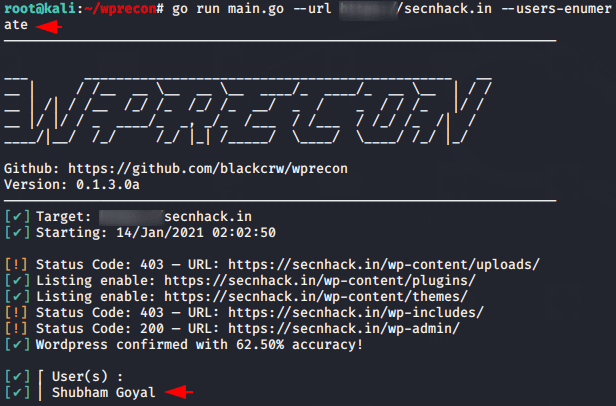
As we told you, the tool is only designed to penetrate WordPress cms, so we have configured a WordPress CMS on our kali linux machine to use this tool. All we have to do is enter the URL of the target and give the parameter we want to get. When we execute the command it dumps all usernames from the target.
Usage
go run main.go --url https://secnhack.in --users-enumerate1go run main.go--url https://secnhack.in --users-enumerate
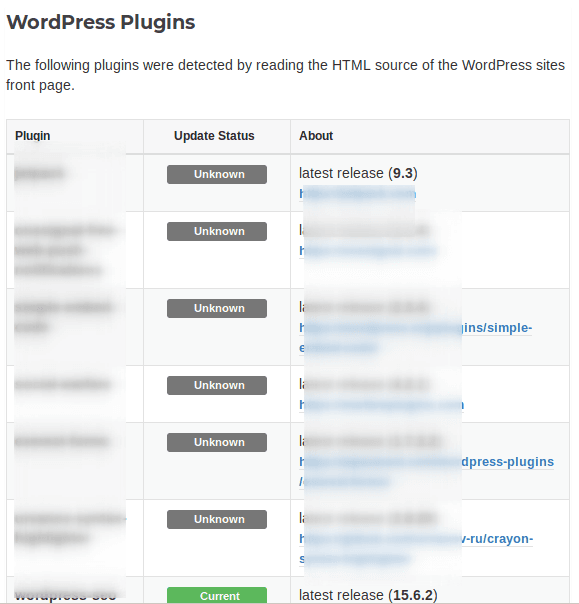
Enumerate WordPress Plugins
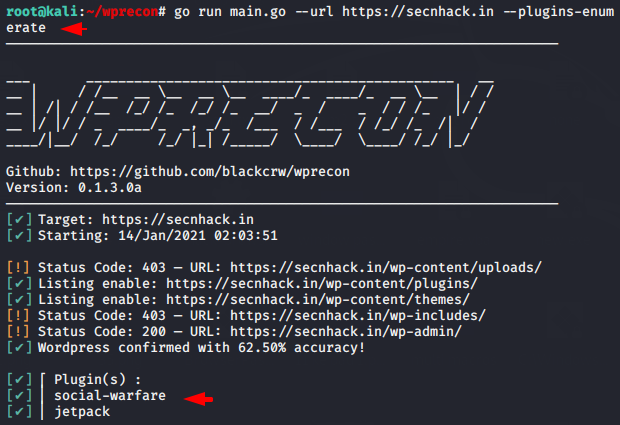
As above, we will try to enumerate the plugins using the following command.
Usage
go run main.go --url https://secnhack.in --plugins-enumerate1go run main.go--url https://secnhack.in --plugins-enumerate
Nice
WPrecon (GUI)
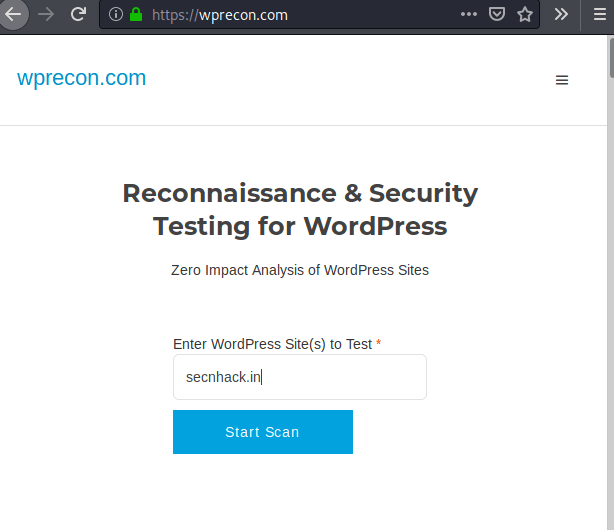
The article is not finished yet because we have a GUI version of this tool if you are not able to operate kali linux.

WordPress Recon and Security Testing | wprecon.com
Online WordPress Testing Tool to discover security related information and configuration issues.
 wprecon.com
wprecon.com
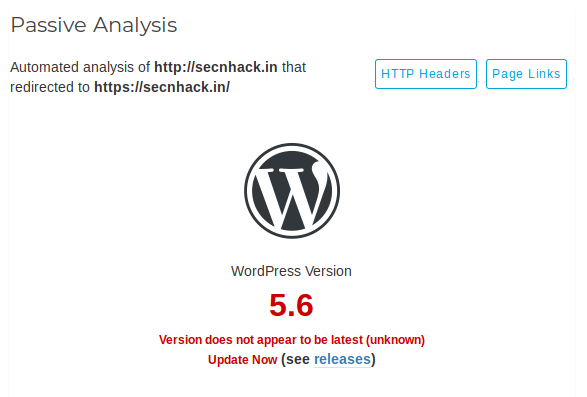
Analysis – Version
All you have to do is give the URL of the target and it will dump all the information just like the command line tool.
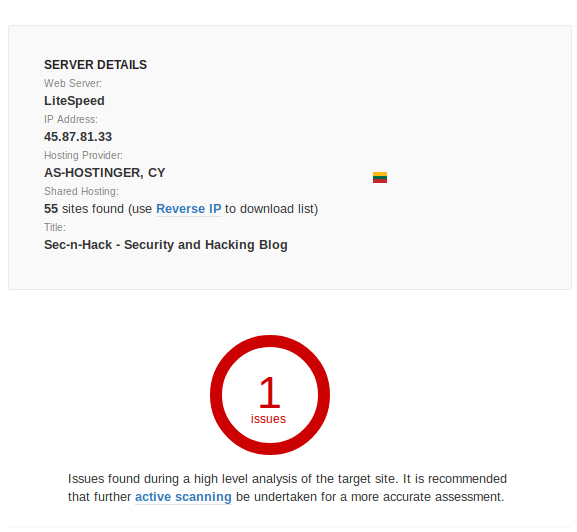
Server Details
You can see the public IP address of the target website along with the hosting provider and server details.
Plugins
One thing we noticed is that the website of this tool is better than the command line utility.