Legendito
Witty Banter Specialist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
100 XP
GERIX WIFI CRACKERis a GUI wireless 802.11 penetration tools which uses the aircrack-ng method behind its point and click method to crack the wifi password.
First of all clone the github repo with command:
git clone https://github.com/J4r3tt/gerix-wifi-cracker-2.git
Now inside the installed directory give the gerix.py file permission to execute with command:
chmod +x gerix.py
and then start the gerix wifi cracker with command:
python gerix.py
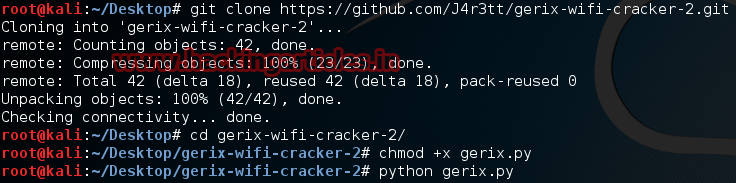
Now a GUI window will appear, click on Reload the Wireless Interfaces and when the wireless interface appears click on it i.e. wlan0 in my case and then click on Enable/Disable Monitor Mode to enable the monitor mode from managed mode.

After enabling the monitor mode the wireless interface name will be changed to wlan0mon and the mode will be monitor .Now for scanning the wireless networks select the monitor mode interface (wlan0mon in my case) and then click on Rescan networks.
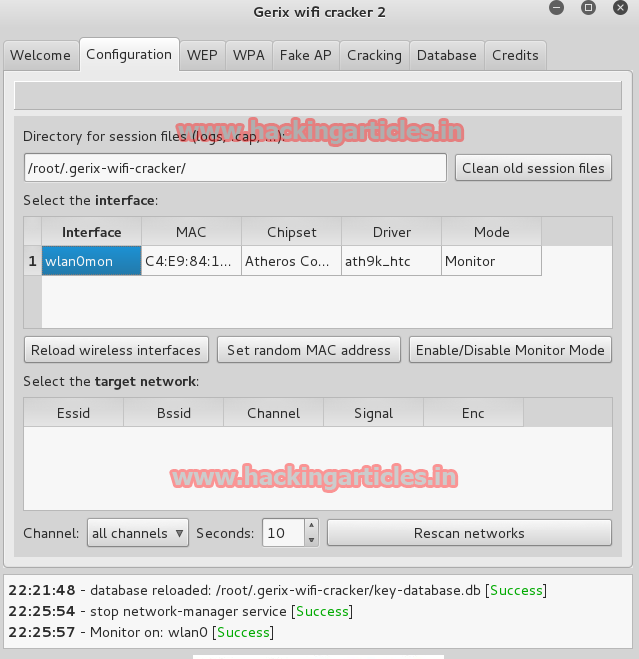
After scanning networks select you target by clicking on it as in my case i have selected tp link and then go to WPA tab (As the target AP is using WPA2 security).
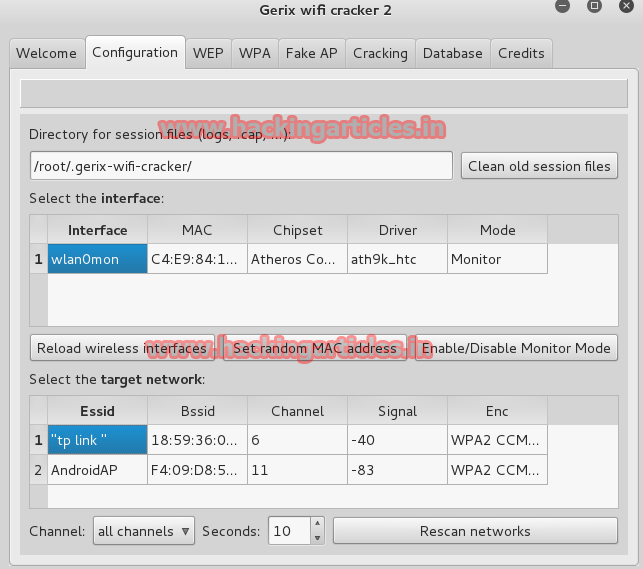
After clicking on WPA tab, go to general functionalities and start sniffing and logging by clicking on it and a terminal window will appear capturing the packets of the target AP.

Now without closing the terminal windows got to WPA attack section and click on Autoload victim clients who will load victim client MAC address to deauthenticate and now click on Client Deauthentication to disconnect the victim so that we can capture the handshake.

Now as you can see WPA handshake is successfully captured and same can be seen in the top right corner of the terminal window. Now close the terminal window.
Now we have to crack the password from the captured file so got to Cracking tab and then to WPA bruteforce cracking section and give the dictionary path in the Add your dictionary field and then click on Aircrack-ng -Crack WPA password .(you can also choose any other method for cracking like pyrite and rainbow tables)

As you can see it has successfully cracked the password.

Author:Himanshu Gupta is an InfoSec Researcher | Technical writer. You can follow him on LinkedIn .
First of all clone the github repo with command:
git clone https://github.com/J4r3tt/gerix-wifi-cracker-2.git
Now inside the installed directory give the gerix.py file permission to execute with command:
chmod +x gerix.py
and then start the gerix wifi cracker with command:
python gerix.py

Now a GUI window will appear, click on Reload the Wireless Interfaces and when the wireless interface appears click on it i.e. wlan0 in my case and then click on Enable/Disable Monitor Mode to enable the monitor mode from managed mode.

After enabling the monitor mode the wireless interface name will be changed to wlan0mon and the mode will be monitor .Now for scanning the wireless networks select the monitor mode interface (wlan0mon in my case) and then click on Rescan networks.

After scanning networks select you target by clicking on it as in my case i have selected tp link and then go to WPA tab (As the target AP is using WPA2 security).

After clicking on WPA tab, go to general functionalities and start sniffing and logging by clicking on it and a terminal window will appear capturing the packets of the target AP.

Now without closing the terminal windows got to WPA attack section and click on Autoload victim clients who will load victim client MAC address to deauthenticate and now click on Client Deauthentication to disconnect the victim so that we can capture the handshake.

Now as you can see WPA handshake is successfully captured and same can be seen in the top right corner of the terminal window. Now close the terminal window.

Now we have to crack the password from the captured file so got to Cracking tab and then to WPA bruteforce cracking section and give the dictionary path in the Add your dictionary field and then click on Aircrack-ng -Crack WPA password .(you can also choose any other method for cracking like pyrite and rainbow tables)

As you can see it has successfully cracked the password.

Author:Himanshu Gupta is an InfoSec Researcher | Technical writer. You can follow him on LinkedIn .