Zayden
Smart Contract Auditor
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Hey Folks, After doing the LAMP setup on ubuntu operation system we will configure vulnerable web application on ubuntu. In this tutorial we are going to configure almost all vulnerable web applications which are designed for penetration testing.
Requirements
Ubuntu
Lets do it
bWAAP
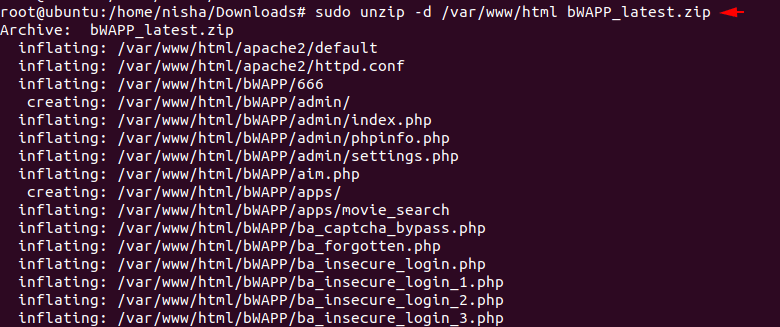
bWAPP is a vulnerable web application which is a free and open source. bWAPP is a PHP application that uses a MySQL database. It can be hosted on Linux/Windows with Apache/IIS and MySQL. prepares one to conduct successful penetration testing and ethical hacking projects. We can download this project from it here.
Installation
I hope you found the link
sudo unzip -d /var/www/html bWAPP_latest.zip1sudo unzip-d/var/www/html bWAPP_latest.zip
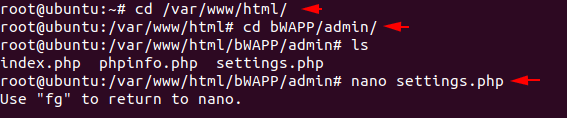
We need to change some configuration on the “setting.php” file and for this we have to reach the destination using the following command.
cd /var/www/html/
cd bWAPP/admin/
ls
nano settings.php1234cd/var/www/html/cd bWAPP/admin/lsnano settings.php
The file will look like this, but we have to change the username and password of the MySQL database that was created on the LAMP setup article.
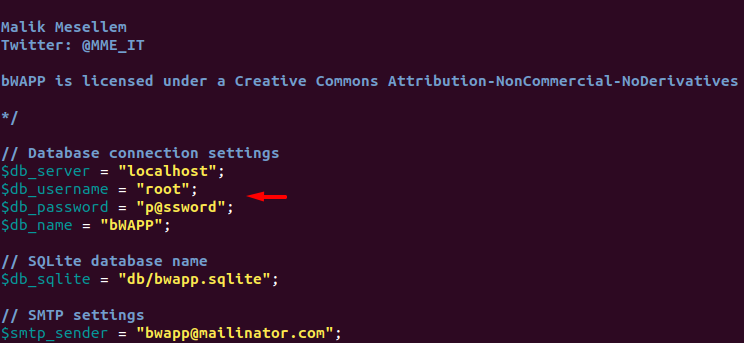
In our case shubham is the user and 123 is the password of the MySQL database. After entering the correct credentials just save the file and exit it.
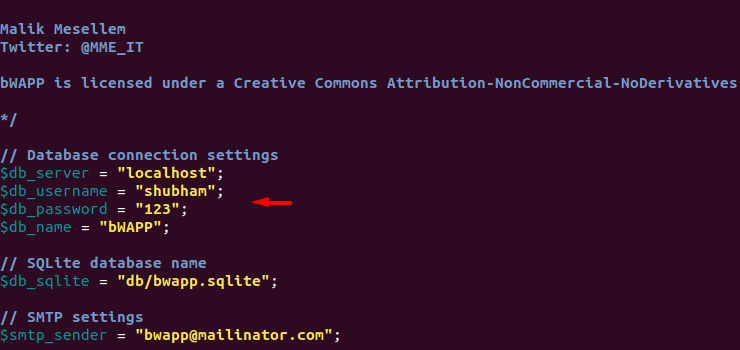
Thats it
Loading…
localhost
Loading…
localhost
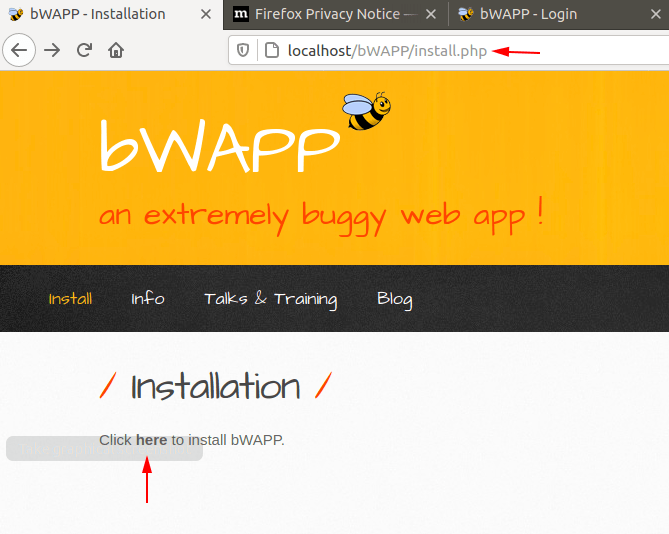
We will redirects to the login page and here we will use the”bee” and “bug” credentials to login into the application.

Great

DVWA
DVWA is an vulnerable web application which coded in PHP/MYSQL. Seriously it is too vulnerable. With the help of this application ethical hackers can test their skills and run this tools in a legal environment. The aim of DVWA is to practice most common web vulnerability, which contains different types of level.
Installation
First we need to download this vulnerable web application from the github page by using the git command. After installed we will going into the configuration directory of the web application and rename the “config.inc.php.dist” file. After rename the file we will open the file through nano command and change some configurations.
git clone https://github.com/ethicalhack3r/DVWA
cd DVWA/config/
ls
mv config.inc.php.dist config.inc.php
nano config.inc.php12345git clone
https://github.com/ethicalhack3r/DVWAcd DVWA/config/lsmv config.inc.php.dist config.inc.phpnano config.inc.php
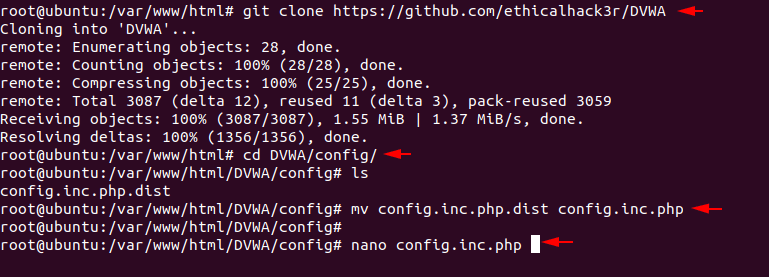
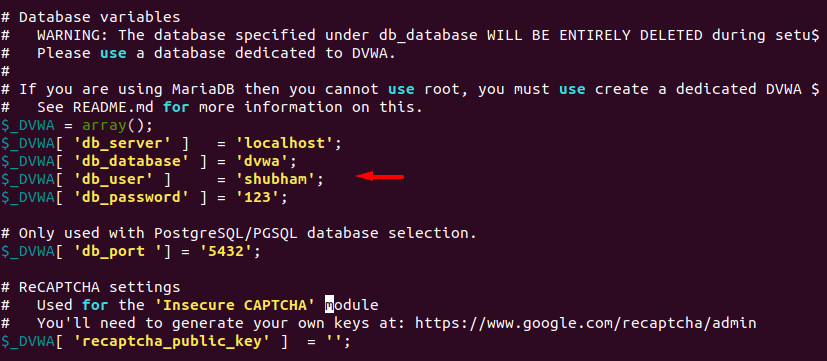
Here we will also add the username and password of our MySQL database.
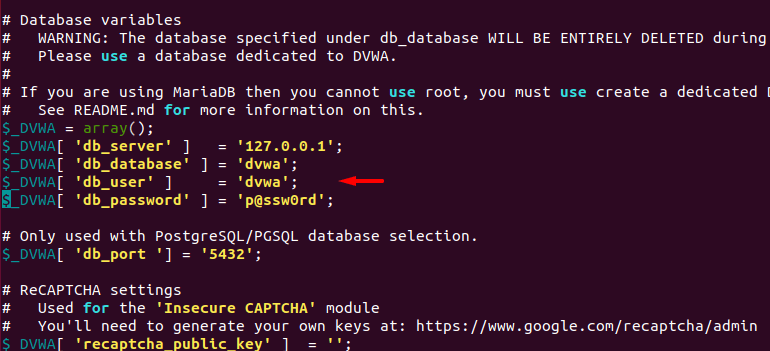
You can see what changes we have made and similarly you can change according to yourself.
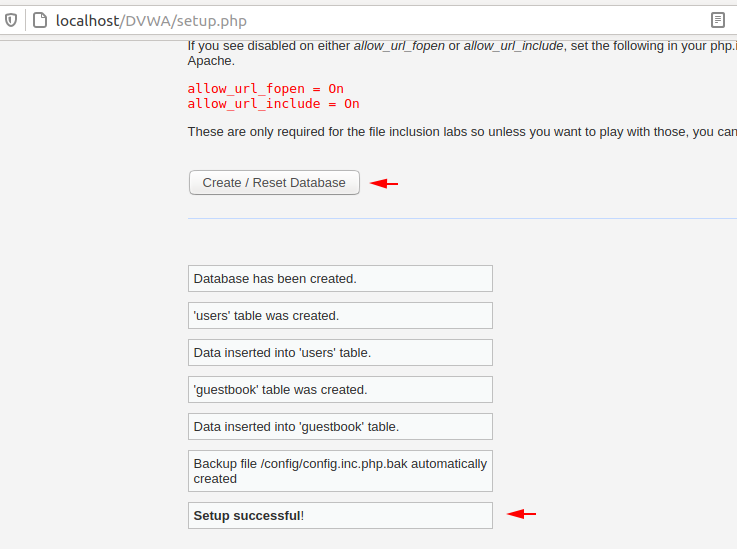
After doing all this we will going to the following location and click on “create /reset database” option.
Loading…
localhost
Loading…
localhost
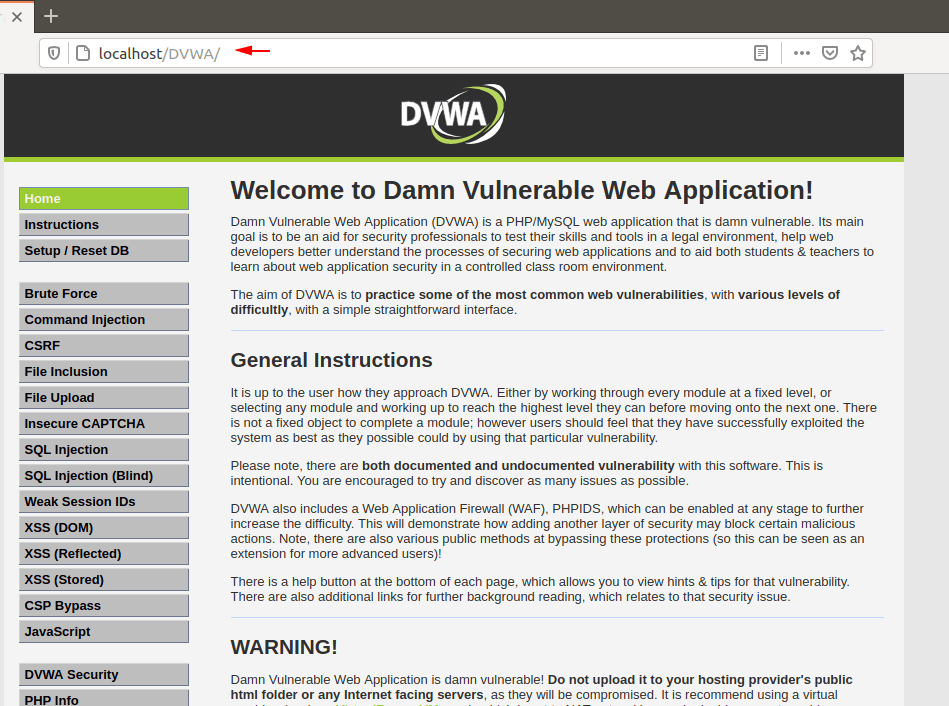
That’s it ! Click on the login button and enter “admin” in the username and “password” in the password.
Mutillidae
Mutillidae is a another pen source web application provided to perform pen-test and hack a web application. Mutillidae can be installed on Linux, Windows XP, and Windows 7 using XAMMP making It easy to install, only we need to configure the linux, apache, mysql and php on web server.
Installation
This project is available on github hence we can download it by using the git command on our terminal. After installation we need to go into the “include” directory of this tool which is inside the “mutilidae” directory. The directory contains the configuration file which we will open.
git clone https://github.com/webpwnized/mutillidae
cd mutillidae
cd includes
ls
nano database-config.inc12345git clone
https://github.com/webpwnized/mutillidaecd mutillidaecd includeslsnano database-config.inc
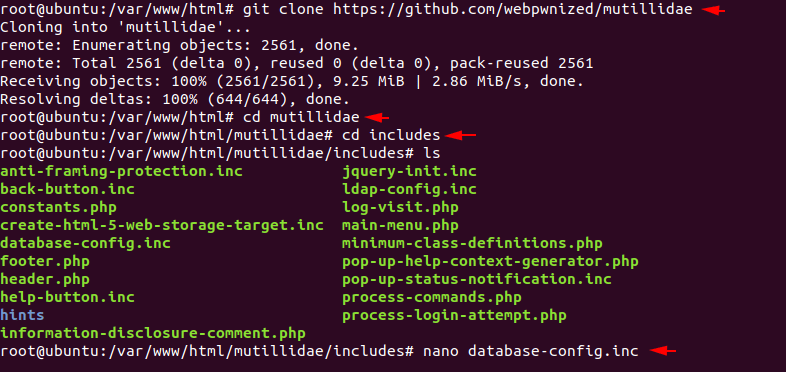
After opening the file the first impression will look like this but we will change the username and password of mysql server according to yourself.
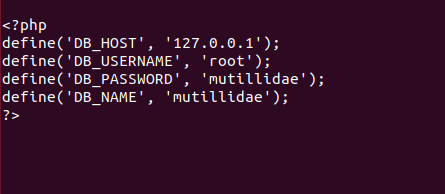
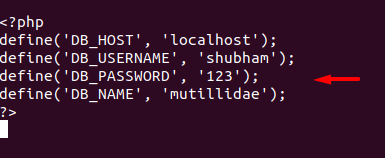
After manipulating the configuration we will save and exit it.
This is how the interface looks when we browse the following location In which we have to click on the “opt-out” option.
Loading…
localhost
Loading…
localhost
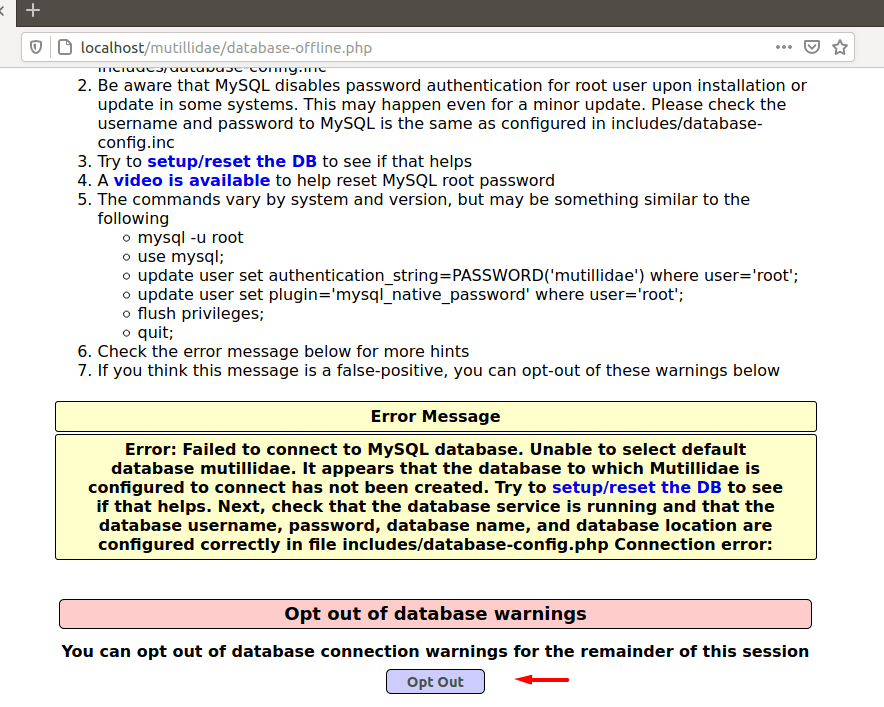
Now we will reset the database which is required to host the web application.
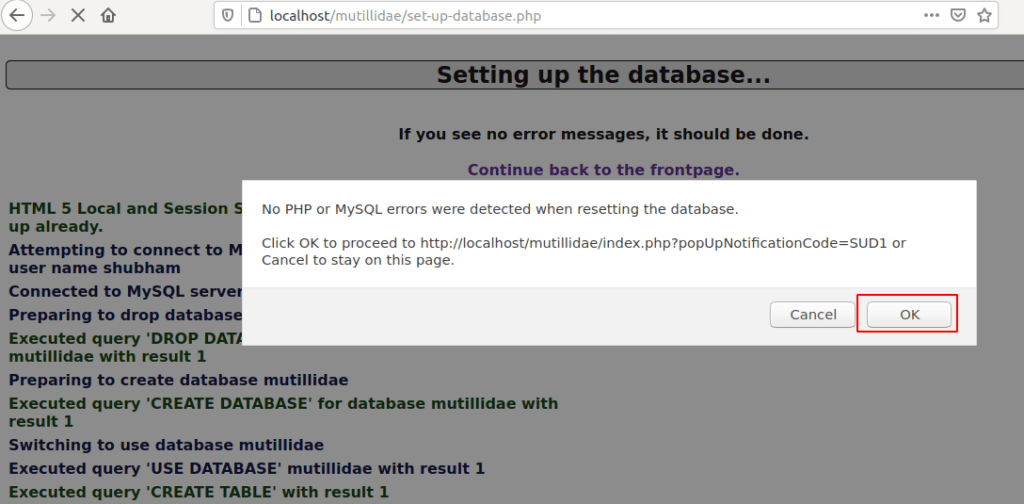
Great ! after click on ok button we will get the complete access of the web application where we can start our penetration testing.
XVWA
XVWA is an another vulnerable web application written in PHP/MySQL that helps security enthusiasts to learn application security. XVWA is designed to understand following security issues and with the help of this vulnerable application we can enhance our penetration testing skills that would be help in our web security carrier.
Installation
Installation is quite simple, we will go to the github page from here and copy the entire code.
Loading…
raw.githubusercontent.com
Loading…
raw.githubusercontent.com
Execute the following command and paste the code below the file.
cat > xvwa.sh1cat>xvwa.sh
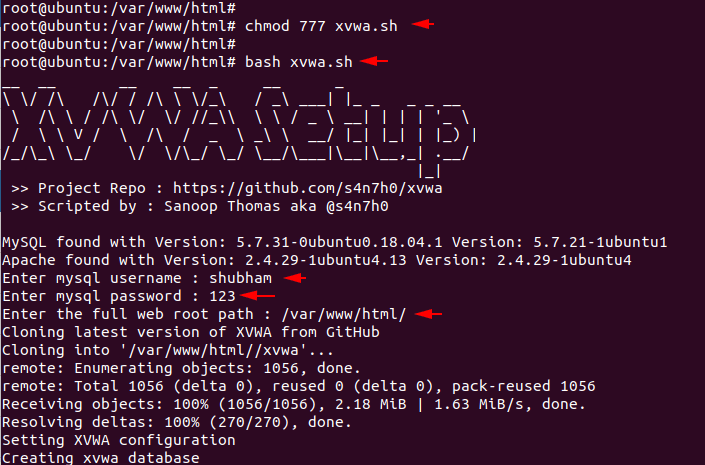
Give some chmod permission by using the given command.
chmod 777 xvwa.sh
bash xvwa.sh12chmod777xvwa.shbash xvwa.sh
Now we will execute this tool by using the bash command and it will automatically setup the web application. But you also have to provide mysql db information.
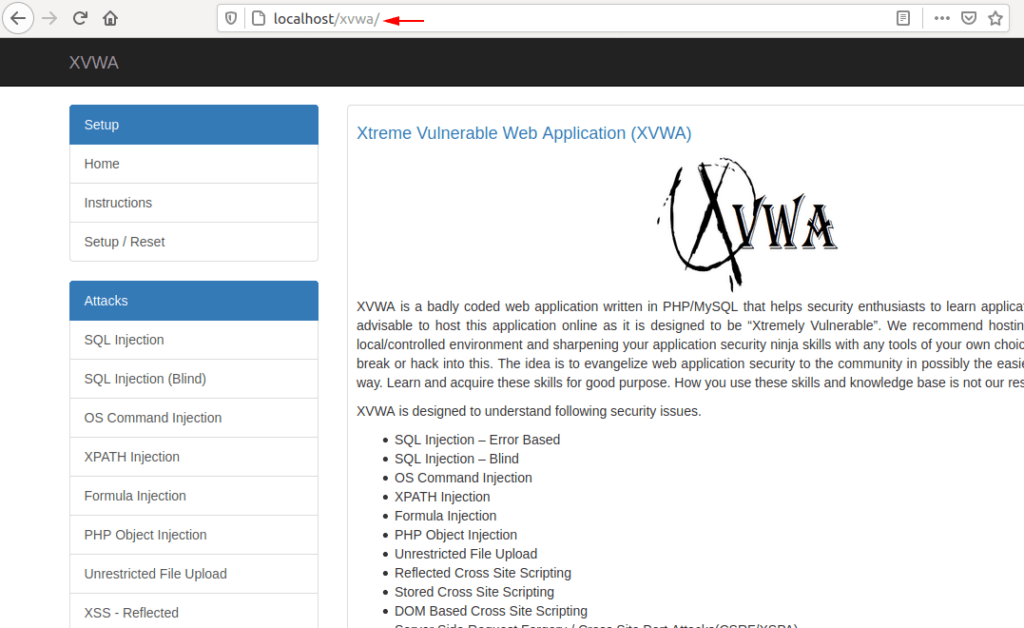
Here you can see that we are able to access web application without getting much effort.
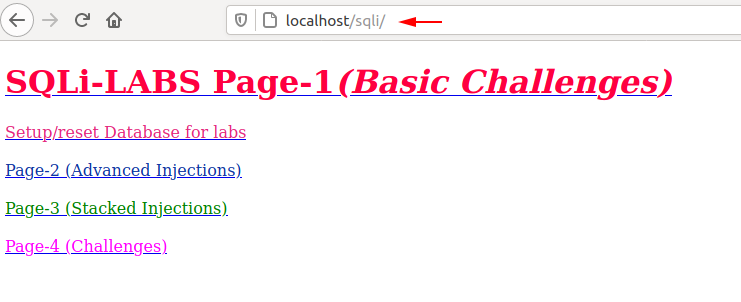
SQLi_Edited_Version – Labs
SQLI-LABS is a platform to learn SQLI Following labs are covered for GET and POST scenarios. It is an open source that is hosted on github page and especially designed to learn sql injection. It contains multiple chapters and lesson in which you will learn different ways to exploit the sql injection vulnerability.
Installation
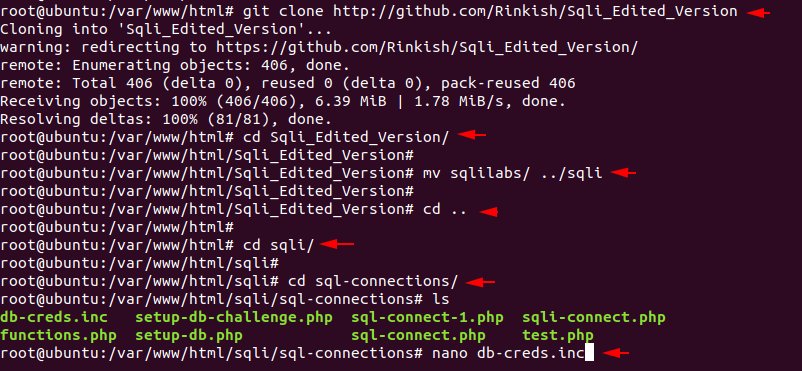
First download it from the github page. The directory will be automatically created in the name of the tool. After moving to the directory we will move the contents of “sqlilab” to the previous “sqli” directory. After coming back again we will go to sql and sql-connection directory. In the last just open the configuration file.
git clone http://github.com/Rinkish/Sqli_Edited_Version
mv sqlilabs/ ../sqli
cd ..
cd sqli
cd sql-connections/
ls
nano db-creds.inc1234567git clone
http://github.com/Rinkish/Sqli_Edited_Versionmv sqlilabs/../sqlicd..cd sqlicd sql-connections/lsnano db-creds.inc
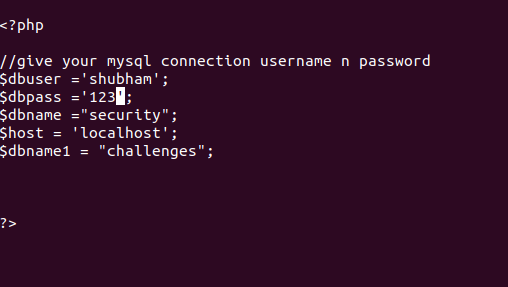
In this file we will change some configuration which is required to everyone. After changing the username and password of the mysql database we will save and exit it.
Browse the following location and you will find your destination i.e. the web application is successfully configured.