mic141414
Patch Tester
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

Hey Folks, In this tutorial we are going to discuss an github tool called “URLBuster”. The tool is similar to dirb or gobuster, but has a lot of manipulation options and is designed for web directory fuzzer to locate existing and / or hidden files or directories.
Features
- Proxy support
- Cookie support
- Basic Auth
- Digest Auth
- Retries (for slow servers)
- Persistent and non-persistent HTTP connection
- Request methods: GET, POST, PUT, DELETE, PATCH, HEAD, OPTIONS
- Custom HTTP header
- Mutate POST, PUT and PATCH payloads
- Mutate with different request methods
- Mutate with different HTTP headers
- Mutate with different file extensions
- Mutate with and without trailing slashes
- Enumerate GET parameter value
Lets take a look
Installation
Installation is not difficult, but we should have a pip tool in our system from which we will download it. If you do not have it, you can use the following command and download the pip tool.
apt-get install python-pip1apt-get install python-pip
Now the time to install this tool and through the below given command we will easily configure it on our system.
pip install urlbuster1pip install urlbuster
All has been done and now we will execute the help command which will give us all the usage details of this tool.
urlbuster --help1urlbuster--help
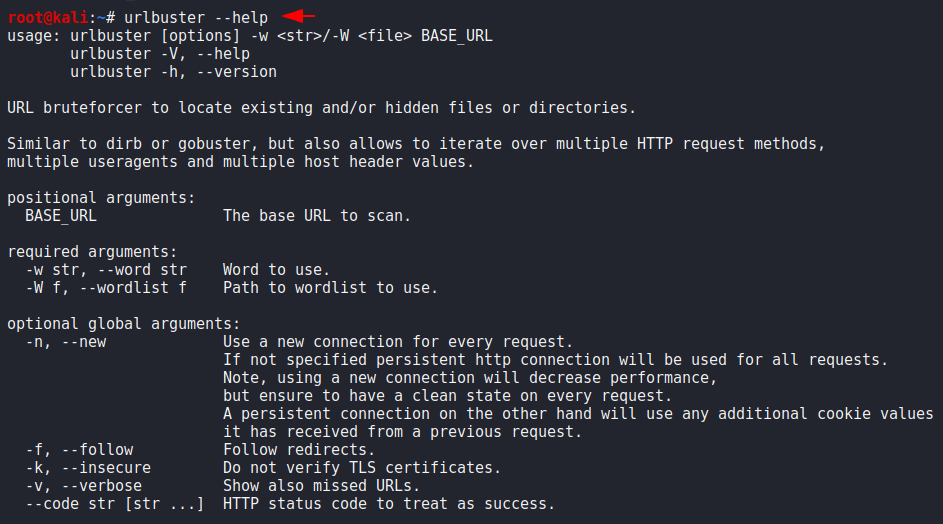
You can see the basic usage of this tool through giving the image below but we will take an example.
Fuzzing with Word list
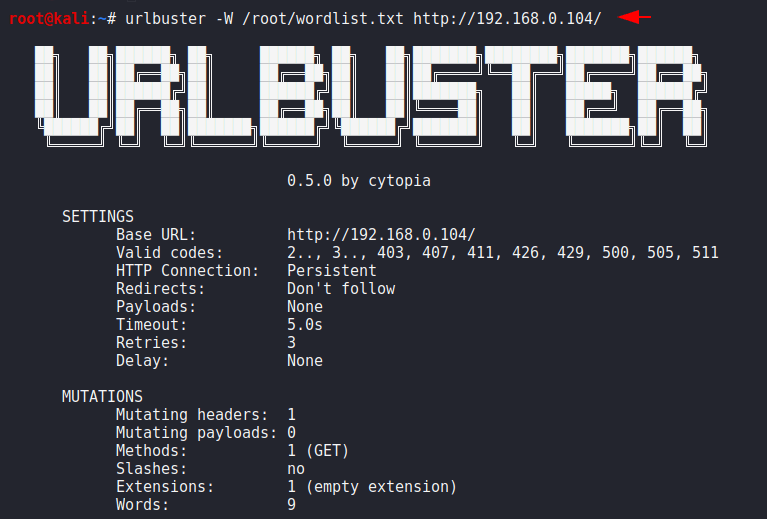
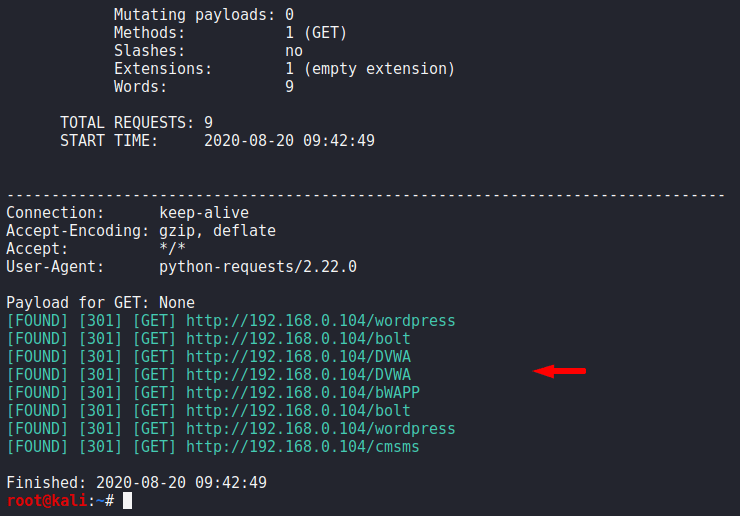
In this tool we have to give the wordlist otherwise it will not work so you can see the code given below and manipulate the target and the wordlist according to your requirement. After executing the command you will see all the settings that it will use during fuzzing.
Usage
urlbuster -W /root/wordlist.txt http://192.168.0.104/1urlbuster-W/root/wordlist.txt http://192.168.0.104/
Nice
No TLS Verification
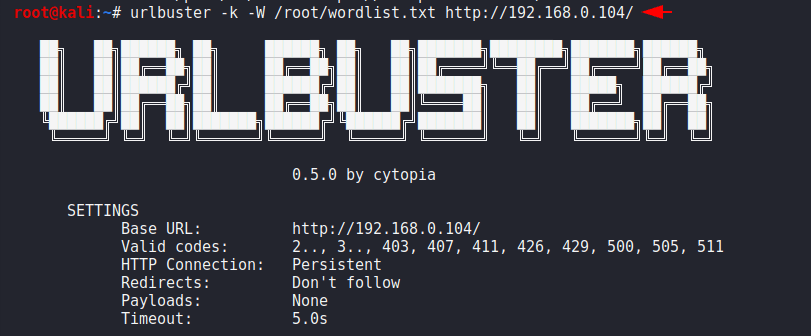
When we visit any website then first TLS handshake processed and if the handshakes succeed then client and server both can communicate and transfer the data to each other. But through this facility we can get the information anonymously without TLS verification.
urlbuster -k -W /root/wordlist.txt http://192.168.0.104/1urlbuster-k-W/root/wordlist.txt http://192.168.0.104/
New Connection
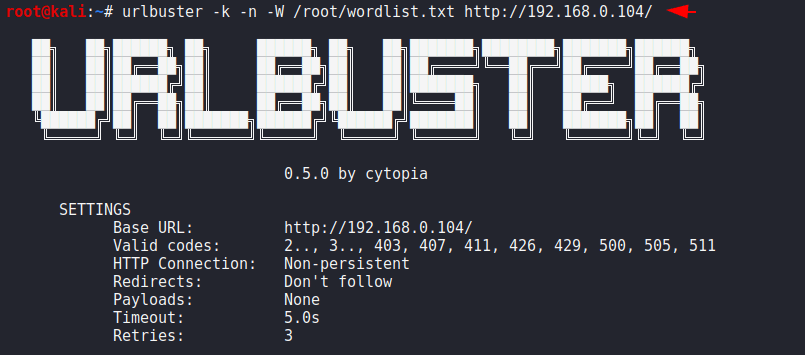
This feature will help to anonymous itself becuase new connection for every request and if not specified persistent http connection will be used for all requests.
urlbuster -k -n -W /root/wordlist.txt http://192.168.0.104/1urlbuster-k-n-W/root/wordlist.txt http://192.168.0.104/
Verbose
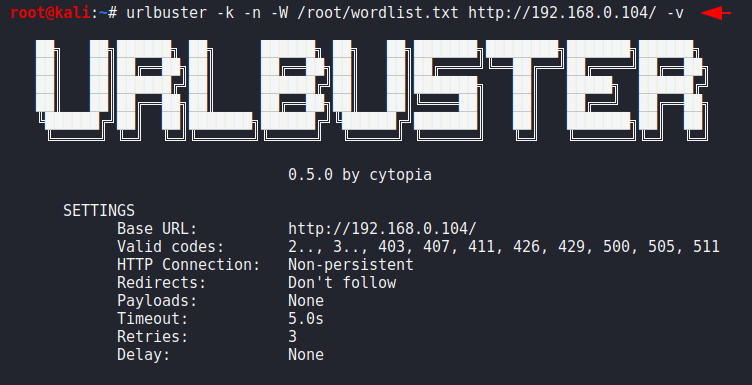
This features will give us the brief details such as : missed URLs, redirection, response code etc. Just we will add “-v” parameter in our search.
urlbuster -k -n -W /root/wordlist.txt http://192.168.0.104/ -v1urlbuster-k-n-W/root/wordlist.txt http://192.168.0.104/ -v
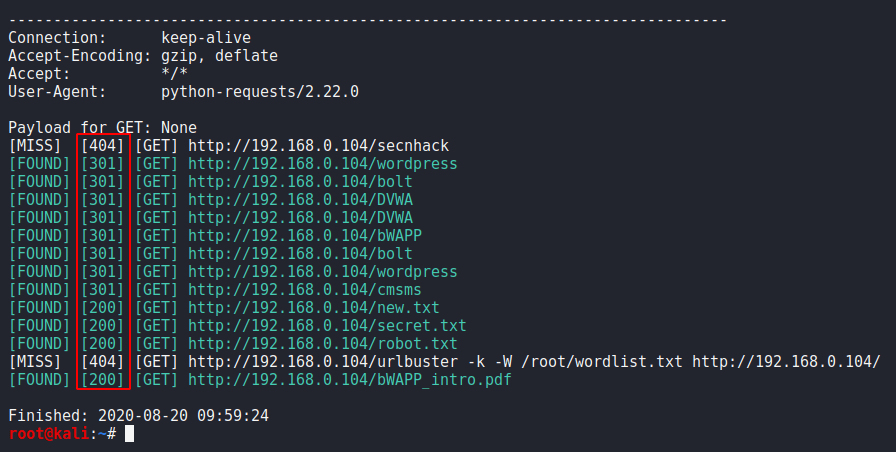
After adding this one we have got status code of the all HTTP requests.
HTTP status code
HTTP status code to treat as success and if we only want to see the specific HTTP response or status code then we go with it. We can add more response code through giving the space.
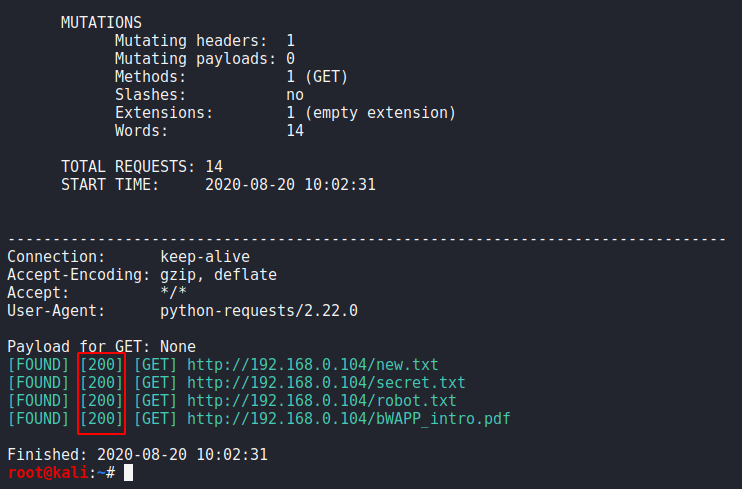
urlbuster -W /root/wordlist.txt http://192.168.0.104/ --code 2001urlbuster-W/root/wordlist.txt http://192.168.0.104/ --code 200
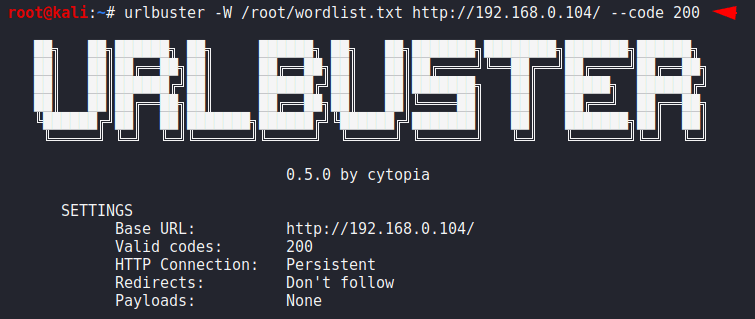
Here you can see that we got only 200 HTTP response results.
Change Header
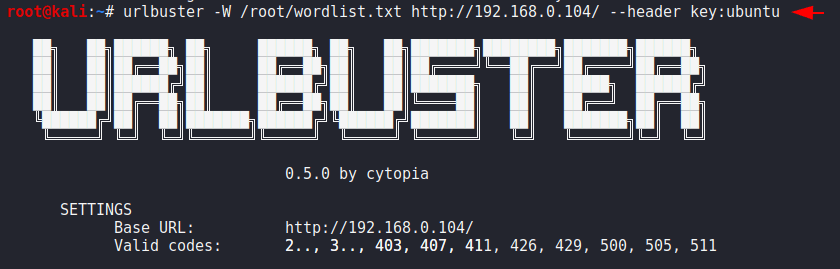
To keep anonymous yourself we can set custom http header string which will be send to the server and the victim will not identify the exact details about the target.
urlbuster -W /root/wordlist.txt http://192.168.0.104/ --header key:ubuntu1urlbuster-W/root/wordlist.txt http://192.168.0.104/ --header key:ubuntu
Method
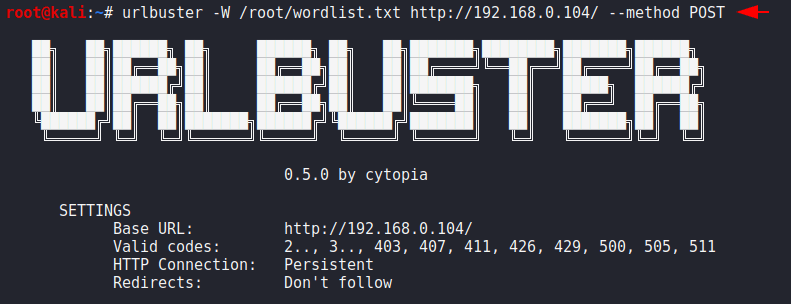
Sometimes we need to send the request to the server in a different way which depends on the situation, we can use this feature in it.
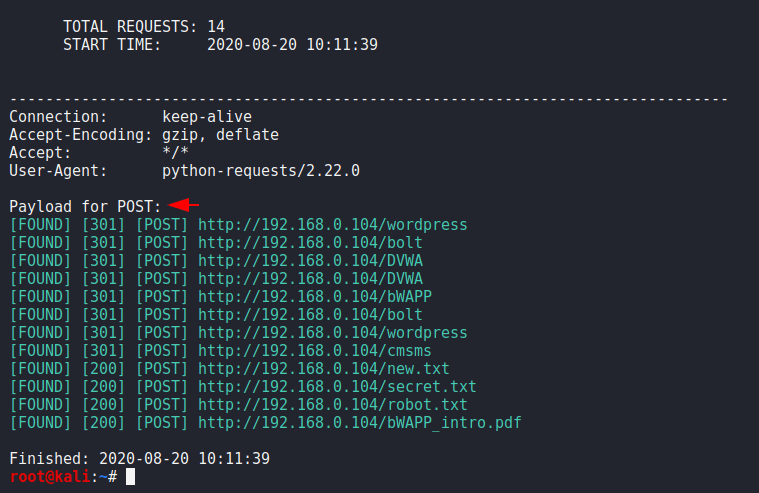
urlbuster -W /root/wordlist.txt http://192.168.0.104/ --method POST1urlbuster-W/root/wordlist.txt http://192.168.0.104/ --method POST
Done