MrWafflez
Follower Insights Pro
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP
Hey Folks, In our previous article we revealed a “Remote Access Trojan” application named “WH-RAT” but in this tutorial we are going to add some more new and working trojans to our list of hacking tools. So the “RAT” tools that we’re going to reveal today are listed below.
List of Tools
- Njrat Danger Edition
- Quasar Gold Rat
- Revenge Rat
- WARZONE Rat
Let’s take a look
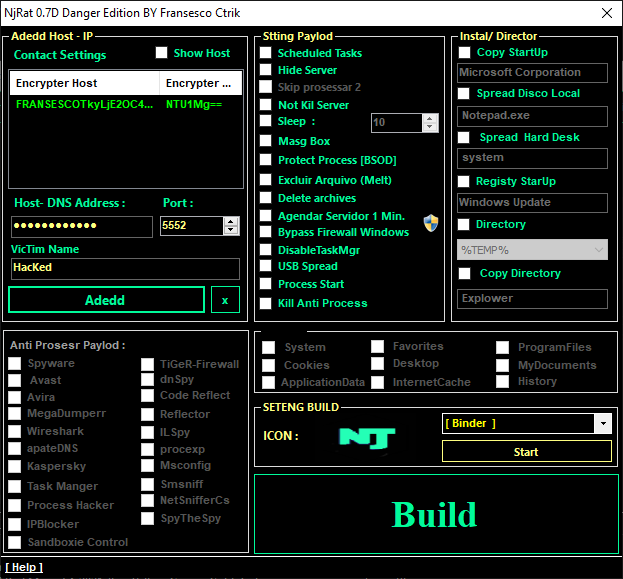
Njrat Danger Edition RAT
njRAT’, also known as ‘Bladabindi’ or ‘Njw0rm’, is a well established and prevalent remote access trojan (RAT) threat that was initially created by a cyber criminal threat group. Now it is available for free that anyone can download and use it. Let’s have a little demonstration of this tool. You can download it from here. After downloading it, open this application and it will automatically ask you to setup the listener. You can change the port number or leave it all up to you. Just click on “start” button.

Hmm

Ok
Great

Nice

Quasar Golden Edition Rat
Quasar RAT is a malware family written in . NET which is used by a variety of attackers. The malware is fully functional and open source. The Quasar tool allows users to remotely control other computers over a network. First download it from here. After clicking on the executable file it will open and the interface will look like the image below. To create a malicious payload, you need to click on “builder” option.

Here you just have to enter your host address and click on the “Build Client” button.

Ready

Done

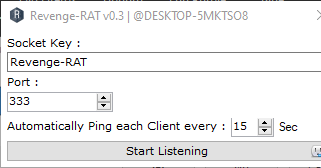
Revenge Rat
Revenge RAT is an simple and open source tool that automatically gathers system information. It is also a type of trojan that cyber criminals often use these tools for malicious purposes. You can download it freely from here. When you open it, it will ask you to setup the listener. You can change the port number as per your choice or leave it and click on start.
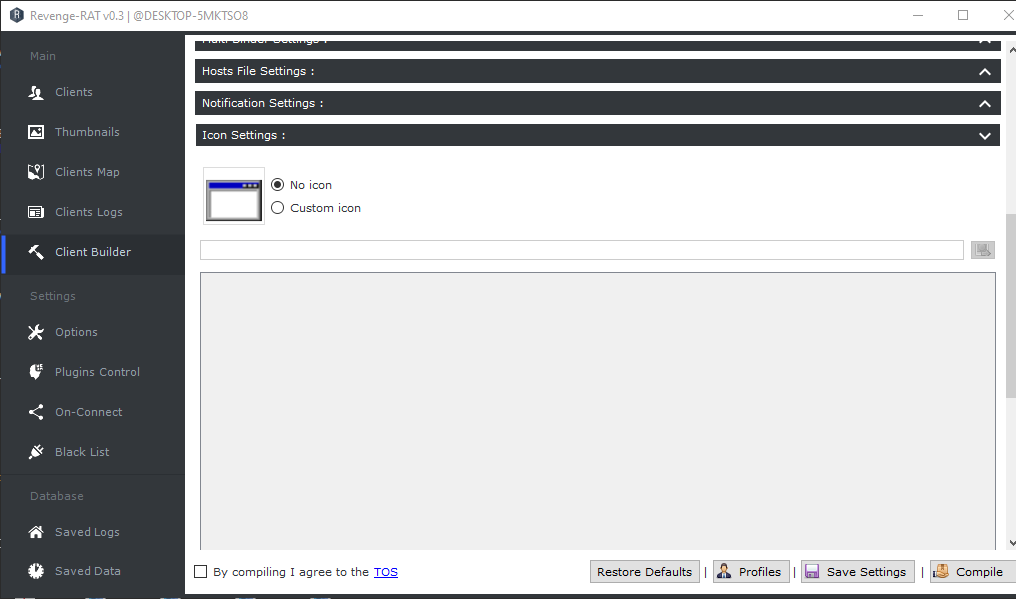
After that go directly to the client builder option, go to network settings and add host details.

It also has another great feature to add any icon to the payload.
Ready

Amazing

WARZONE RAT
Warzone commercial RAT is for sale and has a monthly price structure for access to the license to operate it but warzone rat is now considered publicly available. After opening it, the first thing you need to do is to create client service. Just click on the client builder option, enter your host address and any random string, fill in the empty box and click on build.
Loading…
github.com
Loading…
github.com

Alright

WOW
