CKHypers
Social Media Strategist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
In this article, we will provide the write-up of the Try Hack Me Room: The Server from hell. This is a write-up about a medium level boot to root Linux box which is available for free on TryHackMe for penetration testing practice. Let’s get started and learn how to break it down successfully.
Level: Medium
Penetration Testing Methodology
Reconnaissance
Enumeration
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
Using nmap, we have performed reconnaissance, where we found many open ports available.
Looking at the room description, there was an interesting thing that we discovered. The number 12345 is present in every port’s banner. So thinking that as a hint, I connected to that port.

Enumeration
Using Netcat we will now connect to port 12345, where we found another hint which leads us to NFS port.

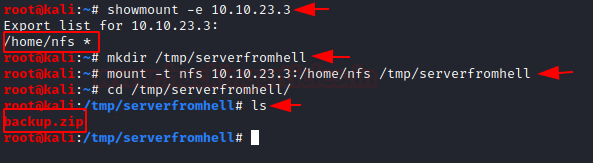
From the hint that we got earlier, we found out /home/nfs directory using showmount command.
Now simply mount that share
After mounting we have found backup.zip file which is password protected.
Exploiting
Now we use fcrackzip to bruteforce the zip file where we find the password.

Let’s unzip the file. On unzipping it shows home/hades/.ssh directory.

We go to home/hades/.ssh/ where we have found one ssh private key, flag.txt and a hint.txt. When we open hint.txt we get a clue which says 2500-4500.

When we conducted a nmap scan, from 2500-4500 we found that ssh is running on port 3333.

Now we connect to ssh port using a private key that we found earlier, Now we have found a shell, which is an interactive ruby shell. So in order to get a /bin/bash shell run
Here we have found user.txt

Privilege Escalation
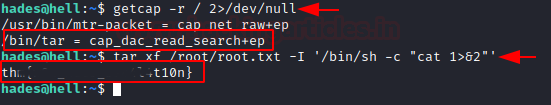
Now we have got a hint about getcap which tells us which of the binary has the capability to get access to everything on the system.
Now with the help of GTFO bin, we have made use of tar capability to find root flag.
Author: Shrishty Dayal is a Cyber Security Enthusiast who loves to explore and gain more knowledge in the cybersecurity Domain Contact Linkedin
Level: Medium
Penetration Testing Methodology
Reconnaissance
- Nmap
Enumeration
- netcat
- Mounting NFS directory
Exploiting
- Cracking zipfile using fcrackzip
- Connecting to ssh port
- Interacting with irb shell
Privilege Escalation
- getcap to checkout file capabilities
- Capture the flag
Walkthrough
Reconnaissance
Using nmap, we have performed reconnaissance, where we found many open ports available.
Looking at the room description, there was an interesting thing that we discovered. The number 12345 is present in every port’s banner. So thinking that as a hint, I connected to that port.

Enumeration
Using Netcat we will now connect to port 12345, where we found another hint which leads us to NFS port.
Code:
nc 10.10.150.211 12345
From the hint that we got earlier, we found out /home/nfs directory using showmount command.
Now simply mount that share
Code:
mount -t nfs 10.10.23.3:/home/nfs /tmp/serverfromhellAfter mounting we have found backup.zip file which is password protected.

Exploiting
Now we use fcrackzip to bruteforce the zip file where we find the password.
Code:
fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt backup.zip
Let’s unzip the file. On unzipping it shows home/hades/.ssh directory.

We go to home/hades/.ssh/ where we have found one ssh private key, flag.txt and a hint.txt. When we open hint.txt we get a clue which says 2500-4500.

When we conducted a nmap scan, from 2500-4500 we found that ssh is running on port 3333.

Now we connect to ssh port using a private key that we found earlier, Now we have found a shell, which is an interactive ruby shell. So in order to get a /bin/bash shell run
Code:
ssh -i id_rsa [email protected] -p 3333
system "/bin/bash"Here we have found user.txt

Privilege Escalation
Now we have got a hint about getcap which tells us which of the binary has the capability to get access to everything on the system.
Now with the help of GTFO bin, we have made use of tar capability to find root flag.
Code:
getcap -r / 2>/dev/null
tar xf /root/root.txt -I '/bin/sh -c "cat 1>&2"'
Author: Shrishty Dayal is a Cyber Security Enthusiast who loves to explore and gain more knowledge in the cybersecurity Domain Contact Linkedin