Xancasp
AI Systems Architect
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we are going to solve another boot2root challenge called “Sunset: Midnight”. It’s available at VulnHub for penetration testing and you can download it from here.The credit for making this lab goes to whitecr0wz. Let’s get started and learn how to successfully break it down.
Level: Intermediate
Penetration Testing Methodology
Reconnaissance
Enumeration
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
We are looking for the machine with netdiscover

So, let’s start by running map to all ports with OS detection, software versions, scripts and traceroute.

We add the IP address and the “sunset-midnight” host to our “/etc/hosts” as indicated by the creator of the machine in the description.

Enumeration
We access the web service and find a site developed with the CMS WordPress.

We also check that the authentication panel is still on the same path.

Exploiting
We attacked the MySQL service with hydra and the rockyou dictionary. We will get the credentials to access the database.

We created a hash in md5 of the password “123456” (we will use it below).
We connect to the database with the obtained credentials, select the database and consult the table of registered users. We don’t know the password, but it’s not a problem, we’ll change it directly indicating our md5 hash (remember that it corresponds to the password 123456).
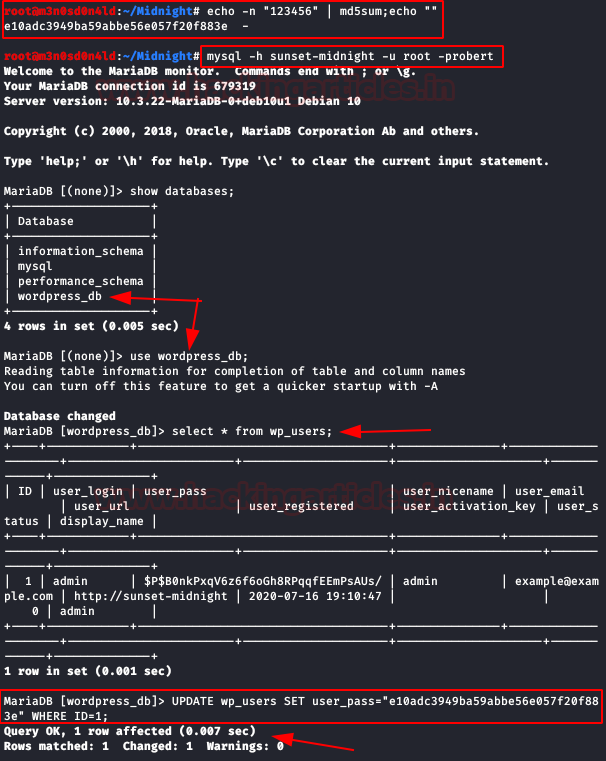
Now we have access to the WordPress administration panel. Now we’ll change the “header.php” file (or another file you can call) and insert the web shell’s PHP code (I used PentestMonkey).

Now we will put a netcat to listen to port 4444 and we will execute any section of the web.If all goes well, we’ll get a shell on our Kali.

We run these two sequences to get an interactive shell. Later, we will read the file “wp-config.php” and it shows us a password in md5.

Privilege Escalation (user “jose”)
We use the password to authenticate ourselves as the user “jose”.

Privilege Escalation (root)
We check which files we have access to and the binary “/usr/bin/status” catches our attention.
We use strings on it, we see that internally it calls the binary “service” but without indicating the path of origin, this would allow us to create a malicious “service” file and thus be able to change our PATH to execute it.
So let’s put it into practice, we create a file in the “tmp” folder with the name “service”, we introduce the sequence “/bin/sh”, we execute the binary of “/usr/bin/status” and we get a shell as root.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.
Level: Intermediate
Penetration Testing Methodology
Reconnaissance
- Netdiscover
- Nmap
Enumeration
- Hydra bruteforce MySQL service
Exploiting
- WordPress administrator’s password change
- Modification of code to build a webshell
Privilege Escalation
- Misuse of recycled passwords
- Binary abuse without fixed load path
- Capture the flag
Walkthrough
Reconnaissance
We are looking for the machine with netdiscover
Code:
netdiscover -i ethX
So, let’s start by running map to all ports with OS detection, software versions, scripts and traceroute.
Code:
nmap -A –p- 192.168.10.178
We add the IP address and the “sunset-midnight” host to our “/etc/hosts” as indicated by the creator of the machine in the description.

Enumeration
We access the web service and find a site developed with the CMS WordPress.

We also check that the authentication panel is still on the same path.

Exploiting
We attacked the MySQL service with hydra and the rockyou dictionary. We will get the credentials to access the database.

We created a hash in md5 of the password “123456” (we will use it below).
We connect to the database with the obtained credentials, select the database and consult the table of registered users. We don’t know the password, but it’s not a problem, we’ll change it directly indicating our md5 hash (remember that it corresponds to the password 123456).

Now we have access to the WordPress administration panel. Now we’ll change the “header.php” file (or another file you can call) and insert the web shell’s PHP code (I used PentestMonkey).

Now we will put a netcat to listen to port 4444 and we will execute any section of the web.If all goes well, we’ll get a shell on our Kali.

We run these two sequences to get an interactive shell. Later, we will read the file “wp-config.php” and it shows us a password in md5.

Privilege Escalation (user “jose”)
We use the password to authenticate ourselves as the user “jose”.

Privilege Escalation (root)
We check which files we have access to and the binary “/usr/bin/status” catches our attention.
We use strings on it, we see that internally it calls the binary “service” but without indicating the path of origin, this would allow us to create a malicious “service” file and thus be able to change our PATH to execute it.
So let’s put it into practice, we create a file in the “tmp” folder with the name “service”, we introduce the sequence “/bin/sh”, we execute the binary of “/usr/bin/status” and we get a shell as root.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.