.hiTit
Code Documentation Specialist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

Hey Folks, today we are back with interesting tools for bug bounty hunters and usually every bug bounty hunters are looking for a tool that can helps to find bugs and give reward them in few seconds and the tool we’re going to talk about, he is completely right according to the requirements. Basically the tools first find the subdomain and then find the subdomain which shows “404” error from those list. Looks good so let’s test it.
Let’s test it
Installation
You must have “python3” and “pip” dependencies already installed in your system in order to install this tool. Let’s go ahead and first download this github project via git clone command, go to the directory of this tool and execute python command.
git clone https://github.com/m8r0wn/subscraper
cd subscraper
python3 setup.py install123git clone
https://github.com/m8r0wn/subscrapercd subscraperpython3 setup.py install

Good
pip install -r requirements.txt1pip install-rrequirements.txt

Done
subscraper -h1subscraper-h

Dump Subdomain
Let’s take an example and try to get all the subdomains associated with this domain. So all you have to do is give any domain name here and it will identify all the subdomains.
subscraper vulnweb.com1subscraper vulnweb.com

Hmm

Custom Wordlist
If you want to use own wordlist than can give path by using “-w” param.
subscraper vulnweb.com -w /usr/share/wordlists/dirb/common.txt1subscraper vulnweb.com-w/usr/share/wordlists/dirb/common.txt

Active Subdomain
There are three options are available but all these options are available for different purposes so we will choose the second option to grab the live subdomain.
subscraper -e 2 vulnweb.com1subscraper-e2vulnweb.com

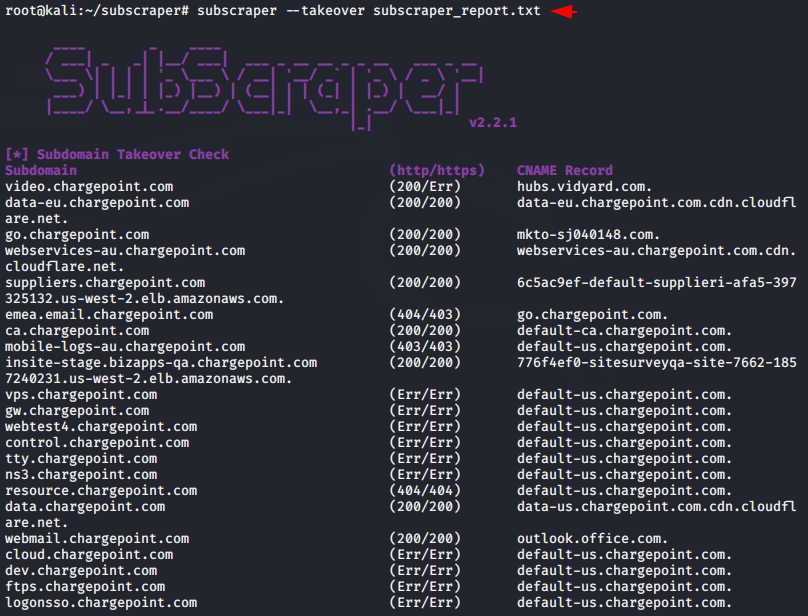
Subdomain Takeover
Now it’s main feature of this tool that become it different from other tool. So whenever we get a “404” response on a subdomain it may be possible that the pointing service is down or the owner has stopped to pick up the service that is pointing at the subdomain, but with the help of other tools we need to do more effort to find the subdomain which is giving “404” error and for that we open each domain one by one but it gives us results along with HTTP response so that it easier to find subdomain vulnerabilities in any web application. All we have to do is pick up the path of the result and append with the command and execute it and the final results will be displayed on the terminal.
subscraper --takeover subscraper_report.txt1subscraper--takeover subscraper_report.txt