JasonB0urne
Privilege Access Management Tester
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Hey Folks, we will continue our research as we have been doing before and will continue to bring you the best tool so that you can reap the best rewards from companies. Similarly, today we come up with an amazing tool that can cut down your effort to find subdomains and deliver the best results possible.
Let’s Find out
Dependencies Must be Installed
The tool is securely configured within the python language, so we need to install python and some related dependencies first before we can operate the tool.
apt install python3
apt install python3-pip12apt install python3apt install python3-pip

Sublist3r Tool Installation
Now coming to the second part of this tool, where we will first download the project from Github, go to the directory and download the required dependencies.
git clone https://github.com/aboul3la/Sublist3r.git
cd Sublist3r
pip install -r requirements.txt123git clone
https://github.com/aboul3la/Sublist3r.gitcd Sublist3rpip install-rrequirements.txt

Done :0 !! Everything is setup perfectly and now we can operate this tool directly through Python commands.
python3 sublist3r.py -h1python3 sublist3r.py-h

Find Subdomain
Finding subdomains through this tool is quite simple as all we have to do is enter the domain name and that’s it.
python3 sublist3r.py -d domain.com1python3 sublist3r.py-ddomain.com
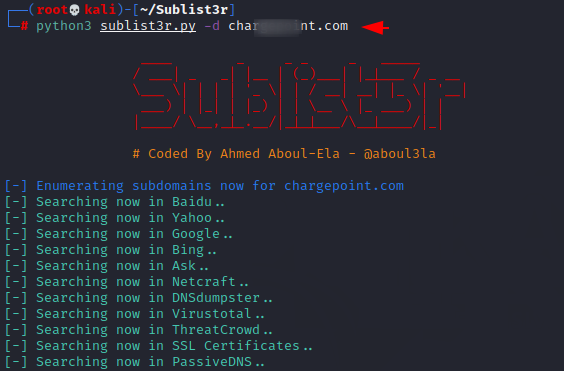
Good

Specific Port
If you want to find the subdomain on which specific port like 80,444,21 etc is running then you can also mention that.
python3 sublist3r.py -d choint.com -p 80,4431python3 sublist3r.py-dchoint.com-p80,443

Save Output
There is also an option available to save all your output to any text file.
python3 sublist3r.py -d chargepoint.com -p 80,443 -o result.txt1python3 sublist3r.py-dchargepoint.com-p80,443-oresult.txt

Amazing
