asadsumra99
Data Exfiltration Specialist
LEVEL 1
400 XP
From Wikipedia
Session hijacking, sometimes also known as cookie hijacking is the exploitation of a valid computer session—sometimes also called session key—to gain unauthorized access to information or services in a computer system. In particular, it is used to refer to the theft of a magic cookie used to authenticate a user to a remote server. It has particular relevance to web developers, as the HTTP cookies used to maintain a session on many web sites can be easily stolen by an attacker using an intermediary computer or with access to the saved cookies on the victim’s computer.
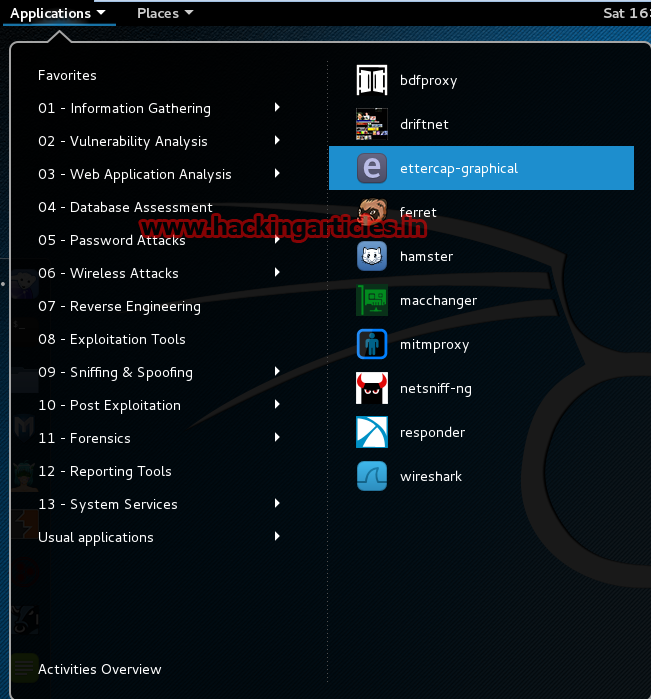
First of all, login to Kali Linux and select ettercap .
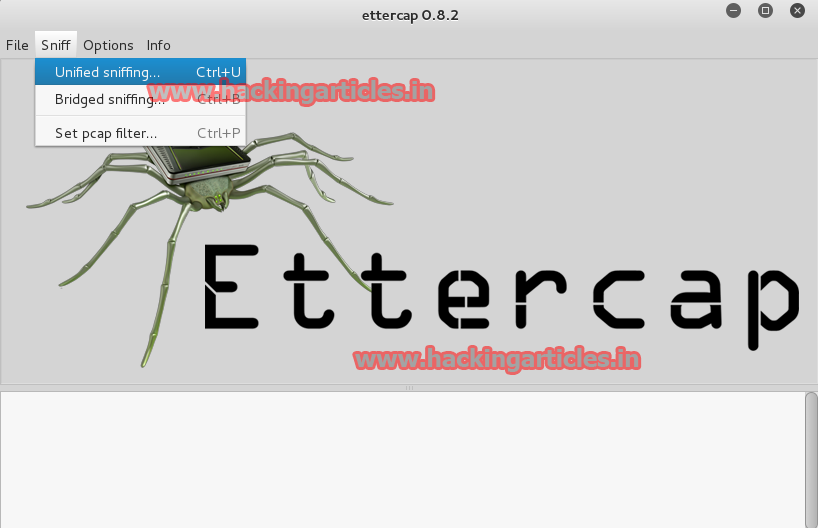
Click on sniff. Select unified sniffing option.
It will ask for network interface. Select eth0 and click OK.

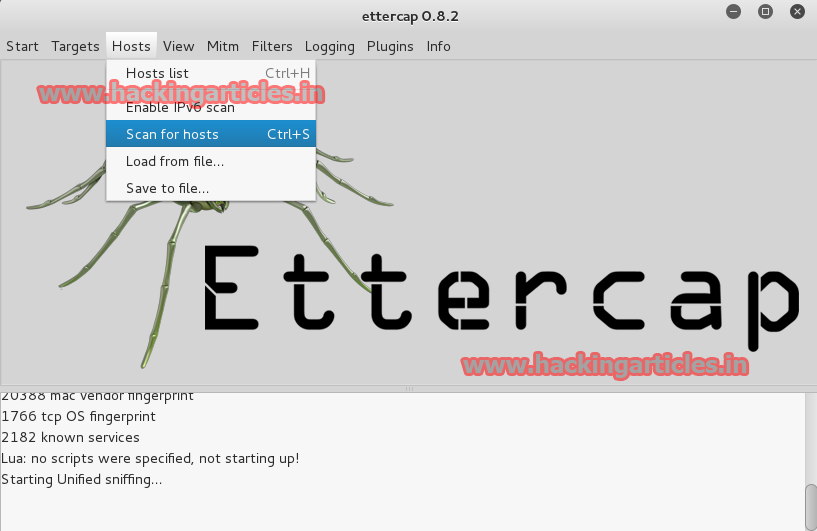
Now select Hosts and click on scan for hosts or press ctrl+s.
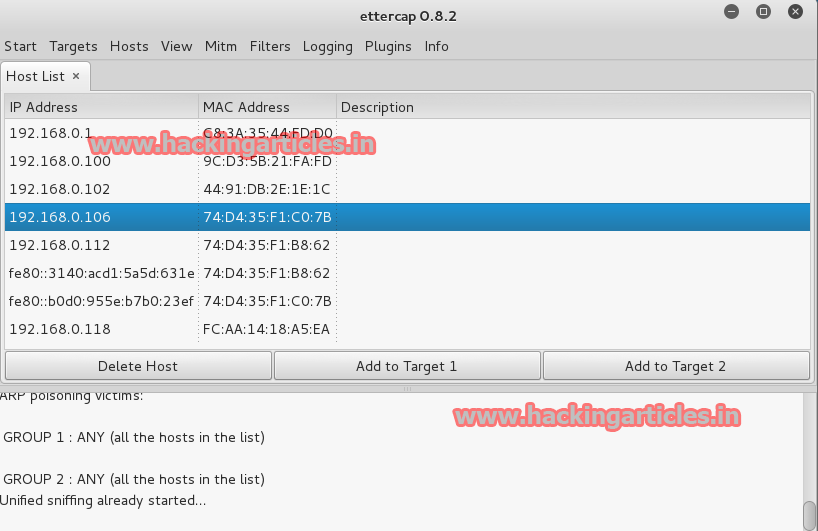
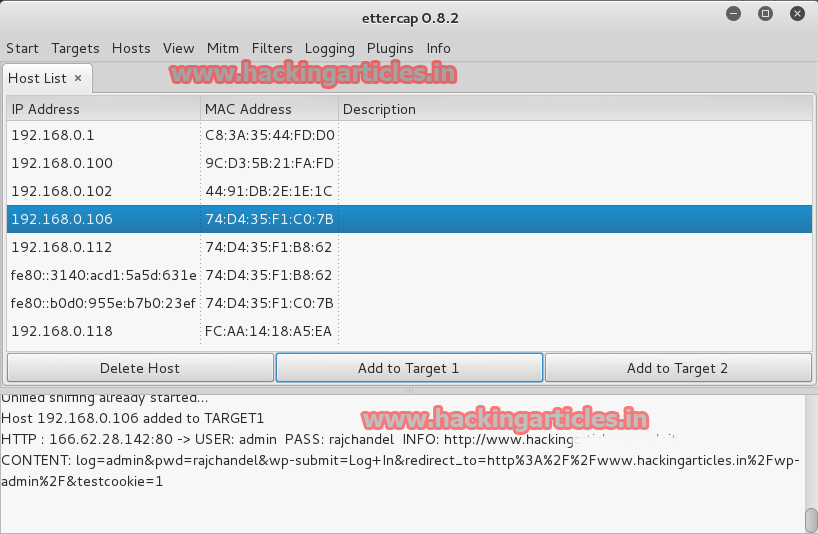
It will show the IP Addresses in the network. Select the target IP Address like 192.168.1.106 and click on add to Target 1.
Now select Mitm ( man in the middle) option. Click on ARP poisoning.

It will ask for sniff remote connections or only poison one-way. Check the option sniff remote connections.

Now Select start option and click on start sniffing or press shift+ctrl+W.

It will show sniffing.
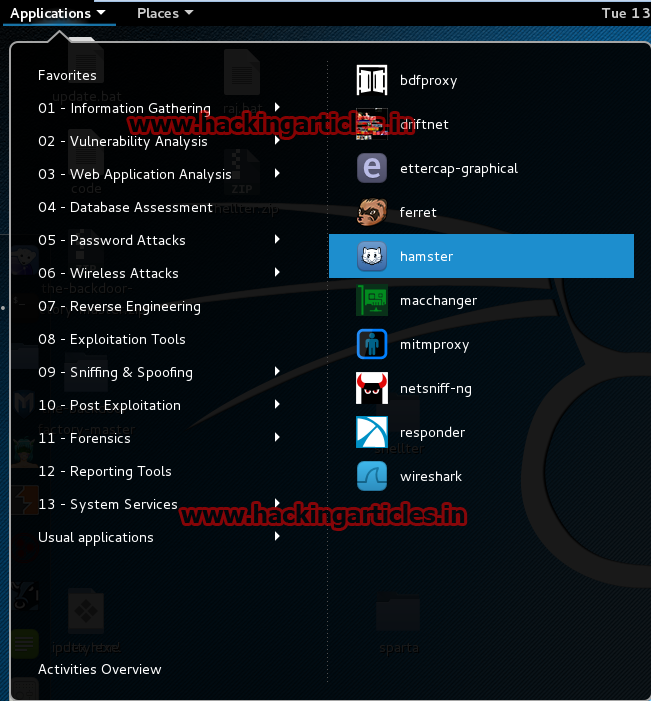
Now select hamster tool to manipulate data by using proxy.
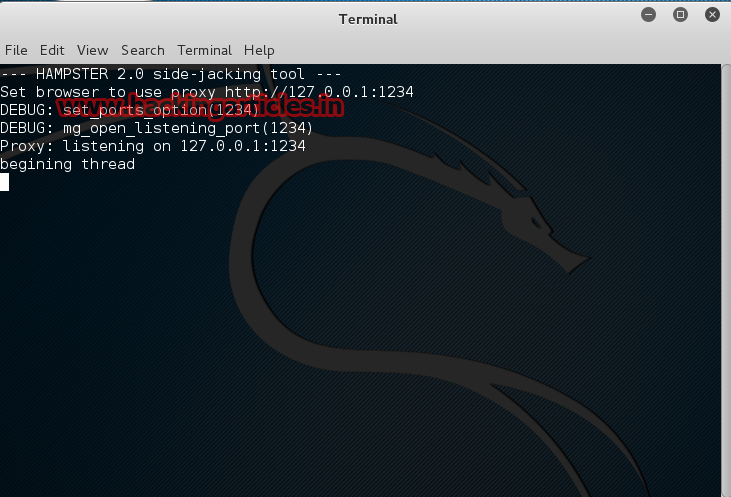
It will show browser proxy such as http://127.0.0.1:1234.
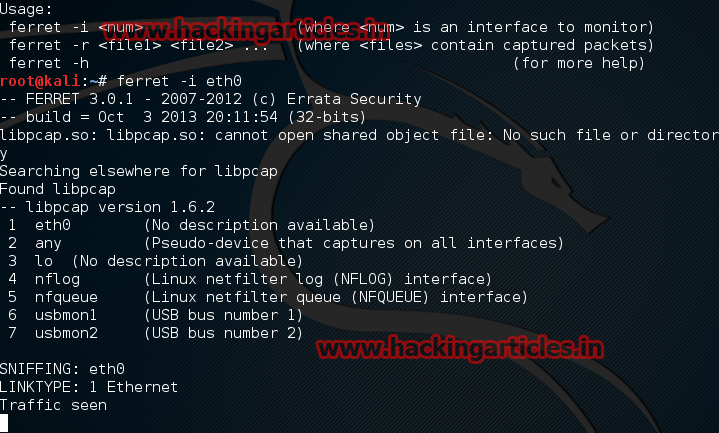
Now select ferret tool to grab the session cookies.

Type the command ferret –i eth0.
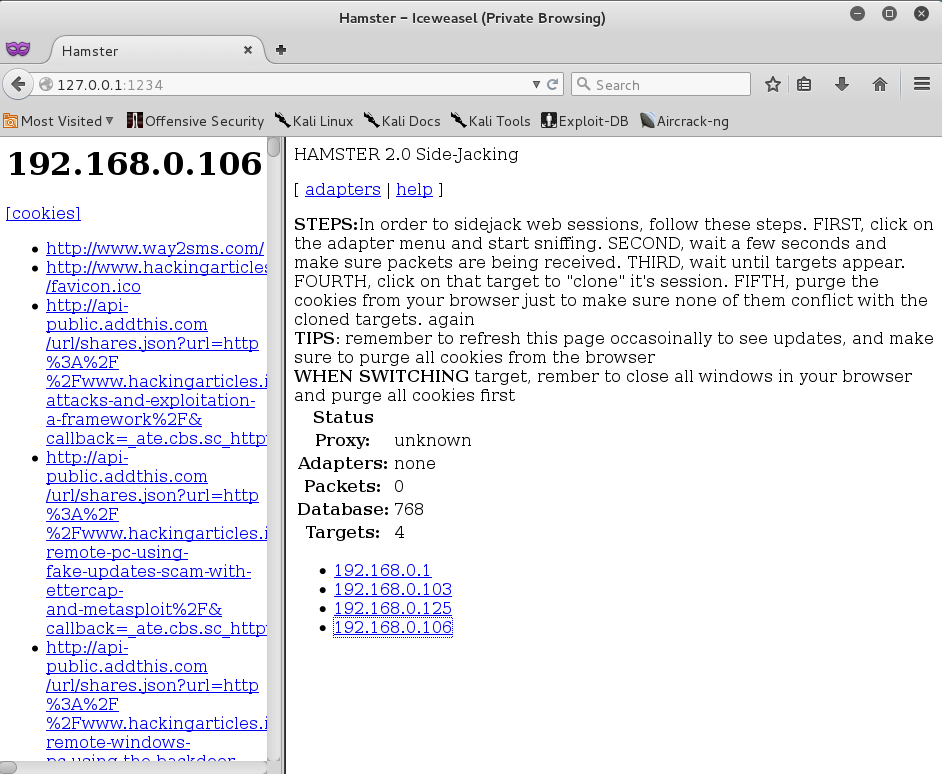
Now type 127.0.0.1:1234 in the browser and click on target IP. It will show Session Cookies.
Session hijacking, sometimes also known as cookie hijacking is the exploitation of a valid computer session—sometimes also called session key—to gain unauthorized access to information or services in a computer system. In particular, it is used to refer to the theft of a magic cookie used to authenticate a user to a remote server. It has particular relevance to web developers, as the HTTP cookies used to maintain a session on many web sites can be easily stolen by an attacker using an intermediary computer or with access to the saved cookies on the victim’s computer.
First of all, login to Kali Linux and select ettercap .

Click on sniff. Select unified sniffing option.

It will ask for network interface. Select eth0 and click OK.

Now select Hosts and click on scan for hosts or press ctrl+s.

It will show the IP Addresses in the network. Select the target IP Address like 192.168.1.106 and click on add to Target 1.

Now select Mitm ( man in the middle) option. Click on ARP poisoning.

It will ask for sniff remote connections or only poison one-way. Check the option sniff remote connections.

Now Select start option and click on start sniffing or press shift+ctrl+W.

It will show sniffing.

Now select hamster tool to manipulate data by using proxy.

It will show browser proxy such as http://127.0.0.1:1234.

Now select ferret tool to grab the session cookies.

Type the command ferret –i eth0.

Now type 127.0.0.1:1234 in the browser and click on target IP. It will show Session Cookies.
