CabbageOwa
Anime Fan Theorist
LEVEL 1
400 XP

Hey Folks, in this tutorial we are going to talk about an (GUI) based vulnerability scanner tool. This tool is specifically designed to find open ports, technology and hidden directories in websites. It uses the same tools that we are using during website scanning and enumeration, but the difference will be that with this tool we can see attacks with (GUI) interfaces.
Requirements
Kali Linux
Lets take a look
Installation
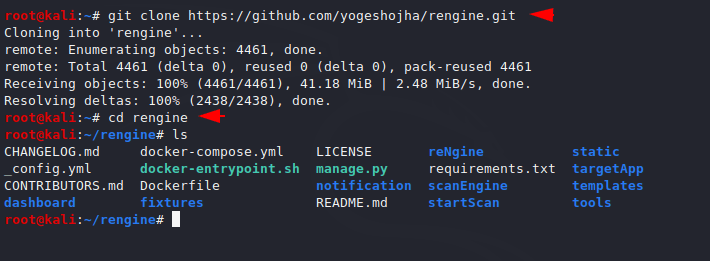
Installation is quite simple but we need to meet some requirements of this tool. First, we download the tool from github using the following command. We need to go to the directory after which we will install some other tools.
git clone https://github.com/yogeshojha/rengine.git
cd rengine
ls123git clone
https://github.com/yogeshojha/rengine.gitcd renginels
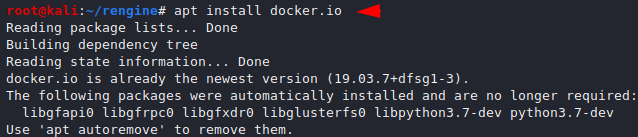
We have to download the docker using the following command. Which is necessary for the tool.
apt install docker.io1apt install docker.io
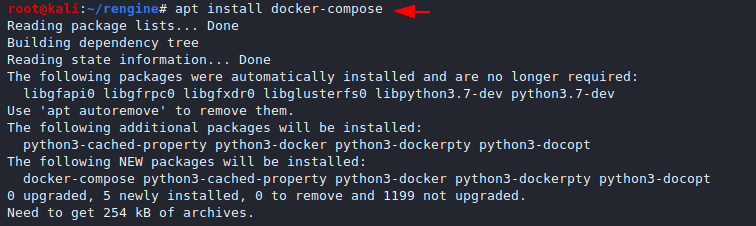
As well as we need to download the composer that will help us to compose our files into the docker.
apt install docker-compose1apt install docker-compose
The installation is almost done, now we will start and enable docker using the following command.
systemctl start docker
systemctl enable docker12systemctl start dockersystemctl enable docker
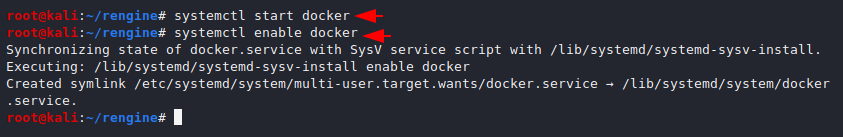
Now all we need to do is execute the following command and it will automatically install all the necessary servers and files and build a vulnerability scanner without much effort.
docker-compose up --build1docker-compose up--build
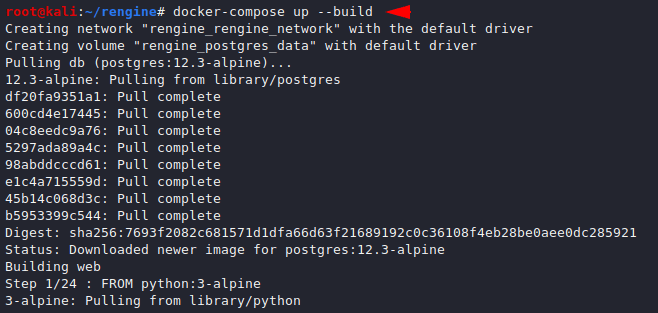
This may take some time but after the process is complete we can check the location of our web server by the ps command.
docker ps1docker ps
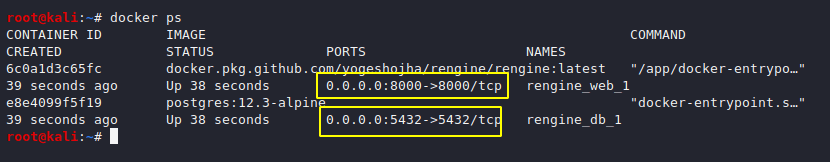
We are all done, now we need to create username and password for login (GUI).
docker exec -it rengine_web_1 python manage.py createsuperuser1docker exec-it rengine_web_1 python manage.py createsuperuser
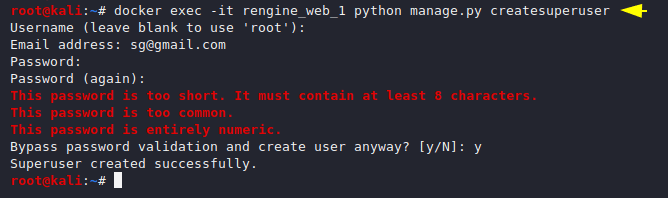
Execute the following location in the terminal and login into the scanner. Interface and usage of this tool is quite easy, just follow our instructions and enter your first target in the input field.
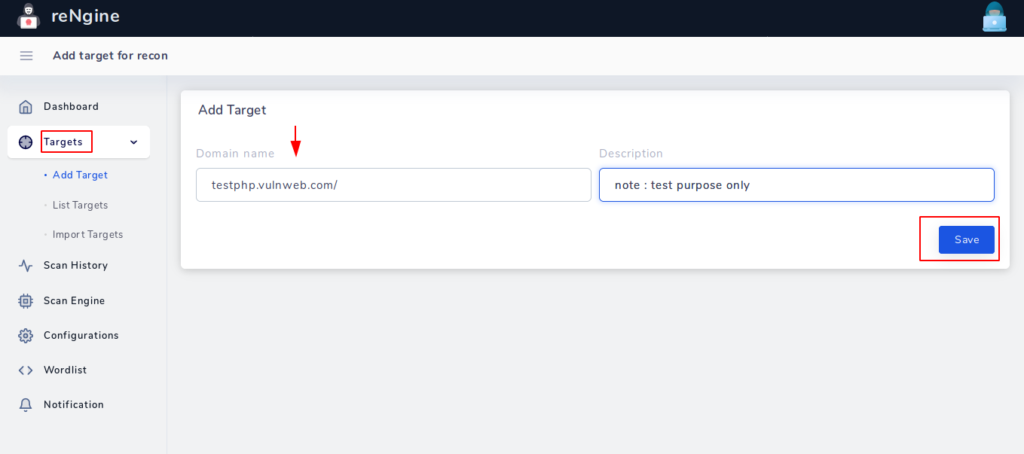
After submitting the target, you will reach the target list in which you have to click on the highlighted icon.
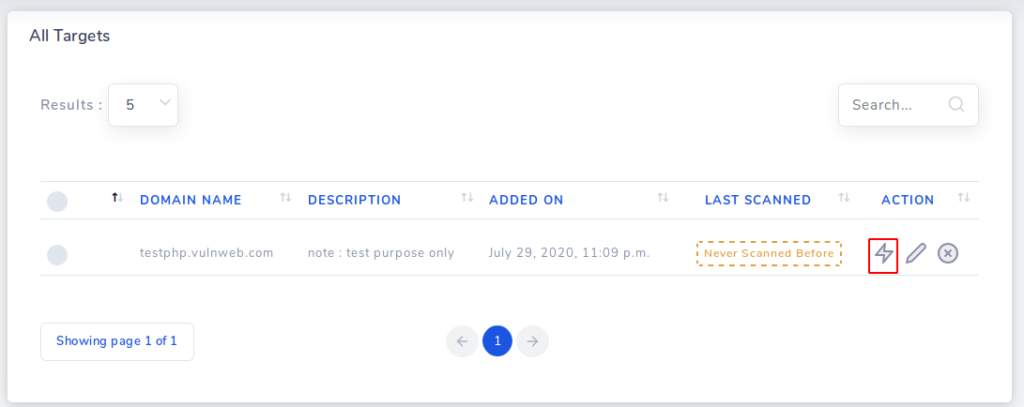
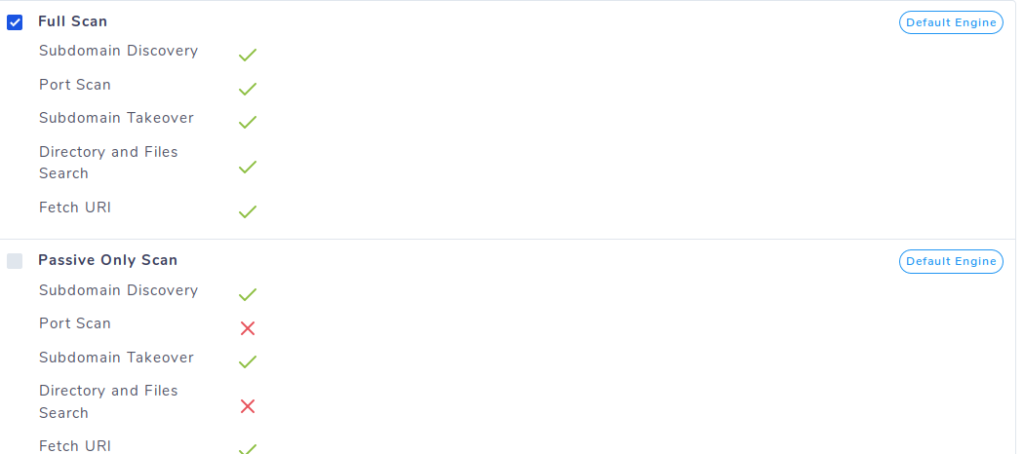
Here we can select the option as per need but for the first attempt we will choose full scan option.
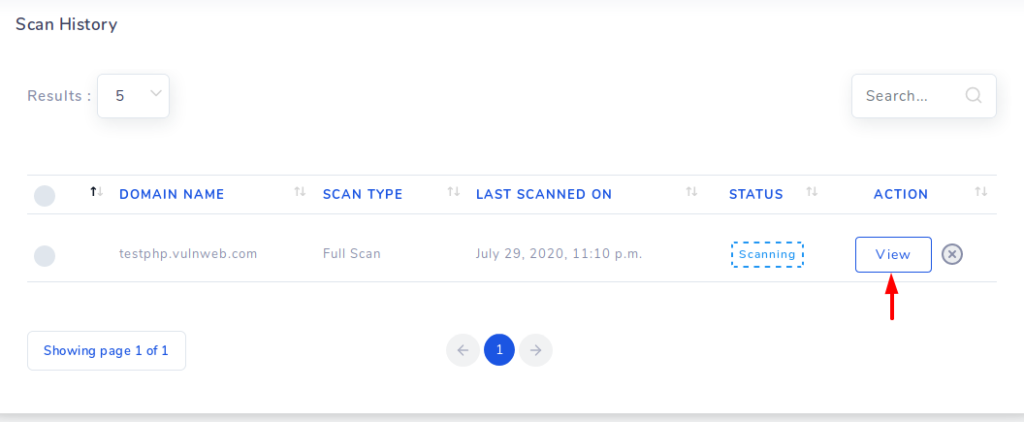
Scanning has started and click on the view option to see the results.
As you can see it can give us results related to open ports, technology and more. But the important thing is that it does not provide us the vulnerability of open ports.
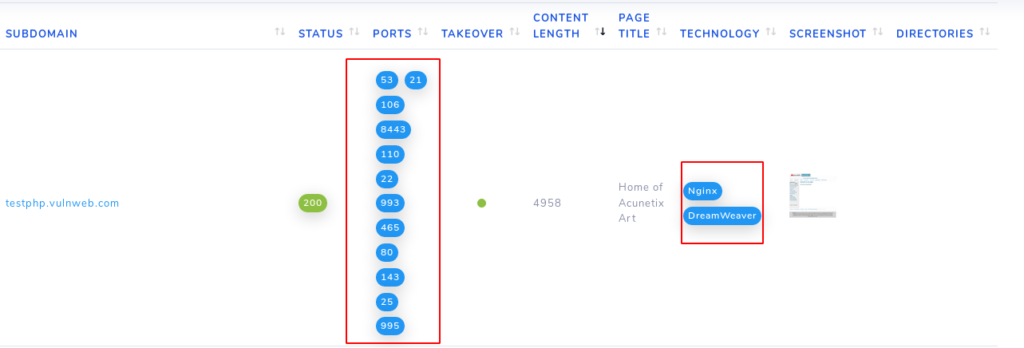
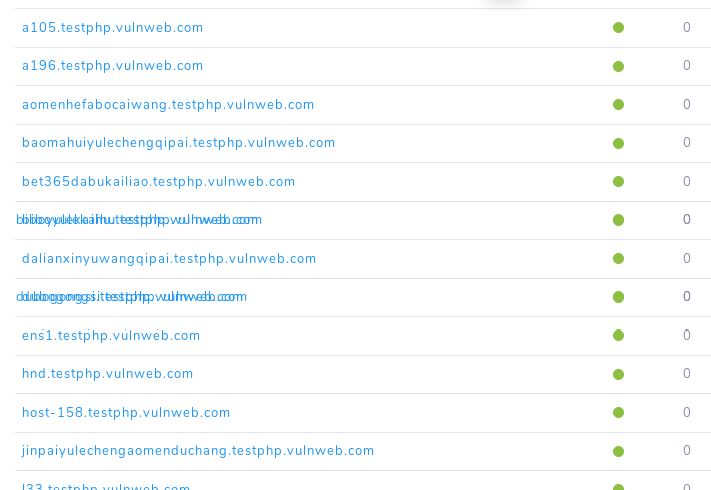
Further it also provide us the subdomain list of the target.
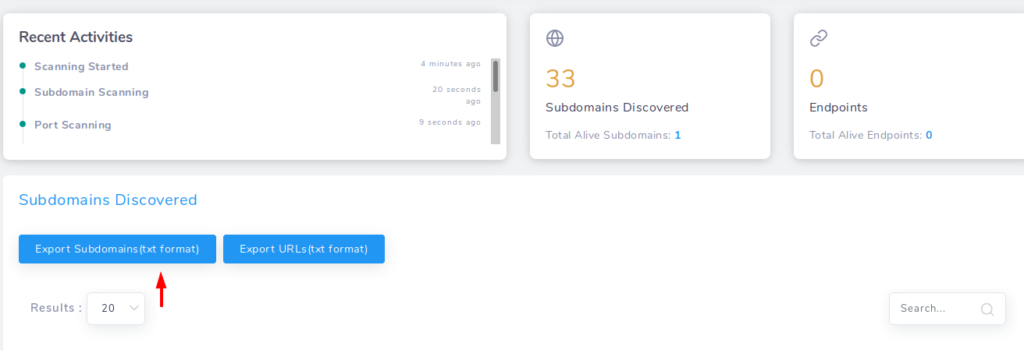
Even we can export the subdomain list in txt file.
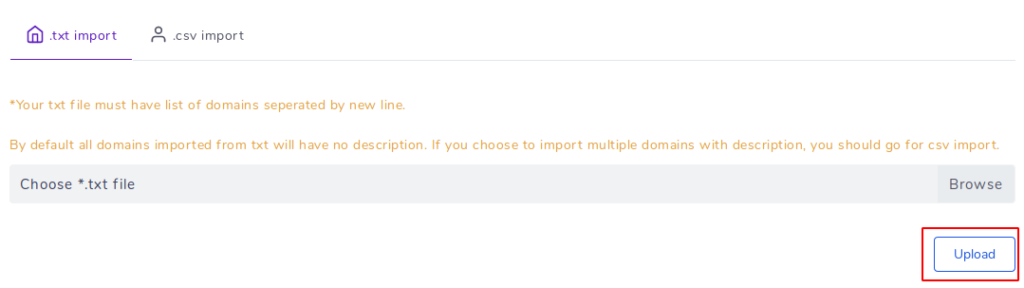
If we want to scan multiple domains at one time then we can use txt file.
In this tutorial, we have included all the features of this tool which can help in our work but similarly you can see all the features of this tool in your terminal.