ItsHighNoon
Debugging Workflow Master
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hey Folks, in this tutorial we will discuss on an interesting tool called “REDHAWK“. It’s an all in one tool for information gathering and vulnerability scanning. The tool uses multiple combinations of other third party tools as well as currently is able to detect the following CMSs (Content Management Systems).
List of CMS Supported
- WordPress
- Joomla
- Drupal
- Magento
Let’s take a look
Installation
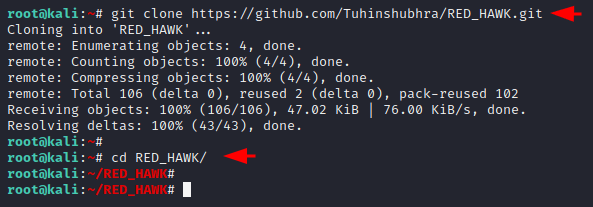
Now first of all we will download this project using git command from gitub and after cloning the repository then we will go to the directory of this tool.
Note : make sure you should have php module to execute this tool.
git clone https://github.com/Tuhinshubhra/RED_HAWK
cd RED_HAWK12git clone
https://github.com/Tuhinshubhra/RED_HAWKcd RED_HAWK
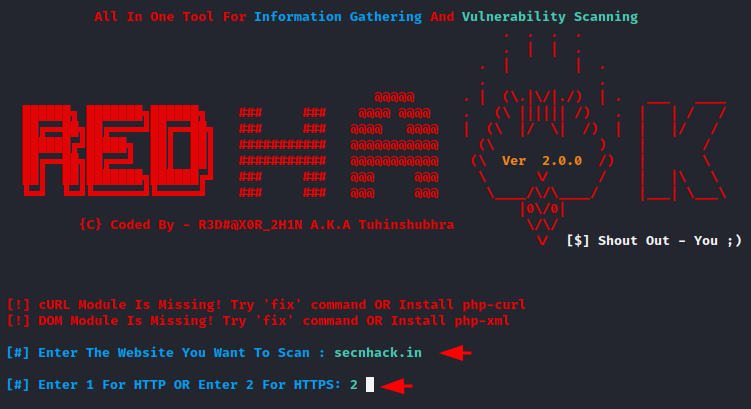
Done
php rhawk.php1php rhawk.php
Great
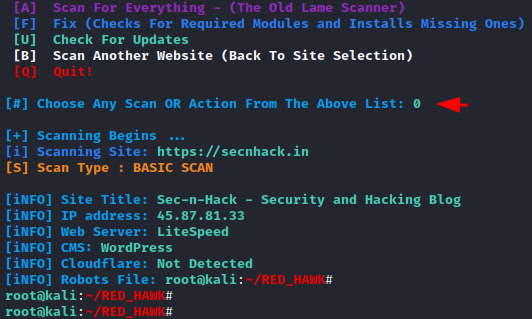
DNS Lookup
If you want to collect information related to the DNS server of the target website then you can use option “4”.
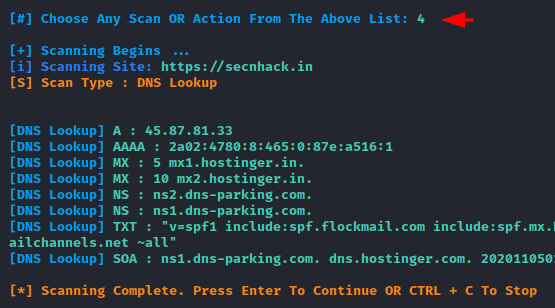
Calculate Subnet Mask
Similarly by using the “5” option of this tool we can calculate the subnet mask of this target web application.
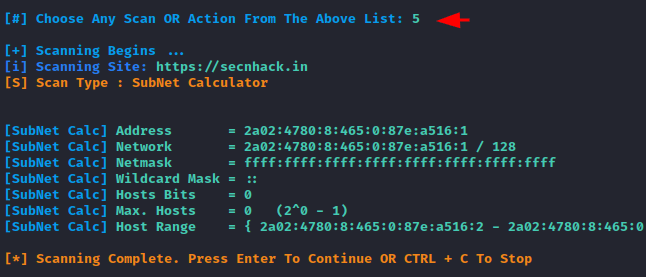
Open Port Scanning
Often developers forget to add security to the active service running on the server, allowing the attacker to exploit those loopholes and remotely acquire the entire web server. So we use the following tools to find available or open ports on target web server.
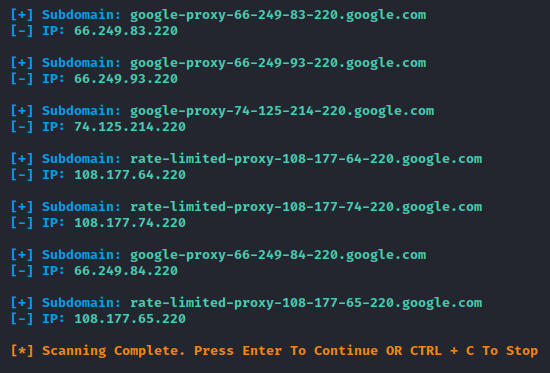
Subdomain Finding
In addition, we can retrieve subdomain details through a particular host.
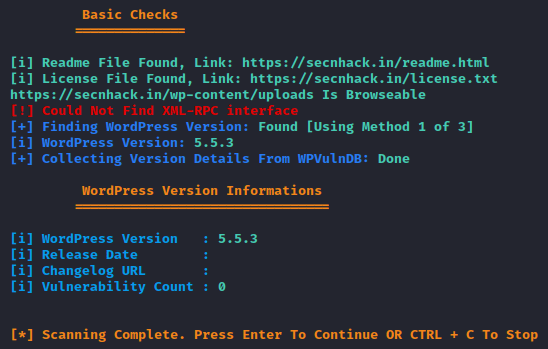
Basic Scanning
Now we will choose option “11” to perform a basic scan against the target web server.
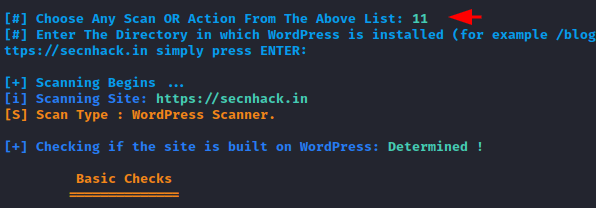
Done