Arzeo
Cloud Security Auditor
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

Nmap is a network mapper that has emerged as one of the most popular and free network discovery tool. Most of the hackers and the pentesters are using this tool for scanning the networks. Nmap is a open source tool which you can download it from here. In Kali linux and parrot it’s inbuilt tool. Just type Nmap it will execute.
About the Nmap Tool
Nmap is a network scanning tool that uses IP packets to identify all devices are connected to network or internet. Its choice of hackers in which they can easily find open ports, which operating systems (OS) you are using and architectures. This tool is also be used for testing the security and find the vulnerability in the network.
Difference Between Nmap and Zenmap
There is no much difference in both tool, both are open source tool and used for network scanning and but Nmap is CLI (Command Line) based tool while Zenmap is GUI ( Graphical User Interface ) based tool. Both is available on many operating system such as (Linux, Windows, Mac OS X etc). Nmap tool is easy to use for beginners in which has lot of additional features. Nmap is pre-installed tool in various os such as parrot os and kali linux while Zenmap is not a pre-installed tool you will have to download form the outside source or official website so you have to try more as compare Nmap.
Installation
First we will install zenmap in our kali machine and for this you have to add the following configuration in sources.list file.
nano /etc/apt/sources.list1nano/etc/apt/sources.list
After open the file add the source commands by given below.
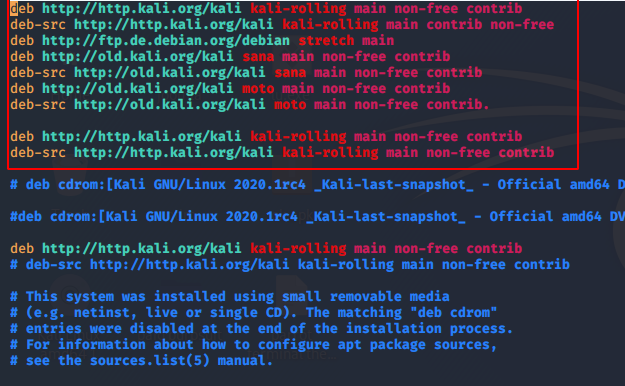
deb http://http.kali.org/kali kali-rolling main non-free contrib
deb-src http://http.kali.org/kali kali-rolling main contrib non-free
deb http://ftp.de.debian.org/debian stretch main
deb http://old.kali.org/kali sana main non-free contrib
deb-src http://old.kali.org/kali sana main non-free contrib
deb http://old.kali.org/kali moto main non-free contrib
deb-src http://old.kali.org/kali moto main non-free contrib.1234567deb http://http.kali.org/kali kali-rolling main non-free contribdeb-src http://http.kali.org/kali kali-rolling main contrib non-freedeb http://ftp.de.debian.org/debian stretch maindeb http://old.kali.org/kali sana main non-free contribdeb-src http://old.kali.org/kali sana main non-free contribdeb http://old.kali.org/kali moto main non-free contribdeb-src http://old.kali.org/kali moto main non-free contrib.
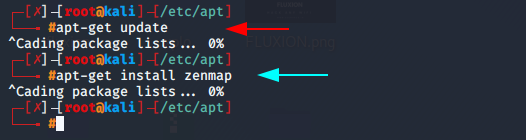
Run the following command to install Zenmap.
apt-get update
apt-get install zenmap12apt-get updateapt-get install zenmap
Now you can start your zenmap tool using the following commmand.
zenmamp1zenmamp
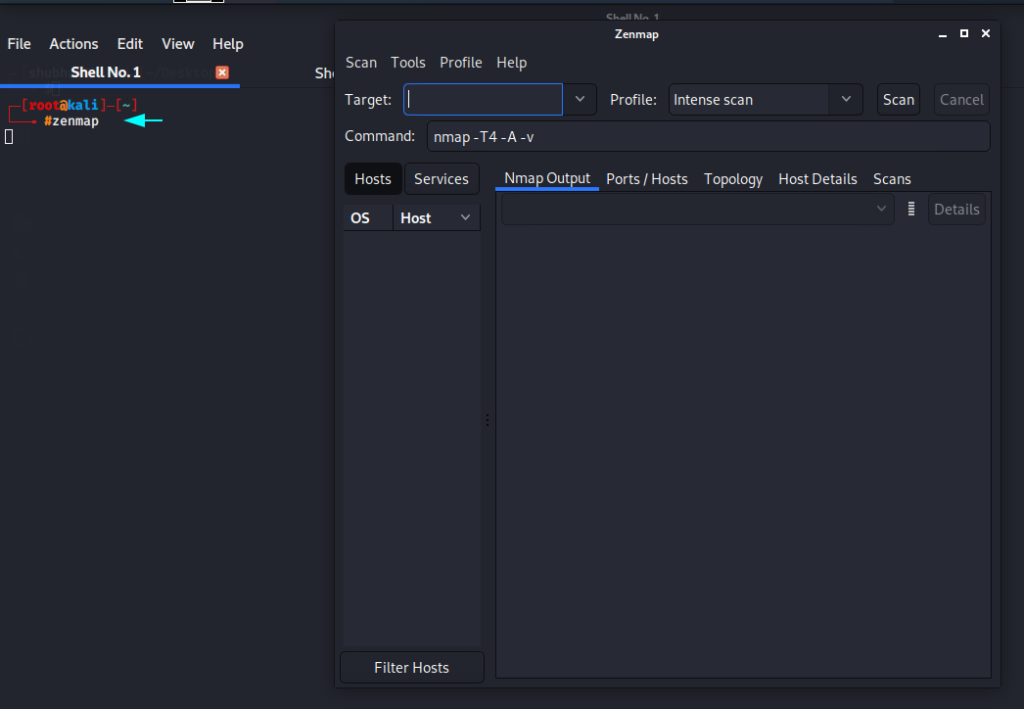
Lets take a look as beginners!!
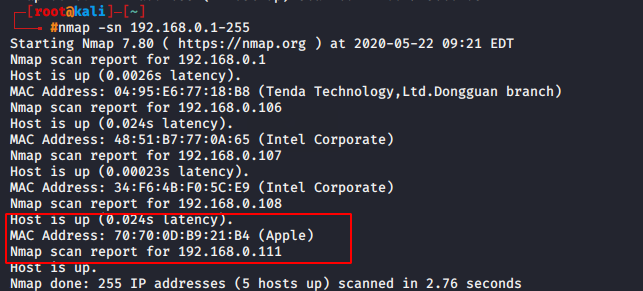
Host Scan
Host scan is use to check how many host are active in network by send the ARP ( Address Resolution Protocol ) request to all host in.
1) nmap -sn <IP range>
2) nmap -sP <IP range>
nmap -sP 192.168.0.1-2551nmap-sP192.168.0.1-255
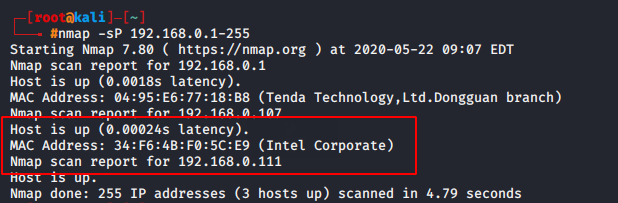
Simple scan
This will tell you the number of TCP/UDP ports open from 1 to 65535.
command
nmap 192.168.0.1071nmap192.168.0.107
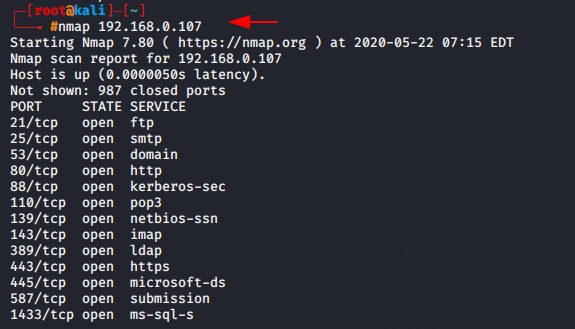
TCP scan
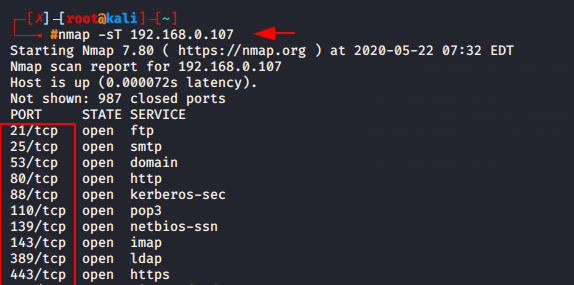
TCP (Transmission Control Protocol) uses a three-way handshake process to establish and maintain a network conversation. If you only want to know about TCP ports then you can use this command.
command
nmap -sT 92.168.0.1071nmap-sT92.168.0.107
UDP scan
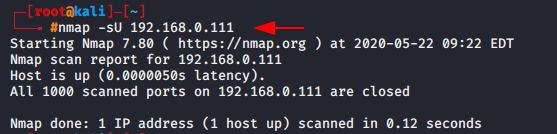
UDP (User Datagram Protocol) is also be used for communicate or data transmission but cause of unreliable packet delivery and packets drops it is not use. In the testing purpose UDP protocol are use to check the availability to UDP ports.
command : ) nmap [scan UDP] [target IP]
nmap -sU 192.168.0.1111nmap-sU192.168.0.111
OS Detection scan
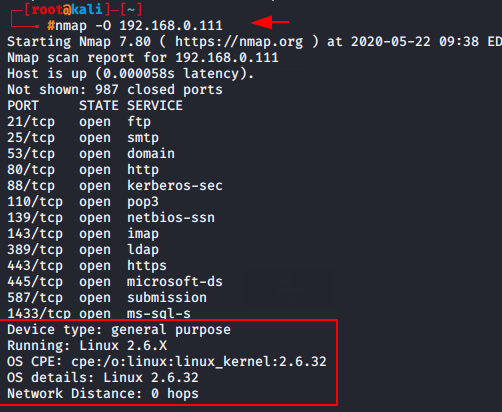
If you want to get information about the operating system of the target machine so you can add ‘o’ syntax in your command.
command
nmap -O 192.168.0.1111nmap-O192.168.0.111
Port range scan
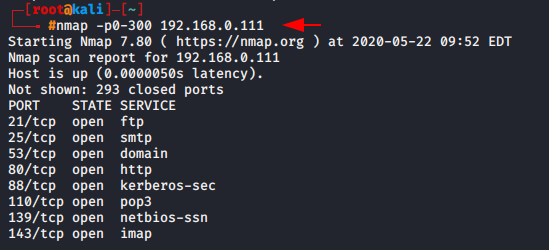
If you suspect that the middle ports may be open so you can set the range of protocols.
command
nmap -p0-300 192.168.0.1111nmap-p0-300192.168.0.111
Port scan
Sometimes we need to scan only specific port of target machine, Hence we can easily scan the particular port by adding ‘-p’ syntax.
command
nmap -p21 192.168.0.11nmap-p21192.168.0.1
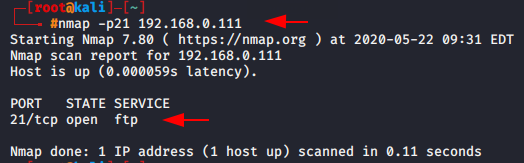
Version scan
If penetration testers want to test that whether the port version is visible, they can use the following command.
command
nmap -sV -p80 192.168.0.1111nmap-sV-p80192.168.0.111
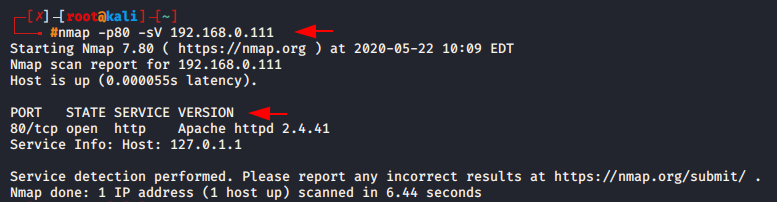
Protocol scan
The protocol scan is useful for beginners to determine which port are work on which protocol.
command
nmap -sO 192.168.0.1111nmap-sO192.168.0.111
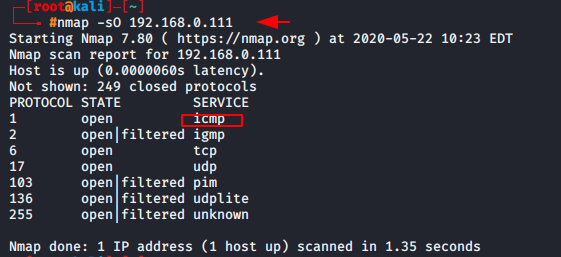
Script scan
Script scan is advantage for penetration tester to detect the service vulnerability, Malware threat and more information about it.
command
nmap -sO 192.168.0.1111nmap-sO192.168.0.111
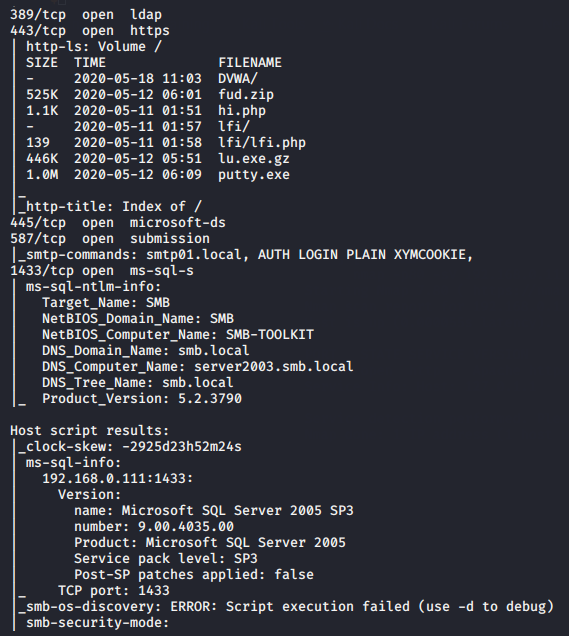
Aggressive Scan
Aggressive scan is time taking scan because it run four scan at a time such as :
-O : OS detection
-sV : version scanning
–sC : script scanning
-traceroute : traceroute ( Hopes Count )
commands
nmap -A 192.168.0.1111nmap-A192.168.0.111
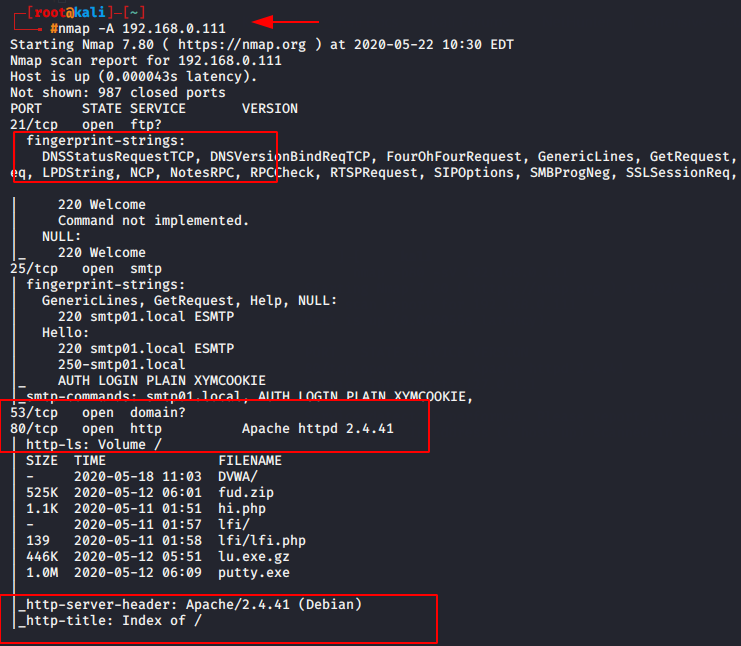
Fast scan
If you are taking this much time to scan the ports so you can go with fast scan option. As you can see in below given image when we execute the normal scan so latency time had 0.00060 sec but when we execute the fast scan then the latency arrive at 0.00050 second.
command
nmap -F 192.168.0.1111nmap-F192.168.0.111
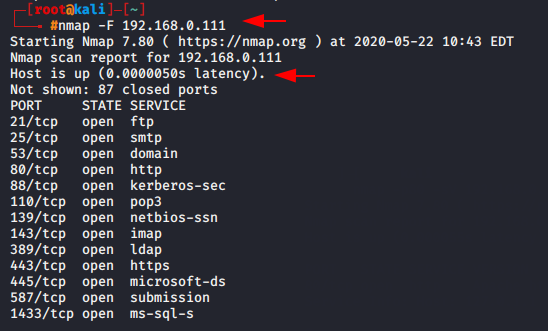
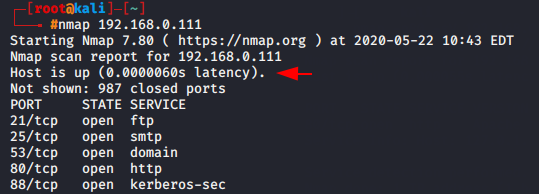
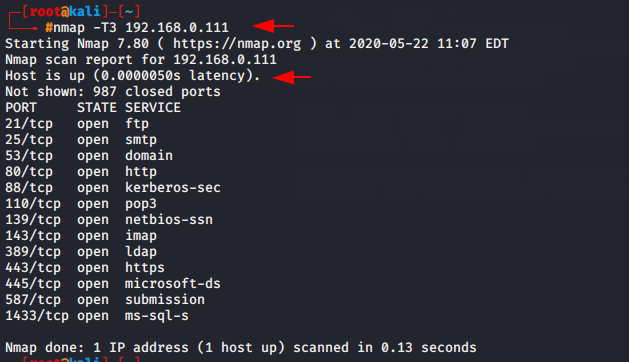
Timing Template Scan
Timing scan is use for reducing the scanning time. Nmap offers six timing templates scan which is known such as :
T0: paranoid
T1: sneaky
T2: polite
T3: normal
T4: aggressive
T5: insane
If you will try to use aggressive scan or insane scan so it will skip some ports, that is problem with it. In our case we will choose normal scan.
command
nmap -T3 192.168.0.1111nmap-T3192.168.0.111
List scan
If you want to scan the select target so you can put the host details such as IP address in Txt file.
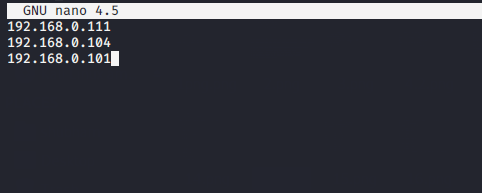
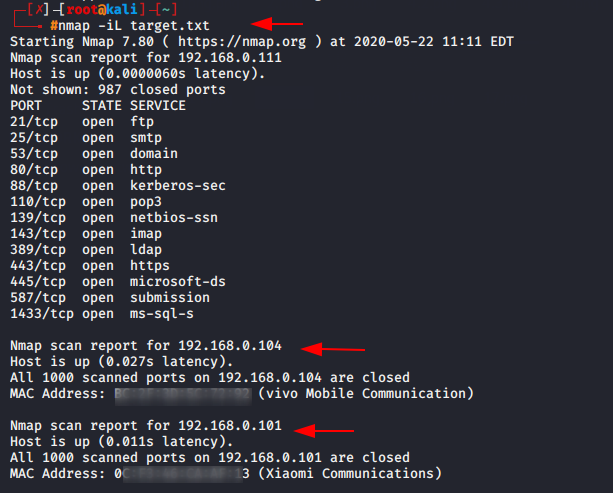
After that execute the following command to obtain the deep details about the IP address.
command : ) nmap
- [list location]
nmap -iL target.txt1nmap-iL target.txt
Output scan
Sometime penetration tester wants to store their outputs in file so they can use the following commands.
command nmap [target IP] [-o] [output location]
nmap [target IP] [-o] [output location]
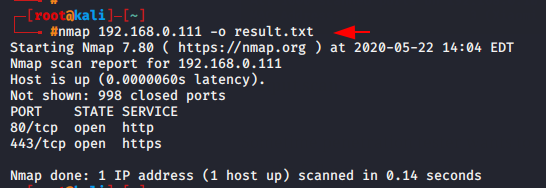
nmap 192.168.0.111 -o result.txt1nmap192.168.0.111-oresult.txt
About the AuthorBhanuprathap Reddy is Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be connect on Linkedin.